We may not have the course you’re looking for. If you enquire or give us a call on 01344203999 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.

A type of cyber security attack in which cyber criminals target users by tricking them into clicking on a malicious link on their mobile phones is known as Smishing. Such links share the personal and private information of the victim with the attacker. These sometimes also install malicious software on the target's mobile phones. Such attacks endanger Cyber Security and put people at risk as the attacker can steal and misuse their data. Despite being coined in 2006, the term 'Smishing' remained unknown until recently when cyber criminals started sending malicious links over SMSs. According to Proofpoint, less than 35% of the population knows Smishing.
This blog provides an overview of Smishing attacks, their various types, past case studies, and ways to safeguard from them.
Table of Contents
1) Smishing: An Overview
2) How does Smishing take place?
3) Types of Smishing Attacks
4) Case studies of Smishing Attacks
5) Ways to avoid becoming a Smishing victim
6) Conclusion
Join Cyber Security Training courses to become well-versed with different tools to protect against Cyber Threats.
Smishing: An Overview

The combination of the words SMS and Phishing is known as Smishing. It is a form of Phishing where the attacker sends compelling and attractive text messages to trick the user into clicking on a malicious link. Consequently, the attacker gains access to the personal and sensitive data of the users. The primary purpose of these attacks is to steal the personal data of people, which scammers can use to commit fraud or other cybercrimes. With such attacks, cybercriminal attempts to steal the money of the recipients of such text messages, underscoring the critical need for individuals to be aware of and implement Cyber Security Essentials to protect against evolving cyber threats like Smishing
Typically, cybercriminals use one of the following two methods to execute a Smishing attack:
Malicious Website - The link in the message can lead to a fake website requesting users to enter their personal information, which attackers can steal. These cyber criminals develop custom websites that mimic the original ones, thereby tricking the users into believing that they are entering the original website and that their data is safe.
Malware - The Smishing messages contain links that trick the users into downloading malware in the form of malicious software, which gets installed on their phones. This malware acts as legitimate software or app and tricks users into entering their confidential information. The hacker can easily access this data.
Become an expert at Computer Forensics with the Computer Forensics Foundation Training course.
Differences between Phishing, Vishing, and Smishing
Phishing, Vishing, and Smishing are three types of sophisticated cyber-attacks that trick recipients into handing over their personal and sensitive information. In such attacks, the sender appears legitimate, like the user's bank, credit card company or others.
a) Phishing - It is the most common type of cybercrime out of the three. It involves a fraudulent email asking the recipient to click on a malicious link. This link asks the user to download malicious software on their system or redirects them to a fake website where they enter their confidential information. This data is sent directly to the hacker without the victim's knowledge.
b) Vishing - This term combines 'voice' and 'Phishing'. In such attacks, the cybercriminal will spoof the phone number to make it look like from a bank or similar trusted sources. All fraudulent calls and voicemails are a form of Vishing. The attacker calls the victim using pre-recorded calls. Further, some scammers may also record the voice of the victims and then pretend to be them to authorise charges to their bank accounts.
c) Smishing - It is in the form of unwanted text messages that ask for the user's personal information or asks them to click on a malicious link appearing to be from a trusted source. It is a new scamming method and is mainly targeted at smartphone users. The link within the Smishing messages can also download malware like viruses, spyware, adware, or ransomware on the victim's device.
Smishing attacks can download and install Malware, Ransomware, and Spyware on your devices. Join the Cyber Security Awareness course to learn how to prevent Cyber threats.
How does Smishing take place?
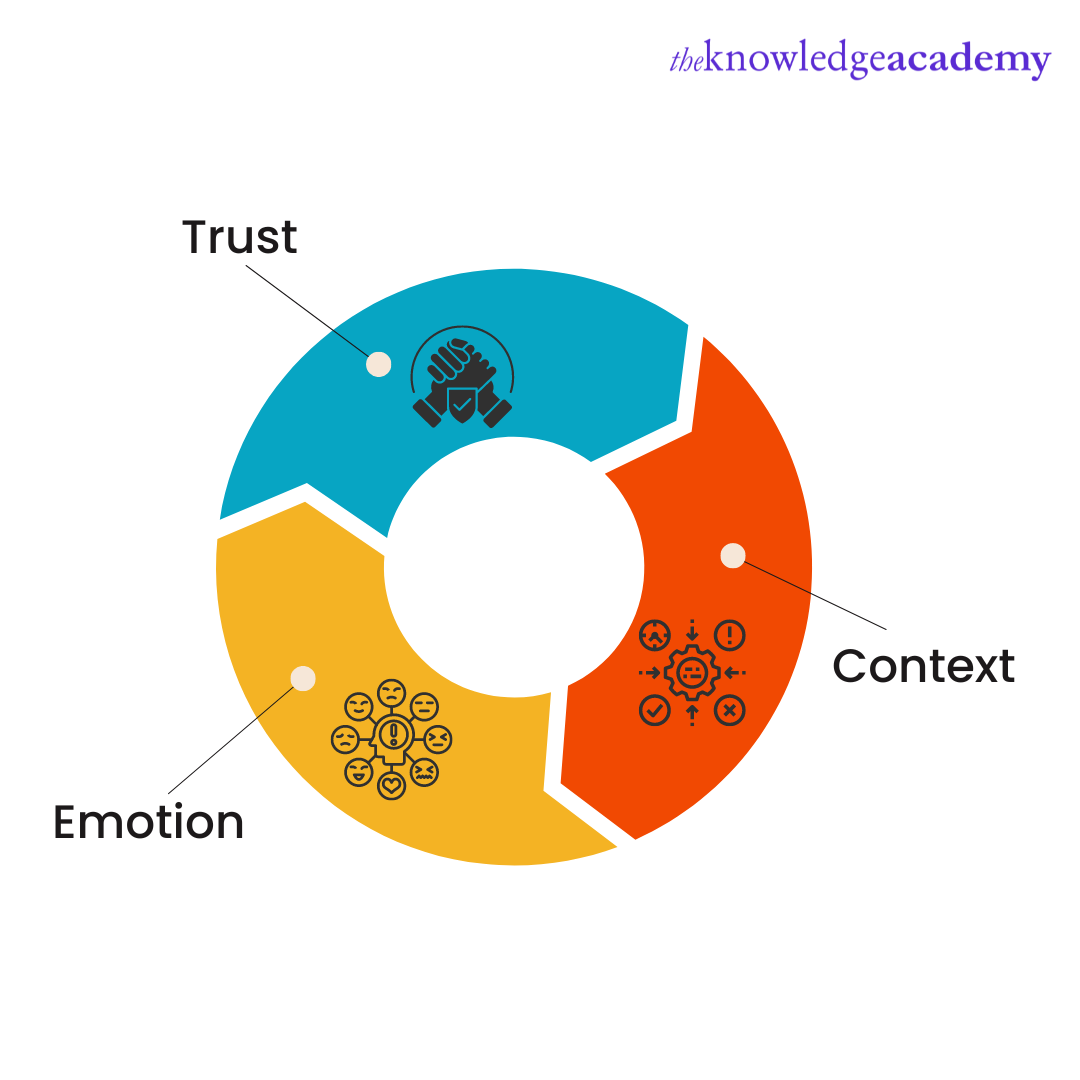
Smishing is fast becoming one of the most used scamming methods by cyber-criminals. Such attacks' success depends on the betrayal of trust and trickery. The attacker imitates to be from a trusted source, and when the target trusts the cyber-criminal, they betray the users. It is a slightly modified version of Phishing to accommodate modern technology like smartphones. Further, Social Engineering is also a key component. There are three elements to such an attack, as shown below:
a) Trust - The attacker poses to be from a legitimate source to reduce the doubt factor in the minds of the target. The cyber-criminal has to gain the target's trust to increase the chances of the link getting clicked. If the recipient does not trust the text message, they will not click on the malicious link, reducing the chances of successfully executing the attack.
b) Context - The cyber-criminal uses a situation relevant to the target. Developing a context enables the criminal to create a strong message that removes any suspicion from the minds of the target that the message might be a scam. Personalised messages are more effective in Smishing and can increase the scope of the attack, thereby making it more effective.
c) Emotion - The third key element of Smishing is emotion. Scammers develop messages that make the target emotional, overriding their critical thinking. These also motivate the target to take quick action without thinking, making the attack successful.
Using these methods, the attacker writes a message that will get the recipient to take quick action. Scammers want the target to click on a link from the text message so that they share their personal information, which the cyber-criminal can access.
With Social Engineering Training course, learn about computer and physical Social Engineering tools.
Types of Smishing Attacks
Smishing attacks have become the new form of Phishing that extracts vital information from the targets by tricking them. Even though these attacks use similar methods, their presentation differs significantly. Some of the common types of such attacks are:
COVID-19 Smishing
The COVID-19 Smishing scam is based on the aid program developed by the government and healthcare organisations to help recover from the COVID-19 pandemic. Scammers have used these programs to alter the health and financial situations of the victims. Asking for sensitive information like social security numbers, tax-based financial relief, and public health safety updates are some of the means used by cyber-criminals to scam people under the pretext of aid for the COVID-19 pandemic.
Financial Services Smishing
It is the most common type of such attack. It involves sending messages masked as being from financial institutions like banks. Generally, people blindly trust these messages, thinking they are from the bank and end up providing the scammers with their financial information.
The Cyber Security Risk Management course can help you understand modern Cyber-attacks. Join today!
Case studies of Smishing Attacks
Here are some well-known examples and case studies of Smishing attacks.
Early Access Apple iPhone 12 Scam - This is an example of gift Smishing. A Smishing campaign came to light in 2020 that baited people into providing their credit card information for a free iPhone 12. It was based on an order confirmation premise. Scammers sent messages to the targets claiming a package was delivered to the wrong address. The link in the message posed as an Apple chatbot that could guide victims to update the delivery address. However, the targets had to enter their credit card information in the chatbot to change the delivery address.
Mandatory Online COVID-19 Test Scam - This is an example of COVID-19 Smishing. It came to light in April 2020 when the Better Business Bureau observed an increase in the reports of impersonators posing as the US government. The message asked the targets to take a mandatory online COVID-19 test through the linked website.
Do you want to expand your understanding of Cyber Security? Then join today the Certified Cyber Security Professional (CCS-PRO) course.
Ways to avoid becoming a Smishing victim

Smishing is a significant cause of concern today. The number of such attacks is increasing day by day. Not responding to the message if it comes from a spam number is the most fundamental way of preventing these attacks. People must refrain from responding to messages received from unknown or spam numbers.
Another way to avoid becoming a Smishing victim is by refraining from taking immediate actions. Scammers send messages that urge the targets to share their information quickly to avoid being penalised or to stop their accounts from getting blocked. However, people must wait to take immediate action. The individuals should read the message carefully, look at its number and take the recommended action if it is from an authentic source.
Conclusion
Maintaining Cyber Security is complex, considering the increasing number of Phishing and Smishing cases. Smishing is just like Phishing but targets mobile phone users. It is new, and only a few people know about this cyberattack. After reading this blog, we hope you understand what Smishing is and its various types and ways to avoid becoming its victim.
Frequently Asked Questions
Upcoming IT Security & Data Protection Resources Batches & Dates
Date
 Certified Cyber Security Professional (CCS-PRO)
Certified Cyber Security Professional (CCS-PRO)
Fri 21st Mar 2025
Fri 23rd May 2025
Fri 22nd Aug 2025
Fri 5th Dec 2025







 Top Rated Course
Top Rated Course




 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


