We may not have the course you’re looking for. If you enquire or give us a call on +32 35001305 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.

Today, technology has surrounded us from all sides. Every single minute of our lives is invested in technology in one way or the other, gathering tons of information.
The introduction of technologies such as Artificial Intelligence (AI) and the Internet Of Things (IoT) have benefited businesses extensively. But with benefits also comes the implied risks from malicious attacks to the data generated over the web. It's crucial for businesses to prioritize cyber security for business to safeguard sensitive information in this technology-driven era.
According to McKinsey & Company, the harm from cyberattacks will be worth £8.73 trillion by 2025 if it continues at the current annual growth rate. Thus, it is essential to use Cybersecurity to eliminate the risk of external interventions and strategise Cyber Security challenges.
But what is Framework in Cyber Security? How can it help in protecting against malware attacks? What are some Frameworks that can be used to avoid cyber-attacks? Check out this blog to know the list of the top 25 Cyber Security Frameworks.
Table of Contents
1) What is Cyber Security Framework?
2) What are the different Cyber security Frameworks
a) Control Objectives for Information Technology (COBIT)
b) Cybersecurity and Infrastructure Security Agency (CISA) Transportation Systems Sector (TSS)
c) International Office of Standardisation (ISO) 27001
d) National Cyber Security Centre (NCSC) Cyber Assessment Framework (CAF)
e) MITRE ATT&CK
3) Conclusion
If you want to learn and build a career in Cybersecurity, join our Cyber Security Training course now and get placed at top tech companies.
What is Cyber Security Framework?
Most companies today emphasise developing concrete solutions for cyber-attacks across their systems, networks, software and devices. A Framework in Cyber Security provides plans and strategies for determining and building risk resistance by setting Cyber Security controls to increase the effectiveness of security measures.
Therefore, adopting different strategies to protect organisations from estimated risks and attacks is essential. However, there is no standardised platform to ensure Cyber Security; many alternatives exist.
What are the different Cyber Security Frameworks
There is just not one, but a long List of Cybersecurity Frameworks used worldwide. So, let's look at the different types of these:
Control Objectives for Information Technology (COBIT)
COBIT is a well-established Framework developed by Information Systems Audit and Control Association (ISACA) about 25 years ago and was updated in 2019. This useful public resource extends to almost all-important aspects required for effective IT management.
COBIT is designed to assign administrative responsibilities by understanding the organisation's strategy and requirements and effectively managing and using the technologies. It promotes the scope to create security Frameworks that simplify inspections and provides improved results.
Cybersecurity and Infrastructure Security Agency (CISA) Transportation Systems Sector (TSS)
The Department of Transportation, Transportation Security Administration, United States Coast Guard, and Transportation Systems Sector created a method to fulfil industry-specific requirements – the National Institute of Standards and Technology (NIST).
It provides five distinct TSS strategy objectives:
1) Define conceptual environment
2) Maintain continuous Cyber Security Awareness
3) Improve and extend voluntary contribution
4) Improve intelligence and security information distribution
5) Ensure prolonged coordination and strategic execution
It adopts a risk-based and security maturity approach allowing organisations to apply threat intelligence to evaluate breach impact. Thus, it streamlines these goals to relevant NIST categories.
International Office of Standardisation (ISO) 27001
One of the most reliable and oldest standards for enterprises and customers is the ISO/IEC family. The ISO is a non-governmental organisation founded in 1947 with 165 member countries. It sets standards for dozens of Frameworks but has its foundation for initiating an Information Security Management System (ISMS).
ISO 27001 includes implementing, executing, and maintaining. It also focuses on regularly enhancing an ISMS varying according to the organisation's requirements, goals, security needs, management size and structure.
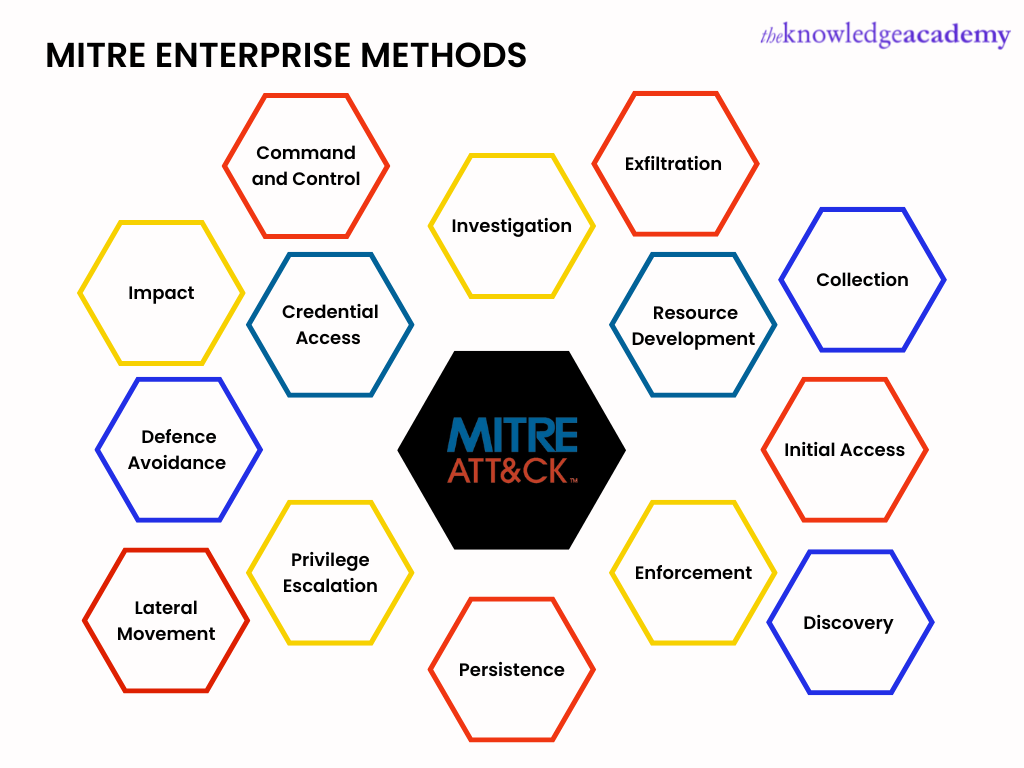
MITRE ATT&CK
MITRE ATT&CK is a non-profit, federally regulated, knowledge-based security centre. It is more research-oriented than a set method.
While ATT&CK is the baseline serving as a common language for hostile as well as defensive researchers, MITRE documents the general cyberattack methods, techniques and processes that are used against Windows-based business networks.
MITRE enterprise has 14 methods used when attackers set up advanced inevitable threats within a business. These are as follows:
1) Investigation
2) Resource development
3) Initial access
4) Enforcement
5) Persistence
6) Privilege escalation
7) Defence avoidance
8) Credential access
9) Discovery
10) Lateral movement
11) Collection
12) Command and control
13) Exfiltration
14) Impact
National Cyber Security Centre (NCSC) Cyber Assessment Framework (CAF)
The United Kingdom's National Cyber Security Centre (NCSC) introduced its Cybersecurity Assessment Framework (CAF) in 2016. It was launched to bring Small and Medium Sized Enterprises (SMEs), enterprise organisations, government agencies, and public departments together to look into cybersecurity concerns.
CAF provides direction for UK's Critical National Infrastructure (CNI) to handle cyber-related threats to public safety. Therefore, CAF's primary goal is to manage risks, protect against cyber-attacks, identify cyber-security phenomena, and finally minimise the influence of these phenomena.
Australian Signals Directorate (ASD) Essential 8
Australian Signal Directorate (ASD) Essential 8 helps manage cybersecurity attacks using three levels. It adopts a maturity model strategy for security that includes eight aspects. These are:
1) Setting and implementing applications control
2) Bridging the gap in applications
3) Constructing Microsoft Office Macro settings
4) Strengthening user applications
5) Controlling governance privileges
6) Fixing operating systems
7) Using multifaceted authentication
8) Ensuring regular backups
Within those eight strategies, each maturity level has particular control. Each level implies that:
1) The organisation is partially aligned.
2) The organisation must put additional controls in place to be fairly aligned.
3) The organisation has executed all necessary controls and is fully aligned.
Center for Internet Security (CIS) Controls
Most professionals use Centre for Internet Security (CIS) Controls. It has a more authoritarian approach (rather than flexible) towards cybersecurity. CIS Control lists 20 business-critical controls across three categories. These categories are as follows:
1) Basic
2) Foundational
3) Organisational
Further, CIS Controls categorises three implementation groups. These groups are divided based on the expertise of implementation. Group one is for organisations with a short supply of resources and cybersecurity expertise. Group two has modest resources and cyber security expertise. On the other hand, group three is for flourishing organisations with extensive resources and expertise.
Cloud Security Alliance (CSA) Cloud Controls Matrix (CCM)
The CMM exclusively focuses on cloud computing. This Framework in Cyber Security comprises 197 directive objectives in 17 areas. These are as follows:
1) Audit and assurance
2) Application and interface security
3) Business regulation management and operational flexibility
4) Change control and structure management
5) Cryptography, encryption and key management
6) Datacentre security
7) Data security and privacy lifecycle management
8) Administration, threat management and compliance
9) Human resources
10) Identity and access management
11) Interactivity and ease of use
12) Infrastructure and virtualisation security
13) Logging and observing
14) Security incident management, e-discovery, and cloud forensics
15) Supply chain management, transparency and liability
16) Risk and sensitivity management
17) Universal endpoint management
Thus, CCM recognises controls and references to help organisations develop a cooperative security program within each area.
Understand about cyber-attacks execution in today’s world; register for our Cyber Security Risk Management course today!
Cybersecurity Maturity Model Certification (CMMC)
The CMMC to standardise cybersecurity in the Defence Industrial Base (DIB) by The Office of the Under Secretary of Defence Acquisition and Sustainment (OUSD(A&S)) with Department of Defence (DoD) stakeholder, University Affiliated Research Centers (UARCs), and Federally Funded Research and Development Centers (FFRDC).
CMMC includes documentation for organisations that seek DoD contracts and practices. It provides five maturity levels based on whether the data that an organisation gathers, circulates, reserves, and processes is Federal Contract Information (FCI). The five levels of certifications are as follows:
1) Fundamental protection of FCI and fundamental cyber hygiene.
2) Listing and processing the progression phase to demonstrate intermediate cyber hygiene practises for FCI and CUI.
3) Implementing fundamental CUI protections, organisational processes, and creating successful cyber hygiene operations.
4) Increasing security over CUI, minimising advanced persistence threat (APT) risks, revaluating processes, and establishing dynamic operations.
5) Stimulating threat mitigation around APTs, enhancing processes, and implementing advanced, growing operations.
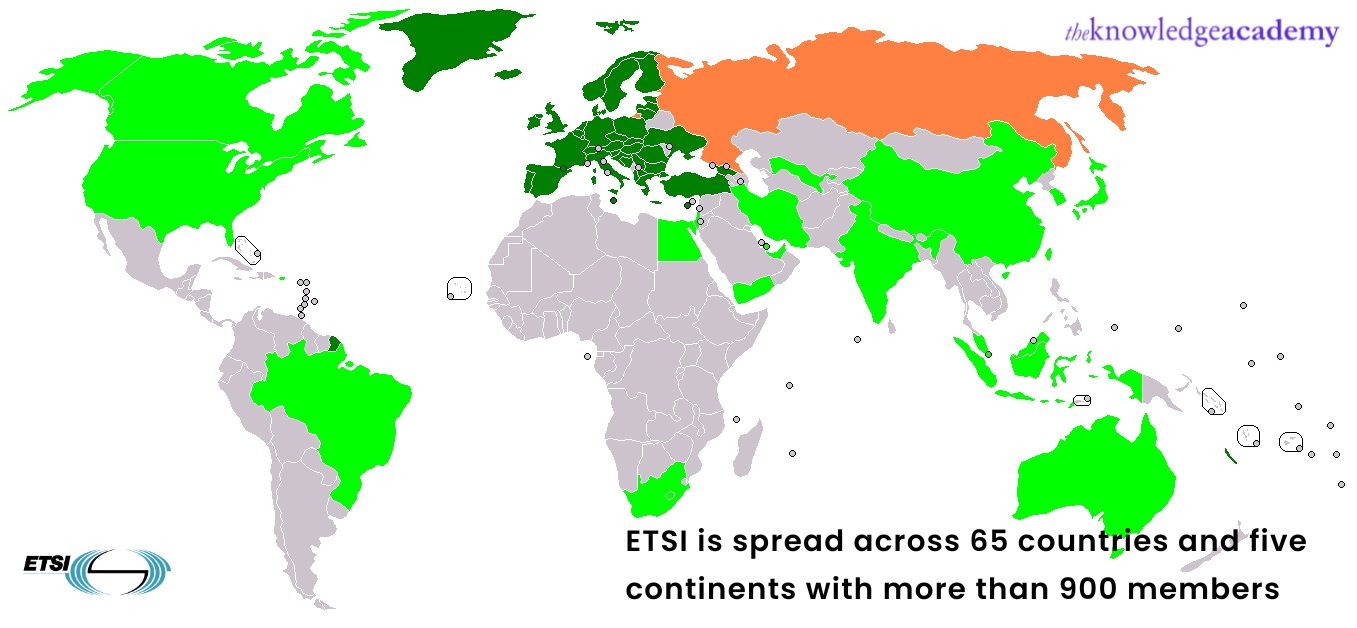
European Telecommunications Standard Institute (ETSI)
The European Telecommunications Standardised Institue (ETSI) spreads across 65 countries and five continents with more than 900 members in total. It is a non-profit standard organisation that supports European laws and jurisdiction by developing standards used in European Union.
ETSI divides enterprise into Implementation Groups. It consists of the following:
1) Control name
2) Explanation of control uncertainties
3) Table with detailed control descriptions
4) Procedures and tools
5) System entity relationship diagram
European Union Agency for Cybersecurity (ENISA) national capabilities assessment Framework
ENISA provides its member states a way to participate in self-assessments to recognise their maturity level. This was published recently in 2020 and proposes countries assess their cybersecurity capabilities by providing guidelines for building national-level techniques.
It provides several benefits to the countries that engage in its use. Some of the benefits are as follows:
1) Identifies fractures in cybersecurity programs and enhances their capabilities.
2) It supports political accountability
3) Establishes public and international integrity
4) Recognises past mistakes and adopt best practices
5) Provides a cybersecurity baseline across the EU
6) Analyse national cybersecurity capabilities
Factor Analysis of Information Risk (FAIR) cyber risk Framework
FAIR is an institute that was established for risk experts to collaborate better with their businesses to implement and boost threat management practices. Its cyber risk Framework opts for a comprehensive approach to Cyber Security Risk Management. Thus, it allows organisations to quantify threats regardless of the cybersecurity strategy they use. FAIR uses a comprehensive approach that includes the following:
1) Compliance needs
2) Alignment controls
3) Creation of responsive risk postures
4) Meanwhile, creating a cycle of constant advancements inclusive of risk targets, controls and responsive threat postures
HITRUST Cybersecurity Framework (CSF)
HITRUST provides a consolidated risk and compliance approach to help healthcare enterprises and business associates find a more resilient method to meet the Health Insurance Portability and Accountability Act (HIPPA).
It comprises 49 control objectives across 156 control hierarchies, all of which fall into 14 control classes. These 14 classes are:
1) Information security management program
2) Access control
3) Human resources security
4) Risk management
5) Security policy
6) The organisation of information security
7) Compliance
8) Asset management
9) Physical and environmental security
10) Communications and operations management
11) Information systems acquisition, development, and maintenance
12) Information security incident management
13) Business continuity management
14) Privacy practises
Information Security Forum (ISF) Standard of Good Practice for Information Security (SOGP 2020)
Companies on Fortune 500 and Forbes 2000 lists are members of ISF. It is another non-profit organisation focusing on creating a knowledge exchange where member companies share security issues, experiences and practical solutions.
Its main objectives include enhancing adaptability, providing a base for information risk evaluation, verifying information security across the supply chain, supporting compliance with crucial business standards, and forming a basis for plans, standards, and processes.
International Society of Automation (ISA/IEC 62443)
ISA is a non-profit professional organisation formed in 1945. It instituted a Global Security Alliance (GSA) to work with manufacturers and crucial infrastructure providers. GSA integrates numerous stakeholders such as end-user businesses, automation and control systems providers, IT infrastructure providers, services providers, and system integrators. It is an industrial security strategy with both traditional IT environments and plant floor environments.
International Telecommunications Union (ITU) National Cybersecurity/ Critical Information Infrastructure Protection (CIIP)
CIIP is a model for governments, businesses, and other public and private organisations to share responsibilities for national security, economic prosperity and brotherhood. ITU created it to identify the importance of Information and Communication Technologies (ICTs). CIIP has some key elements that are a must for national cybersecurity strategy:
1) Government/Private Sector collaboration
2) Incident management capabilities
3) Legal infrastructure
4) Culture of cybersecurity including plans, national awareness, outreach, improved research and recognising training needs.
Internet of Things (IoT) Cybersecurity Alliance (IoTCA)
The IoTCA was established to bring cybersecurity and IoT experts together to create a community that can look into real-world IoT security issues and develop a protective IoT conduct.
It takes a layered approach to develop end-to-end security considering all connected devices and their linked applications. It includes:
1) Endpoint layer: devices/connected objects, short-range networks
2) Network layer: communications network
3) Data/App layer: applications
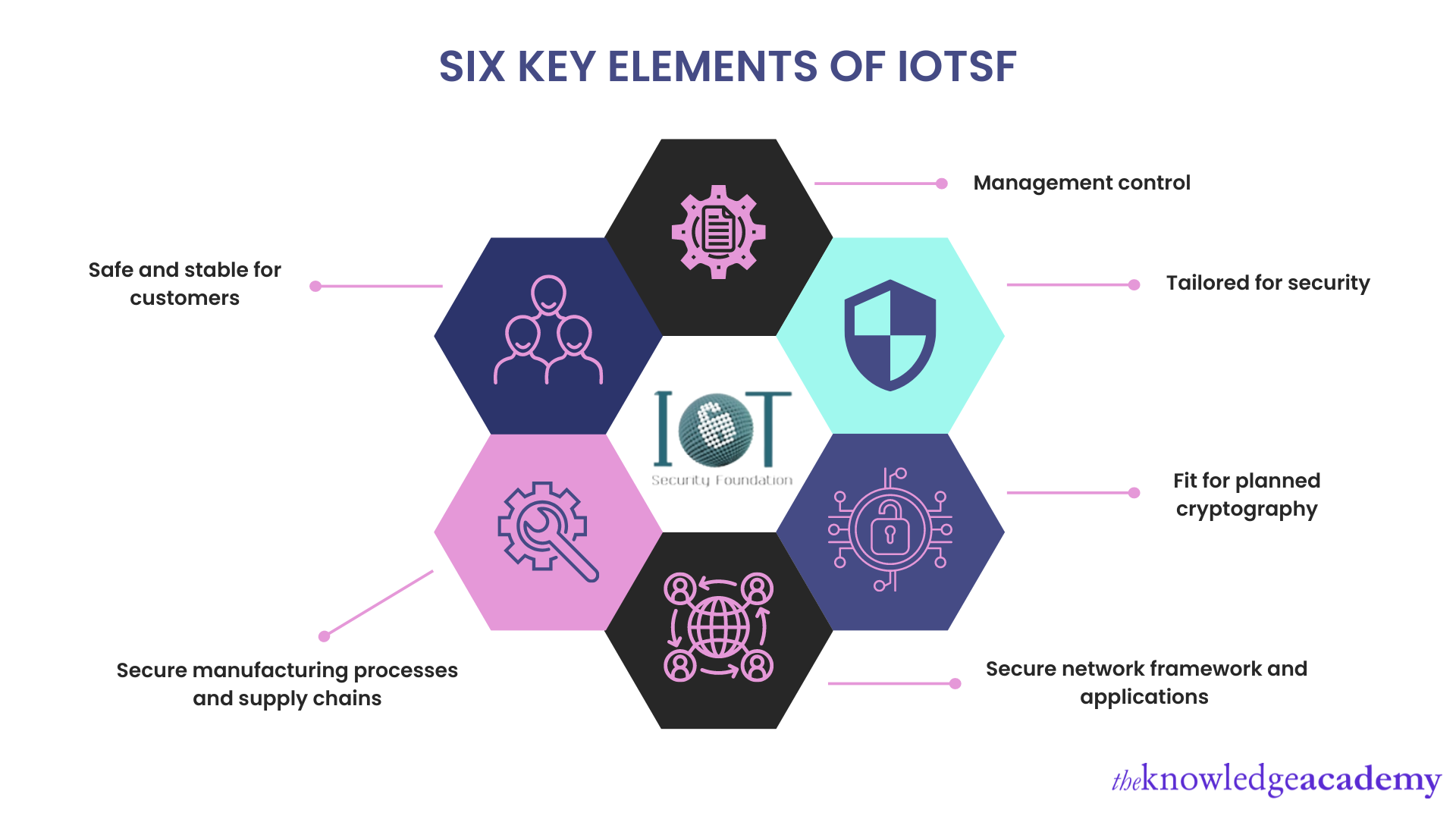
Internet of Things (IoT) Security Foundation (IoTSF) security compliance Framework
IoT security professionals, IoT hardware and software product vendors, network providers, system specifiers, local officials, and government bodies can work together using IoTSF Compliance Frameworks.
It is a non-profit organisation designed to focus on protecting IoT during its design phase to alleviate financial and brand goodwill risks using a risk-based approach. It has the following six key elements:
1) Management control
2) Tailored for security
3) Fit for planned cryptography
4) Secure network Framework and applications
5) Secure manufacturing processes and supply chains
6) Safe and stable for customers
New Zealand Protective Security Requirements (PSR)
It is one of the organisations that develops a policy Frameworks for enterprises. It defines how organisations should manage security administration (GOVSEC), personnel (PERSEC), information (INFOSEC), and physical security (PHYSEC) across various public and private sectors.
It has a four-layered hierarchical structure which recommends the organisations to:
1) Implement a planned security law
2) Set vital policies and necessary requirements
3) Follow protocols and best-practice directions
4) Establish and reconsider management strategies and processes
If you want to learn how to prevent cyber threats; register for our Cyber Security Awareness course now!
National Institute of Technologies (NIST) Cybersecurity Framework (CSF)
NIST is a US-based non-organisational government agency. It sets standards across physical sciences. Companies outside the critical infrastructure industry also use CSF to meet other US federal data protection needs. It consists of the following:
1) Core
2) Implementation Tiers
3) Profiles
NIST Special Publication (SP) 800-82 guide to Industrial Control Systems (ICS) Security
NIST SP 800-82 offers guidelines for Supervisory Control and Data Acquisition (SCADA) systems, distributed control systems (IDS) and other control system infrastructures found in the industrial control sectors. It particularly addresses the unique cybersecurity concerns facing Industrial Control Systems (ICS).
North American Electric Reliability Corporation (NERC)
NERC focuses on successfully and coherently reducing risks facing the grid system. It is a non-profit international organisation whose command lies with power system users, owners and operators. Currently, it has 19 approved security guidelines across these areas. Some of them are as follows:
1) Cloud computing
2) Control systems electronic connectivity
3) Cloud solutions and encrypting
4) Open-source software
5) Across the source
6) Risk management lifecycle
7) Physical security
8) Physical security response
9) Secure delivery of applications
10) Vendor incident rebound
11) Vendor risk management lifecycle
OASIS Security Assertion Markup Language (SAML)
While OASIS is a community where professionals advance projects such as open-source projects, cybersecurity, Blockchain, IoT, disaster management, cloud computing and legal data exchange, etc. On the other hand, SAML was developed by the Security Services Technical Committee that is an XML-based structure.
SAML is a standard to define Frameworks that supports communication among businesses against security information exchange between business partners. It has four main units to it, they are:
1) Assertions
2) Protocols
3) Bindings
4) Profiles
Payment Card Industry Data Security Standard (PCI DSS)
The Payment Card Industry Security Standards Council (PCI SSC) created PCI DSS in 2006. It was established in response to increased credit card frauds. It prescribes security compliance demands for sellers and commercial service providers. PCI DSS has five groups of controls:
1) Develop and regulate safe network and systems
2) Safeguard cardholder's data
3) Provide a sensitivity management program
4) Establish extensive access administrative measures
5) Constantly observe and assess networks
6) Maintain an information security policy
Saudi Arabian Monetary Authority (SAMA) cybersecurity Framework
SAMA's cybersecurity Framework was introduced in 2017 in response to increasing online services and new developments, like Blockchain. SAMA's main objective is to encourage regulatory standards was guard against constantly increasing threats. Further, the SAMA CSF categorises its scope in the following ways:
1) Electronic information
2) Physical information (hardcopy)
3) Applications, software, electronic services, and databases
4) Computers and electronic machines (e.g., ATMs)
5) Information storage devices (e.g., hard disk, USB stick)
6) Premises, equipment, and communication networks (technical infrastructure)
Conclusion
Various organisations set up to provide Cyber Security Frameworks to get rid of many possible malware attacks. We hope that through this blog, you can learn about various cybersecurity Frameworks and their use across industries.
If you are interested in learning to solve key distribution issues with asymmetric encryption; register for our Introduction To System And Network Security course now!
Frequently Asked Questions
Upcoming IT Security & Data Protection Resources Batches & Dates
Date
 Certified Cyber Security Professional (CCS-PRO)
Certified Cyber Security Professional (CCS-PRO)
Thu 1st Jan 1970







 Top Rated Course
Top Rated Course




 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


