We may not have the course you’re looking for. If you enquire or give us a call on 01344203999 and speak to our training experts, we may still be able to help with your training requirements.
We ensure quality, budget-alignment, and timely delivery by our expert instructors.

Our world is rising rapidly with technological advancements, but at the same time, its challenges are also increasing. In particular, Cyber Security Attacks show no signs of slowing down, threatening the growth of many businesses. It is a mighty challenge that needs to be overcome.
According to Checkpoint, Cyber-attacks against software vendors increased by about 146 per cent in 2021 compared to 2020. It just goes to show you the seriousness of the problem. And if a business wants to survive and improve its public reputation, it needs to strengthen its Cyber Security capabilities.
In this blog, you will learn everything about Cyber Security attacks and how to prevent your data from Cyber-attacks.
Sign up for a course on Certified Cyber Security Professional (CCS-PRO) and become an expert on Cyber Security!
Table of Contents
1) What is a Cyber-attack? - Explained
2) Who’s responsible for Cyber-attacks?
3) Let’s learn why Cyber-attacks happen
4) Targets of Cyber-attacks – Let's find out
5) Let’s find out the 12 different types of Cyber-attacks
6) What is attack in Cyber Security and how does it work?
7) How to prevent Cyber-attacks?
8) Why is Cyber Security important?
9) Conclusion
What is a Cyber Attack? - Explained
Cyber Security attacks are breaches and intrusions launched by cyber criminals and attackers with malicious intent to gain access to the victim's data. A cyber-attack can be found to steal sensitive data, alter the sensitive data or threaten the victim in an attempt to extort money. Various tools can do cyber-attacks like malware, ransomware, trojans, SQL injections, Denial of Service attacks, etc.
Who’s responsible for Cyber-attacks?
People who carry out Cyber-attacks can either be individuals or a group working with each other with a malicious intention to carry out cyber-attacks. These attackers can be classified as
1) Hackers
2) Cybercriminals
3) Threat actors
4) Bad or Malicious actors
5) Coordinated group attacks
Definition of Cyber Security attack
Hackers or Cybercriminals launch a Cyber Security attack against one or multiple systems, networks, devices or against an institution.
Register for a course on Introduction To System And Network Security and acquire the skill set to protect systems and networks!
Let’s learn why Cyber-attacks happen
Cyber-attacks are conducted by people with malicious intent exploiting victims by stealing or gaining access to their data. These people can be Cybercriminals, Cyberterrorists, hackers and hacktivists. Cyber-attacks happen because of the motivations behind them. Their motivations can be political gain, personal gain and conduct criminal activities.
People with any motivation for personal gain will try to get financial gain by launching attacks like ransomware attacks, money theft, data theft or conducting activities that can disrupt business activity.
And outside attacks are not the only reason behind the business disruption. Insider attacks in the form of disgruntled or unhappy former and current employees of an organisation could also do it.
Anonymous is a well-known decentralised hacktivist group responsible for many cyber-attacks. Hacktivists are hackers who have a little bit of activism behind their intention. Anonymous launched cyber-attacks when most payment servicing companies like PayPal, MasterCard and Visa halted their service with WikiLeaks. They temporarily took down the sites of MasterCard and Visa in support of Wikileaks.
It is worth noting that WikiLeaks was one of the pioneers of hacktivism and was responsible for releasing several top-secret pieces of information about the US government to the public.
Targets of Cyber-attacks – Let's find out
The targets of these attacks vary based on the motivation of these attackers. If their intention is hacktivism, they are more likely to target public institutions and High-Profile Individuals. If their intention is financial theft, they are more likely to target financial institutions and may launch attacks using ransomware.
1) Government Institutions: There’s a general mistrust among the public of Government Institutions, and hacktivists exploit this mistrust and attack such institutions and try to gather public support for them.
2) Organisations: Big tech companies and other corporations have been on the receiving end of many cyber-attacks in recent years. There are several reasons behind it. It can be either to extort money from them or could be done to damage their business and reputation.
3) High-Profile Individuals: Cyber-attacks on High profile and high-net-worth individuals are nothing new. These attacks are made either to garner attention or for extortion.
4) Banks or Financial Institutions: Attacks on Financial institutions are primarily made to steal money. These attacks are caused by hacking into the server of banks or other financial institutions and illegally wiring money to the attacker's bank account.
5) Individuals: Attacks on Individuals are made for blackmailing, extorting or damaging the individual's reputation.
Let’s find out the 12 different types of Cyber-attacks
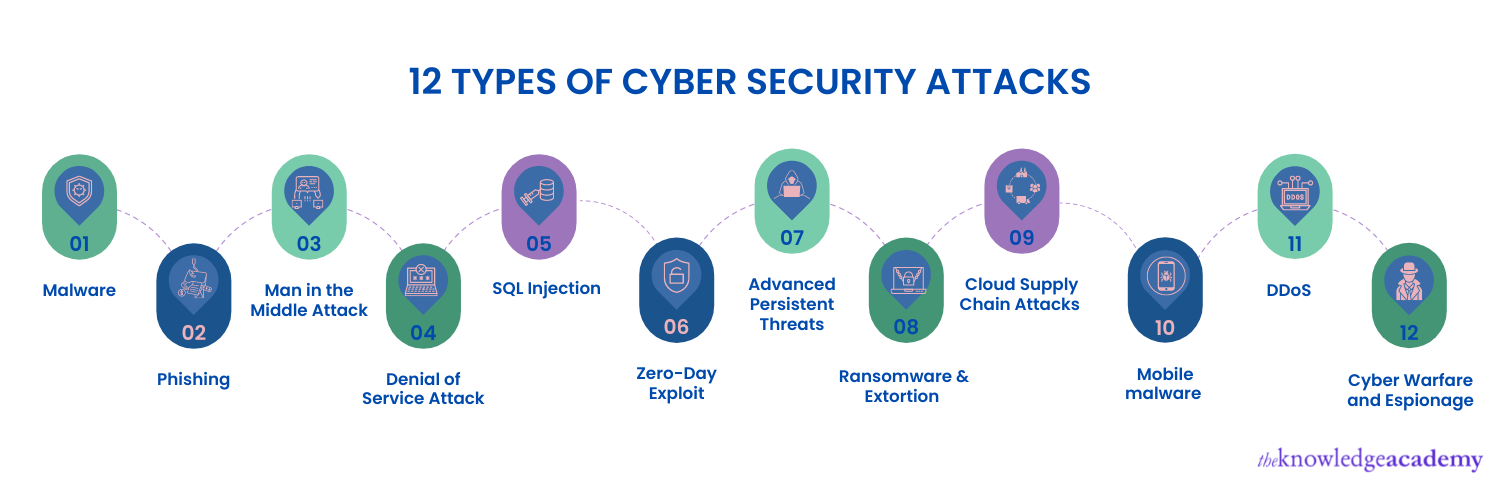
a) Cyber Warfare and Espionage
b) Malware
c) Ransomware & Extortion
d) Cloud Supply Chain Attacks
e) Phishing
f) Mobile malware
g) SQL injection
h) Man in the Middle
i) Zero-day Attack
j) Denial of Service
k) DDoS
l) DNS Tunneling
What is attack in Cyber Security and how does it work?
Cyber-attacks work by penetrating a victim's system and network. Attackers won't launch an attack on an organisation immediately. Like predators on the hunt, they will look out for weakness first. They will perform several test attacks to test the network security, and if they can't find any liability, they will switch their targets.
Next, they will test out the security systems of their partners and third-party vendors. If they find any weakness, they will use it as a springboard to launch attacks on the primary target.
Sign up for a course on Social Engineering Training and gain in-depth knowledge of Social Engineering!
How to prevent Cyber-attacks?

1) Authentication: Improve authentication using Multifactor authentication and other latest techniques. Having a multifactor authentication like 2 Factor Authentication and additional layers of security, it is possible to prevent outside breaches.
2) Encryption: Strong encryption can add an extra layer of security. Encryption is a simple process; you can do this very quickly. Individuals with little time but still want to protect their files can use basic encryption in applications like MS Zip and WinRAR. But when we are talking about the protection of data for organisations, they can use Professional grade software that can give you a higher level of encryption.
3) Superior Internal controls: Improve internal security and access controls in the organisation.
4) Third-party Vendors: Hackers breach an organisation's security by bypassing third-party vendors' security. By Improving the awareness and security infrastructure of your partners and third-party vendors, you can effectively strengthen your organisation's overall security.
5) Cloud and Backup: A proper backup on the cloud prevents unnecessary data loss.
6) Dedicated Security application: Having a reliable Security application and tool can give you peace of mind as it will continually monitor threats.
7) Regular update: Updating systems and software regularly ensures better protection. Software developers often release patches that can fix any security issues in previous versions.
8) Increased awareness: Improved awareness about Cyber security and its threats can make a massive difference in improving your security. Getting a grasp is the key, and ensuring everyone (Employees, Partners, Supply Chain Vendors and third-party vendors) knows about the seriousness and impacts of Cyber security threats will have a profound effect on preventing cyber-attacks.
9) Avoid using Public Networks: Public networks are the primary culprit behind many Cyber-attacks because they barely have any security apparatus making them an easy target for launching attacks. So, avoiding the use of public networks altogether can effectively prevent Cyber-attacks.
Why is Cyber Security important?
Cyber Security is essential because it can protect the data of organisations and individuals by preventing Cyber-attacks like Data breaches, insider attacks and other types of attacks. It gives many organisations a sense of security since it continuously monitors for threats. Not only that, but it also has a proactive approach and will try to alert about any threats well in advance. This early warning system allows organisations and software vendors to work on security issues and gives them sufficient time to release an upgraded security patch. Thus, getting awareness and implementing Cyber Security Essentials measures can be a game-changer.
Conclusion
We hope you have understood everything about Cyber Security Attacks and how to protect your systems and data from various Cyber-attacks. In addition, you would have also learnt about the 12 different types of Cyber-attacks with examples.
If interested, check out our courses on Cyber Security Training and learn about the Cyber Threats affecting businesses!
Upcoming IT Security & Data Protection Resources Batches & Dates
Date
 Certified Cyber Security Professional (CCS-PRO)
Certified Cyber Security Professional (CCS-PRO)
Fri 21st Mar 2025
Fri 23rd May 2025
Fri 22nd Aug 2025
Fri 5th Dec 2025






 Top Rated Course
Top Rated Course



 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


