We may not have the course you’re looking for. If you enquire or give us a call on 01344203999 and speak to our training experts, we may still be able to help with your training requirements.
We ensure quality, budget-alignment, and timely delivery by our expert instructors.

Cyber Security Risk Management is a strategic approach that prioritises risks and helps organisations minimise threats in their online systems and networks. It is also known as Information Technology (IT) Security or Electronic Information Security. These methods can enable companies to handle critical threats promptly and ensure that their systems and processes are safe from cyber thefts and attacks. According to a 2022 IBM Security report, cyberattacks carried out by exploiting vulnerabilities have increased by 33% between 2020-21, highlighting the urgent need for implementing and maintaining robust Cyber Security Essentials in the realm of Cyber Security Risk Management.
This blog will act as a guide and help to get a better understanding of IT Security Risk Management and its process. In this blog, we discuss the following:
Table of Contents
1) What is Cyber Security Risk Management?
2) Process for managing Cyber Security Risks
3) Frameworks and Standards for Cyber Security Risk Management
4) Best Practices for Managing Cyber Security Risks
5) What will you gain from Electronic Information Security Risk Management Process
6) Conclusion
Understand how to safeguard against Cyberattacks with Cyber Security Risk Management course.
What is Cyber Security Risk Management?

Cyber Security Risk Management is a process that provides an organisation with insights into the potential threats in its systems and networks. The integration of advanced cyber security analytics tools plays a pivotal role in proactively identifying and mitigating potential cyber threats, enhancing the overall effectiveness of the risk management process.
In modern times, the role of cyber security attack Risk Management practices is crucial. Such methods reduce the chances of a cyberattack. It is a continuous process that identifies, analyses, evaluates and addresses potential Cyber Security threats for the company.
A robust Cyber Security system can play a vital role in enabling the company to improve its performance while safeguarding the data from cyberattacks. It can provide the management with valuable information concerning best practices and methods to minimise the risk of cyberattacks. This way, the company can protect itself from having to pay huge fines imposed by the governing and regulatory bodies.
Learn how to precent Cyber Threats with Cyber Security Awareness course.
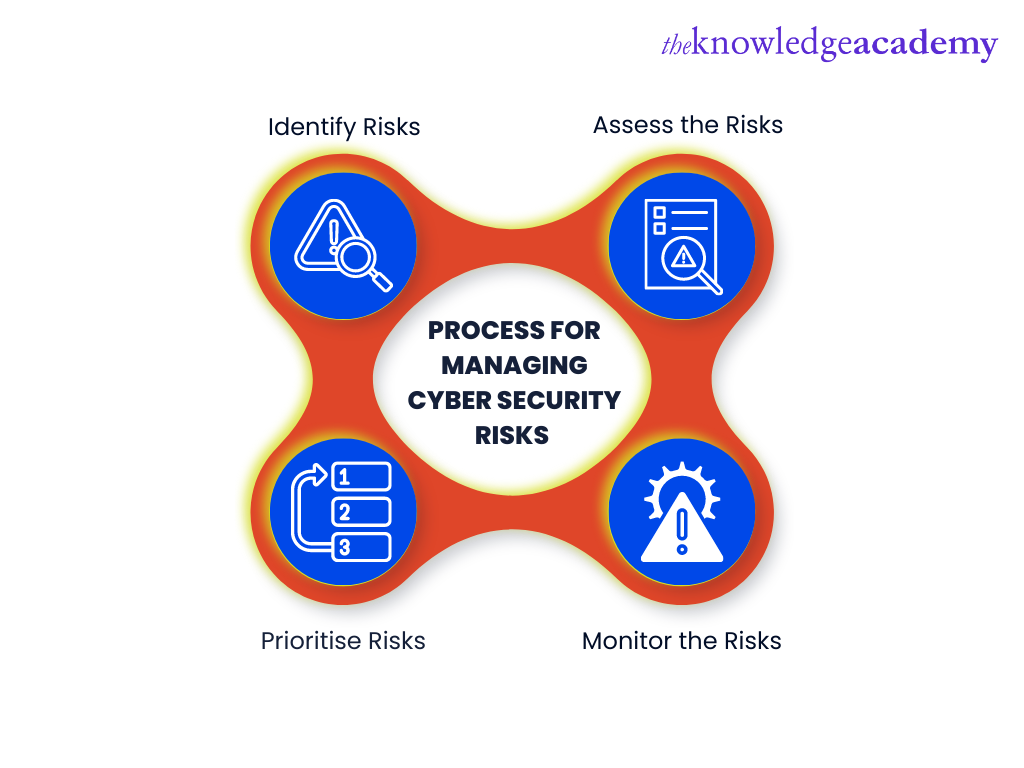
Process for managing Cyber Security Risks
Today, Cyber Security is an essential aspect of business operations. It enables companies to identify and minimise the risks before they become a cause of concern and inflict significant damage to the company. A well-developed and maintained Cyber Security system can analyse and identify the cyber risks and then provide the management with information on the best ways to mitigate the risks. Considering the modern landscape, the use and effectiveness of such systems can be highly beneficial and become a means through which the company can create and implement strong practices to secure the data and its systems and networks.
The Cyber Security Risk Management process can be outlined in four steps, as shown below.
a) Identify Risks – In the first step, the Cyber Security professionals have to identify the risks faced by the IT systems of the company. To identify such risks, these individuals have to conduct a thorough analysis of IT infrastructure and networks. In addition, Cyber Security professionals also need to carry out an analysis of the market to identify the threats and trends in the market that can have a negative influence on the company.
b) Assess the Risks – Once the risks have been identified, IT professionals have to assess them. The information obtained from such assessments will help management in making effective decisions. Based on such information, the management can determine the best course of action and thus mitigate and reduce the cyber risks for the company.
c) Prioritise Risks – The IT professionals will have to prioritise the risks after assessing them. By undertaking this step, the management will be in a better condition to understand the threats. Prioritising the risks will help understand and identify the risks that must be dealt with on priority. The Cyber Security people will have to prioritise the risks based on their severity and potential negative impact on the company.
d) Monitor the Risks – Cyber Risks are evolving on a day-to-day basis. Due to this reason, once the risks have been prioritised, the Cyber Security professionals have to closely monitor the risks to see if any new aspect is added to the risk, which eventually might harm the company. Further, as new versions are added to the cyber risks, the information gained can enable the management to develop the right risk management plan. This way, the company can significantly minimise cyber threats.
Become a Certified Cyber Security Professional (CCS-PRO) today!
Frameworks and Standards for Managing Cyber Security Risks

Managing Cyber Security Risks has become a significant aspect of business operations for companies. Following are some of the critical frameworks and standards that can be used to mitigate and minimise cyber threats.
ISO 27001
It is an international standard used for managing information security. It is one of the leading standards used for protection against cyberattacks. According to clause 6.1.2, the IT systems should have the following:
a) Establish and maintain the information security risk criteria
b) Ensure that from repeated risk assessments ‘consistent, valid, and comparable’ results are achieved
c) Recognise the risks associated with the loss of confidentiality, integrity, and availability of information
d) Identify the risk owners
Thinking of learning ISO 27001? Join ISO 27001 Foundation course today!
NIST Cybersecurity Framework (CSF) 1.1
The National Institute of Standards and Technology (NIST) recommend 108 actions that enhance the IT Security Risk Management process in its five essential functions – identify, protect, detect, respond, and recover. The primary purpose of this framework is to help companies better manage and reduce all types of cyber risks. The NIST CSF recommends organisations take the following steps to manage Cyber Security Risks.
a) Recognise and document vulnerabilities of the systems and networks
b) Keep up to date with the latest trends in Cyber Threat Intelligence
c) Identify and record both internal and external Cyber Security threats
d) Understand the potential impact and likelihood of a cyberattack
e) Identify and prioritise the risks
The Department of Defence (DoD) Risk Management Framework (RMF)
The guidelines of DoD RMF split the risk management process into six steps – categorise, select, implement, assess, authorise, and monitor. In this Cybersecurity Framework, the focus is on determining ways through which chances of similar threats affecting the business again can be reduced to the greatest possible extent. This framework enables companies to get a better understanding of the cyberattacks and then develop ways through which their chances of a repeat cyberattack can either be reduced or eliminated, highlighting the importance of robust Cyber Security for Business.
The Factor Analysis of Information (FAIR)
The FAIR framework was designed to help companies measure, analyse, and understand cyber risks. The primary goal of this framework is to help the management make well-informed decisions while developing the Cyber Security best practices. Using this framework, companies can quantify the risks, providing detailed information to the management. This way, the company's leadership can make effective decisions that help mitigate the risks and safeguard the data.
Center for Internet Security (CIS) Controls
It is one of the widely used and adopted frameworks for Cyber Security. Unlike other frameworks, it takes a more prescriptive approach to manage online threats and enables the leadership to manage risks in their IT infrastructure. It provides twenty critical controls distributed across three categories – Basic, Foundational, and Organisational.
Learn to design a Zero Trust strategy and architecture with the Microsoft Cybersecurity Architect SC100 course.
Best Practices for Managing Cyber Security Risks

The number of risks and threats in the online environment has increased significantly in recent years. Some best practices companies can follow to mitigate and manage their online threats effectively:
a) Know IT Environment and Assets – Implementing the various IT Security Risk Management frameworks and systems requires the management to possess knowledge of the IT environment and assets of the company. This means the organisation's leadership must have a complete idea about the various IT assets, such as servers, computers, and other hardware and software owned by the company. If this information is available and accessible, the management can make relevant decisions protecting the data and networks.
b) Create a strong Cyber Security Risk Management Strategy – To keep the data and IT systems of the company safe, the leadership must focus on building and maintaining a powerful IT Security Risk Management strategy. This will entail the management concentrating on performing a thorough analysis of the company's existing systems and IT infrastructure. Organisations must develop a solid and effective Cyber Security strategy and update it regularly.
In this regard, the management must identify the company's risk tolerance limit and develop a profile to help build an effective strategy. A vital element of a robust Cyber Security strategy is to develop best practices that employees can follow. These must be integrated into the training of the employees.
c) Make Cyber Security a crucial part of Organisational Culture and Values – The management must focus on making online security a part of the company's culture and values. This way, the leadership will be able to train their employees on how to perform their tasks online while keeping their data safe and secure. Once online security is part of organisational culture and company values, it will be simpler for the business to protect its IT infrastructure.
d) Strict Security Protocols must be implemented – To secure the IT infrastructure from cyberattacks and risks, the management must implement strict security protocols. This means the leadership and the IT team should remain vigilant so they can identify and even prevent the cyberattack. This will help safeguard the company from such attacks and provide real-time information and insights, allowing the management to make relevant and effective decisions.
With CCNA Cybersecurity Operation Training, gain an in-depth understanding of SOC infrastructure and TCP/IP.
What will you gain from undertaking the Cyber Security Risk Management Process

The role of IT Security Risk Management is vital. It forms the basis on which the company can focus on protecting its data, networks, and IT infrastructures. A robust IT Security strategy can help improve the organisation's security posture and identify the necessary improvements further to strengthen the security of the data and such systems. The following points show some of the main benefits of managing Cyber Security Risks.
a) Timely Identification and Mitigation of Risks - One of the critical benefits of the IT Security Risk Management process is that it helps in the timely identification and mitigation of Cyber Security Risks. The IT team should be able to recognise the threats on time to manage the cyber risks effectively. To safeguard against cyber threats, proactiveness is very important. The company has to identify the threat and implement its solutions before the risk becomes an issue. A firm can achieve this proactiveness with properly developed Cyber Risk Management plans.
Acquire skills in using Firewalls to control Network Traffic with Introduction to System and Network Security course.
b) Reducing the Vulnerabilities - Another way the IT Security Risk Management processes can help an organisation is by reducing vulnerabilities. Fixing the systems after an attack has taken place is very difficult. This exposes the company to market forces and negatively impacts its image and performance. With such processes, the company can reduce its vulnerabilities by eliminating weak areas and identifying potential threats before they cause any damage.
c) Ensuring Compliance - Laws and regulations such as the General Data Protection Regulation (GDPR) of the European Union (EU) have developed several policies that guide companies on ways to manage their data and IT infrastructure. Compliance with such regulations is essential. Otherwise, the government and agencies can heavily penalise the company. The IT Security Risk Management plans also help in ensuring that the company follows the regulations laid down by the government.
Conclusion
Secure your data! Download the Cyber Security ISO 27001 PDF Guide for complete protection.
Cyber Security has become an essential part of business operations. It enhances the company's security position and provides a way to prevent cyberattacks on its data and networks. The role of IT Security has evolved as organisations use several methods and approaches to secure data and systems. We hope that this blog helps you understand the processes used by companies to manage their Cyber Security better and reduce the overall risks and threats. As you prepare for roles in this area, studying Risk Management Interview Questions will give you the tools to better understand how risk management intersects with cybersecurity practices.
Upcoming IT Security & Data Protection Resources Batches & Dates
Date
 Certified Cyber Security Professional (CCS-PRO)
Certified Cyber Security Professional (CCS-PRO)
Fri 23rd May 2025
Fri 22nd Aug 2025
Fri 5th Dec 2025






 Top Rated Course
Top Rated Course




 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


