We may not have the course you’re looking for. If you enquire or give us a call on 01344203999 and speak to our training experts, we may still be able to help with your training requirements.
We ensure quality, budget-alignment, and timely delivery by our expert instructors.

Wondering What is a Computer Worm? It is a type of malware that spreads on its own without needing any human help. It moves from one computer to another, often through networks, emails, or security flaws. Unlike viruses, worms don’t need to attach to files or programs to spread.
These worms can spread quickly and cause serious damage, such as slowing down networks, stealing data, or even crashing systems. Since they work silently in the background, they can go unnoticed for a long time.
Want to know more? Read this blog to learn about What is a Computer Worm, how it spreads, and the warning signs of an infection. Learn how these threats work and how to protect your devices. Let’s get started!
Table of Contents
1) What is a Computer Worm?
2) How does a Computer Worm Spread?
3) Types of Computer Worm
4) What's the Difference Between a Worm and a Virus?
5) Computer Worm Examples
6) How to Remove a Computer Worm?
7) How to Prevent Computer Worm Infections?
8) What are the Symptoms of a Computer Worm?
9) Can a Firewall Stop Computer Worms?
10) Conclusion
What is a Computer Worm?
A Computer Worm is a type of malware that spreads by copying itself and infecting other computers. It stays active on infected systems and spreads without needing user action. Worms often take advantage of hidden parts of an operating system to move between devices.
Since they work in the background, most users don’t notice them until their computer slows down or stops working properly. Unlike a virus, a worm doesn’t need to attach to a file—it spreads on its own. Also, don’t confuse it with WORM (Write Once, Read Many), which is something completely different!
How Does a Computer Worm Spread?
A Computer Worm spreads by copying itself and moving from one device to another, often without any user action. It travels through networks, emails, or infected software, looking for vulnerabilities to exploit. Worms can spread in several ways:
1) Networks – They move between connected devices by exploiting security gaps.
2) Emails – Some worms hide in email attachments or links, infecting a system when opened.
3) USB Drives – Plugging in an infected USB can allow the worm to copy itself onto a new computer.
4) Software Vulnerabilities – Outdated programs or operating systems provide an easy entry point.
Sign up for our comprehensive Cyber Security Risk Management Training and empower yourself with the knowledge to safeguard your digital assets.
Types of Computer Worm
There are several types of adversarial Computer Worms; the following are some of the important types of Computer Worms:
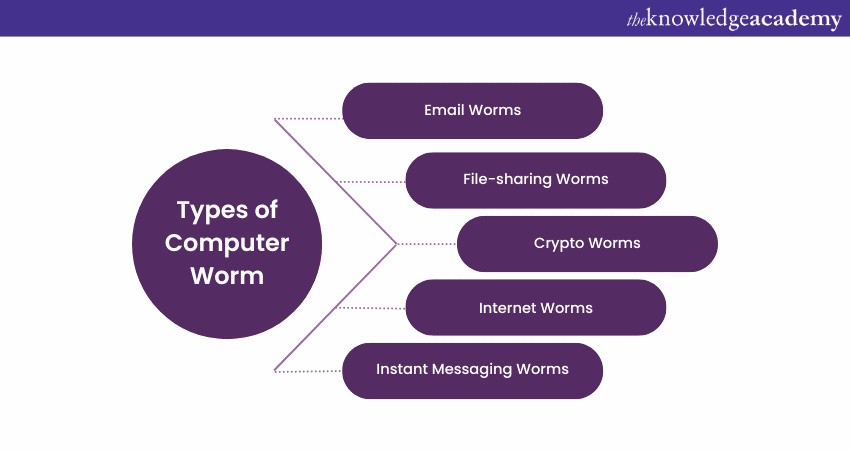
1) Email Worms
Email worms replicate themselves by generating new messages and sending them to all the addresses stored in a user's contact list. Successful email worms often use social engineering and phishing methods to entice users to click the attached file. The emails include a malicious executable file that infects the new machine when the receiver downloads the attachment.
2) File-sharing Worms
File-sharing worms spread by copying themselves into shared folders and moving through peer-to-peer networks. Cybercriminals often disguise these worms as media files, tricking users into downloading them.
One of the most infamous worms, Stuxnet, had two main components. The first was a worm that propagated malware through infected USB drives, while the second specifically targeted Supervisory Control and Data Acquisition (SCADA) Systems. This made Stuxnet particularly hazardous, as it disrupted industrial operations. To understand more about SCADA-related threats and security measures, explore our SCADA Interview Questions.
Worms like this show how harmful self-replicating malware can be. Staying cautious while downloading files and avoiding unknown USB devices can help prevent infections.
Join our Computer Forensics Foundation Training and master the art of digital investigation – sign up now!
3) Crypto Worms
A crypto worm is a type of malware that targets a computer system and encrypts the data, making it inaccessible to the user. Hackers often use This type of worm in ransomware attacks, where they seize control of the victim's information and demand payment in exchange for a decryption key that can open the files. These episodes can have excruciating consequences for individuals and organisations, resulting in critical data loss and significant financial costs.
4) Internet Worms
A particular category of Computer Worms has the specific purpose of targeting widely used websites with weak Cyber Security measures. The ultimate goal of these worms is to infiltrate the website's system, which then allows them to spread to any computer that has accessed the site and infect them as well.
5) Instant Messaging Worms
Like email worms, Instant Messaging (IM) worms conceal themselves within attachments or links. Once opened, the worm will spread to the contacts within the infected person's list. The main distinction is that instead of email, it enters through an instant message on a chat platform.
What's the Difference Between a Worm and a Virus?
Here are five key differences between a Computer Worm and a virus:
a) Propagation: A Computer Worm can spread independently and self-replicate without human intervention. In contrast, a virus requires human action to spread, such as opening an infected file.
b) Host Dependency: Viruses need a host file or program to attach themselves to and remain dormant until triggered. Worms do not require a host and are stand-alone malicious programs.
c) Objective: While both can cause damage, worms primarily aim to consume system resources and slow down the system, whereas viruses tend to modify or delete data.
d) Control: Worms can sometimes be controlled remotely, but viruses cannot be controlled once they have infected a system.
e) Detection and Protection: Both worms and viruses can be detected and removed by antivirus software. However, worms can also be blocked by firewalls due to their network-based nature of spreading.
Computer Worm Examples
The history of Computer Worms dates back over fifty years, with the inaugural worm, Creeper, emerging in 1971. Although not designed to be harmful, Creeper set the stage for subsequent impactful attacks. Here’s a refined overview of some notable worms:
a) Morris (1988)
Created by Robert Morris, this worm unintentionally overloaded 6,000 UNIplexed Information Computing System (UNIX), leading to crashes and damages worth £78,826.50 to £78,82,650.00 million.
b) SQL Slammer (2003)
This worm caused widespread internet disruption and router crashes globally, infecting 75,000 victims within minutes.
c) Mydoom (2004)
Targeting Windows systems, Mydoom became one of the fastest-spreading worms, causing an estimated $38 billion in damages. It persists, accounting for a significant portion of malicious emails.
c) Storm Worm (2007)
Utilising a catastrophic European storm as a lure, the Storm Worm infected millions of computers through deceptive emails.
e) Duqu (2011)
A sophisticated worm, Duqu is believed to be related to Stuxnet, which disrupted Iranian nuclear facilities. It gathers intelligence potentially useful for attacking industrial controls.
f) ILOVEYOU (2000)
Masquerading as a love letter, this worm rapidly infected over 50 million PCs, accruing a removal cost of approximately £1,18,23,900.00 billion.
Advance your career with our Digital Forensics Training – register today and dive into comprehensive modules and practical exercises.
How to Remove a Computer Worm?
Getting rid of a Computer Worm requires a careful approach to make sure it’s fully removed from your system. Follow these steps to eliminate the threat and keep your device safe.
a) Disconnect from the Internet
First, unplug your computer from the internet and any network connections. This prevents the worm from spreading to other devices or communicating with hackers.
b) Run an Antivirus Scan
Use updated antivirus software to scan your system. Let it check all files, folders, and system areas where the worm might be hiding. Antivirus tools are designed to detect and remove harmful code.
c) Remove or Quarantine Infected Files
Once the scan is complete, review the results. Delete or quarantine any files flagged as infected. Follow the antivirus software’s instructions to ensure the worm is fully removed.
d) Use an Anti-Malware Tool
For extra security, run a second scan using an anti-malware tool. This helps catch any leftover threats that the antivirus software might have missed.
e) Manually Check for Issues
If the worm is stubborn, a manual check may be needed:
a) Startup Programs & Registry – Look for suspicious entries and remove them.
b) System Files – Check important system folders for unusual files or changes.
f) Update Your System
Make sure your operating system, software, and security tools are up to date. Installing the latest updates helps protect against security flaws that worms and other malware might exploit.
By following these steps, you can remove a worm and strengthen your system against future attacks!
How to Prevent Computer Worm Infections?
Keeping your system safe from Computer Worms requires proactive steps to block potential threats. Here’s how you can protect your device from these harmful infections.

a) Use Antivirus Software
A good antivirus program is your first line of defence against worms and other malware. Choose a trusted software and keep it updated regularly. Set it to run automatic scans to catch threats before they cause damage.
b) Keep Your System Updated
Make sure your operating system and software have the latest updates and security patches. Companies release updates to fix weaknesses that hackers might exploit. Turn on automatic updates for added security.
c) Enable a Firewall
Firewalls help protect your system by blocking unauthorised access. They act as a security barrier, monitoring internet traffic and preventing worms from spreading. Ensure your computer’s built-in firewall is active.
d) Be Careful with Emails and Downloads
Worms are often spread through email attachments and downloads. Avoid opening attachments from unknown senders and only download files from trusted websites. If something looks suspicious, don’t click on it!
e) Use Secure Browser and Network Settings
Enhance your safety by enabling pop-up blockers, phishing filters, and safe browsing features in your web browser. These tools help prevent accidental downloads of harmful software.
f) Educate Yourself and Others
Understanding how worms spread is key to preventing infections. Learn to recognise phishing emails, suspicious links, and malware signs. Use strong passwords and back up important files regularly.
g) Monitor Your System
Watch for unusual system activity, like slow performance, high network traffic, or unauthorised access attempts. Using Intrusion Detection Systems (IDS) or Prevention Systems (IPS) can help spot threats early.
By following these steps, you can reduce the risk of Computer Worm infections and keep your system safe!
What are the Symptoms of a Computer Worm?
A Computer Worm can slow down your system, cause frequent crashes, or display strange error messages. You may notice high network activity, missing files, or unknown programs appearing. Your device might act strangely or send messages without your knowledge. If you see these signs, run an antivirus scan immediately.
Can a Firewall Stop Computer Worms?
Yes, a firewall helps block Computer Worms by controlling network traffic and stopping unauthorised access. It prevents worms from spreading, but it’s not foolproof. Using antivirus software, regular updates, and safe browsing habits is essential for full protection. A firewall is a strong defence, but it works best with other security measures.
Conclusion
We hope you have read and understood What is a Computer Worm. They are rather sophisticated entities capable of causing widespread disruption. Awareness and vigilance are the best allies in combating these silent invaders. informed, stay secure, and ensure that the cyber environments remain resilient against the relentless tide of these worms. For a deeper understanding of cybersecurity threats and defenses, explore Cyber Security MCQs With Answers, which can help reinforce your knowledge and preparedness.
Master the techniques to thwart Cyber-attacks with our Malware Analysis Training – secure your spot now!
Frequently Asked Questions
Do Computer Worms Still Exist?

Yes, Computer Worms still exist and remain a serious threat. While cybersecurity has improved, hackers continue to create new worms that exploit system vulnerabilities. They spread through networks, emails, and USB drives, causing data breaches and system slowdowns. Staying updated and using security tools helps prevent infections.
Are Computer Worms Harmful?

Yes, Computer Worms can be very harmful. They spread quickly, consuming system resources and slowing down devices. Some worms steal sensitive data, disrupt networks, or install other malware. Others create security gaps that hackers can exploit. Preventing worms with strong cybersecurity measures is crucial to keeping your system safe.
What are the Other Resources and Offers Provided by The Knowledge Academy?

The Knowledge Academy takes global learning to new heights, offering over 3,000 online courses across 490+ locations in 190+ countries. This expansive reach ensures accessibility and convenience for learners worldwide.
Alongside our diverse Online Course Catalogue, encompassing 19 major categories, we go the extra mile by providing a plethora of free educational Online Resources like News updates, Blogs, videos, webinars, and interview questions. Tailoring learning experiences further, professionals can maximise value with customisable Course Bundles of TKA.
What is The Knowledge Pass, and How Does it Work?

The Knowledge Academy’s Knowledge Pass, a prepaid voucher, adds another layer of flexibility, allowing course bookings over a 12-month period. Join us on a journey where education knows no bounds.
What are the Related Courses and Blogs Provided by The Knowledge Academy?

The Knowledge Academy offers various Cyber Security Trainings, including the Cyber Security Awareness Course, Cyber Security Risk Management Course, and Social Engineering Training. These courses cater to different skill levels, providing comprehensive insights into Internet Security.
Our IT Security & Data Protection Blogs cover a range of topics related to Computer Worms, offering valuable resources, best practices, and industry insights. Whether you are a beginner or looking to advance your IT Security & Data Protection skills, The Knowledge Academy's diverse courses and informative blogs have got you covered.
Upcoming IT Security & Data Protection Resources Batches & Dates
Date
 Certified Cyber Security Professional (CCS-PRO)
Certified Cyber Security Professional (CCS-PRO)
Fri 23rd May 2025
Fri 22nd Aug 2025
Fri 5th Dec 2025






 Top Rated Course
Top Rated Course



 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


