We may not have the course you’re looking for. If you enquire or give us a call on 01344203999 and speak to our training experts, we may still be able to help with your training requirements.
We ensure quality, budget-alignment, and timely delivery by our expert instructors.

DNS Hijacking, the malicious art of redirecting internet traffic to fraudulent destinations, threatens our security and privacy. To navigate the digital domain safely, it is imperative to understand the inner workings of DNS Hijacking, its varied forms, and the means to defend against it.
This blog explores DNS Hijacking and equip you with the knowledge needed to protect our online presence. DNS Hijacking is a sort of cyberattack. It involves a hacker intercepting DNS requests from a browser and diverting them to another IP address. Read more!
Table of Contents
1) What is DNS Hijacking?
2) How DNS works?
3) Types of DNS Hijacking
4) Signs of DNS Hijacking
5) Common targets of DNS Hijacking
6) Preventing DNS Hijacking
7) Responding to DNS Hijacking
8) Conclusion
What is DNS Hijacking?
DNS Hijacking is a malicious practice that involves manipulating the Domain Name System (DNS) to redirect users to fraudulent websites or compromise the integrity of internet communications. This type of DNS Attack occurs when cybercriminals exploit vulnerabilities in the DNS infrastructure to alter DNS records, leading to various adverse consequences.
To understand it better, let us break down its key components:
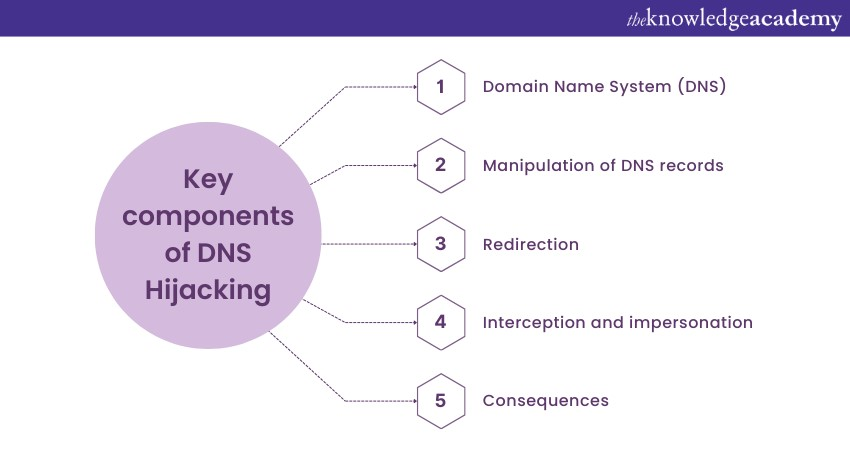
a) Domain Name System (DNS): DNS is the decentralised hierarchical system that solves human-readable field names into the numerical IP addresses that computers use to discover and convey with each other on the internet. DNS serves as the internet's address book, ensuring that when you type a web address into your browser, your device knows which server to contact to retrieve the requested web page.
b) Manipulation of DNS records: DNS hijacking occurs when unauthorised parties manipulate the DNS records associated with a specific domain. These DNS records, stored on authoritative DNS servers, contain information like IP addresses and other essential data for directing internet traffic to the correct destinations.
c) Redirection: The primary goal is to redirect users to alternative, often malicious, destinations. Attackers alter DNS records to replace legitimate IP addresses with their own, redirecting users to fraudulent websites or servers controlled by the attackers.
d) Interception and impersonation: In some cases, DNS hijacking involves intercepting and impersonating legitimate DNS servers. This can lead to "man-in-the-middle" attacks, where the attacker eavesdrops on or modifies communication between the user and the intended server, potentially leading to data theft or other malicious activities.
e) Consequences: DNS hijacking can have various effects, depending on the attacker's intentions. These may include phishing attacks aimed at stealing login credentials or financial information, spreading malware, redirecting traffic to fake websites, altering website content, or even performing espionage activities.
How DNS works?
Understanding how DNS (Domain Name System) works is crucial for grasping the concept of DNS hijacking and its implications. DNS is essentially the internet's phone book, translating human-friendly domain names into IP addresses that desktops locate and communicate with one another. Let us explore the workings of DNS in more detail:
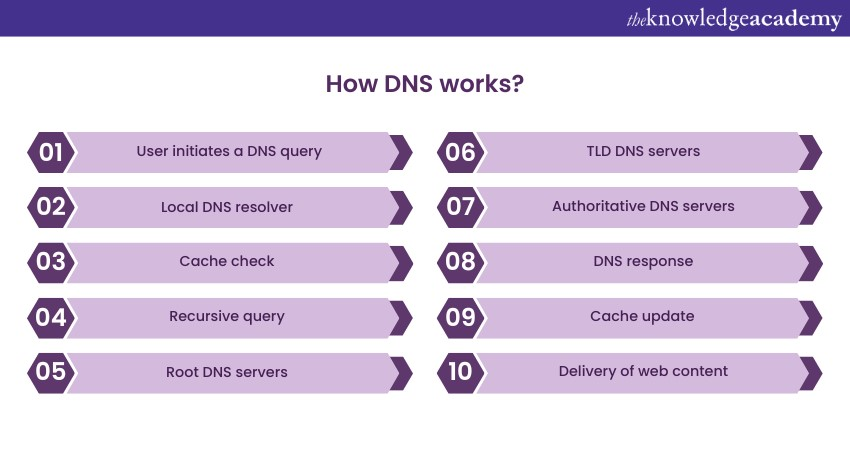
a) User initiates a DNS query: When a user enters a URL into their web browser and press Enter, their device must find the IP address associated with that domain to establish a connection.
b) Local DNS resolver: Your device, typically a computer or smartphone, sends a DNS query to a local DNS resolver, often provided by your internet service provider (ISP). The local resolver is responsible for handling DNS requests from your device.
c) Cache check: The local DNS resolver checks its cache, which stores recently resolved domain-to-IP mappings. The resolver can return the corresponding IP address immediately if the requested domain is in stock. This caching mechanism helps improve DNS query response times and reduce network traffic.
d) Recursive query: The local resolver initiates a recursive DNS query if the domain is not in the cache or has expired. This involves a series of requests to multiple DNS servers to resolve the field.
e) Root DNS servers: The root DNS servers are the first stop in the recursive query process. These servers maintain a list of authoritative DNS servers for all top-level domains (TLDs) like .com, .org, .net, etc.
f) TLD DNS servers: The root DNS servers direct the question to the proper TLD DNS server based on the TLD of the requested domain (e.g., .com). TLD DNS servers maintain information about the authoritative DNS servers for second-level domains (e.g., example.com).
g) Authoritative DNS servers: The TLD DNS server directs the query to the traditional DNS server for the requested domain (e.g., example.com). In the DHCP vs DNS context, while DNS manages domain name resolution, authoritative DNS servers specifically store DNS records for different components, including the IP address assigned within the environment.
h) DNS response: The authoritative DNS server provides the IP address of the requested domain back to the local DNS resolver.
i) Cache update: The local resolver stores this IP address in its cache for future use, ensuring quicker access to the same domain if requested again.
j) Delivery of web content: With the IP address in hand, your device can now connect to the web server associated with the domain. It retrieves the requested web content, and you see the website in your browser.
This complex, hierarchical system ensures the efficient and accurate resolution of domain names to IP addresses across the internet. It is designed to handle many DNS queries daily and ensure users can access websites and online services using human-readable domain names.
Types of DNS Hijacking
DNS hijacking is a broad term encompassing various techniques and methods cybercriminals employ to manipulate or compromise the Domain Name System (DNS). Understanding the different types of DNS hijacking is crucial for identifying and mitigating these attacks. Here are some of the common types seen:
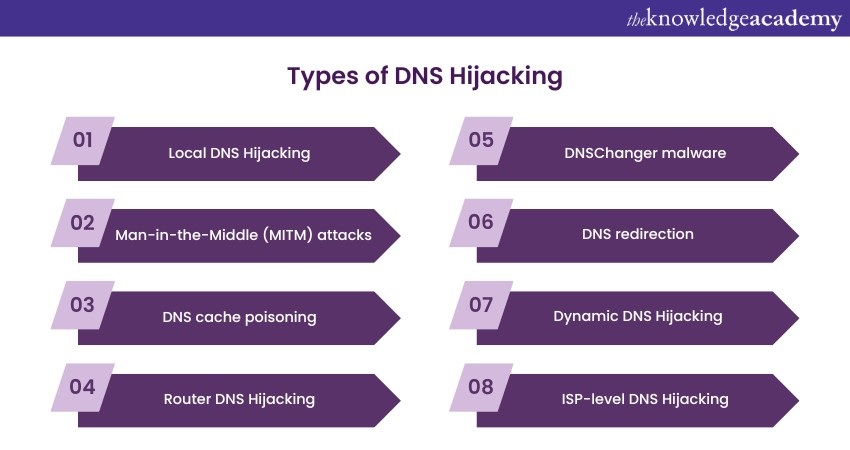
a) Local DNS Hijacking: In this, an attacker compromises the DNS settings on an individual device or within a local network. This manipulation leads to DNS queries being redirected to a malicious DNS server controlled by the attacker. Users within the affected network are then directed to fake websites, potentially exposing them to phishing scams or malware.
b) Man-in-the-Middle (MITM) attacks: MITM attacks involve intercepting communication between a user and a legitimate DNS server. Attackers position themselves between the user and the DNS server and manipulate DNS responses in real time. This allows them to redirect users to malicious websites or capture sensitive information exchanged during the communication.
c) DNS cache poisoning: It is a technique in which an attacker injects malicious DNS data into the cache of a DNS resolver. When the resolver responds to DNS queries, it provides the wrong IP addresses, leading users to malicious websites. Cache poisoning can have widespread effects as it affects the DNS resolver, potentially impacting all users relying on it.
d) Router DNS Hijacking: In it, attackers compromise the settings of routers within a network. They modify the DNS server settings on the router, forcing all devices connected to it to use malicious DNS servers. This type of hijacking can affect an entire network, making it a valuable target for attackers looking to redirect traffic for various purposes.
e) DNSChanger malware: DNSChanger is notorious for changing DNS settings on infected devices. Once installed, it reroutes DNS queries to malicious servers under the attacker's control. DNSChanger has been responsible for large-scale DNS hijacking incidents, impacting thousands of users.
f) DNS redirection: DNS redirection involves altering DNS records to point legitimate domain names to malicious IP addresses. Users who attempt to visit the affected domains are unknowingly redirected to fake websites, which can be used for phishing, distributing malware, or stealing credentials.
g) Dynamic DNS Hijacking: Dynamic DNS (DDNS) is a service that allows users to map dynamic (changing) IP addresses to a static domain name. Attackers may hijack DDNS accounts to update the DNS records with malicious IP addresses, redirecting traffic to their controlled servers.
h) ISP-level DNS Hijacking: Some Internet Service Providers (ISPs) have hijacked DNS for various reasons, such as injecting ads or error pages into web traffic. While this is typically not malicious in intent, it can still interfere with the intended user's experience.
DNS hijacking can have severe consequences, including data theft, malware distribution, financial losses, and reputational damage. To mitigate these risks, individuals and organisations must implement robust security measures, regularly update DNS settings and software, and stay vigilant for signs of DNS manipulation.
Using DNSSEC (DNS Security Extensions) can protect against DNS hijacking attacks by digitally signing DNS records to verify their authenticity.
Ready to become a master of BIND DNS Administration? Gain the skills and knowledge you need to excel in DNS administration and take your IT career to new heights.
Signs of DNS Hijacking
Detecting hijacking is crucial for online security. Signs include unexpected redirects to unfamiliar websites, SSL certificate errors indicating potential man-in-the-middle attacks, slow website loading due to added redirection steps, incredible ads or pop-ups injected into pages, inconsistent resolution of specific websites, difficulty accessing sites, multiple devices experiencing issues simultaneously, and unusual network traffic patterns.
If you suspect DNS hijacking, investigate by checking DNS settings, clearing DNS caches, and considering DNSSEC. Report incidents to your ISP or authorities to address the issue and prevent further attacks. Staying vigilant for these signs can help protect against the potentially severe consequences of DNS hijacking, including data theft and malware distribution.
Common targets of DNS Hijacking
DNS hijacking is a cyberattack targeting various entities, including individuals, businesses, government entities, and critical infrastructure. The reasons for these attacks can range from financial gain to espionage and censorship. Here is an expanded look at common targets of DNS hijacking:
a) Popular websites: Attackers often target well-known and widely visited websites. By compromising the DNS records of these sites, they can redirect many users to malicious or fraudulent pages. Such attacks can tarnish the reputation of popular websites and expose users to various risks, including phishing scams and malware downloads.
b) Government entities: Government agencies and departments can be targeted for DNS hijacking to gain unauthorised access to sensitive data or to control the flow of information. These attacks can be politically motivated and aim to disrupt government operations or surveil communications.
c) Financial institutions: Banks and other financial organisations are lucrative targets for DNS hijacking. Attackers may redirect users to fake banking websites that steal login credentials and financial information. This can result in substantial economic losses for both individuals and institutions.
d) Large corporations: Large corporations, especially those involved in technology, finance, or critical industries, may be targeted for industrial espionage. DNS hijacking can lead to data breaches, unauthorised access to proprietary information, and damage to a company's reputation.
e) E-commerce platforms: Online retailers and e-commerce platforms are attractive targets for DNS hijacking, as they handle financial transactions and store personal information. Attackers may redirect users to counterfeit websites to steal payment card data and personal details.
Ready to shine in your DNS interview? Explore the best DNS Interview Questions and Answers to help you prepare confidently.
Preventing DNS Hijacking
Preventing DNS hijacking is crucial for safeguarding the integrity of the Domain Name System (DNS) and protecting against the various cyber threats associated with these attacks. Here are several strategies and best practices to prevent DNS hijacking:
a) Implement DNS Security Extensions (DNSSEC): DNSSEC is a suite of security protocols designed to add a layer of security to DNS. It digitally signs DNS records, enabling the verification of their authenticity. When DNS records are marked with DNSSEC, it becomes much more difficult for attackers to manipulate or forge DNS responses. Implementing DNSSEC is a highly effective way to prevent DNS hijacking.
b) Use reputable DNS servers: Choose DNS servers provided by reputable organizations, such as your Internet Service Provider (ISP) or well-known DNS hosting providers, as they are more likely to have robust security measures to prevent DNS hijacking and mitigate threats like DNS Fast Flux. Additionally, consider using DNS-over-HTTPS (DoH) or DNS-over-TLS (DoT) to encrypt your DNS queries and responses, enhancing protection against malicious redirections.
c) Regularly update router firmware: Ensure that the firmware of your routers and networking equipment is up to date. Manufacturers often release updates that address vulnerabilities attackers could exploit to manipulate DNS settings. Regularly scanning for firmware updates and using them promptly is vital.
d) Enable router security features: Many routers offer features like DNS filtering, which can help protect against DNS hijacking. Configure your router to use DNS filtering services or security features to detect and block malicious DNS traffic.
e) Use strong authentication: Implement robust authentication methods for your DNS management accounts, including complex passwords and two-factor authentication (2FA). It decreases the chance of unauthorised access to your DNS settings, which attackers often exploit during DNS hijacking.
Register now and unlock a world of opportunities in the IT industry with IT Support and Solution Training.
Responding to DNS Hijacking
Responding to DNS hijacking requires a well-orchestrated and swift approach to mitigate potential risks and restore the integrity of your DNS infrastructure. Begin by verifying the DNS settings on your devices and network equipment, ensuring they haven't been tampered with.
Clear the DNS cache on your devices to eliminate any potentially malicious entries and promptly change passwords for critical accounts, especially DNS management and router credentials, to prevent unauthorised access.
Conduct thorough malware scans using reputable antivirus and anti-malware software, as malware often facilitates DNS hijacking. Verify the digital signatures on DNS records if you have implemented DNSSEC, a security protocol that helps ensure DNS response authenticity.
Reporting the happening to your Internet Service Provider (ISP) or network administrator is essential, as they can aid in analysing and fixing the issue. Continuously monitor network traffic, implement robust security measures, and document the incident for future reference. Swift and comprehensive responses to DNS hijacking are crucial for containing other damage and maintaining a secure online presence.
Conclusion
After exploring DNS Hijacking, it is clear that vigilance is essential to defend against this threat. Whether targeting individuals, businesses, or critical infrastructure, DNS Hijacking poses significant risks.
Implementing DNSSEC, using reputable DNS servers, and monitoring networks can enhance online security. We can prevent DNS Hijacking from threatening us by staying informed and vigilant.
Ready to kickstart your IT career with a solid foundation? Register for our IT Fundamentals Training.
Upcoming IT Infrastructure & Networking Resources Batches & Dates
Date
 BIND DNS Administration Training
BIND DNS Administration Training
Fri 16th May 2025
Fri 18th Jul 2025
Fri 19th Sep 2025
Fri 21st Nov 2025






 Top Rated Course
Top Rated Course



 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


