We may not have the course you’re looking for. If you enquire or give us a call on 01344203999 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.

Cyber Security Attacks are constantly on the rise, along with the cost of managing them. Statista states there were about 24 thousand Cyber Security Incidents globally between 2020 and 2021. The professional sector was the most targeted, with nearly 3600 Incidents.
Countries like Russia, North Korea and China are constantly testing and trying to penetrate their rival's Cyber Space. Although they do it under the guise of private entities, many Intelligence agencies and experts believe that they act on behalf of their nation-states.
Going back to a recent Cyber Security Incident in August 2022, a Russian group claimed responsibility for breaching a privately owned UK water supply company, “South Staffordshire Water,” and leaking files in an extortion attempt. With attacks like these, they are looking to find weaknesses in their opponent's Cyber Space.
Table of Contents
1) Let’s understand - Cyber Security Incidents?
2) Types of Cyber Security Incidents with examples - Explained
3) What are the impacts of Cyber Security Incidents?
4) Now, let’s learn how to prevent Cyber Security Incidents
5) Conclusion
Let’s understand - Cyber Security Incidents?
According to Computer Misuse Act (1990), Cyber Security Incident is unauthorised access to a system or systems by breaching its security policy to affect the integrity and availability of the system. It could be anything from the listed items below:
a) Unauthorised access to a network, system or Data
b) Unauthorised storage and distribution of Data
c) Unauthorised changes to either hardware or software
d) Disruption of a service or a system in a Network
e) Intentional or Unintentional leakage of Data
Get an in-depth insight into Cyber Security and its importance. Signup for our Cyber Security Risk Management course now!
Types of Cyber Security Incidents with examples - Explained
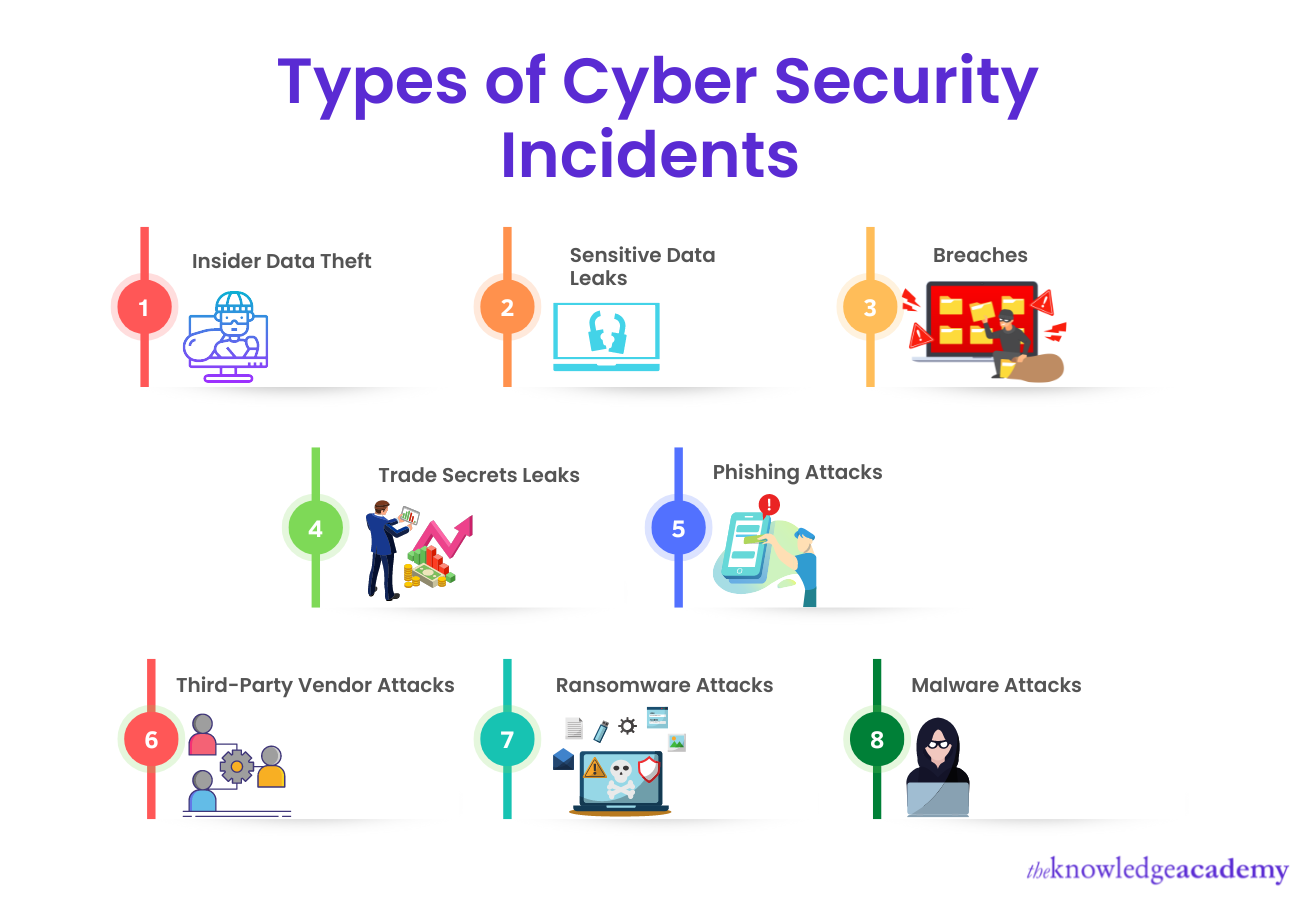
1) Insider Data Theft
2) Sensitive Data Leaks
3) Breaches
4) Trade Secrets Leaks
5) Phishing Attacks
6) Third-Party Vendor Attacks
7) Ransomware Attacks
8) Malware Attacks
1) Insider Data Theft
Insider Data Theft is one of the most common and often overlooked types of Data breach. It can be just as damaging as an outside breach. Insider Data Theft can be better defined as a person posing as an employee (Insider) stealing Data or any other valuable information from the organisation’s Database and Devices. In 2021 alone, the total average cost of Insider Attacks stood at a whopping 12.5 million GBP, underscoring the critical importance of implementing effective Cyber Security Essentials.
Example: An employee negligence in Dallas Police Department resulted in a massive data loss in 2021. Around 8.7 million files were leaked, with over 23 terabytes of data. Although this Data leak isn’t deliberate or malicious, it would still come under as an Insider Attack.
2) Sensitive Data Leaks
When sensitive Data is leaked online or offline without proper authorisation of the data owner, sensitive Data Leaks can cause catastrophic damage to an individual or an organisation. And the damage can impact both financially and psychologically, and the user is at risk of losing privacy. The following are a few examples of sensitive data.
1) Username
2) Password
3) Security Pin
4) Credit Card Data
5) Personal & protected Information such as Social Security Number, address or Phone number
Example: Australian healthcare and insurance provider Medibank was targeted by an unknown hacker. When Medibank refused to accept their demands, the hacker released sensitive data containing the procedures and diagnosis codes of about 9.7 million customers.
3) Breaches
A Data Breach is anything that violates the confidentiality of the Data. If confidential Data is accessed, viewed, transmitted, or any other unauthorised action can be considered a Data Breach. Even if the incident is unintentional, it would still be considered a Data Breach.
Example: One of the most significant breaches in the UK happened on September 2022. A Russian-based hacking group targeted the website of the UK’s intelligence agency MI5, which temporarily took their site offline.
4) Trade Secret Leaks
A Trade Secret is confidential or secret information with substantial economic value for an organisation. And this type of information is generally known and shared between a few persons. Therefore, if this information is leaked, it could significantly impact a company’s profit and jeopardise its survivability.
Example: A former employee of Intel who worked for nearly a decade stole classified documents considered trade secrets on his final days at Intel. And the same employee was later hired by Microsoft.
5) Phishing Attacks
Phishing is sending messages or emails claiming to be from a well-known company with the malicious intent of stealing a person's personal and sensitive Data of a person. And it is responsible for more than 60 per cent of Social Engineering oriented Cyber Security Incidents.
A Phishing Attack happens when an attacker contacts the victim through a communication channel like email or text message and then sends them links or attachments that contain harmful content that can steal the recipient’s Data.
Example: Amidst the Russia-Ukraine war in 2022, a well-known Russian hacking group named “Cold River” launched Phishing Attacks on three nuclear research labs in the US to trick the scientists working there into revealing their passwords. Whether the attempt was successful or not is not yet disclosed.
6) Third-Party Vendor Attacks
A Third-Party Vendor Attack is when someone attacks your partner or any other third-party agency associated with you to steal your clients' data. Moreover, Third-Party Attacks are also known as Supply Chain Attacks. Rather than hacking the leading organisation, these attackers target their partner agencies as their security measures can be easily compromised.
Example: Mariott Hotels & Resorts were the victims of a Third-Party Vendor attack when hackers misused the third-party application Mariott group uses to provide guest services. The attackers accessed more than 5 million guest records, including their Personal Data.
7) Ransomware Attacks
Ransomware is malware that uses cryptology to block you from accessing your device and its Data in exchange for a ransom. Not only that, but they can also threaten to publish the Data unless the ransom is paid. Even if the victim pays the ransom, there is no guarantee that they won’t post the data or restore your access.
Example: In February 2022, it was reported that the biggest semiconductor chip and GPU manufacturer Nvidia was attacked by ransomware by a group named “Lapsus$”. The group claimed it had access to Nvidia’s source code and nearly one terabyte of data.
8) Malware Attacks
Malware is a harmful software program or code that can cause damage to a computer system or network. In Layman’s terms, Malware can be anything like Viruses, Trojans, Malware and Computer codes that can damage a device or network. Attackers use Malware to gain access to a victim’s Data and will try to deprive them of entry.
Example: In May 2021, the largest fuel pipeline in the US, “The Colonial Pipeline”, was attacked by a group called “DarkSide” using Ransomware. This attack posed a risk of fuel shortages in many states across the East Coast. In the end, Colonial Pipeline had to pay off a ransom of about 4.6 million GBP to the attackers.
Register for our Cyber Security Awareness course to learn more about the significance of Cyber Security
What are the impacts of Cyber Security Incidents?
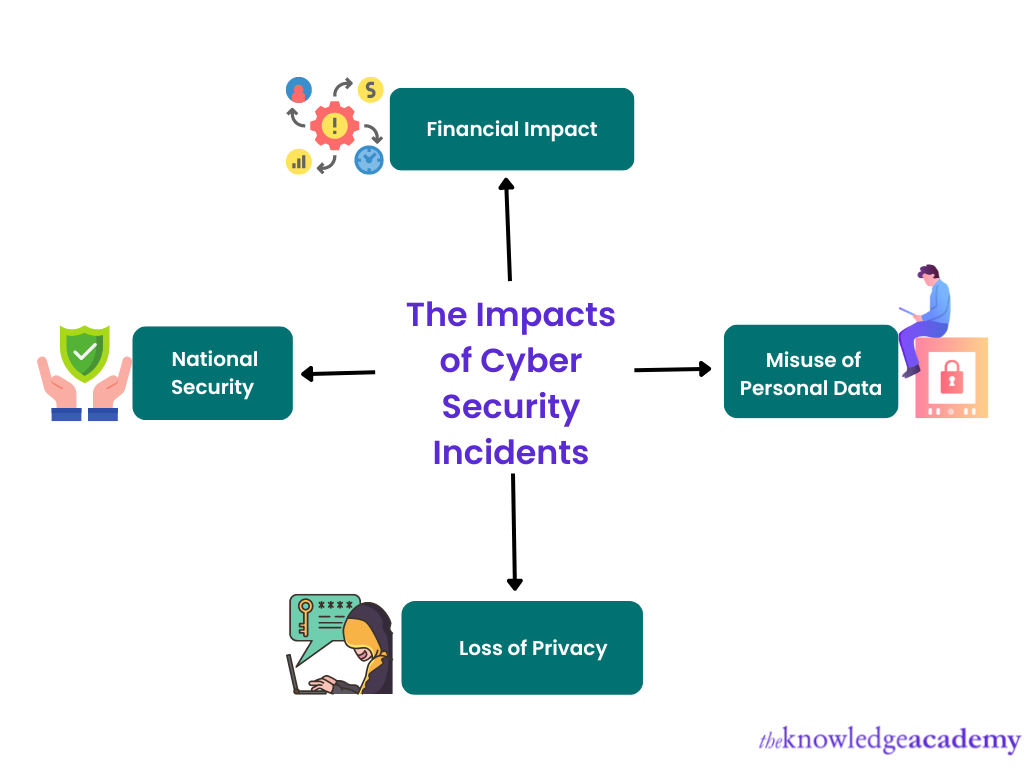
Between 2020 to 2022, the average cost of a data breach is reported to be around 3.1 million GBP. And the healthcare sector is the most impacted, with an average price of about 5.8 million GBP. So let’s look at a few impacts of Cyber Security Incidents.
Financial Impact: A single Trade Secret Leak could considerably blow a company’s profit and threaten its existence. Moreover, the exact purpose of Ransomware Attacks is monetary exploitation.
Misuse of Personal Data: Millions of user data are available for sale on the so-called “Dark Web”, and there’s a high chance that people with malicious intent could misuse these personal data.
Loss of Privacy: Perhaps the most important and often overlooked issue from a Cyber Security Incident is the loss of privacy to an individual.
National Security: Based on the recent Cyber Security Incidents on Colonial Pipeline and SolarWinds, it is becoming evident that a single Cyber Attack can disrupt a country’s infrastructure. Hence, it’s starting to become a significant threat to national security.
Now, let’s learn how to prevent Cyber Security Incidents
Now that you know these impacts, let’s learn how to prevent and mitigate these issues.
Monitoring: By constantly monitoring who accesses the Data, you can identify and prevent such incidents.
Restricting Access: Ensure access to the Data is denied and only given to the right people.
Encryption: Encryption gives an extra layer of security to the Data and makes it harder to access.
Pre-emptive Measures: In some cases, it took months to identify a Data breach. If the problem is identified earlier, the damage can be minimised. In addition, using security software that can monitor and give security can give you an edge.
Weed out Weakness: Conduct Penetration tests using the guidelines of ethical hacking. Find out areas of weaknesses and fix those issues immediately.
Conclusion
Now that you’ve read the blog, we hope that you understood the importance and impacts of Cyber Security Incidents with real-life examples. Apart from this, you might have also learned about the different types of these attacks and how to prevent them.
Check out our courses on Cyber Security to gain expertise in this field.
Frequently Asked Questions
Upcoming IT Security & Data Protection Resources Batches & Dates
Date
 Certified Cyber Security Professional (CCS-PRO)
Certified Cyber Security Professional (CCS-PRO)
Fri 21st Mar 2025
Fri 23rd May 2025
Fri 22nd Aug 2025
Fri 5th Dec 2025







 Top Rated Course
Top Rated Course




 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


