We may not have the course you’re looking for. If you enquire or give us a call on +971 8000311193 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.
Kali Linux stands out in cybersecurity, particularly for its comprehensive suite of tools tailored for wireless network analysis and security. This powerful distribution is designed for penetration testers and security professionals. The Kali Linux Features offers an array of features to assess and strengthen the protection of wireless networks.
Kali Linux has capabilities for WiFi network cracking, real-time traffic analysis, packet sniffing, and injection. It supports various wireless protocols, making it an invaluable tool for uncovering vulnerabilities, conducting thorough security audits, and implementing robust defensive strategies against potential wireless threats. Read this blog to learn more about the Kali Linux Features.
Table of Contents
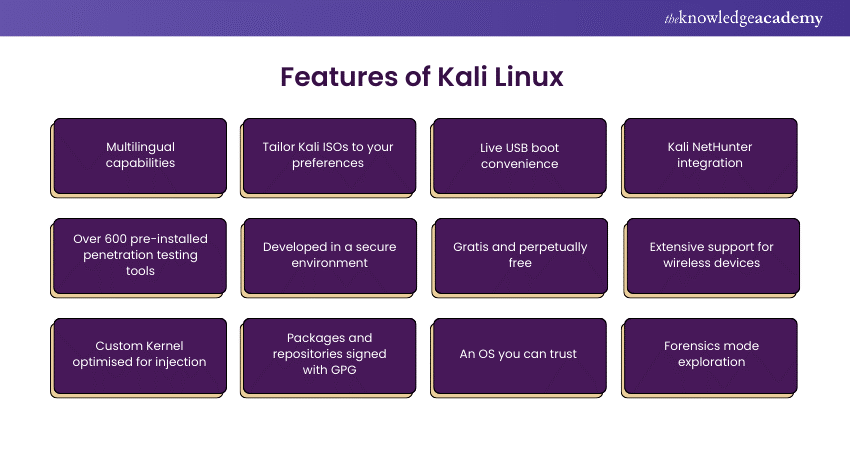
1) Features of Kali Linux
a) Multilingual capabilities
b) Tailor Kali ISOs to your preferences
c) Live USB boot convenience
d) Kali NetHunter integration
e) Over 600 pre-installed penetration testing tools
f) Developed in a secure environment
g) Gratis and perpetually free
h) Extensive support for wireless devices
i) Custom Kernel optimised for injection
j) Packages and repositories signed with GPG
k) An OS you can trust
l) Forensics mode exploration
2) Conclusion
Features of Kali Linux
Let’s discuss the features of Kali Linux in detail:
Multilingual capabilities
Acknowledging the global nature of cybersecurity, Kali Linux offers multilingual support, which makes it accessible to users globally. This feature enables non-English speaking users to interact with the software in their native language, breaking down language barriers and enhancing the overall user experience. Multilingual support is crucial for a diverse user base, allowing more people to effectively leverage Kali Linux's capabilities.
Tailor Kali ISOs to your preferences
One of the unique aspects of Kali Linux is its customisability. Users can create tailor-made Kali ISOs, selecting only the necessary tools and components. This flexibility allows for a lightweight and efficient setup, particularly beneficial for users with specific requirements or those operating on hardware with limited resources. Custom ISOs ensure the user's environment is streamlined for their particular use case, whether for a portable pen-testing kit or a specialised security setup.
Live USB boot convenience
Kali Linux supports live USB booting, a feature that allows users to run the operating system directly from a USB drive without installing it on the hard drive. This provides immense convenience and flexibility, especially for those who need a portable and quick-to-deploy system. The live USB feature is also beneficial for trying out Kali Linux without altering the existing setup of a computer.
Kali NetHunter integration
Kali Linux integrates with Kali NetHunter, an Android-based penetration testing platform. This integration expands the capabilities of Kali Linux to mobile devices, allowing security professionals to perform tests and attacks from smartphones and tablets. NetHunter supports various Android devices and offers a range of tools tailored for mobile security.
Over 600 pre-installed penetration testing tools
Kali Linux has a vast arsenal of over 600 pre-installed penetration testing tools. These tools cover various cybersecurity tasks, from network analysis and vulnerability scanning to hacking and forensic analysis. This extensive collection saves users time and effort in acquiring and installing these tools separately, making Kali Linux a comprehensive solution for security professionals.
Developed in a secure environment
Security is at the forefront of Kali Linux's development. The operating system is developed in a secure environment, ensuring the code and the packages are free from vulnerabilities and backdoors. This focus on security makes Kali Linux a trustworthy tool for professionals who handle sensitive security tasks.
Gratis and perpetually free
Kali Linux is available for free and commits to remaining gratis. This approach makes powerful cybersecurity tools accessible to everyone, from students and hobbyists to professionals and organisations. The absence of a price tag encourages a broader audience to explore and utilise these security tools, contributing to the overall strengthening of global cybersecurity knowledge and practices.
Extensive support for wireless devices
Kali Linux offers extensive support for wireless devices, making it a go-to choice for professionals working with wireless security. This includes support for a range of wireless network adapters and protocols, crucial for tasks like network monitoring, packet sniffing, and penetration testing.
Custom Kernel optimised for injection
Kali Linux features a custom kernel that is optimised for packet injection, a technique used in network security assessments. This custom kernel enhances the effectiveness of tools that perform such tasks, making Kali Linux particularly efficient for testing the security of wireless networks.
Learn more about Automation and Penetration with our Automation & Penetration Testing Training!
Packages and repositories signed with GPG
The integrity of Kali Linux is further ensured by using GPG signatures for its packages and repositories. This security measure guarantees that the packages have not been tampered with and are from a trusted source. Users can confidently install updates and new tools, knowing they're safeguarded against malicious tampering.
An OS you can trust
Trust is a cornerstone of Kali Linux. With its commitment to security, constant updates, and strong community backing, Kali Linux has established itself as a reliable and versatile operating system for security professionals. The transparency in its development process and the open-source nature further contribute to its trustworthiness.
Forensics mode exploration
Kali Linux includes a forensics mode explicitly designed for forensic investigators. In this mode, the operating system does not automatically mount the host computer's hard drive, preventing potential evidence contamination during a forensic analysis. This feature makes Kali Linux suitable for penetration testing and digital forensics, an essential aspect of cybersecurity.
Conclusion
We hope that from this blog, you learnt about the different Kali Linux Features and how they make it necessary for cybersecurity professionals. Its rich set of features like multilingual capabilities, customisability, live USB booting, NetHunter integration, and extensive pre-installed tools make it a powerhouse for cybersecurity professionals. Its focus on security, accessibility, and comprehensive device support further solidifies its position as a preferred choice in cybersecurity tools.
Do you want to learn more about tools and techniques used in Automation? Sign up now for our Tools and Techniques for Penetrating Testing Training!
Frequently Asked Questions

Kali Linux offers over 600 pre-installed penetration testing tools, customisability, and multilingual support, and it is free. It's optimised for security professionals with features like a custom kernel for packet injection and extensive wireless device support.

Drawbacks of Kali Linux include a steep learning curve for beginners, it's not ideal for daily computing needs and can be overwhelming due to its vast array of tools and features.

Kali Linux, prioritising user privacy and security, does not collect user data. It's built with a focus on ethical hacking and cybersecurity, adhering to privacy standards expected in such environments.

The Knowledge Academy takes global learning to new heights, offering over 30,000 online courses across 490+ locations in 220 countries. This expansive reach ensures accessibility and convenience for learners worldwide.
Alongside our diverse Online Course Catalogue, encompassing 17 major categories, we go the extra mile by providing a plethora of free educational Online Resources like News updates, Blogs, videos, webinars, and interview questions. Tailoring learning experiences further, professionals can maximise value with customisable Course Bundles of TKA.

The Knowledge Academy’s Knowledge Pass, a prepaid voucher, adds another layer of flexibility, allowing course bookings over a 12-month period. Join us on a journey where education knows no bounds.

The Knowledge Academy offers various Programming Training, including Python Course, Ruby, and Swift Training. These courses cater to different skill levels, providing comprehensive insights into Object-Oriented Programming methodologies.
Our Programming and DevOps blogs covers a range of topics related to Ruby, offering valuable resources, best practices, and industry insights. Whether you are a beginner or looking to advance your Ruby programming skills, The Knowledge Academy's diverse courses and informative blogs have you covered.
Upcoming IT Security & Data Protection Resources Batches & Dates
Date
 Kali Linux Fundamentals
Kali Linux Fundamentals
Fri 20th Dec 2024
Fri 14th Feb 2025
Fri 11th Apr 2025
Fri 13th Jun 2025
Fri 15th Aug 2025
Fri 10th Oct 2025
Fri 12th Dec 2025







 Top Rated Course
Top Rated Course



 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


