We may not have the course you’re looking for. If you enquire or give us a call on 01344203999 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.
Ensuring the security of the computer systems and networks has become paramount today. As cyber threats become more sophisticated, it's crucial to employ proactive measures to safeguard your data and infrastructure. Penetration Testing and the various Types of Penetration Testing provide a comprehensive approach to identifying vulnerabilities and strengthening your defences.
According to Check Point Research, cyberattacks globally increased by 38% in 2022, compared to 2021. With the exponentially increasing amount of sensitive data collected and stored worldwide, the necessity for protection against these attacks by various Testing methods has become even more grave. In this blog, we'll delve into the various Types of Penetration Testing, shedding light on their distinct focuses and benefits.
Table of Contents
1) Penetration Testing- An overview
2) Types of Penetration Testing
a) Network Penetration Testing
b) Web Application Penetration Testing
c) Mobile Application Penetration Testing
d) Wireless Network Penetration Testing
e) Social Engineering Testing
f) Physical Penetration Testing
g) Red team vs blue team Testing
3) Conclusion
Penetration Testing- An overview
In cybersecurity, Penetration Testing stands as a powerful methodology designed to proactively identify vulnerabilities within digital systems, applications, and networks. Also known as Pen Testing, this process involves simulating controlled attacks to uncover potential weak points that malicious hackers could exploit.
The primary goal of Penetration Testing is to emulate the actions of real attackers while operating within a secure and controlled environment. By doing so, organisations gain invaluable insights into their security posture, enabling them to remediate vulnerabilities before cybercriminals can capitalise on them.
Penetration Testing plays a pivotal role in enhancing the overall security strategy of an organisation. It provides actionable information on potential risks and weaknesses, allowing for targeted investments in security measures and resources. Additionally, it aids in compliance efforts by identifying gaps that might put sensitive data at risk.
Ultimately, Penetration Testing empowers businesses to take a proactive stance against evolving cyber threats. By understanding the intricate vulnerabilities within their digital infrastructure, organisations can fortify their defences, safeguard their data, and maintain the trust of clients and partners in an increasingly interconnected world.
Types of Penetration Testing
Now, let’s discuss about the different Penetration Testing Types employed by testers to maintain the security and robustness of applications and systems:
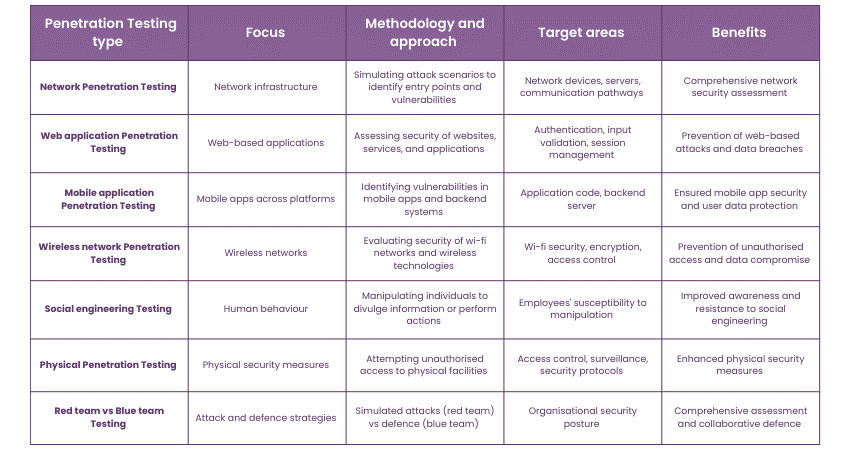
Network Penetration Testing
Network Penetration Testing is a Crucial facet of cybersecurity, aimed at gauging the robustness of an organisation's network infrastructure against potential cyber threats. In an era where networks are the backbone of digital operations, identifying vulnerabilities before malicious actors exploit them is paramount.
During Network Penetration Testing, skilled Cybersecurity professionals conduct systematic assessments to pinpoint weak points in network devices, servers, and communication pathways. By simulating various attack scenarios, they strive to uncover potential entry points and data leakage vulnerabilities that could be exploited by hackers.
This Testing approach encompasses a variety of techniques, from vulnerability scanning to manual exploitation. It goes beyond surface-level assessments, delving deep into the intricacies of network components. The process involves identifying misconfigurations, unpatched software, weak access controls, and other vulnerabilities that could be exploited by cybercriminals.
The benefits of Network Penetration Testing are manifold. Firstly, it provides organisations with a comprehensive view of their network's security posture, enabling informed decisions on how to strengthen defences. Secondly, it assists in compliance efforts by ensuring that industry-specific security standards are met. Using apprpriate penetration testing tools for each type greatly helps. Moreover, Network Penetration Testing helps in identifying potential avenues for data breaches or unauthorised access, thereby, it helps safeguarding sensitive information and maintaining customer trust.
Network Penetration Testing is a proactive approach to Cybersecurity wherein, the vulnerabilities are uncovered before they can be exploited. This enables organisations not only prevent potential breaches but also demonstrate their commitment to data protection and information security. As technology continues to advance, Network Penetration Testing remains a fundamental strategy in the ongoing battle against cyber threats.
Unlock the power of Cybersecurity - register in our Ethical Hacking and Penetration Testing Training Today!
Web application Penetration Testing
Web Application Penetration Testing, a specialised form of Cybersecurity assessment, plays a critical role in identifying vulnerabilities within these applications before malicious actors can exploit them. Web Application Penetration Testing involves a comprehensive evaluation of the security measures of web-based software. This assessment delves into the intricate layers of the application's architecture, scrutinising elements such as authentication mechanisms, input validation, session management, and data handling procedures.
The primary objective of web application Penetration Testing is to identify potential security flaws and weaknesses that hackers might exploit. Common vulnerabilities targeted include SQL injection, Cross-Site Scripting (XSS), Cross-Site Request Forgery (CSRF), and insecure data storage. By simulating real-world attack scenarios, Penetration Testers can provide insights into how attackers might compromise the application's security.
Beyond just identifying vulnerabilities, web application Penetration Testing also offers solutions for mitigating risks. The findings of the test guide developers and security teams in prioritising remediation efforts. This can involve implementing patches, enhancing input validation, fortifying authentication procedures, and applying encryption where needed.
By investing in web application Penetration Testing, organisations ensure not only the protection of their sensitive data but also the preservation of user trust. A successful test leads to improved security measures, reduced potential for data breaches, and compliance with industry regulations.
In an era where digital services are integral to business operations, the assurance of a secure online presence is paramount. Web application Penetration Testing stands as a proactive measure to fortify the digital frontiers, creating a resilient shield against cyber threats and reaffirming an organisation's commitment to data protection and Cybersecurity excellence.
Mobile Application Penetration Testing
Mobile Application Penetration Testing emerges as a critical process to identify vulnerabilities within mobile apps and their corresponding backend systems. This comprehensive Testing approach helps mitigate potential risks, protect the user data, and maintain the trust of app users.
Mobile application Penetration Testing involves a systematic assessment of the security controls and protocols implemented in both the app and the server-side infrastructure. Testers employ techniques akin to those of real attackers, attempting to exploit weaknesses that could compromise the app's confidentiality, integrity, and availability.
One of the vital aspects of mobile app Penetration Testing is evaluating the app's communication with external servers. This analysis helps uncover potential points of data leakage or unencrypted transmissions that could be exploited by attackers. Additionally, testers scrutinise the authentication mechanisms and authorisation protocols to ensure that only authorised users gain access to sensitive functionalities.
Another critical focus area is the identification of coding vulnerabilities that could lead to common attacks, like SQL injection or XSS. By pinpointing these vulnerabilities, developers can then rectify the underlying coding flaws, enhancing the overall security posture of the application.
Mobile Application Penetration Testing also examines the potential risks associated with third-party libraries and dependencies. These external components may introduce security vulnerabilities available for exploitation by attackers to gain unauthorised access to the app's data or functionality.
Conducting thorough Penetration Testing is imperative. It not only helps identify and rectify potential security vulnerabilities but also demonstrates a commitment to user privacy and data protection.
Unlock your Cybersecurity arsenal: Dive into Tools and Techniques for Penetration Testing Now!
Wireless Network Penetration Testing
Wireless Network Penetration Testing emerges as a vital approach to assess the vulnerabilities in wireless infrastructures. This method involves evaluating Wi-Fi networks and other wireless technologies to identify potential entry points for cyber attackers.
The process entails meticulously scanning the wireless environment to uncover security weaknesses. It addresses concerns such as weak encryption protocols, insecure configurations, and potential avenues for unauthorised access. By simulating attacks that mirror those of malicious hackers, testers determine how robust an organisation's wireless security truly is.
Wireless Network Penetration Testing holds significance for both businesses and individuals. Organisations benefit from stronger safeguards against data breaches, while individuals can trust that their sensitive information remains private within secure networks.
With the proliferation of wireless technology, ensuring the integrity of digital connections is paramount. By engaging in wireless Network Penetration Testing, organisations can bolster their security measures, thwart potential threats, and sustain the trust of clients and stakeholders in an increasingly connected world.
Social Engineering Testing
Social Engineering Testing takes a unique approach by delving into the human element of security. This method seeks to assess an organisation's susceptibility to manipulation and exploitation by simulating various deceptive tactics that cybercriminals might employ.
Social Engineering Testing involves scenarios where individuals within an organisation are targeted through techniques like phishing emails, pretexting, and baiting. The objective is to evaluate how well employees recognise and respond to these potential threats. By understanding how easily individuals might inadvertently divulge sensitive information or take actions that compromise security, organisations can take proactive steps to enhance awareness and training.
The significance of social engineering Testing lies in its ability to expose vulnerabilities that technical solutions alone cannot address. Even the most advanced Cybersecurity systems can be circumvented if human behaviour is compromised. By identifying weak links in the human chain, organisations can develop tailored training programmes and establish protocols to fortify their defences against social engineering attacks.
In an age where cyber threats continuously evolve, social engineering Testing is an essential component of a comprehensive Cybersecurity strategy. It fosters a culture of vigilance and equips employees with the knowledge and skills needed to withstand manipulative tactics, ultimately bolstering an organisation's security posture.
Physical Penetration Testing
While cybersecurity predominantly focuses on digital realms, Physical Penetration Testing steps beyond the virtual to evaluate an organisation's real-world security measures. This method involves simulating unauthorised physical access attempts to assess vulnerabilities in physical facilities, premises, and equipment.
Physical Penetration Testing examines the effectiveness of access controls, surveillance systems, security protocols, and employee awareness in preventing unauthorised entry. Testers employ tactics like tailgating (following authorised personnel without authentication) or attempting unauthorised entry through restricted areas
By executing these simulated scenarios, organisations can identify weaknesses in their physical security infrastructure and procedures. This could range from unsecured entrances to inadequate surveillance coverage. The insights gained from Physical Penetration Testing allows organisations to enhance their real-world security measures, preventing potential breaches that could lead to data theft, equipment damage, or other security compromises.
Incorporating Physical Penetration Testing into an overarching security strategy provides a holistic view of vulnerabilities. It ensures a comprehensive approach to safeguarding assets and data, both in the digital and physical spheres, fortifying an organisation's resilience against multifaceted threats.
Red team vs Blue Team Testing
In the field of Cybersecurity, red team vs blue team Testing emerges as a strategic approach that mirrors the cat-and-mouse game between attackers and defenders. These two distinct teams, each with a unique role, collaborate to bolster an organisation's security posture comprehensively.
The red team, often include ethical hackers, mimics the tactics, techniques, and procedures of real-world adversaries. They launch simulated attacks on an organisation's systems, attempting to breach defences and exploit vulnerabilities. This proactive approach enables businesses to identify weak points and anticipate potential threats before they can be exploited by malicious actors.
Conversely, the Blue Team, consisting of the organisation's security defenders, is tasked with detecting, responding to, and mitigating the simulated attacks launched by the red Team. This team operates as the first line of defence, using their expertise to identify vulnerabilities, assess their impact, and implement measures to strengthen security protocols.
The synergy between red team and blue team Testing is crucial. While the Red team exposes vulnerabilities, the blue Team's response and defence strategies are tested and refined. This collaborative process ensures that an organisation's security strategy is robust, adaptable, and capable of withstanding a range of cyber threats.
In essence, red team vs blue team Testing goes beyond the conventional security approach by creating an environment of continuous improvement. By simulating attacks and evaluating responses, organisations can develop a more proactive and resilient security posture, safeguarding their digital assets and reputation in an ever-evolving cyber landscape.
Conclusion
With rapidly increasing cyber threats, Penetration Testing is a critical tool for identifying vulnerabilities and enhancing your organisation's security. By understanding the different Types of Penetration Testing, you can tailor your approach to address the specific challenges and risks your organisation faces. Remember, a proactive approach to security not only safeguards your data but also fosters trust among your clients and partners in the digital realm.
Learn the intricacies of tools used for Penetration Testing with our Tools and Techniques for Penetration Testing - join now!
Frequently Asked Questions

The five Types of Penetration Testing are Network Penetration Testing, Web Application Penetration Testing, Mobile Application Penetration Testing, Client-Side Penetration Testing, and Social Engineering Penetration Testing. Each type focuses on assessing specific security aspects to identify vulnerabilities and strengthen overall Cybersecurity measures.

The four stages of Penetration Testing include reconnaissance, scanning, exploitation, and post-exploitation. In the reconnaissance phase, information is gathered about the target. Scanning involves identifying live hosts and open ports. Exploitation entails actively probing for vulnerabilities and gaining access. Post-exploitation involves maintaining access and assessing the impact of the breach.

The Knowledge Academy takes global learning to new heights, offering over 30,000 online courses across 490+ locations in 220 countries. This expansive reach ensures accessibility and convenience for learners worldwide.
Alongside our diverse Online Course Catalogue, encompassing 17 major categories, we go the extra mile by providing a plethora of free educational Online Resources like News updates, Blogs, videos, webinars, and interview questions. Tailoring learning experiences further, professionals can maximise value with customisable Course Bundles of TKA.

The Knowledge Academy’s Knowledge Pass, a prepaid voucher, adds another layer of flexibility, allowing course bookings over a 12-month period. Join us on a journey where education knows no bounds.

The Knowledge Academy offers various Automation & Penetration Testing Courses, including Tools and Techniques for Penetrating Testing, Fundamentals of Test Automation etc. These courses cater to different skill levels, providing comprehensive insights into Cyber Security Sklils.
Our IT Security & Data Protection Blogs covers a range of topics related to Fundamentals of Test Automation, offering valuable resources, best practices, and industry insights. Whether you are a beginner or looking to advance your IT skills, The Knowledge Academy's diverse courses and informative blogs have you covered.
Upcoming IT Security & Data Protection Resources Batches & Dates
Date
 Tools and Techniques for Penetrating Testing
Tools and Techniques for Penetrating Testing
Thu 27th Feb 2025
Thu 15th May 2025
Thu 7th Aug 2025
Thu 30th Oct 2025







 Top Rated Course
Top Rated Course



 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


