We may not have the course you’re looking for. If you enquire or give us a call on 01344203999 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.

Confidential organisational data ending up in the wrong hands is the ultimate nightmare for a company and the industry as a whole. But here's the good news - for every path a Cyber attacker finds to drill into your private data, a gateway for enhanced security opens up! Such a gateway is precisely what the ISO 27001 framework and its access control policy unlocks.
But what does it take to craft a foolproof ISO 27001 Access Control Policy? That's what this blog explores, detailing how it handles critical elements including authorisation and authentication. Read on and fortify your organisation's sensitive information with ease and confidence!
Table of contents
1) What is ISO 27001?
2) What is Access Control?
3) How to Build an Access Control Policy?
4) Implementing, Monitoring, and Reviewing Access Control Policy
5) Conclusion
What is ISO 27001?
ISO 27001 Framework is a global benchmark that establishes guidelines for the development, execution, and continuous upkeep of an Information Security Management System (ISMS) within a company. It is a blueprint for protecting sensitive data and managing Information Security risks. It aids organisations in recognising potential threats, integrating ISO 27001 controls for security, and perpetually enhancing security measures.
There are plenty of Benefits of ISO 27001 Compliance that sets the path safeguarding confidential information, ensuring legal and regulatory, and building trust with customers and partners. It's a comprehensive framework that helps organisations of all sizes and types fortify their defences in the ever-evolving world of cybersecurity.
What is Access Control?
Access Control is a security protocol designed to ascertain which individuals or entities can enter, utilise, or view resources or areas within an organisation's digital infrastructure or physical facilities. Its primary objective is to grant access exclusively to authorised parties while preventing unauthorised users from gaining entry.

Access Control mechanisms include user authentication (e.g., usernames and passwords), biometrics (like fingerprint or facial recognition), and Role-Based Access Control (RBAC), which assigns permissions based on a user's role in an organisation. Access Control is essential for protecting sensitive data, maintaining confidentiality, preventing unauthorised actions, and ensuring overall security in digital and physical environments.
Elevate your cybersecurity knowledge with our ISO 27001 Courses today!
How to Build an Access Control Policy?
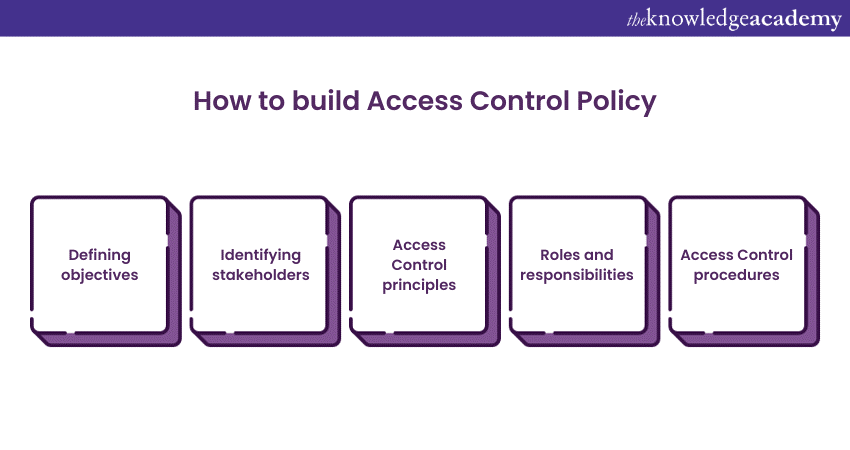
Creating an Access Control policy is crucial in safeguarding your organisation's sensitive information and achieving ISO 27001 compliance. We will explore critical aspects of constructing an effective Access Control policy:
a) Defining Objectives: Start by clearly defining the purposes of your Access Control policy. Are you aiming to protect sensitive data, ensure regulatory compliance, or prevent unauthorised access? Setting specific goals will guide your policy development process.
b) Identifying Stakeholders: Determine the key stakeholders in crafting and enforcing the policy. These may include IT teams, security professionals, HR, and legal departments. Collaboration with these stakeholders ensures comprehensive coverage and helps garner policy implementation support.
c) Access Control Principles: Establish the foundational principles that your Access Control policy will be built upon. These principles should cover critical elements such as authentication, authorisation, least privilege, segregation of duties, and continuous monitoring. Ensure that these principles align with ISO 27001 standards.

d) Roles and Responsibilities: Provide an overview of the duties and obligations of individuals or groups participating in Access Control. Specify who can grant, modify, or revoke access rights and who is responsible for ISO 27001 audit and monitoring access. This clarity ensures accountability within your organisation.
e) Access Control Procedures: Detail the specific guidelines for granting and revoking access, managing passwords, and provisioning user accounts. Consider leveraging automation to streamline these processes, making them more efficient and less error prone.
Take the lead in safeguarding information with ISO 27001 Lead Auditor– Secure your future today!
Implementing, Monitoring, and Reviewing Access Control Policy
Implementing, monitoring, and reviewing an Access Control policy is important for ensuring the security and compliance of an organisation's information assets.
a) Implementation involves putting the documented procedures into action, which includes configuring ISO 27001 Physical Security settings, providing training to personnel, and maintaining compliance records. It's vital to instil a culture of security awareness.
b) Monitoring encompasses continuous surveillance of user activities and access logs in real time. This proactive approach helps identify and respond to security threats promptly. An incident response plan should also be in place to handle breaches effectively.
c) Reviewing is an ongoing process that includes scheduled policy reviews, access reviews, and documentation updates. Regularly assess the policy's alignment with evolving organisational needs and changes in technology or regulations.
Enhance your organisation's security posture with ISO 27001 Internal Auditor – Join now!
Conclusion
Understanding and implementing an ISO 27001 Access Control Policy is pivotal in today's digital landscape. It serves as a shield for safeguarding sensitive data, ensuring compliance, and fortifying an organisation's cybersecurity posture. As the global shift toward Information Security intensifies, adhering to ISO 27001 standards not only protects against threats but also builds trust with stakeholders.
Take the first step towards cybersecurity excellence – Join our ISO 27001 Foundation now!
Frequently Asked Questions

The common challenges include:
a) Distributed IT systems scattered across multiple geographical locations
b) Policy management
c) Excessive permissions and exceptions
d) Continuous monitoring and reporting
e) Choosing the right access control models

Physical access control uses keys and badges and limits access to buildings, rooms and IT assets. Logical access control limits system files, computer networks, and data connections.

The Knowledge Academy takes global learning to new heights, offering over 30,000 online courses across 490+ locations in 220 countries. This expansive reach ensures accessibility and convenience for learners worldwide.
Alongside our diverse Online Course Catalogue, encompassing 19 major categories, we go the extra mile by providing a plethora of free educational Online Resources like News updates, Blogs, videos, webinars, and interview questions. Tailoring learning experiences further, professionals can maximise value with customisable Course Bundles of TKA.

The Knowledge Academy’s Knowledge Pass, a prepaid voucher, adds another layer of flexibility, allowing course bookings over a 12-month period. Join us on a journey where education knows no bounds.

The Knowledge Academy offers various ISO 27001 Courses, including the ISO 27001 Lead Auditor Course and the ISO 27001 Lead Implementer Course. These courses cater to different skill levels, providing comprehensive insights into ISO 27001 Roles and Responsibilities.
Our IT Security & Data Protection Blogs cover a range of topics related to ISO 27001, offering valuable resources, best practices, and industry insights. Whether you are a beginner or looking to advance your ISO Compliance knowledgebase, The Knowledge Academy's diverse courses and informative blogs have got you covered.
Upcoming IT Security & Data Protection Resources Batches & Dates
Date
 ISO 27001 Foundation
ISO 27001 Foundation
Mon 27th Jan 2025
Tue 22nd Apr 2025
Mon 28th Jul 2025
Mon 27th Oct 2025
Mon 15th Dec 2025







 Top Rated Course
Top Rated Course



 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


