We may not have the course you’re looking for. If you enquire or give us a call on 01344203999 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.
In the rapidly evolving digital industry, "Hacking" and "Ethical Hacking" are frequently used but often misunderstood. Hacking, in its broadest sense, refers to unauthorised intrusion into computer systems and networks, often associated with malicious intent. Ethical Hacking, on the other hand, involves similar techniques but is conducted with legal authorisation and aims to identify and rectify security vulnerabilities. In this blog, we are going to discuss the Difference Between Hacking and Ethical Hacking and give some real-life examples of the same.
Table of Contents
1) What is Hacking?
2) What is Ethical Hacking?
3) Key Differences Between Hacking and Ethical Hacking
4) Ethical Hacking vs Hacking: Real-life examples
5) Conclusion
What is Hacking?
Hacking, in Cybersecurity, is the process of exploiting weaknesses in computer systems, networks, or applications to gain unauthorised access, manipulate data, or cause disruptions. It is an intricate skill set that involves understanding the intricacies of software and hardware systems. Hackers, often portrayed as enigmatic figures in popular culture, vary widely in intent and methodology.
Types of Hackers
1) Black Hat Hackers: Black Hat Hackers exploit vulnerabilities for personal gain, often engaging in activities such as stealing sensitive data, financial fraud, or launching cyber-attacks for political or ideological motives. Their actions are illegal and highly malicious.
2) White Hat Hackers: These are Ethical Hackers who use their skills for constructive purposes. Organisations employ them to identify security flaws before malicious Hackers can exploit them. White Hat Hackers conduct Penetration Testing, vulnerability assessments, and other Ethical Hacking techniques to fortify digital defences.
3) Grey Hat Hackers: This group operates in the morally ambiguous space between black and White Hat Hackers. They may hack without legal authorisation but not necessarily with malicious intent. Grey Hat Hackers might expose security vulnerabilities without causing significant harm, often to highlight the weaknesses in a system.
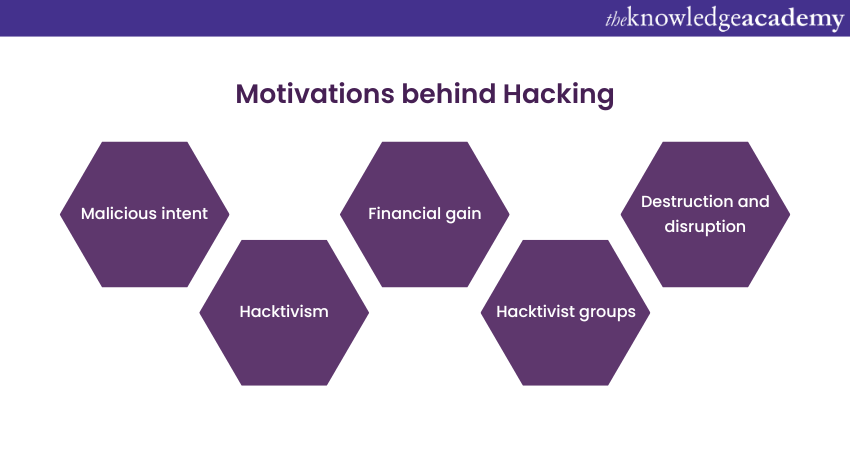
Motivations behind Hacking
Here are some reasons why Hacking is conducted in businesses:
1) Curiosity: Some Hackers are driven by a genuine interest in technology. They explore systems to understand their intricacies and push the boundaries of what is possible, often without causing harm.
2) Malicious intent: Hackers are motivated by personal gain, revenge, or ideological beliefs. They seek to exploit systems for financial profit, revenge against individuals or organisations, or to further their agendas, leading to widespread Cybersecurity threats.
3) Hacktivism: Some Hackers engage in activities known as hacktivism, where they hack into systems to promote social, political, or environmental causes. They may deface websites or leak sensitive information to raise awareness about specific issues, making them digital activists.
4) Financial gain: One of the most common motivations for Hacking is economic profit. Cybercriminals may hack into banking systems, e-commerce websites, or cryptocurrency platforms to steal financial information, conduct fraudulent transactions, or demand ransoms in cryptocurrency. The allure of monetary gain often drives sophisticated and targeted attacks.
5) Hacktivist groups: Certain Hacking activities are carried out by organised hacktivist groups. These groups, driven by social or political ideologies, launch coordinated attacks on specific targets to make a statement or protest against perceived injustices. Their actions are often high-profile and attract media attention.
6) Destruction and disruption: Some Hackers engage in destructive acts with the sole purpose of causing chaos and disruption. They might launch Distributed Denial of Service (DDoS) attacks, deface websites, or corrupt data, leading to financial losses, reputational damage, and operational disruptions for businesses and organisations.
7) Intellectual property theft: Hackers, especially those sponsored by competitors or rival nations, target corporations to steal proprietary information, trade secrets, or research and development data. Intellectual property theft can have severe consequences, including economic losses and a decline in innovation.
8) Personal vendettas: In some cases, individuals with personal grudges or vendettas may resort to Hacking to seek revenge against specific individuals, organisations, or communities. These attacks are often emotionally driven and can lead to significant harm to the targeted individuals' personal and professional lives.
What is Ethical Hacking?
Ethical Hacking, or Penetration Testing or White-Hat Hacking, is the legal and authorised practice of intentionally probing computer systems, networks, or applications to identify security vulnerabilities. Unlike malicious Hackers, Ethical Hackers use their expertise to uncover weaknesses before cybercriminals can exploit them. Organisations employ these professionals to simulate potential cyber-attacks and assess existing security measures, ensuring robust protection against unauthorised intrusions.
Motivations behind Ethical Hacking
Ethical Hacking, unlike malicious Hacking, is driven by a set of positive and constructive motivations that aim to enhance Cybersecurity and safeguard digital assets. Ethical Hackers are motivated by various factors, all geared toward ensuring the safety and integrity of digital systems:
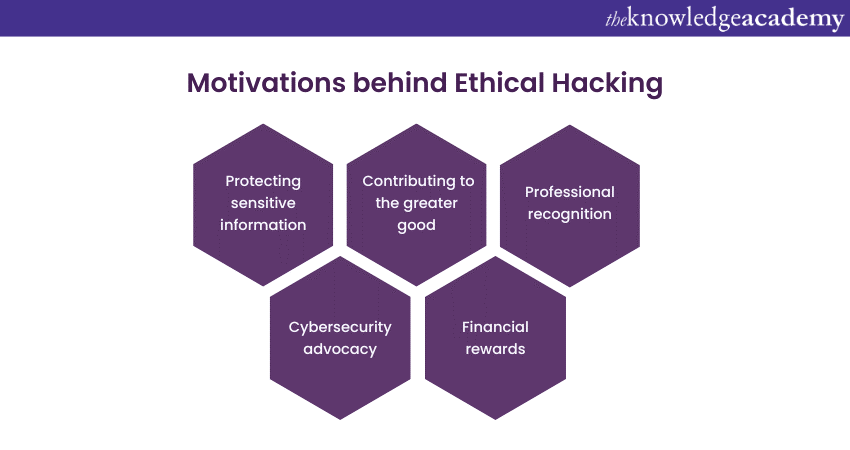
1) Cybersecurity advocacy: Ethical Hackers are passionate advocates for robust Cybersecurity practices. Their motivation stems from the belief that a secure digital environment is essential for individuals, businesses, and society. By identifying vulnerabilities and helping organisations strengthen their defences, Ethical Hackers actively contribute to a safer online ecosystem.
2) Protecting sensitive information: They desire to protect sensitive data from falling into the wrong hands. They understand the value of privacy and work diligently to safeguard confidential information, financial records, personal identities, and other critical data from unauthorised access, theft, or manipulation.
3) Challenge and intellectual stimulation: Ethical Hacking offers a challenging and intellectually stimulating career path. Ethical Hackers are motivated by the opportunity to learn and apply their knowledge in novel ways constantly. The ever-changing landscape of Cybersecurity keeps them engaged as they face new challenges and threats that require innovative solutions.
4) Contributing to the greater good: Many Ethical Hackers are motivated by social responsibility. They recognise the impact of cybercrime on individuals, businesses, and communities and strive to make a positive difference. Ethical Hackers view their work as contributing to the greater good, helping organisations protect their stakeholders and maintain trust.
5) Professional recognition: They often seek professional honour and respect within the Cybersecurity community. By successfully identifying vulnerabilities and assisting in developing secure systems, they establish themselves as experts in their field. Recognition and respect from peers and the industry serve as solid motivational factors.
6) Financial rewards: Ethical Hacking can be financially rewarding, especially for skilled professionals. Many organisations offer lucrative salaries, bonuses, and benefits to Ethical Hackers with exceptional skills and a proven track record. Financial incentives serve as a motivation for Ethical Hackers to improve their expertise and deliver high-quality security services continuously.

Key Differences Between Hacking and Ethical Hacking
Understanding the Difference Between Hacking and Ethical Hacking is important to protect your organisation from malware. Here are some differences between them:
Intentions and motivations
Hacking involves unauthorised intrusion into computer systems, networks, or applications with malicious intent. The motives behind Hacking can range from financial gain to personal vendettas, ideological beliefs, or sheer curiosity. The actions of Hackers can lead to financial losses, data breaches, and reputational damage for individuals and organisations alike.
Conversely, Ethical Hacking encompasses authorised Penetration Testing and vulnerability assessments conducted by professionals known as Ethical Hackers or White-Hat Hackers. The primary motivation behind Ethical Hacking is to identify security vulnerabilities before malicious Hackers can exploit them. Ethical Hackers are driven by a sense of responsibility and a genuine passion for Cybersecurity. They use their skills to protect sensitive information and prevent cyber-attacks.
Legality and authorisation
Hacking, being unauthorised and illegal, carries severe legal consequences. Perpetrators can face criminal charges, fines, and imprisonment for their actions. Ethical Hacking, conversely, operates within the boundaries of the law. Ethical Hackers receive explicit permission from system owners to assess and test the security of computer systems. This authorisation ensures that Ethical Hacking activities are conducted responsibly and ethically, differentiating them from illegal Hacking attempts.
Want to learn Cybersecurity skills and safeguard your digital assets? Register now for our Ethical Hacking Training!
Methodologies and techniques
Hacking employs an arsenal of tools and techniques to exploit vulnerabilities. Malicious Hackers use Hacking tools, malware, and social engineering tactics to gain unauthorised access. They exploit weaknesses in software, hardware, or human behaviour, often employing techniques like phishing, ransomware attacks, and Distributed Denial of Service (DDoS) attacks.
Ethical Hackers, on the other hand, employ similar tools and techniques but with a fundamentally different objective. They use their expertise to conduct Penetration Testing, vulnerability assessments, and security audits. Ethical Hacking methodologies involve simulating real-world cyber-attacks within a controlled environment. This allows Ethical Hackers to identify vulnerabilities, assess the effectiveness of security measures, and provide recommendations for strengthening defences.
Impact and consequences
The impact of Hacking can be catastrophic, leading to financial losses, compromised sensitive information, legal consequences, and reputational damage. Hacking incidents can erode trust between businesses and their customers, resulting in long-term effects on an organisation's bottom line and market standing. Individuals can suffer identity theft, loss of personal data, and emotional distress due to Hacking attacks.
In contrast, Ethical Hacking aims to prevent such adverse outcomes. By proactively identifying vulnerabilities, Ethical Hackers enable organisations to patch security holes, strengthen their defences, and mitigate the risk of cyber-attacks. Ethical Hacking exercises contribute to the overall Cybersecurity posture of businesses, ensuring that customer data remains secure and that organisations can maintain their reputation and trustworthiness.
Skills and knowledge
Hacking demands a deep understanding of coding, network protocols, system vulnerabilities, and various Hacking tools. Malicious Hackers often possess advanced technical skills to exploit complex security weaknesses. They constantly adapt to new technologies and security measures, seeking ways to bypass defences and gain unauthorised access.
Ethical Hackers, too, possess a high level of technical expertise. However, their skills are channelled toward moral pursuits. Ethical Hackers are proficient in Cybersecurity tools, programming languages, and legal frameworks related to digital security. They stay abreast of the latest Cybersecurity trends and vulnerabilities, ensuring they are well-equipped to identify and address emerging threats effectively.
Advance your career in Cybersecurity with our Ethical Hacking Professional Training. Sign up now!
Authorisation and scope
Hacking attacks occur without any form of authorisation from the targeted entities. Perpetrators exploit vulnerabilities wherever they find them, regardless of the ownership or legal implications. These attacks can be random or specifically targeted, aiming at individuals, businesses, or even governments. The lack of authorisation differentiates Hacking from Ethical Hacking, making unauthorised intrusion a criminal act.
Ethical Hacking, conversely, is conducted within a defined scope and with explicit permission. Organisations hire Ethical Hackers or Cybersecurity firms to assess the security of their systems, networks, or applications. The scope of Ethical Hacking engagements is predetermined and agreed upon by both parties. Ethical Hackers adhere strictly to the agreed-upon scope, ensuring that their assessments are focused, comprehensive, and conducted in a controlled manner.
Ethical Hacking vs Hacking: Real-life examples
Real-life incidents vividly illustrate the contrasting impact of Ethical Hacking and malicious Hacking on individuals, organisations, and society. For example, the notorious case of the 2017 Equifax breach stands out as an example of Hacking. In this malicious Hacking incident, cybercriminals exploited a vulnerability in Equifax's web application, compromising the sensitive personal data of nearly 147 million individuals. The consequences were dire, leading to financial losses, identity theft, and widespread panic among affected consumers.
In contrast, Ethical Hacking has saved organisations from similar fates. The case of Kevin Mitnick, once a notorious black-hat hacker turned white-hat consultant, exemplifies this transformation. After serving prison time for his malicious Hacking activities, Mitnick became an Ethical Hacker, assisting companies in bolstering their security measures. His expertise helped corporations identify vulnerabilities before malicious Hackers could exploit them, preventing potential disasters and financial losses.
Conclusion
We hope that this blog has helped you understand the Difference Between Hacking and Ethical Hacking. These distinctions will help organisations and businesses to protect their data from malicious intent, thereby improving the Cybersecurity of the organisation.
Elevate your Cybersecurity skills with our course on Mastering Metasploit Framework. Join now!







 Top Rated Course
Top Rated Course



 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


