We may not have the course you’re looking for. If you enquire or give us a call on 01344203999 and speak to our training experts, we may still be able to help with your training requirements.
We ensure quality, budget-alignment, and timely delivery by our expert instructors.
There is a new vector of data exposure known as “What’s been called” where a Microsoft Power App Breach recently revealed 38 million data online. There are a lot of Personally Identifiable Information (PII), including Social Security numbers, COVID-19 vaccination status and various other customer data.
According to the reports of UpGuard website, A security breach happened where over a thousand web applications were exposed and could be accessed online without permission. UpGuard's cybersecurity researchers were the ones who found this issue. Check out the blog to dive deeper into the Microsoft Power Apps Breach, in which you will learn how to prevent power apps from having data leaks happen and how to protect data.
Table of Contents
1) Understanding Microsoft Power Apps
2) The Data Breach Incidents 2023
3) Key vulnerabilities in Power Apps
4) Preventing data leaks in Microsoft Power Apps
5) Consequences of ignoring security measures
6) Conclusion
Understanding Microsoft Power Apps
Microsoft Power Apps is a set of low-code development tools that empower users to create custom business applications without extensive coding knowledge. It enables rapid app development, allowing organisations to streamline processes, automate tasks, and improve productivity while considering the Microsoft Power Apps Cost. Data security is paramount in Microsoft Power Apps, with robust features for access control, encryption, and compliance to protect sensitive information. Organisations can define permissions, implement data encryption, and adhere to industry standards like GDPR, ensuring the safety and confidentiality of their data.
The Data Breach Incident 2023
Data breaches can have severe repercussions for organisations. In this section, we will examine the recent data breach incident involving Microsoft Power Apps.
Chinese hackers breach U.S agencies through Microsoft Cloud: July 2023
On July 11, Microsoft revealed that a group of hackers from China spied on U.S. government agencies using a vulnerability in Microsoft's online services. This spying began in June and was noticed by a government agency, which then told Microsoft and the Department of Homeland Security about it.
The hackers, whom Microsoft calls "Storm-0558," seem to have connections to the Chinese government. They targeted emails from the State and Commerce departments, especially when the U.S. Secretary of State, Antony Blinken, was planning to visit China. Fortunately, officials say that important information was not stolen in this email attack.
Microsoft refuses claimed Data Breach: July 2023
On July 2, a group called Anonymous Sudan said they hacked into Microsoft and took information from more than 30 million Microsoft accounts. They showed a small piece of the data they claimed to have, but it's still unclear where this data actually came from. A spokesperson from Microsoft said that these claims of a data breach are not true. They also said that they have not found any proof that customer data was accessed or stolen.
More than 548,000 users revealed in BlueBleed data leak: October 2022
On October 19th, a security company called SOCRadar found a big problem with Microsoft's setup. They discovered that more than 2.4 terabytes of information were accessible because Microsoft didn't set things up properly. This data was related to more than 65,000 companies and 548,000 users. It included things like customer emails, project details, and signed documents.
Microsoft admitted to the data leak in a blog post. They said they fixed the issue and told the people whose accounts might have been affected. However, they also explained that they didn't find any proof that customer accounts were actually hacked, just that the data was out in the open for anyone to see.
Land Your Dream Job! Excel with these must-know Power Apps Interview Questions.
Key vulnerabilities in Power Apps
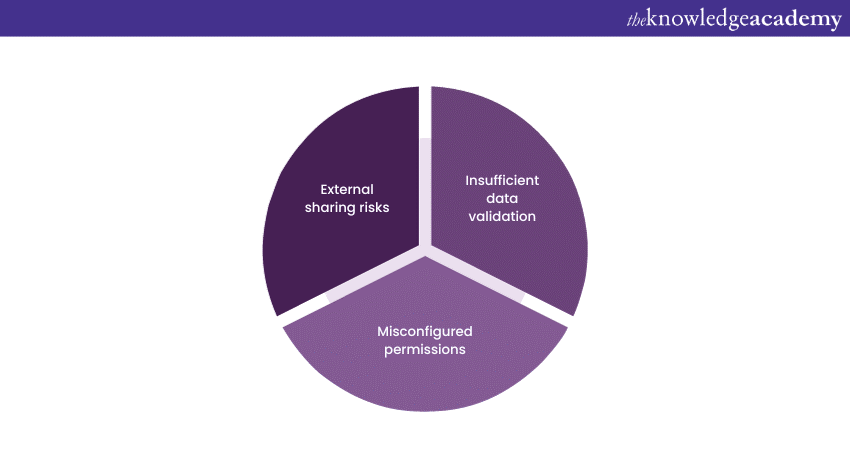
While Microsoft Power Apps offer incredible flexibility and efficiency in creating custom applications, it's essential to be aware of certain vulnerabilities that can jeopardise data security and operational integrity. Here are three critical vulnerabilities that organisations should address.
Insufficient data validation
Insufficient data validation occurs when Power Apps do not thoroughly examine and verify the information entered by users. When user inputs are not properly validated, it can lead to various problems, such as data inaccuracies, security breaches, or even application failures. For instance, if a user enters malicious data, it can manipulate the app's behaviour or expose sensitive information. It's crucial to establish robust data validation processes within Power Apps to prevent these issues. This includes implementing checks for data type, length, format, and content to ensure that only valid and safe data is accepted.
Misconfigured permissions
One of the most common vulnerabilities in Power Apps is misconfigured permissions. This occurs when access controls are not appropriately set up, allowing unauthorised users to gain access to sensitive data or perform actions they shouldn't. Misconfigured permissions can have severe consequences, such as data breaches, data loss, or unauthorised modifications. It's paramount to define and enforce precise access controls and permissions within Power Apps. This involves granting access only to those who need it, limiting privileges to the necessary level, and conducting regular reviews to ensure permissions align with organisational roles and responsibilities.
External sharing risks
Power Apps can be shared externally to facilitate collaboration with users outside your organisation. However, this convenience comes with potential risks. If not managed carefully, external sharing can expose your Power Apps to unauthorised individuals, potentially compromising sensitive data or functionality. To mitigate external sharing risks, organisations should establish clear policies and guidelines for sharing apps externally. This includes setting restrictions on what can be shared, with whom, and for how long. Additionally, educating users about the importance of secure sharing practices and monitoring external access can help maintain a balance between collaboration and security.
Join our Introduction To Microsoft Dynamics 365 55250A Training course and explore the world of Dynamics 365 today!
Preventing data leaks in Microsoft Power Apps
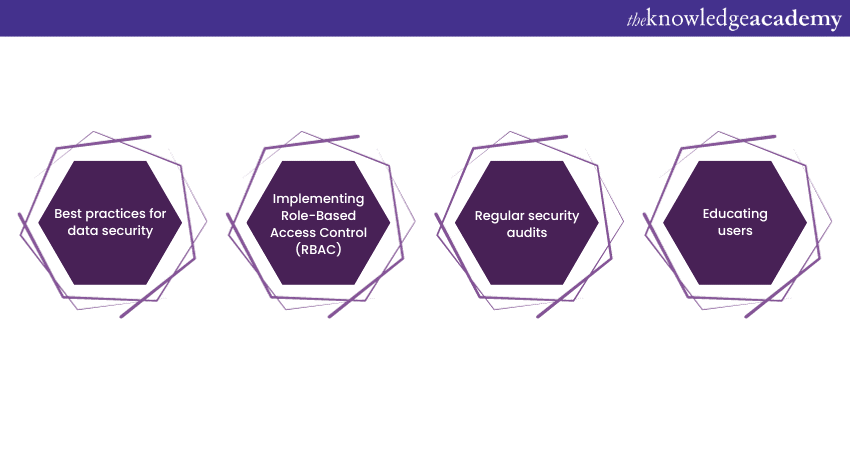
Microsoft Power Apps offer great utility, but safeguarding against data leaks is paramount. Let's explore key strategies to bolster security.
1) Best practices for data security: Implementing robust data security practices is fundamental. This involves defining clear data handling policies, encrypting sensitive information, and establishing stringent access controls. Regularly update and patch your Power Apps to protect against known vulnerabilities. Train your team on data security best practices to build a culture of responsibility and awareness.
2) Implementing Role-Based Access Control (RBAC): Role-Based Access Control (RBAC) is crucial in limiting user permissions to only what's necessary for their roles. Define roles and assign permissions accordingly. This makes sure that users can access only the data and functionalities essential for their tasks. Regularly review and update role assignments to align with organisational changes.
3) Regular security audits: Frequent security audits are indispensable for identifying and addressing vulnerabilities. Conduct comprehensive assessments of your Power Apps environment to pinpoint weaknesses. Regularly test your applications for security flaws, and promptly address any issues that arise. Collaborate with IT experts or security professionals for thorough evaluations.
4) Educating users: Your users play a pivotal role in data security. Educate them on the importance of secure practices, including strong password creation, safe data sharing, and recognising phishing attempts. Regularly provide training and awareness programs to keep your users informed about evolving security threats.
Consequences of ignoring security measures
Let’s understand the consequences of ignoring security measures with an example. Imagine a medium-sized company, XYZ Inc., which heavily relied on Microsoft Power Apps to streamline its internal processes and improve efficiency. However, due to budget constraints and a perception that security measures were an unnecessary expense, XYZ Inc. failed to implement robust security protocols within their Power Apps ecosystem.
One day, an attacker with malicious intent identified a vulnerability in one of XYZ Inc.'s Power Apps. Exploiting this vulnerability, the attacker gained unauthorised access to sensitive customer data and proprietary company information. This breach remained undetected for several weeks, during which the attacker exfiltrated critical data. Now, let’s see what the consequences of it will be.
1) Data Loss: The breach resulted in the loss of valuable customer data, including personal information and financial records. XYZ Inc. faced severe reputational damage due to its inability to safeguard customer data.
2) Legal Consequences: The company was held liable for the breach, facing lawsuits and regulatory fines for failing to save customer data according to data protection regulations like GDPR.
3) Financial Impact: XYZ Inc. had to allocate a significant budget to resolve the breach, cover legal expenses, and compensate affected customers. Their revenue took a hit due to the loss of customer trust.
4) Reputation Damage: The company's reputation was tarnished, making it challenging to regain customer trust and attract new clients. Shareholders were also concerned about the company's ability to secure sensitive information.
5) Operational Disruption: The breach forced XYZ Inc. to divert resources and manpower to address the security incident, disrupting normal business operations and causing financial losses.
Get yourself registered in our Microsoft Power Platform Fundamentals PL900 course now!
Conclusion
We hope you found this blog post useful and knowledgeable. The Microsoft Power Apps breach underscores the critical importance of prioritising data security. By executing robust security measures and staying vigilant, organisations can effectively safeguard their data and mitigate the risks associated with potential breaches. Additionally, leveraging Microsoft Power Apps and Power Automate Email functionalities can enhance security by automating alerts and notifications, ensuring timely responses to potential threats. Furthermore, using Microsoft Power App Templates ensures that apps are built with security in mind from the outset, further protecting sensitive information.
Check out our Microsoft Dynamics 365 Training course now!
Frequently Asked Questions
What are the Other Resources and Offers Provided by The Knowledge Academy?

The Knowledge Academy takes global learning to new heights, offering over 3,000 online courses across 490+ locations in 190+ countries. This expansive reach ensures accessibility and convenience for learners worldwide.
Alongside our diverse Online Course Catalogue, encompassing 19 major categories, we go the extra mile by providing a plethora of free educational Online Resources like News updates, Blogs, videos, webinars, and interview questions. Tailoring learning experiences further, professionals can maximise value with customisable Course Bundles of TKA.
Upcoming Microsoft Technical Resources Batches & Dates
Date
 Microsoft Power Apps for End Users 55265AC
Microsoft Power Apps for End Users 55265AC
Thu 8th May 2025
Thu 4th Sep 2025
Thu 6th Nov 2025






 Top Rated Course
Top Rated Course


 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


