We may not have the course you’re looking for. If you enquire or give us a call on 01344203999 and speak to our training experts, we may still be able to help with your training requirements.
We ensure quality, budget-alignment, and timely delivery by our expert instructors.

In the vast digital universe, where cyber threats orbit every corner of your business galaxy, mastering Information Security Risk Management becomes the gravitational force that keeps your world intact. This blog is a beacon for business leaders navigating through the nebula of digital risks, offering clarity and direction in a complex field.
It's not just about defence but about building a resilient infrastructure that supports your mission while safeguarding your digital frontiers. Are you ready to command your Cyber Jedi Order? Or are you a hitchhiker needing a blog to the galaxies of information security, read along to find your way.
Table of Contents:
1) Understanding Information Security Risk Management (ISRM)
2) Identifying risks to information systems
3) Importance of Information Security Risk Management
4) What is a Risk Management framework?
5) Stages of ISRM
6) Roles in Information Security Risk Management ownership
7) Conclusion
Understanding Information Security Risk Management (ISRM)
The ISRM acts as a shield against cyber attacks. The program is almost an integral part of your business and is designed to keep hackers at bay at all times, protecting and preserving its most precious data. It goes beyond conventional IT security, emphasising an integrated strategy that will complement the organisation’s objectives and risk appetite. Through ISRM, executive managers will be able to foresee, assess, and react to information security risks to create a “resilience culture”.
Identifying Risks to Information systems
Information Security Risk Management begins with the identification of risks that may lead to the compromising of information infrastructure. This step consists of complete study of both internal and external digital environments to discover problematic places in your software, hardware, and processes platforms. It is a crafted compilation that meticulously covers each and every possible point of failure, from unauthorised entry to information leaks, and thus ensures there is no error left unattended in securing your digital realm.
Importance of Information Security Risk Management
The significance of ISRM cannot be merely underlined, it must be emphasised in the most prominent manner possible. It is the base principal of the survival of your organisation in the digital era. Robust Information Security Risk Management (ISRM) policy is an efficient tool to combat the threat of damaged data leaks and cyber-attacks and ensures that all regulatory requirements are met, customer confidence is improved, and ultimately, the entity's reputation is enhanced. Therefore, it is fundamental to the continuity of your company development - the secure, controlled environment which will provide the basis for growth and innovation.
Learn to manage your company’s Systems Security, with our Information Systems Security Management Training- Sign up now!
What is a Risk Management Framework?
The Risk Management Framework (RMF) is the blueprint that governs the operations of Information Security Risk Management. It gives an organisation a set of steps for handling risk identification, risk assessment, risk response and risk monitoring in a systemic, structured manner. The RMF effectiveness is determined by the organisation’s unique requirements, integrating well with its risk management philosophy and the business strategy, making sure that information security risks are properly handled, consistently, efficiently, and comprehensively.
Stages of ISRM
ISRM is a program carried out in several stages, for a better understanding they have been categorised in five stages and explained below.
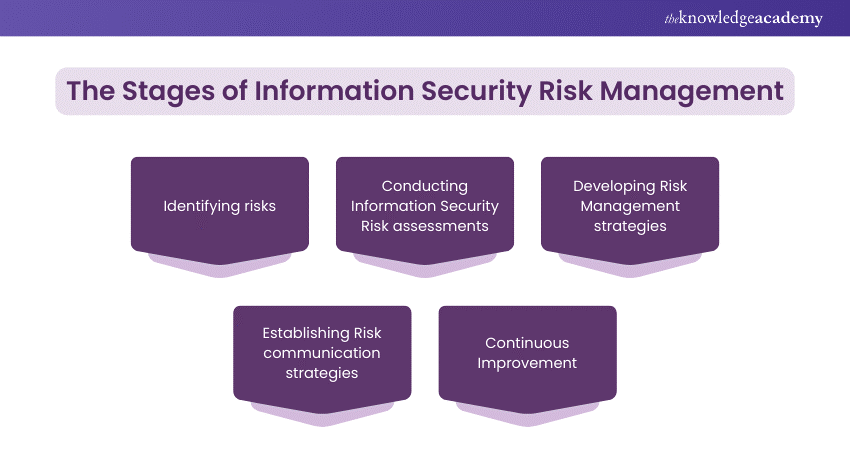
1) Identifying risks
This first phase involving a detailed analysis of the organisation's information assets and the various threats they could possibly face, establishing a clear understanding of the potential risks.
2) Conducting Information Security Risk assessments
Assessments quantify or qualify the potential impact and likelihood of identified risks, prioritising them based on their severity and the vulnerability of affected asse
3) Developing Risk Management strategies
With a clear understanding of the risks, strategies are formulated to address them. This may involve implementing specific security measures, altering business processes, or accepting certain risks based on a cost-benefit analysis.
4) Establishing Risk communication strategies
Communication is vital to ISRM. It ensures that all stakeholders are informed about the risks and the rationale behind the chosen mitigation strategies, fostering a culture of security awareness.
5) Continuous Improvement
Given the dynamic nature of cyber threats, ISRM demands ongoing evaluation and adaptation. Continuous improvement processes ensure that the organisation's risk management strategies evolve in line with new threats and business changes.
Become a pro at Cloud Security, with our CCSP Certified Cloud Security Professional Course -Sign up now!
Roles in Information Security Risk Management Ownership
To prevent the company’s data from cyber-attacks there is a small army of cyber soldiers, but soldiers need a commander, a form of management that gives them direction. Here are three significant roles Information Security Risk Management Ownership:
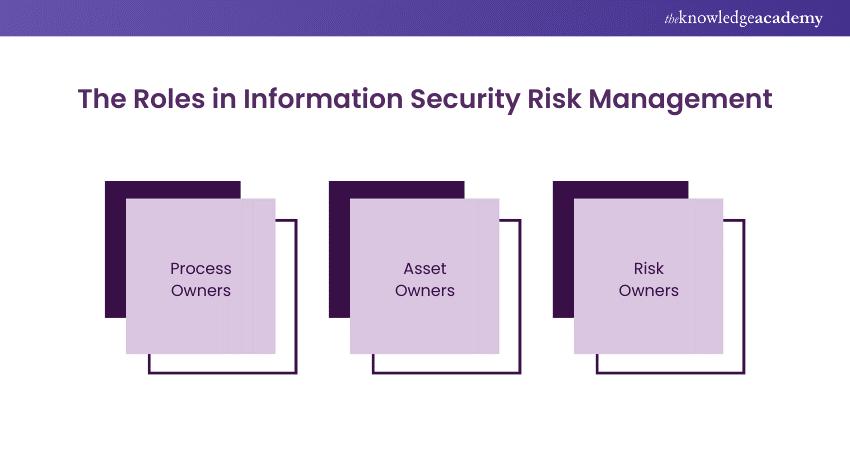
1) Process Owners
Individuals or teams responsible for managing and securing specific business processes, aligning their operations with overarching ISRM policies and goals.
2) Asset Owners
Designated guardians of specific assets tasked with ensuring the security and resilience of these resources against information security risks.
3) Risk Owners
Key players oversee the management of specific risks, from identification to mitigation, ensuring that risks are kept within acceptable limits.
Conclusion
The blog navigated through the complexities of Information Security Risk Management, a vital mission for today's business leaders. Armed with the insights from this blog, you're prepared to lead your organisation through the digital wilderness, securing your assets against the unknown.
Embrace Information Security Risk Management not just as a necessity but as a strategic advantage, enabling your business to thrive in the cyber age. With this new information, we wish you a safe journey through the universe of Information Security, hoping you are equipped with the skill to manage all risks that come your way.
Become a Chief Information Security Officer. Sign up for our Chief Information Security Officer Training - Register Now!
Frequently Asked Questions
How can I ensure my ISRM strategies remain effective over time?

Regularly review and update your ISRM strategies to reflect new cyber threats, technological advancements, and changes in business operations. Incorporating feedback from ongoing monitoring and assessment activities ensures your approach adapts to the evolving digital landscape.
Are there affordable ISRM solutions for startups and small businesses?

There are scalable ISRM solutions suitable for businesses of all sizes. Startups and small businesses can focus on core principles and implement cost-effective measures tailored to their specific risks and resources. Utilising open-source tools, prioritising critical assets for protection, and fostering a culture of security awareness among employees can be highly effective strategies.
What are the other resources and offers provided by The Knowledge Academy?

The Knowledge Academy takes global learning to new heights, offering over 3,000 online courses across 490+ locations in 190+ countries. This expansive reach ensures accessibility and convenience for learners worldwide.
Alongside our diverse Online Course Catalogue, encompassing 19 major categories, we go the extra mile by providing a plethora of free educational Online Resources like News updates, Blogs, videos, webinars, and interview questions. Tailoring learning experiences further, professionals can maximise value with customisable Course Bundles of TKA.
What is the Knowledge Pass, and how does it work?

The Knowledge Academy’s Knowledge Pass, a prepaid voucher, adds another layer of flexibility, allowing course bookings over a 12-month period. Join us on a journey where education knows no bounds.
What are related Courses and blogs provided by The Knowledge Academy?

The Knowledge Academy offers various CISM Training, including Certified Information Security Manager (CISM) Training Course, Certified Data Protection Officer (CDPO) course and Certified in Risk and Information Systems Control (CRISC) courses. These courses cater to different skill levels, providing comprehensive insights into CISM or CRISC: A Complete Comparision
Our IT Security & Data Protection Blogs covers a range of topics offering valuable resources, best practices, and industry insights. Whether you are a beginner or looking to advance your Business Improvement skills, The Knowledge Academy's diverse courses and informative blogs have you covered.
Upcoming IT Security & Data Protection Resources Batches & Dates
Date
 CISM Certified Information Security Manager
CISM Certified Information Security Manager
Mon 3rd Mar 2025
Sat 8th Mar 2025, Sun 9th Mar 2025
Sat 5th Apr 2025, Sun 6th Apr 2025
Mon 14th Apr 2025
Sat 3rd May 2025, Sun 4th May 2025
Tue 6th May 2025
Mon 2nd Jun 2025
Sat 7th Jun 2025, Sun 8th Jun 2025
Sat 5th Jul 2025, Sun 6th Jul 2025
Mon 7th Jul 2025
Sat 2nd Aug 2025, Sun 3rd Aug 2025
Mon 4th Aug 2025
Mon 1st Sep 2025
Sat 6th Sep 2025, Sun 7th Sep 2025
Sat 4th Oct 2025, Sun 5th Oct 2025
Mon 6th Oct 2025
Mon 3rd Nov 2025
Sat 8th Nov 2025, Sun 9th Nov 2025
Mon 1st Dec 2025
Sat 6th Dec 2025, Sun 7th Dec 2025






 Top Rated Course
Top Rated Course



 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


