We may not have the course you’re looking for. If you enquire or give us a call on +61 272026926 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.

It is not child’s play to track cyber security attacks taking place every second. It is because cybercrimes can also occur through Social Engineering in Cybersecurity, i.e., manipulating the user to obtain confidential information. Yes, you read it right!
But not many people are aware of this type of crime. It is the reason the global cybercrime rate is expected to go from £2.50 trillion in 2015 to £8.68 trillion by 2025. Since these threats are equally harmful, how can we remain aware of such malicious activities? How can one identify if they are tricked into spilling confidential information? Importantly, what is Social Engineering Cyber Security?
Look no further! In this blog, you will understand what is Social Engineering in Cyber Security and how to save and secure your business.
Learn more about cybersecurity threats and how to mitigate them; register for our Cyber Security Training course now!
Table of Contents
1) What is Social Engineering?
2) How does it work?
3) Different Social Engineering attacks
4) Why are Social Engineering attacks harmful?
5) How to detect and prevent?
6) Conclusion
What is Social Engineering?
Social Engineering in Cybersecurity is more of a vector attack than a cyber security risk. It involves manipulating people into providing usual security codes to gain illegal control of systems, networks, and locations for financial profit. Thus, these crimes are built around users’ psychology and behaviours.
Criminals use this technique to benefit from users’ trust. Scammers typically persuade innocent people to reveal information, spread malware infections, or grant unauthorised access to systems. As soon as the attacker understands the motivations of a user’s actions, they cheat and divert the user’s attention by learning ways to step into their software secretly.
Such attacks can occur online, in person, and through other interactions as well. Moreover, hackers try to exploit users’ lack of knowledge. In simple terms, many users are unaware of certain threats and may not realise the value of personally sensitive information. Therefore, many users might end up giving up information that needs to be protected.
Usually, attackers have the following goals:
a) Corrupting confidential information to cause disturbances
b) Acquiring sensitive data such as personal information, phone numbers, and passwords
How does Social Engineering work?
Imagine an attacker impersonating a bank official sends this message-
Hello! This is XYZ bank, and we need the password to unlock your insurance account.”
User/victim - “Yes, the password is ABC”
Boom! Your money is gone! But it was just a one-time password, right? The bank might need it. However, you have been socially engineered to provide the password to an unknown source.
The human-to-human interaction between attacker and user is all that is needed to gain information. They win the users' trust by compromising their information rather than using violent methods of cyber security breaches. The Social Engineering attack takes place in a vicious cycle that includes the following steps:
1) The first step – Includes collecting background information of the user and tracking their activities over the internet.
2) The second step – Is permeating through developing and initiating relationships with the user to establish trust. For example, a user may regularly get messages to check with their bank.
3) The third step – Is to gain an advantage from the victim to bring out the information.
4) The final step – Is disconnecting the user once the damage is done.
The process may occur through online mediums such as emails, fake websites and links, chats, social media advertisements, or even through word-of-mouth shared with you over a long period.
Different Social Engineering attacks
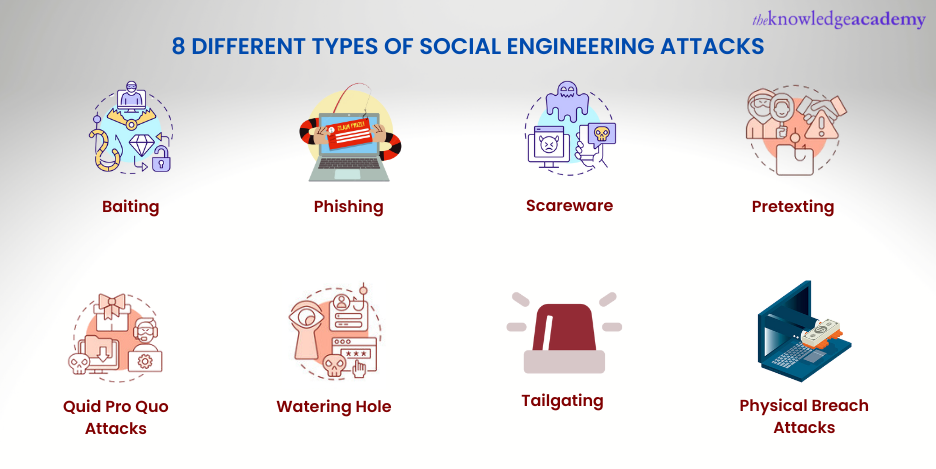
Users are manipulated to share confidential information without any awareness on their part. It is because these cyber security attacks can take place in various unimaginable ways. Let's have a look at them in detail:
Baiting
Baiting means making false promises to trigger the victim's greed or curiosity. The attacker leaves a malware-infected physical device like a USB drive (Universal Serial Bus) or even email attachments for the victim to find. The malware is also installed unknowingly when the curious target inserts it into their system or clicks on the attachment. Thus, the user is hacked.
Phishing
This attack occurs when the scammer disguises themselves as a trusted administrator, organisation or individual. The attacker builds trust by persuading the victim to disclose personal information and other data assets. Phishing is done in two ways:
1) Spam phishing: It means attacking a large group of users all at once. These attacks aren’t target-specific, but they try to catch any innocent person that can fall into the trap.
2) Spear phishing: Unlike spam phishing, it is user-specific to exploit information. These mainly aim at high-value victims like celebrities, upper management and government officials.
It can be initiated through spam calls, texts over phones, placing links to fake websites, and interrupting users during browsing.
Scareware
Scareware involves misleading users with false alarms and malicious threats. Users are deceived into thinking that their system is infected or they have accidentally downloaded an illegal file. It provides a chance for scammers to play a helping hand in providing a solution to fix the problem in the system. Still, in reality, the user is blinded into buying and installing the attacker’s malware, thus giving away their credentials to scammers.
Pretexting
Here, the attacker disguises their personality and lies to gain confidential information from the user. For example, the attacker may ask the user for their business credentials, claiming that some important tasks need to be done. The attacker may pose as an official, co-worker, bank, police or other government body.
Quid pro quo attacks
As the term suggests, it means “a favour for a favour.” The attacker asks the user for a favour against a favour done to them. A bank, for example, may provide you with a waiver on the interest rate if you invest X amount immediately.
Users are lured into exchanging confidential data in exchange for a reward. The excitement to gain the reward exploits users’ valuable data assets. But the attacker simply takes assets without any reward.
Watering hole
Watering hole means finding loopholes and tapping the users into exposing information. In simple terms, the attacker attempts to infect web pages that the user might browse. It is a long process where the attacker tracks user activity over the web and discovers their vulnerabilities, finally watering these sites with malware. Thus, while casually surfing the site, the user is tricked into providing certain information to the attacker. A watering hole attack targets a group of people through host websites rather than targeting them directly.
Tailgating
Tailgating is also known as piggybacking. It occurs when the attacker enters a secured system by following someone with authorised access. The attack takes place on the presumption that the user with access is considerate enough to welcome the attacker with open arms, assuming the attacker is permitted to be there. It may include creating a fake/duplicate identity to look like the organisation’s employees.
Physical breach attacks
As the name suggests, in a “physical breach,” the attacker interacts with the user in person, impersonating someone authoritative to acquire control over their highly personal information. These attacks are common in environments such as governments, businesses, or other organisations.
While attackers may imitate to represent a known and reliable vendor, sometimes they may even be a recently fired employee with a dispute against their former employer. The attacker’s identity is obscure but convincing enough to avoid conflicts. However, it requires a lot of research on the attacker’s part, like, tracking down the company’s activities and monitoring its network. It also includes high-risk.
Why are Social Engineering attacks harmful?
Annually, an organisation is targeted by over 700 Social Engineering attacks, says ZD Net report. These attacks are increasing at a high rate with harmful impacts. They are harmful because:
1) Attacks are target-specific: Scammers seek vulnerable individuals or groups to target and obtain sensitive information.
2) Attackers impersonate themselves as trustworthy: Users may get a call, text, email, advertisement, or a link from attackers disguised as a trustable source. They communicate with the users as an official, notable organisation, bank and government body.
3) Users are manipulated: It is not a one-day process. User activity is traced down for a prolonged period and then taken into the trap. An attacker charms them and even bribes them into providing otherwise inaccessible information.
4) Attackers use multiple ways to obtain data: An increasing use of technology has made not only websites or emails but word-of-mouth methods, social media interactions, unknown links and chats some of the mediums to gain information.
5) Users remain unaware: Attackers breach an organisation’s initial defence to cause further harm. However, the users remain unaware of this activity due to their look-alike nature. Thus, while an attacker might want specific information, they will end up getting more.
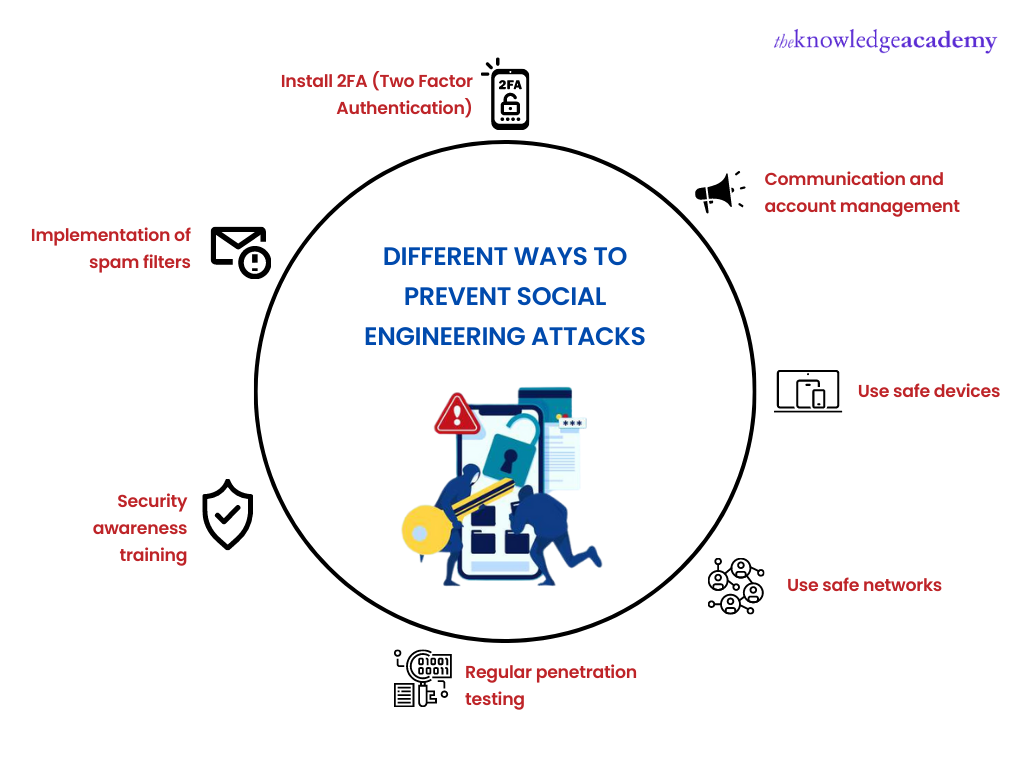
How to detect and prevent?
Now that you have learnt how dangerous Social Engineering attacks can be. It is essential to know about its preventive measures. So, let’s look in detail at how you can detect and prevent yourself from falling into the scammer's trap. First, let’s understand how you can detect these attacks:
Detection techniques
Detecting these attacks is more challenging than it might look. It requires a lot of cyber security awareness on users’ part as these may secretively slide into your system. Thus, to detect such attacks adopt the following techniques:
1) Look for authorised sites, numbers and links: Always verify authorisation if you have been sent a link on a social media application. Even while browsing the web, look for official sites; many duplicate sites make a fool of users.
2) Check for spam: If you find your email and chats filled with (un)known files and attachments from a supposedly legitimate source, you need to become aware.
3) Check up on the rewards they are offering you: If the attacker/sender offers you rewards against the information, look if the offer is practically valid or too good to be true.
5) Verify senders: Sometimes, the attacker may even send you unauthorised links, messages, and files masked as someone you know, co-workers, close friends and relatives.
Preventive measures
After detecting the possible signs of a Social Engineering attack, taking preventive measures to reduce these attacks becomes much more important. Being aware is first and foremost of them all, but here is more on what all you can do:
1) Communication and account management: While communicating online, you may be vulnerable. Social media, email, and text messages are some of the easy and common targets. Therefore, you should:
a) Never click on links in unauthorised emails or messages
b) Use strong passwords and a password manager
c) Resist sharing names of your place and date of birth, phone numbers, or other personal details
d) Be aware while developing online friendships
2) Use safe devices: Devices are continuously in touch with the network vibrations; thus, it is easy for attackers to track your location and phone numbers. Therefore, it is essential to:
a) Use comprehensive internet security software
b) Never leave your devices in unsafe public places
c) Keep all your software updated as soon as the new version is available
d) Check for familiar data breaches of online accounts
3) Use safe networks: Careless networking can also result in attacks. Following are some protective measures you need to take:
a) Never connect to Unkown or public Wi-Fi networks. Also, do not let unknown users connect to your network at home, workplace and public places
b) Use a VPN (Virtual Private Network), which includes an encrypted tunnel on any internet connection you use
c) Keep all network-connected devices and services secure
4) Regular penetration testing of your system: This can help you learn which user can pose a threat.
5) Security awareness training: It should be the utmost priority to encourage people to prevent Social Engineering.
6) Implementation of spam filters: It helps determine potential spam emails. Installing applications to recognise spam calls can also be a great idea.
7) Install 2FA (Two Factor Authentication): To access important accounts, i.e., a confirmation code via text message or voice recognition.
Conclusion
Social Engineering in Cybersecurity is increasing at a faster pace. Attackers and scammers use look-alike techniques to tempt users and win their trust to get crucial, confidential information that is otherwise difficult to obtain. It is essential to understand the method of these attacks and mitigate them using various preventive methods.
Become aware of the various threats surrounding your network; join our Cyber Security Awareness course now!
Frequently Asked Questions
Upcoming IT Security & Data Protection Resources Batches & Dates
Date
 Certified Cyber Security Professional (CCS-PRO)
Certified Cyber Security Professional (CCS-PRO)
Fri 17th Jan 2025
Fri 7th Mar 2025
Fri 23rd May 2025
Fri 18th Jul 2025
Fri 12th Sep 2025
Fri 14th Nov 2025
Fri 12th Dec 2025







 Top Rated Course
Top Rated Course



 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


