We may not have the course you’re looking for. If you enquire or give us a call on 01344203999 and speak to our training experts, we may still be able to help with your training requirements.
We ensure quality, budget-alignment, and timely delivery by our expert instructors.

The threat of a Domain Name System (DNS) Flood attack is significant, underscoring the critical importance of Cybersecurity. As organisations and individuals rely heavily on the DNS for online activities, understanding and defending against DNS Flood attacks is vital.
Moreover, malicious actors leverage botnets to overpower DNS Servers with a deluge of fake queries, aiming to overwhelm and disrupt the target's DNS infrastructure. In a DNS Flood attack, the hacker targets one or more DNS Servers that are a member of a certain zone to prevent resource entries. Read more!
Table of Contents
1) Understanding What is DNS Flood
2) A look at how the DNS Flood Attack works
3) Methods to mitigate a DNS Flood Attack
4) Conclusion
Understanding What is DNS Flood
A DNS Flood is a type of cyberattack that targets the Domain Name System, a critical component of the internet infrastructure. The DNS is responsible for translating human-readable domain names, like www.example.com, into the corresponding IP addresses that computers use to locate websites and services.
Additionally, in a DNS Flood attack, malicious actors attempt to overwhelm a DNS Server or network with an excessive volume of DNS queries. These queries are typically generated by a botnet, a network of compromised computers under the attacker's control.
Now, to amplify the attack, the attacker often employs DNS amplification techniques, where a small query generates a disproportionately large response from open DNS resolvers. Moreover, the primary objective of a DNS Flood attack is to disrupt the target's DNS services, causing them to become slow or completely unavailable.
This can result in service outages, downtime, and significant inconvenience for users. DNS Flood attacks are a concern for organisations and individuals alike, highlighting the importance of robust cybersecurity measures to mitigate such threats.
A look at how the DNS Flood Attack works
A DNS Flood attack is a malicious assault on the DNS infrastructure, exploiting its fundamental components to overwhelm targeted systems. Here's how it works:
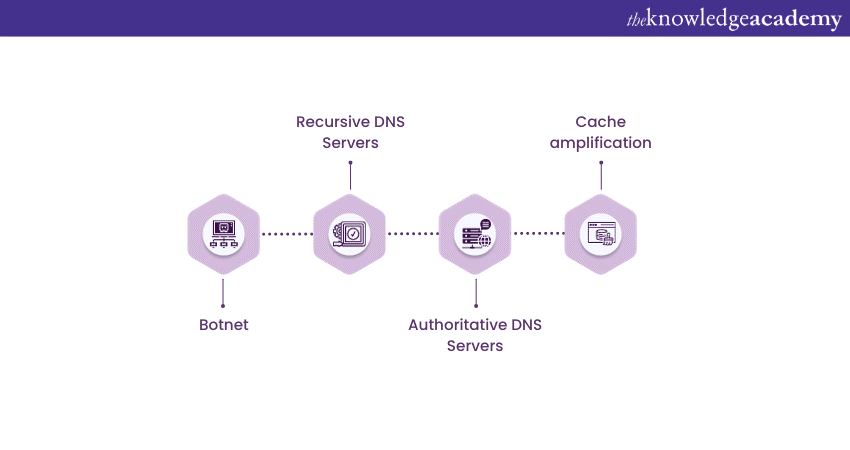
Botnet
Attackers often control a network of compromised computers, known as a botnet, to carry out DNS Flood attacks. These bots can number in the thousands or more, enabling a coordinated attack.
Recursive DNS Servers
The attacker's bots send a barrage of DNS queries to open or misconfigured Recursive DNS Servers. These servers are responsible for resolving DNS queries by looking up information in the DNS hierarchy. Attackers use forged source IP addresses to make it appear as though the requests are coming from legitimate sources.
Authoritative DNS Servers
Recursive DNS Servers, unable to fulfil the massive volume of DNS queries, need to contact Authoritative DNS Servers to resolve the requested domain names. The attackers manipulate this step by directing the requests towards the target's Authoritative DNS Servers.
Cache amplification
Here's where the amplification factor comes into play. Authoritative DNS Servers often store recently resolved queries in their cache to speed up future requests. The attackers' queries generate large responses, which get stored in the cache. This amplifies the attack as the victim's server is forced to process and store these large responses.
Prevent system intrusions by signing up for Introduction to System and Network Security Training now!
Methods to mitigate a DNS Flood attack
Mitigating a DNS Flood attack is crucial to maintaining the stability and availability of online services. Several methods can be adopted to defend against such attacks:

a) Rate limiting: Implement rate-limiting rules on your DNS Servers to restrict the number of incoming queries per second. This can help prevent overwhelming traffic spikes associated with DNS Flood attacks.
b) Anycast DNS: Distribute your DNS infrastructure across multiple geographically dispersed locations using Anycast. This spreads the load and ensures redundancy, making it more challenging for attackers to pinpoint a single target.
c) Traffic filtering: Employ traffic filtering techniques, such as Access Control Lists (ACLs) and firewall rules, to block traffic from suspicious or untrusted sources. This can help filter out malicious queries.
d) DNS traffic monitoring: Continuously monitor DNS traffic for anomalies and patterns that indicate an ongoing attack. Intrusion Detection Systems (IDS) and anomaly detection tools can aid in early detection.
e) Use of Content Delivery Networks (CDNs): CDN services can absorb and mitigate DNS Flood traffic by distributing it across their vast network infrastructure, reducing the impact on your own servers.
f) Load balancing: Employ load balancers to distribute DNS queries evenly across multiple servers. This can help prevent overloading a single DNS Server and ensure high availability.
g) DNS Security Extensions (DNSSEC): Implement DNSSEC to authenticate DNS responses, reducing the risk of forged or malicious DNS data.
h) Regular patching and updates: Keep your DNS Server software and operating system up to date to patch known vulnerabilities and enhance security.
i) Cloud-based DDoS protection services: Consider using cloud-based DDoS protection services that specialise in mitigating DNS Flood Attacks. These services can scrub incoming traffic and only allow legitimate queries to reach your DNS infrastructure.
Conclusion
Safeguarding against DNS Flood attacks is imperative for the uninterrupted functionality of online services. Employing a combination of rate limiting, traffic filtering, and DNSSEC, among other strategies, is essential to protect against the ever-evolving threat landscape posed by DNS Flood attacks.
Protect your organisation against cyber-attacks by signing up for our Cyber Security Training now!
Upcoming IT Infrastructure & Networking Resources Batches & Dates
Date
 BIND DNS Administration Training
BIND DNS Administration Training
Fri 16th May 2025
Fri 18th Jul 2025
Fri 19th Sep 2025
Fri 21st Nov 2025






 Top Rated Course
Top Rated Course



 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


