We may not have the course you’re looking for. If you enquire or give us a call on 01344203999 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.
Have you ever wondered how a single virus can wreak havoc on your computer system? From slowing down your machine to wiping out entire data, viruses are a nightmare for anyone using a digital device. But what if you could understand the Types of Computer Viruses out there and take steps to protect yourself?
In this blog, we’ll take a closer look at the Types of Computer Viruses that have emerged over time. We'll explore how they spread, what damage they can cause, and, more importantly, how you can safeguard your devices from these threats. Are you ready to explore the dark side of the digital world? Let’s get started!
Table of Contents
1) What is a Computer Virus?
2) Types of Computer Viruses
3) How do Viruses Spread?
4) Tips for Preventing Computer Viruses
5) Conclusion
What is a Computer Virus?
A computer virus is a type of malicious software (malware) that is designed to attach itself to other programmes, self-replicate, and spread to other devices.
When executed, a virus modifies other computer programmes by inserting its code into them. If the virus successfully replicates, the affected device is considered “infected.”
Key points about computer viruses:
1) Self-replication: A virus can copy itself and spread to other programmes and devices.
2) Infection: It modifies other programmes by inserting its own code.
3) Malicious activities: The virus can:
a) Damage to the local file system.
b) Steal data
c) Interrupt services
d) Download additional malware
e) Perform other harmful actions as coded by the malware author
4) Deception: Many viruses disguise themselves as legitimate programmes to trick users into executing them, thereby delivering the virus payload.
Types of Computer Viruses
The following are various Types of Computer Viruses:
1) Macro Virus
1) First Occurrence: Mid-1990s
2) Target: Microsoft Office applications (Word, Excel)
3) When it Affects:
a) Virus is embedded in macros of documents
b) Activates when the document is opened
c) Spreads quickly through shared documents
2) Direct Action
1) First Occurrence: Early 1980s
2) Target: Executable files (.exe, .com)
3) When it Affects:
a) Activates when the infected file is executed
b) Searches for other files to infect
c) Does not remain in memory after task completion
3) Trojan Horses
1) First Occurrence: 1970s (became more common in the 1990s)
2) Target: Users (disguised as legitimate software)
3) When it Affects:
a) Activated when users download/install the fake software
b) Creates backdoors for hackers to exploit
c) Can steal data and remotely control the system
4) Overwrite Virus
1) First Occurrence: 1990s
2) Target: Files (overwrites content)
3) When it Affects:
a) Activates as soon as the file is opened
b) Overwrites the file's content immediately
c) No data recovery is possible after infection
5) File Infector
1) First Occurrence: 1980s
2) Target: Executable files
3) When it Affects:
a) Activated when the infected executable file is run
b) Infects other files on the system
c) Can lead to system crashes and loss of data
6) Boot Sector Virus
1) First Occurrence: Late 1980s and early 1990s
2) Target: Master Boot Record (MBR) of storage devices
3) When it Affects:
a) Activated when the system boots
b) Loads into memory before the operating system
c) Spreads to other systems via external devices (e.g. USB drives)
7) Resident Virus
1) First Occurrence: 1980s
2) Target: System memory
3) When it Affects:
a) Activates whenever specific files or programmes are accessed
b) Stays in memory and causes ongoing damage until removed
c) Does not require an infected file to be opened to execute
8) Multipartite Virus
1) First Occurrence: 1990s
2) Target: Boot sector and executable files
3) When it Affects:
a) Activates in two phases:
1) At boot-up (affects boot sector)
2) When infected files are run (affects files)
b) Harder to detect due to multiple attack methods
9) Spacefiller Virus
1) First Occurrence: Late 1990s
2) Target: Executable files
3) When it Affects:
a) Injects its code into empty spaces in files
b) Harder to detect because it does not increase file size
c) Activates when the infected file is executed
10) Network Virus
1) First Occurrence: 1990s (with the rise of the internet)
2) Target: Local and wide area networks (LANs, WANs)
3) When it Affects:
a) Activated once the network is accessed
b) Spreads quickly across all connected devices
c) Exploits vulnerabilities in network protocols
11) Browser Hijacker
1) First Occurrence: Early 2000s
2) Target: Web browsers
3) When it Affects:
a) Alters browser settings (homepage, search engine) without permission
b) Redirects users to malicious websites
c) Activates as soon as the browser is opened
12) Web Scripting Virus

1) First Occurrence: 2000s (with dynamic websites)
2) Target: Web browsers and applications
3) When it Affects:
a) Injects malicious scripts into websites
b) Activates when the user visits the infected site
c) Can steal data or install Malware
13) Polymorphic Virus
1) First Occurrence: 1990s
2) Target: A wide range of files
3) When it Affects:
a) Changes its code with each infection to evade detection
b) Activates when the infected file is opened
c) Can spread via email attachments or downloads
Become a Certified Cyber Security Professional to safeguard digital environments with our Certified Cyber Security Professional (CCS-PRO) Course. Sign up now!
How do Viruses Spread?
Computer viruses have several ways of infiltrating systems. Here are the most common methods viruses use to propagate.
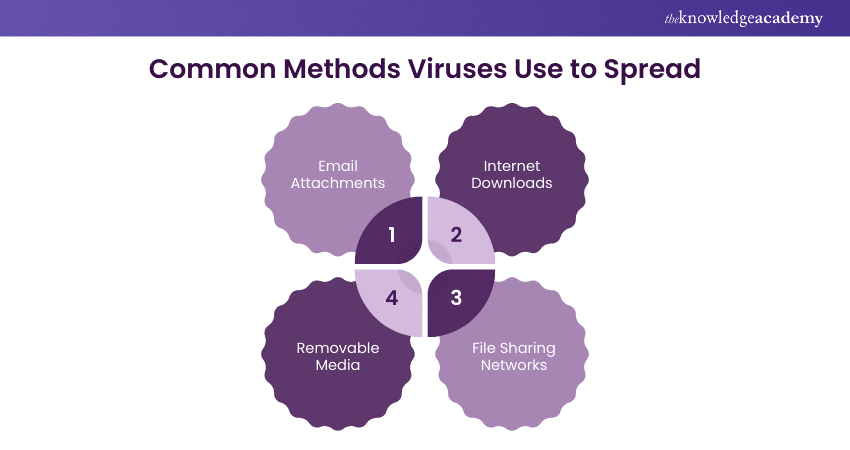
1) Email Attachments
a) Virus Spread: Common method.
b) Disguised Files: Documents, images, PDFs.
c) Activation: Opens and infects.
d) Workplace Risk: Frequent file sharing.
e) Phishing: Appears from trusted sources.
f) Prevention: Email filters, antivirus, employee training.
2) Internet Downloads
a) Content Variety: Not all safe.
b) Malicious Code: Pirated software, freeware.
c) Compromised Sites: Legitimate-looking but hacked.
d) Trusted Sources: Reputable, secure websites.
e) Browser Security: Built-in features.
f) Download Scanners: Check files.
g) Avoid Piracy: Often contains malware.
3) File Sharing Networks
a) Virus-prone: P2P networks.
b) Direct Sharing: User-to-user.
c) Cybercriminals: Spread corrupted files.
d) No Oversight: Risky content.
e) Unintentional Harm: Downloading infected files.
f) Security: Antivirus, avoid unknown users.
g) File Verification: Check integrity.
4) Removable Media
a) Virus Carriers: USBs, external drives, CDs, DVDs.
b) Automatic Transfer: Connect and infect.
c) Shared Environments: Schools, companies.
d) Rapid Spread: Multiple devices.
e) Scanning: Use antivirus.
f) Write Protection: Prevent transfer.
g) Regular Updates: Keep antivirus current.
Step into the world of Cyber Security by mastering Malware Analysis Training to defend your systems and enhance your expertise!
Tips for Preventing Computer Viruses
Prevention is the most effective defence against computer viruses. Here are some crucial tips to help you protect your system from harmful viruses:
Install and Update Antivirus Software
a) Reliable Protection: Essential for virus protection.
b) Regular Updates: Detect and remove new threats.
c) Antivirus Scans: Remove or quarantine malicious software.
Avoid Downloading From Untrusted Sources
a) Be Cautious: Careful with unfamiliar websites.
b) Trusted Websites: Download from reputable, secure sites.
Don’t Open Suspicious Email Attachments
a) Avoid Unsolicited Emails: Especially with attachments.
b) Verify Source: Don’t open if unsure of the source.
Keep Your System Updated
a) Regular Updates: Fix security vulnerabilities.
b) Protection: Guard against viruses exploiting outdated systems.
Use Strong Passwords
a) Strong, Unique Passwords: For all accounts.
b) Reduce Hacking Risk: Prevent phishing or brute-force attacks.
Back up Your Data Regularly
a) Timely Backups: Save data in case of infection.
b) External Storage: Use external devices or cloud storage.
Be Cautious With Removable Media
a) Scan Devices: Check USB drives and other media for viruses.
b) Prevent Spread: Avoid spreading viruses through external devices.
Protect your organisation from cyber attacks - start your journey with our Cyber Security Awareness Course today!
Conclusion
Understanding the Types of Computer Viruses is crucial for protecting your digital devices from potential threats. From macro viruses to Trojan Horses Malware, each poses unique risks. Stay cautious, use antivirus software, and practice safe browsing habits to effectively protect your systems from harmful digital intruders. Remember, a little caution today can save you from a digital disaster tomorrow!
Stay ahead of cyber threats with our Cyber Security Training. Sign up today!
Frequently Asked Questions

The most common computer virus is the Trojan horse, which pretends to be genuine software. Once downloaded, it has the ability to steal data, install backdoors, and allow hackers to access the system.

Viruses affect computers by corrupting files, slowing down performance, stealing sensitive data, and sometimes allowing hackers to gain control. They can cause system crashes, data loss, and security breaches.

The Knowledge Academy takes global learning to new heights, offering over 30,000 online courses across 490+ locations in 220 countries. This expansive reach ensures accessibility and convenience for learners worldwide.
Alongside our diverse Online Course Catalogue, encompassing 19 major categories, we go the extra mile by providing a plethora of free educational Online Resources like News updates, Blogs, videos, webinars, and interview questions. Tailoring learning experiences further, professionals can maximise value with customisable Course Bundles of TKA.

The Knowledge Academy’s Knowledge Pass, a prepaid voucher, adds another layer of flexibility, allowing course bookings over a 12-month period. Join us on a journey where education knows no bounds.

The Knowledge Academy offers various Cyber Security Training, including Malware Analysis Training, Certified Cyber Security Professional (CCS-PRO), Cyber Security Awareness and Fraud Analytics Training Course. These courses cater to different skill levels, providing comprehensive insights into Malware.
Our IT Security & Data Protection Blogs cover a range of topics related to Malware Analysis, offering valuable resources, best practices, and industry insights. Whether you are a beginner or looking to advance your Cyber Security skills, The Knowledge Academy's diverse courses and informative blogs have got you covered.
Upcoming IT Security & Data Protection Resources Batches & Dates
Date
 Malware Analysis Training
Malware Analysis Training
Fri 14th Feb 2025
Fri 11th Apr 2025
Fri 13th Jun 2025
Fri 15th Aug 2025
Fri 10th Oct 2025
Fri 12th Dec 2025







 Top Rated Course
Top Rated Course



 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


