We may not have the course you’re looking for. If you enquire or give us a call on +61 272026926 and speak to our training experts, we may still be able to help with your training requirements.
We ensure quality, budget-alignment, and timely delivery by our expert instructors.

Ever wonder how investigators obtain secret computer records left behind by cyber criminals? The answer lies in Digital Forensic Tools. Digital Forensic Tools are important components that help in discovering hidden data, recovering critical evidence, and simplifying the complex tasks associated with digital forensic experts. Continue diving into blog to study the top 20 Digital Forensics Tools for pursuing a successful career in the Cyber Security and digital investigations field. Let's begin our journey!
Table of Contents
1) What are Digital Forensics Tools?
2) Top 20 Digital Forensics Tools
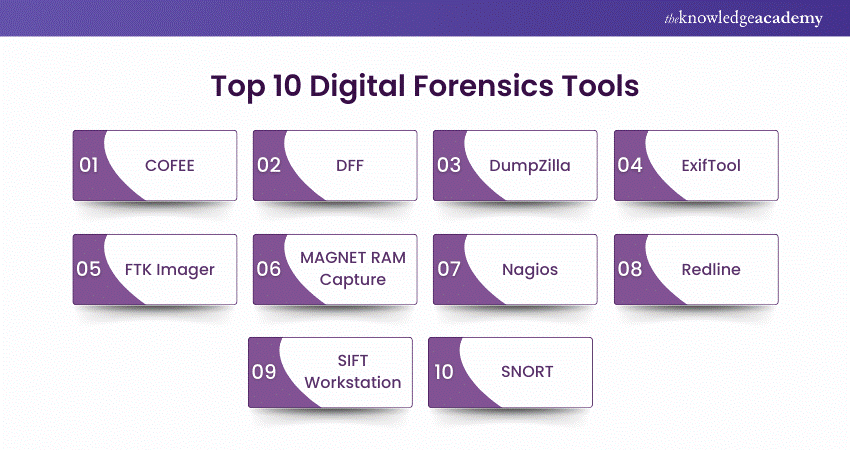
a) COFEE
b) DFF
c) DumpZilla
d) ExifTool
e) FTK Imager
f) MAGNET RAM Capture
g) Nagios
h) Redline
i) SIFT Workstation
j) SNORT
3) Conclusion
What are Digital Forensics Tools?
Digital Forensics Tools are the software (or set of software) and applications implemented by digital forensics experts to gather and analyse evidence alongside information in cybercrime and investigation cases.
It functions by transforming evidence into standard formats, facilitating faster and more seamless analysis. Later, they filter this data to derive valuable insights and conclusions.
Top 20 Digital Forensics Tools
There are plenty of essential Digital Forensics Tools that cater to diverse users’ needs. Below, we have listed some of the most common open-source tools used by Digital Forensics experts worldwide.
1) COFEE
COFEE gathers digital evidence from a suspect’s computer by generating a forensic image of a computer or mobile device's storage. This image allows investigators to access files, emails, and other data without modifying the original system.
2) DFF
DFF analyses and extracts data from file systems and network sources. It works by allowing users to connect to a device and then utilise various plugins to collect and analyse digital evidence.
3) DumpZilla
DumpZilla extracts data from web browsers like Firefox and Chrome by retrieving browsing history, cookies, and passwords.
4) ExifTool
ExifTool reads and writes metadata from various file formats by finding details such as the origin, creation date, and modification file history.
5) FTK Imager
FTK Imager preserves evidence in its original condition and gathers crucial data to generate a forensic picture of a disk. It also simplifies focused data collection and analysis by allowing users to see files and folders before imaging.
Become a specialist in forensic data recovery methods—register for our Computer Forensics Foundation Training!
6) MAGNET RAM Capture
MAGNET RAM Capture captures live memory data (RAM) from a computer by analysing running processes and recovering data that are not stored on the hard drive.
7) Nagios
Nagios monitors network devices, systems, and services by alerting administrators for any kind of suspicious activities. This can be performed by providing real-time insights to administrators about the network health, helping prevent potential breaches before their escalation.
8) Redline
Redline provides capabilities for endpoint analysis by effortlessly collecting comprehensive data to detect malware or unusual activity.
9) SIFT Workstation
SIFT Workstation consists of a suite of open-source forensic tools for investigations. It handles data from multiple storage devices, such as raw disks, Windows, and Linux systems.
10) SNORT
SNORT is a crucial network intrusion detection system that analyses network traffic in real-time to detect any kind of cyber threats activities. Its powerful rule-based engine enables customisable detection of known attacks and anomalies.
11) Tor
Tor provides anonymous browsing capabilities by accessing dark websites without revealing IP addresses or identity. It enhances user privacy through multiple layers of encryption, making tracking nearly impossible.
12) Cellebrite
Cellebrite tool extracts and decodes data from mobile devices by retrieving deleted messages and call logs. It also supports the data extraction from various apps, allowing for comprehensive insights into user activity and communications.
Advance skills in AI-based threat detection with our Certified Artificial Intelligence (AI) For Cyber Security Professionals Training—sign up today!
13) Velociraptor
Velociraptor monitors endpoint, hunting, and digital forensics by investigating suspicious activities across multiple systems.
14) Wireshark
Wireshark captures and analyses network packets by examining detailed contents of network traffic. Its extensive filtering options enable in-depth analysis of specific protocols or traffic patterns.
15) X-Ways Forensics
X-Ways Forensics analyses disk images, processes, and memory seamlessly through data recovery options. It provides a comprehensive suite of tools for both file system analysis and timeline reconstruction.
16) Magnet Axiom
Magnet Axiom extracts and analyses data from digital sources by providing comprehensive case management. It integrates evidence from various sources, facilitating a holistic view of the investigation.
17) The Sleuth Kit
The Sleuth Kit analyses disk images and recovers data through command-line tools applications for file system analysis. Additionally, its modular design allows for the integration of additional tools and scripts to expand its functionality.
18) Autopsy
Autopsy serves as the graphical interface for The Sleuth Kit. It works by simplifying forensic investigations with an easy-to-use interface. The tool also allows investigators to quickly search, filter, and visualise data, thereby, streamlining the analysis process.
Master advanced cybersecurity defense techniques with our Certified Cyber Security Professional (CCS-PRO) Training—register now!
19) Digital Forensics Framework
Digital Forensics Framework manages and analyses digital evidence by helping to extract relevant data from multiple sources. It further provides a modular approach, allowing users to customise their forensic workflows based on the specific investigative needs.
20) Open Computer Forensics Architecture (OCFA)
Open Computer Forensics Architecture (OCFA) processes and analyses digital evidence by integrating various tools to perform forensic analysis automation. Furthermore, its flexible architecture supports the development of plugins development, enhancing its functionality for diverse forensic tasks.
Conclusion
We hope you understand the top 20 Digital Forensic Tools. Digital forensic tools are important software applications that help investigators discover hidden evidence and solve complex cybercrime cases. By gaining Digital Forensic Tools proficiency, you can maximise your ability to analyse data, track digital footprints, and protect against cyber threats.
Become proficient with advanced cyber risk strategies—kickstart your Cyber Security Risk Management Course today!
Frequently Asked Questions

The main problems with digital forensics tools are their limited compatibility with newer technologies and their encrypted data analysis challenges. Additionally, they are costly and have a higher chance of altering evidence during extraction.

Digital forensics tools are validated through a process called tool testing and verification. This includes comparing the tool’s output against known results to ensure optimum accuracy and reliability.

The Knowledge Academy takes global learning to new heights, offering over 30,000 online courses across 490+ locations in 220 countries. This expansive reach ensures accessibility and convenience for learners worldwide.
Alongside our diverse Online Course Catalogue, encompassing 19 major categories, we go the extra mile by providing a plethora of free educational Online Resources like News updates, Blogs, videos, webinars, and interview questions. Tailoring learning experiences further, professionals can maximise value with customisable Course Bundles of TKA.

The Knowledge Academy’s Knowledge Pass, a prepaid voucher, adds another layer of flexibility, allowing course bookings over a 12-month period. Join us on a journey where education knows no bounds.

The Knowledge Academy offers various Cyber Security Training, including the Certified Artificial Intelligence (AI) For Cyber Security Professionals Training, Cyber Security Risk Management Course, and Certified Cyber Security Professional (CCS-PRO) Course. These courses cater to different skill levels, providing comprehensive insights into 5 Best Languages To Learn for Cyber Security.
Our IT Security & Data Protection Blogs cover a range of topics related to cybersecurity threats, data protection strategies, and compliance practices, offering valuable resources, best practices, and industry insights. Whether you are a beginner or looking to advance your cybersecurity and data management skills, The Knowledge Academy's diverse courses and informative blogs have got you covered.
Upcoming IT Security & Data Protection Resources Batches & Dates
Date
 Digital Forensics Training
Digital Forensics Training
Fri 28th Mar 2025
Fri 23rd May 2025
Fri 4th Jul 2025
Fri 5th Sep 2025
Fri 24th Oct 2025







 Top Rated Course
Top Rated Course



 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


