We may not have the course you’re looking for. If you enquire or give us a call on +43 720 115337 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.

Increased Cyber Security attacks pose a huge threat to data streaming over the web. To get rid of these malware attacks, businesses across industries are adopting various Cyber Security risk management strategies. As a result, the Global Cyber Insurance Market is estimated to increase rapidly over the next five years, with the total market size increasing from around £6.61 billion in 2020 to just over £16.54 billion by 2025.
But this isn’t enough. What about the devil in disguise? Dangers caused by Insider Threats are another unrevealed storm that is spreading like wildfire. Although these threats are recognisable; however, businesses still lack sufficient resources to alleviate the risk they pose.
So, how can they hamper security? What are these inevitable threats? Can there be many types of threats? The answer to these questions is here.
Check out this blog to learn more about Insider Threats, how to defend your business from them, and the strategies to prevent them when they arise.
Table of Contents
1) What is Insider Threat in Cybersecurity?
2) Different types of Insider Threats
3) How do Insider Threats occur?
4) How to be safe from insider attacks?
5) Conclusion
Learn more about the potential threats businesses face today and how to mitigate them; register for our Cyber Security Training course today!
What is Insider Threat in Cyber Security?
An Insider Threat is a dynamic and hostile risk that originates from within the organisation affecting its network, applications and databases.
Insider Threats may occur intentionally or unintentionally due to the misuse of the company’s network by various users, such as current employees, former employees, and temporary workers who have direct/indirect access to the company’s networks. These threats may also arise due to tampering with the company’s physical or digital assets by third parties, vendors, and business collaborators.
While traditional Cyber Security measures may detect and remediate risks from external attacks, they cannot always identify internal threats. Additionally, they are two times more harmful than external threats since the organisation's users have plausible control over its assets. As a result, Insider Threats become the cause of most Cyber Security breaches.
Different types of Insider Threats
Due to their presence in different forms and lack of Cybersecurity resources, it becomes impossible to find an Insider Threat. But you need not worry more. Here, we have discussed the different types of Cybersecurity Insider Threats:
Malicious threats
Malicious Insider Threats often appear due to an employee intentionally misusing a company’s information, applications or databases. They have a privilege over other attackers as they are familiar with the company’s security policies and procedures and its vulnerabilities.
The usual intention is to exploit their access to steal information or debase the system for personal, monetary or destructive reasons. A Cyber Security Insider Threat example includes an employee selling confidential information to a competitor. Let's understand malicious threats in detail:
1) Collaborators
Usually, collaborators are authorised users within the organisation who covertly collaborate with a third party to harm the organisation intentionally. They tend to leak, share and sell confidential data to third parties, thus disrupting business operations. Third-party may include competitors, nation-states, criminal organisations or even an individual.
2) Lone wolves
They work independently and act without external support or influence. Lone wolves are particularly harmful as they are privileged with system access. For example, a former employee holding grudges could misuse the assets.
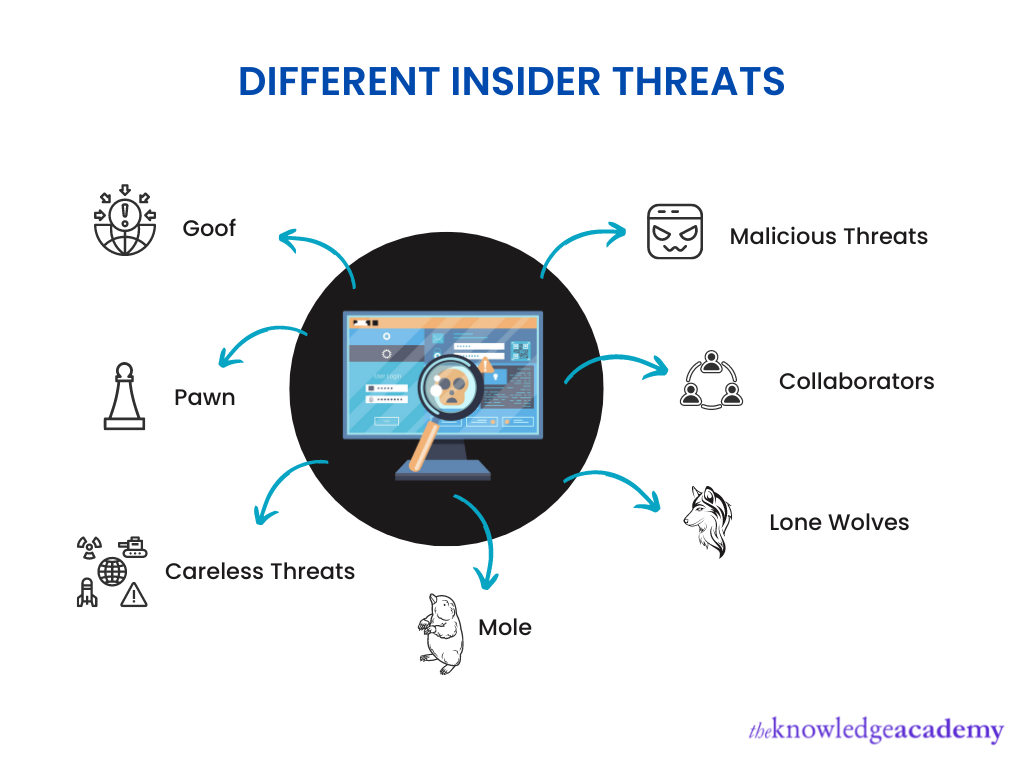
Careless threats
Careless Insider Threats can be categorised as unintentional threats. They can occur due to human error, where an individual could accidentally expose the system to malware attacks. Lack of judgement, unintentional assistance and support, phishing, malware, and a stolen license can be considered errors. Careless threats are also of various types. Let's look at them briefly:
1) Pawn
Users with official control over an organisation’s systems, engineered to act maliciously to harm the organisation’s system inadvertently, are called pawns. This is usually done through social engineering techniques like spear phishing to download malware on a computer or disclose confidential data to fraud.
2) Goof
Unlike a pawn who is engineered to harm the system unintentionally, a goof deliberately takes destructive actions. These can be arrogant, unsophisticated and inefficient users who do not feel the need to follow security rules and regulations. An example of a goof may include a user who stores customers' private data on their own device, even though it is against the policies.
A mole
A mole is an outsider who has gained insider access to the organisation’s systems. They may be a vendor, partner, trader or employee. In this way, they can obtain an advantaged control which they would not have obtained otherwise.
How do Insider Threats occur?
Insider attacks can pop up in various ways and can particularly create a terrifying and derogatory environment. Insider Threats can manifest in various ways; let’s look at why they create a hostile environment:
1) Theft
Simply stealing an organisation’s assets (monetary and intellectual property) can also harm an organisation. Any monetary theft done with the intent to benefit from it is subjected to crime, along with stealing creative ideas, trade secrets, etc.
2) Cyber
Digital fraud is done intentionally or unintentionally through stealing, spying, threatening and damaging technology, virtual reality, computers, devices and networks.
3) Spying
Covert behaviours shown by users (employees, partners, vendors) to gain personal information for military, political, strategic or financial advantage can prove dangerous to an organisation’s financial, intellectual and digital assets.
4) Vandalism
Deliberately damaging an organisation’s physical and virtual assets, such as misconduct with the conservation of data, polluting clean spaces, physically harming the resources, and deleting code to obstruct regular tasks.
How to be safe from insider attacks?
After you have learnt what an Insider Threat is, it's different types, and how it harms enterprises, let’s now understand how one can detect these threats and various ways to mitigate them.
Let's learn how to detect Insider Threats
Threat intelligence tools focus on investigating an organisation's network, computers and application data. But they give minimal attention to the actions of authorised users who can misuse their advantageous access.
Therefore, to keep an eye on Insider Threats, professionals must be aware of abnormal behavioural and web activities. There are specific indicators to register such activities; let’s look at them:
|
Behavioral indicators |
Digital indicators |
|
These indicators include: a) An unhappy or dissatisfied employee, trader, vendor or partner b) Beholding resignation c) Animosity towards co-workers d) Constantly working off-hours e) Attempts to obstruct security f) Regular violation of organisational policies |
Digital indicators imply: a) Atypically signing into the company’s applications and networks b) A sudden rise in the volume of network traffic c) Using unauthorised devices such as USB drives d) Accessing resources that they are not authorised to access e) Sneaking into the network and deliberately searching for confidential data f) Searching for data that is not relevant to their job function g) Emailing crucial data outside the organisation |
But how do you protect yourself from insider attacks?
Most companies still lack resources and methods to fight these attacks and fall into a vicious cycle. So, let’s learn how to be safe from Insider Threats:
1) Promote cultural changes
Promoting a security-aware culture change and digital transformation is the key to eradicating Insider Attacks. Promoting the right attitude can help mitigate carelessness and recognise the roots of abnormal behaviour.
Employees and other officials should participate in regular security training, awareness programs, and constant examination to promote employee satisfaction. Thus, they can recognise their responsibility of ensuring Cybersecurity and keeping the organisation safe.
2) Enforce policies
Create, implement and regulate security policies that every worker should strictly follow in the organisation. This would help prevent doubts and establish a suitable base for administration by employees, vendors, and partners.
3) Increase visibility
Increasing visibility means installing resources to examine user’s activities continuously. Additionally, accumulate and coordinate activity information from numerous sources. Thus, this information would then be fed into other enterprise security solutions to identify and prevent attacks.
4) Protect sensitive properties
To prevent Insider Attacks, it is essential to identify the organisation’s crucial intellectual and physical assets, such as networks, systems, confidential information (consumer data, employee details, plans and strategies) and services. Identifying, prioritising, and determining the state of assets should be done to protect the organisation from any malicious attacks, emphasising the implementation of robust Cyber Security Essentials in safeguarding sensitive information. Emphasising the implementation of robust Cyber Security Essentials in safeguarding sensitive information.
5) Track employ behaviour
Deploying User Behaviour Analytics (UBA) that can track employee activities over the systems can be one of the significant preventive steps. UBA centralises user activity information by analysing control, authentication, account change, endpoint and Virtual Private Network (VPN) logs. Further, it uses this data to frame and assign risk scores to user behaviour linked to malicious events.
Conclusion
Insider Threats are growing fast, which has posed a massive problem for industries across domains. They are especially harmful because they are often confused with normal activities occurring over an organisation's network, thus impacting business operations.
Learn to use different Spyware, Ransomware and Malware and create Cyber Security awareness with our Cyber Security Awareness course. Register now!
Frequently Asked Questions
Upcoming IT Security & Data Protection Resources Batches & Dates
Date
 Certified Cyber Security Professional (CCS-PRO)
Certified Cyber Security Professional (CCS-PRO)
Fri 21st Mar 2025
Fri 23rd May 2025
Fri 22nd Aug 2025
Fri 5th Dec 2025







 Top Rated Course
Top Rated Course




 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


