We may not have the course you’re looking for. If you enquire or give us a call on 01344203999 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.

Data is the new oil and holds great value for individuals and businesses. Securing data has become essential for companies, as they spend a significant amount safeguarding their systems and networks to protect the data. As online threats are increasing rapidly, the role of Cyber Security Essentials is also becoming crucial. Data thefts are causing damages to companies in the millions and are negatively affecting their performance and profitability. According to PwC's 2022 Global Digital Trust Insights, 66% of businesses expect their Cyber Security budget to increase to double-digits.
Cyber Security Audits are a comprehensive review and assessment of a company's IT infrastructure. It is a process that helps businesses identify risks and vulnerabilities in IT systems and networks. Undertaking this process exposes the firm's weaknesses and allows the management to determine the proper high-risk practices.
This blog describes Cyber Security Audit and how it is essential for companies.
Table of contents:
1) What is Auditing in Cyber Security?
2) Types of Cyber Security Audit
3) Importance of Cyber Security Audit
4) When is Auditing needed?
5) Benefits of Auditing in Cyber Security
6) Conclusion
Want to learn Zero Trust Strategy and Architecture? Join the Microsoft Cyber Security Architect SC100 course – today!
What is Auditing in Cyber Security?

Cyber Security Audit can be described as a thorough analysis and assessment of an organisation's existing digital infrastructure, firewall, and security systems. Even though companies have internal teams that take care of the Cyber Security systems, such an audit is mainly carried out by third parties. Governments and their relevant bodies recognise these organisations. These firms provide services to identify potential threats to their client's data, systems and Cyber Security Infrastructure.
These assessments recognise weak spots in the digital infrastructure of the firm, such as backdoors used by cybercriminals for common types of scams. The main goal of this audit is two-fold:
a) To comply with guidelines of regulatory bodies and validate different certifiable standards, and
b) To provide an in-depth analysis of the company's cyber security status to managerial staff, employees, staff, and vendors.
Types of Cyber Security Audit
Cyber Audit has become essential to how companies manage their digital infrastructure and safeguard their data and systems. Cyber Security Audits are of two types – internal and external.
a) Internal Audit – When a business uses its resources and internal audit department, it is known as Internal Audit. The primary purpose of such an audit is to validate the business systems to ensure compliance with policies and procedures.
b) External Audit – These audits are carried out by third parties, usually outside the organisation. Through these audits, the company wants to ensure that it follows all the regulations, guidelines, and government policies.
Learn how modern Cyber Attacks are executed with the Cyber Security Risk Management course.
Importance of Cyber Security Audit

As businesses and their processes are being carried out online, the role and importance of such assessments have become all the more critical. It helps in identifying any potential threats and weaknesses in the systems. This way, organisations can determine ways to safeguard their data and networks. The role of a Cyber Audit can reveal valuable information to the management, helping them to make decisions and support the business operations.
The importance of these audits can be understood because they help management identify critical datasets. In addition, these also help in developing protocols that help in protecting and safeguarding the data as well as networks and systems for the company. Through such audits, the organisation's overall capacity can be increased to handle cyberattacks.
Several companies have integrated their operations, and IT functions into their day-to-day functioning and decision-making. This has made the first line of defence for businesses and enables them to manage their operations effectively. This way, they can ensure that the network and data are secured. The second line involves the information and technology risk management leaders. They establish governance and oversight to monitor the security operations and take decisions and actions to secure the company's data.
Cyber Security Audits have emerged as the third line of defence for organisations. With such processes, companies' leadership can identify potential threats, determine ways to mitigate them effectively and safeguard the data and company systems.
Such an audit ensures that an in-depth, 360-degree security analysis of the company is carried out. The Cyber Security Audit scope extended beyond securing data, providing security to the operations, securing the network and systems, and checking the physical safety of the hardware like servers and computer systems. These assessments also influence the overall functioning of the company as well as the performance and image of the firm in the market.
Gain in-depth knowledge of security incident investigation with the CCNA Cybersecurity Operation Training course.
When is Auditing needed?

The frequency of Cyber Audits is entirely dependent on the industry that the organisation is a part of and the demands of its systems and applications. Companies today tend to handle a vast amount of sensitive data and therefore they are more likely to conduct such audits. If there is more data and the company uses multiple systems, then the frequency of cyber audits will be higher. In addition, external factors like regulatory requirements and others also have an impact on the number of times Cyber Audits will be necessary.
The Cyber Security measures of a majority of companies are carried out at least twice a year. However, they can also be done on a monthly or quarterly basis. In addition, different departments can have different times for audits which can be scheduled as per the application, systems, and data used. Quarterly or monthly audits are more effective for organisations because these provide management with regular updates about the accurate status of the systems. This way the firm can manage its Cyber Security with greater ease and effectiveness. In addition, the frequency of audits is also dependent on the type of data. If the data is highly sensitive, then more Cyber Audits will be required.
Cyber Audits become all the more important after a data breach. The company quickly needs to identify the reasons for the breach and determine ways to ensure that it does not happen in the future. Similarly, such audits are required once the system has been upgraded or after data migration.
Acquire skills in deploying firewalls with an Introduction to System and Network Security course.
Benefits of Auditing in Cyber Security
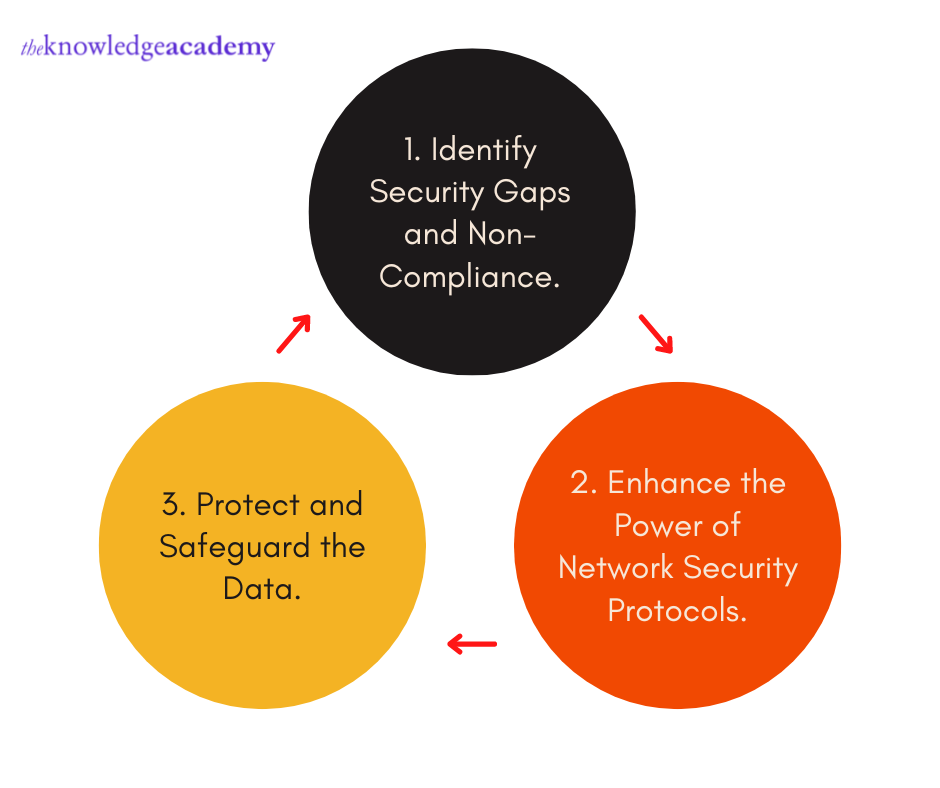
Protecting data has become an essential task for companies, as their performance and image are dependent on the way the data, systems, and networks are secured. Following are some of the key benefits of Cyber Audits.
a) Identify the Security Gaps and Non-Compliance – One of the key advantages of a Cyber Audit is that it identifies any gaps in security and any non-compliance with the key regulations. Every organisation has to follow the regulatory requirements laid out by the government and such entities. Such analysis also helps in identifying any gaps in the security measures implemented by the company.
b) Enhance the Power of Network Security Protocols – In recent years, the number of cybercrimes has increased substantially, especially on unsecured networks. This way the hackers can take undue advantage of the vulnerability of the companies. However, with Cyber Audits, organisations can ensure the security of their networks. This way they can also enhance the protocols put in place to secure the systems, thereby filling the security gaps.
c) Protect and Safeguard the Data – Through such audits, the firms get an additional layer of security that they can use to protect and safeguard the data. Businesses’ existing Cyber Security measures can be improved significantly with such assessments. These audits are a way that enables organisations to be proactive in protecting and securing their data. This limits the risk of a data breach and becomes a means that can help in maintaining the image of the company.
Learn to protect Data better with the Computer Forensics Foundation Training course.
Conclusion
Data security has become an essential aspect for businesses, as it is a means through which they can improve their operations and protect their image in the market. Cyber Security Audits have emerged as the third layer of defence for companies. It helps in identifying threats and risks even before they become an issue for the firm. In this blog, we described the importance of auditing Cyber Security for businesses. We hope that you have gained clarity on what are such forms of assessments and how they can be useful for organisations.
Enhance your understanding of Cyber Threats with the Cyber Security Awareness course.
Frequently Asked Questions
Upcoming IT Security & Data Protection Resources Batches & Dates
Date
 Certified Cyber Security Professional (CCS-PRO)
Certified Cyber Security Professional (CCS-PRO)
Fri 21st Mar 2025
Fri 23rd May 2025
Fri 22nd Aug 2025
Fri 5th Dec 2025







 Top Rated Course
Top Rated Course



 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


