We may not have the course you’re looking for. If you enquire or give us a call on 01344203999 and speak to our training experts, we may still be able to help with your training requirements.
We ensure quality, budget-alignment, and timely delivery by our expert instructors.
Picture a fortress, a digital one, with a special zone that welcomes strangers while keeping the residents safe and secure! In the realm of networking, this fortress is your internal network, and the special zone is a Demilitarized Zone (DMZ). It's where public-facing services like email servers and websites reside, protected yet accessible. A DMZ essentially ensures that your precious internal data stays secure even if a guest turns rogue. Dive in as this blog explores What is DMZ in intricate detail, outlining its vital features, benefits, risks and more!
Table of Contents
1) What is a DMZ Network?
2) The Importance of DMZ
3) Key Features of DMZ
4) How Does a DMZ Network Work?
5) Advantages of Using a DMZ
6) Disadvantages of Using a DMZ
7) Designing and Architecting DMZ Networks
8) Examples of DMZs
9) Conclusion
What is a DMZ Network?
In the field of computer security, a DMZ stands for a demilitarised zone and is also called a perimeter network (or screened subnet). A DMZ is a logical or physical subnet that isolates a Local Area Network (LAN) from untrusted networks such as the public Internet. Any service provided to users on the public Internet must be set up in the DMZ network.
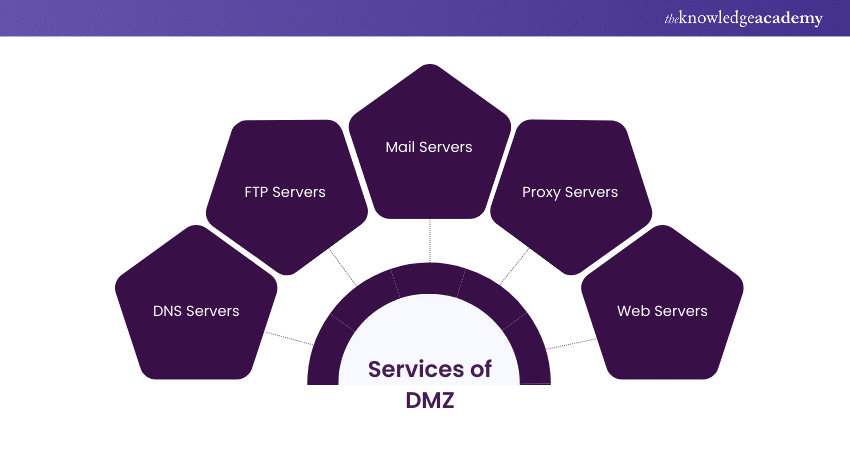
The servers and resources in the DMZ network can be tapped into from the Internet but are isolated and have limited LAN access. The external-facing servers, resources and services are usually placed in the DMZ. The Services include:
1) Web
2) Email
3) Proxy servers
4) Domain Name System (DNS)
5) File Transfer Protocol (FTP)
6) Voice over Internet Protocol (VoIP)
This approach provides the LAN with an additional layer of security that restricts a hacker from gaining direct access to internal servers and data from the Internet.
The Importance of DMZ
DMZs offer a level of network segmentation that helps shield internal corporate networks. These subnetworks stop remote access to internal servers and resources, making it nearly impossible for attackers to access the internal network.
This strategy is helpful for both individual usage and large organisations. Businesses can place servers and applications that are exposed to the Internet in a DMZ, which separates them from the internal network. The DMZ isolates these resources, and so in case they are compromised, the attack is unlikely to cause damage, exposure, or loss.
Key Features of DMZ
A DMZ is vital for protecting an organisation’s internal network from external threats. Here are some of its key features:
1) Isolation: Firewalls isolate the DMZ from both the internal network and the Internet. This ensures that the internal network remains protected even if a DMZ server is compromised.
2) Network Segmentation: DMZ segments network traffic, separating public-facing services (such as web servers) from internal resources. This minimises the risk of external attacks reaching sensitive internal systems.
3) Redundancy: Many organisations implement redundant DMZs to ensure high availability and resilience against attacks. If one DMZ fails, another can take over without disrupting services.
4) Monitoring and Logging: Robust monitoring and logging are essential features. All traffic in and out of the DMZ is heavily monitored to promptly detect and respond to suspicious activities.
5) Access Control: Strict access control policies allow only authorised traffic. This includes firewalls, intrusion detection/prevention systems, and other security measures.
6) Buffer Zone: The DMZ acts as a buffer zone between the untrusted external network (Internet) and the trusted internal network, providing an additional layer of defence.
These features collectively enhance an organisation's security posture by creating a multi-layered defence strategy, often called "defence-in-depth".
Want to learn how to deploy robust firewalls? Our Introduction to System and Network Security Course will guide you - Sign up now!
How Does a DMZ Network Work?
It's essential for businesses to make their web server accessible to the Internet, especially when customers use their public website. The web server is installed on a separate computer from internal resources to protect the corporate LAN.

A DMZ is ideally located between two firewalls and the DMZ firewall setup ensures that incoming network packets are detected by a firewall (or other security tools) before they make it to the DMZ-hosted servers. So, even if sophisticated attackers can get past the first firewall, they must access the services in the DMZ before they can damage a business.
If an attacker breaches the external firewall and compromises a system in the DMZ, they must pass an internal firewall before gaining access to sensitive data. Organisations that comply with regulations such as Health Insurance Portability and Accountability Act (HIPAA) sometimes install a proxy server in the DMZ. This enables organisations to simplify the monitoring and recording user activity and centralise web content filtering.
Stay ahead in IT interviews – prepare with expert Networking Interview Questions!
Advantages of Using a DMZ
The separation and control that DMZs offer make it easier to safeguard internal resources, provide access, and reduce the risks of cyberattacks. The benefits of a DMZ include:
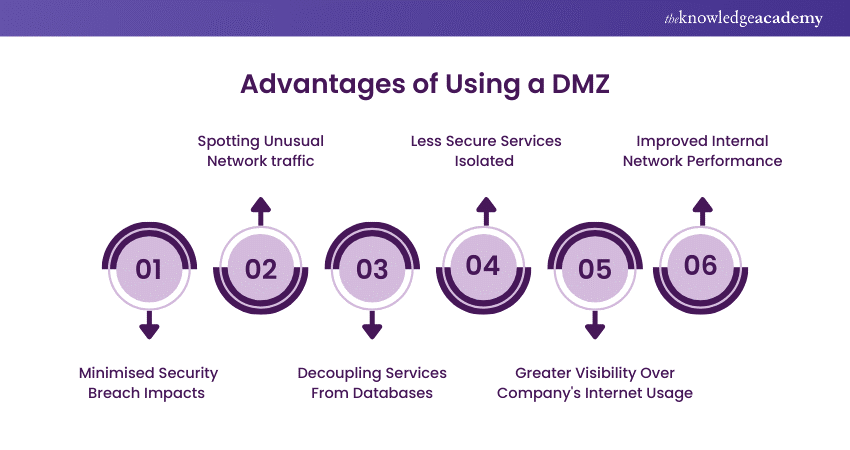
1) Minimise Security Breach Impacts: DMZs limit the scope of successful security breaches. If hackers penetrate a DMZ, they only have access to the resources within that DMZ. Network access controls restrict their ability for lateral movement and prevent them from surveying the internal network.
2) Spotting Unusual Network traffic: A DMZ’s extra security measures offer administrators a better chance to detect unusual network traffic and seal the breach quickly.
3) Decoupling Services From Databases: External-facing systems often require access to proprietary databases and other resources. For example:
a) Web servers need access to customer information.
b) Email servers need access to company directories.
c) API servers need access to backend databases.
However, placing these proprietary resources on a public-facing server can pose high risks. Hosting the front-end server within DMZ while holding sensitive backend resources on the protected internal network helps avoid those risks.
4) Isolate Less Secure Services: FTP and services with fewer security controls can become Cyber attack targets. Holding the FTP servers in their own DMZ reduces the risk of a successful attack permeating the internal network.
5) Internet Access for Internal Users: Access control rules compel all internal internet use through a dedicated proxy server in a DMZ. This gives administrators greater visibility and control over the company’s internet usage.
6) Improve Internal Network Performance: Frequently accessed web servers inflict high network loads. Placing these servers in a DMZ removes the burden of the internal network. Administrators can optimise the DMZ subnet for more efficient handling of those loads.
Expand your Cyber security knowledge base and skillset with our Certified Cyber Security Professional (CCS-PRO) Course - Sign up now!
Disadvantages of Using a DMZ
Despite its security features, a DMZ can be a risky endeavour as outlined below:

1) Authenticated Data Access Risk: An attacker with authenticated data can access the system as an authorized user.
2) Public Network Data Leakage: The data from public networks to external networks can be leaked or replicated.
3) Lack of Internal Data Protections: There are no internal protections, which means your employees and authorized users will still access the sensitive data you store for your company.
4) False Sense of Security in DMZ: DMZ can provide a false sense of security. Hackers come up with new nefarious ways of slipping past security systems every day. Even when your build is complete, you must monitor the environment relentlessly.
5) DMZ vs Cloud: Some experts claim that the cloud has made the DMZ network obsolete. Without network servers, you may not have anything to protect.
Maximise Your Streaming Experience! Connect Chromecast to WiFi with This Guide.
Designing and Architecting DMZ Networks
There are several ways a DMZ can be used to build a network. The two primary methods of accomplishing this are the single firewall (or a three-legged model) or dual firewall configuration, both of which can be expanded to create complex DMZ architectures that align with network requirements:
Single Firewall Configuration
A single firewall is a modest approach to network architecture and has a minimum of three network interfaces. The DMZ is placed inside this firewall. The ISP connects to the external network device, the second device connects to the internal network, and the third handles the connections within the DMZ.
Dual Firewall Configuration
Creating a DMZ using two firewalls offers greater security. The frontend firewall is built only to allow traffic headed towards the DMZ. The second firewall (the backend firewall) is only in charge of traffic from the DMZ to the internal network.
To further increase the level of protection, firewalls built by separate vendors are utilised, as there are fewer possibilities of encountering the same security vulnerabilities. While this is more effective, it's a costlier scheme to implement across an extensive network.
Become an expert at monitoring malware behaviour and propagation through our comprehensive Malware Analysis Training - Register now!
Examples of DMZs
Here are some examples that showcase the various ways DMZs are utilised:
1) Cloud Services: Some cloud services, like Microsoft Azure, use a hybrid security approach to implement a DMZ between an organisation's virtual and on-premises networks. This method is typically used when the organisation's applications run partly on-premises and the virtual network.
2) Home Networks: A DMZ can be useful even in a home network where a broadband router establishes connection between computers (and other devices) and the internet. Some home routers include a DMZ host feature, which can be contrasted with the DMZ subnetwork used in organisations with more devices than in a home. This feature designates one device on the home network to function outside the firewall, acting as the DMZ.
3) Industrial Control Systems (ICS): DMZs offer a potential solution to ICS's security risks. The merging of Industrial equipment with information technology (IT) is creating a larger threat surface. Much of the industrial technology equipment is not designed to handle Cyber attacks in the same way IT devices are. This is where a DMZ can provide greater network segmentation, making it difficult for ransomware to pervade networks.
Conclusion
Understanding What is DMZ is vital for any aspiring Network Security professional as it acts as an essential security buffer, safeguarding internal networks from external threats. DMZ accomplishes this by isolating public-facing public-facing services and even if attackers breach the first layer of defence, they must still overcome additional barriers before accessing any sensitive data.
Learn how to identify security solutions for cloud environments in our CCNP Security Training - Sign up now!
Frequently Asked Questions
What is the Goal of DMZ?

A DMZ aims to offer access to untrusted networks, like the internet, while keeping private networks or Local Area Networks (LANs) secure.
Is a DMZ the Same as VPN?

No. There’s a key difference between the two. A DMZ isolates public-facing services from the internal network. A Virtual Private Network (VPN) demonstrates an encrypted network tunnel between a user and a remote network (often over the public internet). When comparing Proxy vs VPN, it's worth noting that a VPN works on the user end to shield their online activities from third parties.
What are the Other Resources and Offers Provided by The Knowledge Academy?

The Knowledge Academy takes global learning to new heights, offering over 3,000 online courses across 490+ locations in 190+ countries. This expansive reach ensures accessibility and convenience for learners worldwide.
Alongside our diverse Online Course Catalogue, encompassing 19 major categories, we go the extra mile by providing a plethora of free educational Online Resources like News updates, Blogs, videos, webinars, and interview questions. Tailoring learning experiences further, professionals can maximise value with customisable Course Bundles of TKA.
What is The Knowledge Pass, and How Does it Work?

The Knowledge Academy’s Knowledge Pass, a prepaid voucher, adds another layer of flexibility, allowing course bookings over a 12-month period. Join us on a journey where education knows no bounds.
What are the Related Courses and Blogs Provided by The Knowledge Academy?

The Knowledge Academy offers various IT Support and Solution Courses, including the IT Fundamentals Course and the VPN Course. These courses cater to different skill levels, providing comprehensive insights into What are Network Protocols.
Our IT Infrastructure & Networking Blogs cover a range of topics related to Network Security, offering valuable resources, best practices, and industry insights. Whether you are a beginner or looking to advance your IT Networking skills, The Knowledge Academy's diverse courses and informative blogs have got you covered.
Upcoming IT Infrastructure & Networking Resources Batches & Dates
Date
 Introduction to System and Network Security
Introduction to System and Network Security
Fri 16th May 2025
Fri 18th Jul 2025
Fri 19th Sep 2025
Fri 21st Nov 2025






 Top Rated Course
Top Rated Course



 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


