We may not have the course you’re looking for. If you enquire or give us a call on 01344203999 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.

To ensure that the company will function with stability – It is crucial that you implement Cyber Security measures in your organisation. These security measures will help you secure your network or your company's data against unauthorised access.
Enforcing Cyber Security is paramount to all the individuals or organisations connected to the internet for obvious reasons. Any system connected to the internet is prone to security risks. The benefits of Cyber Security are immense. It includes the safety and responsibility of your credentials and sensitive information while resisting any form of cyber-attacks and threats.
According to reports from multiple sources, there has been a continuous rise in cyberattacks in recent years. Hence, administering standard Cyber Security measures is vital for an organisation to protect and prevent any possible malicious attacks.
As stated by the Security Magazine, more than 22 billion records were exposed to cyber vulnerabilities in 2021, which is approximately 5% lesser when compared to 2020. This report highlights the necessity of employing Cyber Security measures to stall such Cybersecurity threats.
Further in this blog, you will be directed towards understanding the use cases and multiple benefits of Cyber Security.
Table of Contents
1) What is Cyber Security?
2) Benefits of Cybersecurity
3) Top 5 Use Cases of Cyber Security
4) Conclusion
What is Cyber Security?
Cyber Security is all about protecting internet-connected systems from any possible cyber-related risks. It involves data protection, software & hardware protection, and measures to prevent malicious attacks that try to access devices or networks.
Cyber Security also includes disaster recovery planning with preventative methods to ensure recovery from any untoward Cyber Security incidents. It aids in tackling such future occurrences in an organisation.
Cyber risks can pop up in several ways. Here are a few common Cyber Security attacks listed below:
a) Malware Attacks
b) Ransomware Attacks
c) SQL Injection
d) DDoS Attack
e) Phishing
Are you an advanced professional with high-level experience and skills in a wide range of security areas? Then this Microsoft Cybersecurity Architect SC100 Training is for you.
Benefits of Cyber Security
The benefits of employing Cyber Security measures are immense. Businesses and people may defend themselves and others against the complete spectrum of cyber security risks by using cyber security solutions.
The Cyber Security measures can take the credit as the businesses may relax knowing that their network and data are safe and secure. The benefits of employing Cyber Security accrue to companies, end users, and staff members.
Cybersecurity not only improves and strengthens detection, but it also enhances mitigation and reaction against any form of cyber threat. The recovery can happen much faster in case of any attack using sophisticated approaches if Cybersecurity measures are in place.
Additionally, businesses have discovered that users and developers have greater faith in products protected by reliable Cybersecurity measures.
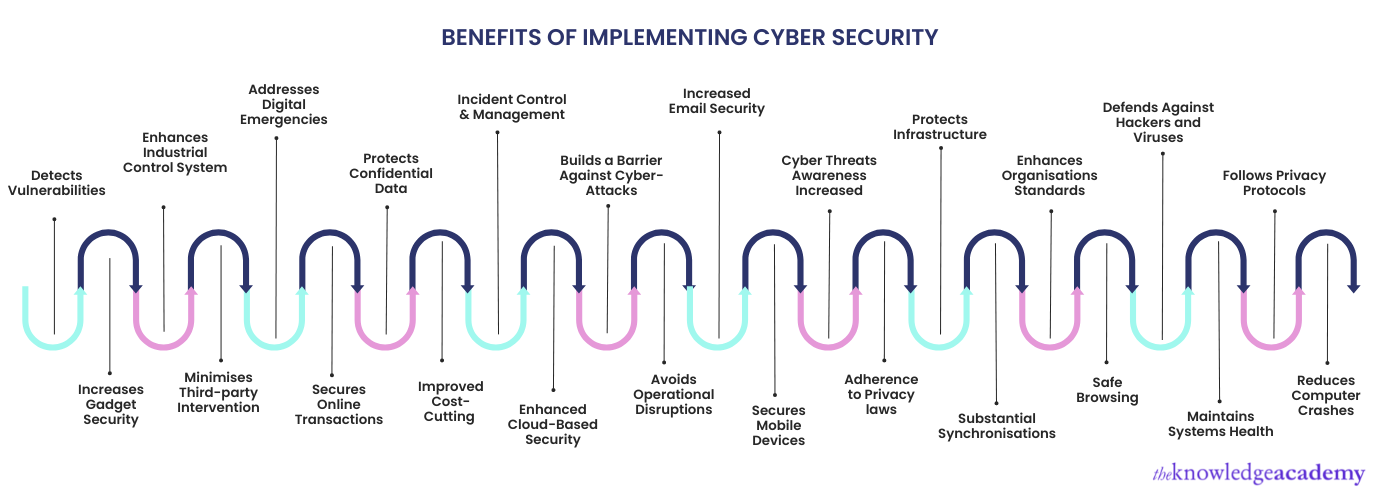
Below is a list of benefits discussed for you to have a better and clear understanding of Cyber Security benefits acquired by implementing the Cybersecurity measures in the organisation.
Benefits of implementing Cybersecurity measures in an organisation.
The benefits of implementing Cybersecurity measures are immense; it can increase cyber resilience, enhance cyberspace security, speed up data protection & information, tackle hackers & theft attempts and safeguard networks and resources.
Following is a list of the most significant benefits of Cybersecurity explained.
Eliminates External and Internal Threats
Cyber Security threats can come in multiple ways through an external or internal medium. Hence, it is significant that organisations concentrate on developing Cyber Security measures for both External and Internal threats.
Now let us analyse what these two threats are:
External Threats:
External Threats can be defined as an attempt made by a malicious outsider who is outside the company to exploit the vulnerabilities. The attempts involve using malicious software, phishing, hacking, injecting viruses, or other similar attempts with an evil motive.
These cyber criminals' motives might vary as some attackers would attack to demand a ransom, others might act to spoil an organisation's image, and a few might be spies hired to collect information and make a political influence or for social gain.
Irrespective of the reason for the attack to be carried out, it is vital that the organisations employ necessary Cyber Security measures to combat and prevent such attacks.
Internal Threats:
No company or organisation would feel good about facing an Internal Threat. But it is a reality that needs to be taken seriously and ensure necessary measures and policies are applied to resist such threats from happening.
Internal Threats usually come up from the employees who are working inside the same organisation. With an increase in remote work, the importance of ensuring security measures is necessary now, more than ever.
Implementing proper Cyber Security measures can ward off and eliminate External and Internal Cyber Threats. Hence, organisations need to ensure regular surveillance and employ Cyber Security standards to help bring down the chances of such incidents and assist in exposing vulnerabilities.
Regulates Guidelines
Based on the type of organisation and the level of sensitive information of the company and customers stored in your database, you need to follow the necessary Cybersecurity guidelines and implement stringent Cybersecurity measures, leaving no room for malicious attacks.
Enhances Productivity
Having Cyber Security strategy can enhance the productivity of the organisation. The basic Cybersecurity standards or measures expected to ensure the smooth workflow of the organisation that can boost productivity are supportive firewalls, cloud security, data backups, virus scanning, and software updates.
Boosts Brand Value
Employing Cyber Security standards can instil confidence in the customers' minds and bring in brand loyalty. It can also increase trust and allow people to promote your services. Cybersecurity can influence your brand value and build a good client base.
Aids in Cost Cutting
Installing Cyber Security measures can cost you some amount, but certainly, it is reasonable and necessary to invest. This investment in Cyber security can help your organisation to be safe and protected from various cyber-attacks and breaches, which could cause you a great deal of money and effort to recover.
Benefits of training employees in Cybersecurity
By training employees in Cyber Security an organisation can gain numerous benefits.
Cyber Security training can help employees to gain knowledge and understanding of how to cope with cyber-related risks. Conducting Cybersecurity training will help employees to learn about the latest cyber threats and risks. Also, it guides them to follow the latest best practices for data security.
Cyber Security measures support an organisation to develop a secure culture in an organisation. It also helps build a skilled workforce to identify and mitigate cyber threats.
Are you interested in mastering skills to mitigate cyber-related risks? Then, register with the CCNA Cybersecurity Operation Training now!
Top 5 Use Cases of Cyber Security
First let us understand, what is a Use Case in Cybersecurity.
In simple terms, a Use Case in Cybersecurity is a list of steps or guidelines that explains when, what, and how to use a product or service in a Cybersecurity system to prevent or mitigate threats.
Following is a list of use cases in Cybersecurity you need to understand for the purpose of updating Cyber Security of an organisation.
Keeping a track of system changes
Consistently monitor operators who share, store, and delete information vital to the company’s growth and development. Automating using software or keeping an eye on such critical activities can usually help flag a red signal in case of any tampering with audit logs. These modifications escalated immediately can assist in stopping any further damage and reduce subsequent risks.
Hence, establishing firm rules and procedures for flagging critical events, such as the deletion of audit trails or unlawful configuration modifications, is a valuable Use Case you need to refer to in Cybersecurity.
Identifying abnormal behaviour on high-profile accounts
Monitoring frequently accounts accessed multiple times outside login hours or expected login areas can help you immediately raise a red flag in case of any visible threat. Also, avoid using generic accounts such as administrator or admin, which commonly attract cybercriminals.
System or database administrators are the best examples of privileged users who have expanded access permissions, making them a prime target for hackers. Analysts should closely monitor for any unusual actions attempted by these privileged users and check for any odd behaviour that would point to a threat or a breach.
Detecting Phishing activities
Phishing is a malicious attempt by swindlers to gain private information to conduct impersonation and fraud activity globally. The Phishing attack usually attempts to get personal data, such as social security numbers, bank account numbers, PIN codes, and passwords. You must ensure that the data is protected throughout the business to minimise any possible phishing activity.
Phishing activities are usually carried out (particularly spear phishing) to gain initial access to a network. Analysts may take prompt action to reduce damage when they receive phishing emails by using a security software system to trace who opened them, clicked any links in them, or responded to them.
Identifying compromised credentials of users
Let us understand what compromised user credentials mean.
Compromised user credentials refer to the account of a particular user being hacked or used by an unidentified malicious user. It means that someone other than you possesses illegal access to your user ID and password.
You must consider and apply this use case to prevent any attempts of compromises through user credentials using Brute Force, Pass the Hash, Golden Ticket, or other techniques. It is crucial to identify the users and entities affected to analyse the effect and impact in the event of a successful hack to prevent further damage.
Threat Hunting
Threat Hunting is actively looking for cyber hazards within a business or a network. A threat search addresses a security problem or can find new and unforeseen assaults or breaches.
You can set up alerts based on behavioural analytics intelligence that detect and notify the new and previously undetected threats in real time. Also, by applying automation methods, many minute details that go undetected or get missed by the human eye can be noticed.
Conclusion
Employing Cyber Security can help an organisation by reducing the chances of data breaches and other Cybersecurity incidents. By reading this blog, you will understand the use cases and the benefits provided by Cybersecurity.
Are you interested in identifying attacks and vulnerabilities before it infiltrates? You can register with the CompTIA Cybersecurity Analyst CySA+ Certification course for expert training and help.
Frequently Asked Questions
Upcoming IT Security & Data Protection Resources Batches & Dates
Date
 Certified Cyber Security Professional (CCS-PRO)
Certified Cyber Security Professional (CCS-PRO)
Thu 1st Jan 1970







 Top Rated Course
Top Rated Course




 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


