We may not have the course you’re looking for. If you enquire or give us a call on 01344203999 and speak to our training experts, we may still be able to help with your training requirements.
We ensure quality, budget-alignment, and timely delivery by our expert instructors.
In an era dominated by the digital realm, web applications have become the lifeblood of modern businesses and organisations. From e-commerce platforms to online banking and social media networks, these applications handle sensitive data, transactions, and user interactions daily. However, as web applications flourish, so do the threats and vulnerabilities that can compromise their security. This is where Web Application Firewalls (WAFs) step in as the guardians of online integrity.
A Web Application Firewall protects online services by defending against cyberattacks and ensuring data security and service availability. In this comprehensive blog, we will guide you through Web Application Firewalls, dissecting their purpose, functionality, and significance.
Table of content
1) Understanding Web Application Firewall (WAF)
2) Importance of Web Application Firewall
3) Types of Web Application Firewalls
4) How does a WAF work?
5) Features of Web Application Firewall (WAF)
6) Security models for Web Application Firewalls (WAFs)
7) Conclusion
Understanding Web Application Firewall (WAF)
A Web Application Firewall (WAF) is a security tool designed to protect web applications from various online threats and attacks. It acts as a shield between your web application and potential malicious actors, helping to safeguard your web-based services, data, and users. WAFs are essential for enhancing the security of websites and web applications, as they focus on the application layer of the OSI model, specifically targeting HTTP and HTTPS traffic.

Importance of Web Application Firewall
The importance of a (WAF) cannot be overstated in today's digital landscape, where web applications are vulnerable to a wide array of cyber threats. Here are some key reasons why a WAF is essential:
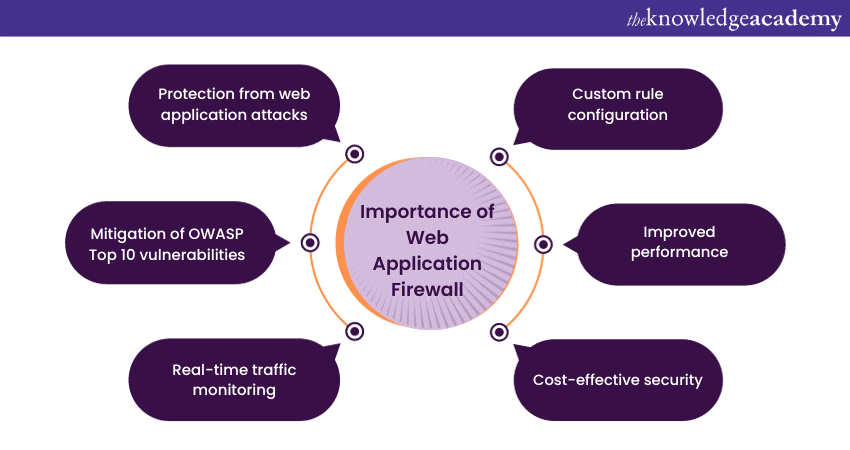
a) Protection from web application attacks: Web applications are prime targets for cyberattacks. A WAF acts as a shield, effectively mitigating threats like SQL injection, Cross-Site Scripting (XSS), Cross-Site Request Forgery (CSRF), and more. It helps prevent data breaches, unauthorised access, and other malicious activities.
b) Mitigation of OWASP Top 10 vulnerabilities: The Open Web Application Security Project (OWASP) publishes a list of the top 10 web application vulnerabilities. A WAF is a crucial tool for addressing these vulnerabilities, ensuring your application's compliance with security best practices.
c) Real-time traffic monitoring: WAFs continuously monitor incoming and outgoing web traffic. This real-time monitoring allows them to identify and block suspicious activities instantly, reducing the risk of attacks and data breaches.
d) Custom rule configuration: WAFs allow for the creation of custom security rules tailored to your web application's specific needs. This flexibility ensures that your WAF adapts to your unique security requirements.
e) Improved performance: Although primarily a security tool, a well-configured WAF can also enhance your application's performance. By optimising and caching content, it can mitigate the impact of DDoS attacks and reduce the load on your web servers.
f) Cost-effective security: Implementing a WAF can be a cost-effective security measure when compared to dealing with the consequences of a security breach. The financial and reputational damage that can result from an attack often far exceeds the cost of a WAF.
Unlock the power of specialised Business Relationship Management with ITIL® 4 Specialist Business Relationship Management Training. Elevate your skills and drive your career forward.
Types of Web Application Firewalls
Web Application Firewalls (WAFs) come in various types, each with its own characteristics and deployment options. These different types allow organisations to choose the one that best fits their specific security needs. Here are the primary types of WAF:
Network-based WAF:
Location: Deployed at the network perimeter, typically between the internet and the web server.
Functionality: Focuses on filtering and monitoring traffic at the network level, including inspecting packets and filtering based on source and destination IP addresses.
Pros: Provides a central point of protection for multiple applications, can protect against volumetric attacks, and is often easier to manage for large-scale environments.
Cons: May have limitations in terms of deep application-layer inspection.
Host-based WAF:
Location: Installed directly on the web server or as part of the web server software.
Functionality: Monitors and filters traffic on the host where the web application resides. It has better visibility into application layer traffic.
Pros: Provides granular control over the security policies and can detect and mitigate application-specific vulnerabilities.
Cons: Requires installation and management on individual servers, which can be more complex for larger deployments.
Cloud-based WAF:
Location: Hosted in the cloud and configured to protect web applications remotely without the need for on-premises hardware or software.
Functionality: Monitors traffic en route to the web server and can be implemented easily for cloud-hosted or on-premises applications.
Pros: Quick and scalable deployment, often provided as a managed service, and can protect applications regardless of their location.
Cons: May introduce latency, and the level of control over security policies can vary depending on the service provider.
Appliance-based WAF:
Location: A physical or virtual appliance that is deployed on-premises within the organisation's data centre or cloud infrastructure.
Functionality: Offers the same protection as other WAF types but within a dedicated appliance that is typically self-contained.
Pros: Provides control and isolation, especially for organisations with stringent compliance requirements, and can be fine-tuned for specific needs.
Cons: Requires hardware or virtualised infrastructure, which might be costlier to set up and maintain.
Serverless WAF:
Location: Designed for serverless computing environments, such as AWS Lambda, Azure Functions, and Google Cloud Functions.
Functionality: Offers application layer security for serverless functions and APIs, often integrated directly into the serverless platform.
Pros: Designed to protect functions and APIs in a lightweight, serverless environment.
Cons: Limited to protecting specific functions or APIs and might not be as feature-rich as traditional WAFs.
Accelerate your IT career with ITIL® 4 Specialist: High Velocity IT Training. Join now and propel your skills to the next level!
How does a WAF work?
A WAF works by monitoring and filtering the incoming and outgoing web traffic to a web application or website. It is designed to protect the application at the application layer of the OSI model (Layer 7) and to identify and block malicious or unwanted traffic while allowing legitimate traffic to pass through. Here's how a WAF typically works:
a) Traffic inspection: When a user sends a request to a web application, the traffic passes through the WAF, which acts as a security checkpoint. This inspection occurs at both the request (inbound) and response (outbound) stages.
b) Signature-based filtering: WAFs use predefined security rules and signatures to identify known patterns of malicious traffic. These rules are based on common web application attack techniques and vulnerabilities, such as SQL injection, Cross-Site Scripting (XSS), and more. If the incoming traffic matches any of these signatures, it is flagged for further action.
c) Behavioural analysis: In addition to signature-based filtering, some WAFs employ behavioural analysis to detect anomalies. They establish a baseline of normal traffic behaviour and flag or block traffic that deviates from this baseline. This helps in identifying zero-day attacks and previously unknown threats.
d) Access Control Lists (ACLs): WAFs can be configured with access control lists to allow or deny traffic based on IP addresses, geographic locations, or specific user agents. This helps control access to the web application and reduces the attack surface.
e) Rate limiting: WAFs often include rate-limiting features to prevent abuse of the application. They can restrict the number of requests a user or IP address can make within a specific time frame, mitigating brute-force and DDoS attacks.
f) Positive and negative security models: WAFs can operate using either positive or negative security models. In a negative security model, they block traffic that matches known attack patterns. In a positive security model, they allow only known good traffic and block everything else. The choice of model depends on the organisation's security posture.
g) Logging and monitoring: WAFs log all traffic and security events for analysis. This log data can be invaluable for understanding attack attempts and patterns. It also helps in compliance and auditing.
Lead your organisation to digital excellence with ITIL® 4 Leader: Digital and IT Strategy (DITS) Training!
Features of Web Application Firewall (WAF)
WAF come with a variety of features and capabilities to provide robust security for web applications. These features are designed to protect against various types of threats and vulnerabilities. Here are some common features of WAFs:
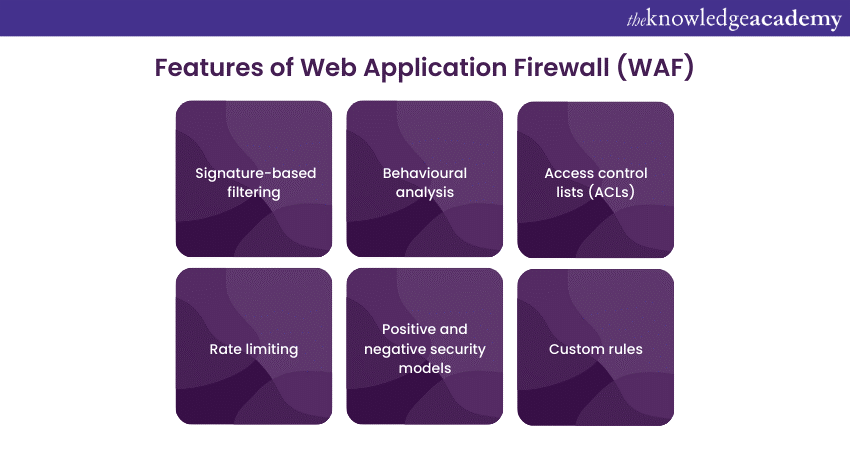
1) Signature-based filtering: WAFs use predefined signatures and patterns to identify and block known web application attacks, such as SQL injection, Cross-Site Scripting (XSS), and Cross-Site Request Forgery (CSRF).
2) Behavioural analysis: Some WAFs employ behavioural analysis to detect anomalies in web traffic. They establish a baseline of normal behaviour and flag or block traffic that deviates from this baseline.
3) Access control lists (ACLs): ACLs allow you to control access to your web application by specifying which IP addresses, geographical locations, or user agents are allowed or denied access.
4) Rate limiting: WAFs can limit the number of requests that users or IP addresses can make within a specific time frame. This helps prevent brute-force attacks and DDoS attacks.
5) Positive and negative security models: WAFs can operate using either a positive security model (allow only known good traffic) or a negative security model (block known bad traffic). The choice of model depends on the organisation's security strategy.
6) Custom rules: Organisations can create custom security rules to tailor the WAF's protection to their specific needs. This is useful for applications with unique security requirements.
Embrace sustainability in the digital age with ITIL® 4 Specialist: Sustainability in Digital and IT (ITIL® SDIT) Training now!
Security models for Web Application Firewalls (WAFs)
WAF employ different security models to protect web applications from various threats and vulnerabilities. The choice of security model depends on an organisation's security requirements, policies, and the nature of the web applications they are safeguarding. Here are the two primary security models for WAFs:
Negative security model
In a negative security model, the WAF assumes that all traffic is potentially malicious, and it only allows known "good" traffic to pass. The WAF is configured to block traffic that matches known attack signatures and patterns. This model is essentially a blacklist approach.
Advantages:
a) Effective at blocking known threats: Since it relies on predefined rules and signatures, it is particularly effective at blocking well-known and documented attacks.
b) Simple and easy to implement: It's relatively straightforward to set up and provides immediate protection based on a database of known threats.
Challenges:
a) Vulnerable to zero-day attacks: Negative security models may not detect or block new, previously unknown vulnerabilities or attack techniques, making them vulnerable to zero-day attacks.
b) False positives: Overly aggressive filtering can lead to blocking legitimate traffic, causing false positives and potentially impacting user experience.
Positive security model
In a positive security model, the WAF allows only explicitly defined, legitimate traffic to access the web application. It builds a whitelist of known valid requests and blocks everything else. This model focuses on explicitly permitting only known good traffic, making it a whitelist approach.
Advantages:
a) Effective at blocking unknown attacks: Positive security models are more robust against zero-day attacks because they permit only legitimate traffic, and any deviations are automatically blocked.
b) Minimal false positives: Since the focus is on allowing known good traffic, there are fewer false positives, which can improve the user experience.
Challenges:
a) Initial setup complexity: Configuring a positive security model requires a thorough understanding of the application's behaviour, which can be time-consuming and complex.
b) Maintenance overhead: Updating and maintaining the whitelist to accommodate changes in the application can be challenging, especially for dynamic applications.
Conclusion
This comprehensive guide has shed light on the crucial role that Web Application Firewalls (WAFs) play in safeguarding web applications in today's digital landscape. As web application attacks continue to evolve and threaten the security of online services, a WAF stands as a formidable defence mechanism.
Elevate your career with ITIL® Certification Training. Join us to master the art of IT service management!
Frequently Asked Questions
What are the Other Resources and Offers Provided by The Knowledge Academy?

The Knowledge Academy takes global learning to new heights, offering over 3,000 online courses across 490+ locations in 190+ countries. This expansive reach ensures accessibility and convenience for learners worldwide.
Alongside our diverse Online Course Catalogue, encompassing 19 major categories, we go the extra mile by providing a plethora of free educational Online Resources like News updates, Blogs, videos, webinars, and interview questions. Tailoring learning experiences further, professionals can maximise value with customisable Course Bundles of TKA.
Upcoming IT Security & Data Protection Resources Batches & Dates
Date
 ITIL® 4 Foundation Certification Course
ITIL® 4 Foundation Certification Course
Wed 26th Mar 2025
Mon 31st Mar 2025
Wed 2nd Apr 2025
Sat 5th Apr 2025
Mon 7th Apr 2025
Wed 9th Apr 2025
Mon 14th Apr 2025
Wed 16th Apr 2025
Tue 22nd Apr 2025
Mon 28th Apr 2025
Wed 30th Apr 2025
Tue 6th May 2025
Sat 10th May 2025
Mon 12th May 2025
Wed 14th May 2025
Mon 19th May 2025
Wed 21st May 2025
Tue 27th May 2025
Mon 2nd Jun 2025
Wed 4th Jun 2025
Sat 7th Jun 2025
Mon 9th Jun 2025
Wed 11th Jun 2025
Mon 16th Jun 2025
Wed 18th Jun 2025
Mon 23rd Jun 2025
Wed 25th Jun 2025
Mon 30th Jun 2025
Wed 2nd Jul 2025
Mon 7th Jul 2025
Wed 9th Jul 2025
Sat 12th Jul 2025
Mon 14th Jul 2025
Wed 16th Jul 2025
Mon 21st Jul 2025
Wed 23rd Jul 2025
Mon 28th Jul 2025
Wed 30th Jul 2025
Mon 4th Aug 2025
Wed 6th Aug 2025
Sat 9th Aug 2025
Mon 11th Aug 2025
Wed 13th Aug 2025
Mon 18th Aug 2025
Wed 20th Aug 2025
Mon 25th Aug 2025
Mon 1st Sep 2025
Wed 3rd Sep 2025
Mon 8th Sep 2025
Wed 10th Sep 2025
Sat 13th Sep 2025
Mon 15th Sep 2025
Wed 17th Sep 2025
Mon 22nd Sep 2025
Wed 24th Sep 2025
Mon 29th Sep 2025
Wed 1st Oct 2025
Mon 6th Oct 2025
Wed 8th Oct 2025
Sat 11th Oct 2025
Mon 13th Oct 2025
Wed 15th Oct 2025
Mon 20th Oct 2025
Wed 22nd Oct 2025
Mon 27th Oct 2025
Wed 29th Oct 2025
Mon 3rd Nov 2025
Wed 5th Nov 2025
Sat 8th Nov 2025
Mon 10th Nov 2025
Wed 12th Nov 2025
Mon 17th Nov 2025
Wed 19th Nov 2025
Mon 24th Nov 2025
Wed 26th Nov 2025
Mon 1st Dec 2025
Wed 3rd Dec 2025
Mon 8th Dec 2025
Wed 10th Dec 2025
Sat 13th Dec 2025
Mon 15th Dec 2025
Wed 17th Dec 2025






 Top Rated Course
Top Rated Course


 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


