We may not have the course you’re looking for. If you enquire or give us a call on 01344203999 and speak to our training experts, we may still be able to help with your training requirements.
We ensure quality, budget-alignment, and timely delivery by our expert instructors.

In a world where digital interactions are integral to our daily lives, the concept of Hacking often sparks curiosity and concern. But What is Hacking, really? It encompasses both the positive efforts of Ethical Hackers who enhance our security and the harmful actions of cybercriminals who exploit vulnerabilities.
So, what happens when someone hacks a system? More importantly, how can we protect ourselves? The key lies in awareness and prevention. Understanding What is Hacking and how to counter it can safeguard your personal and professional data. Let's look at various types of Hacking and the precautions you may take to keep your systems secure.
Table of Contents
1) What is Hacking?
2) Types of Hacking
3) The Most Hacker-Prone Devices
4) How Much Harm Can Hackers Cause?
5) Historic Cyberattacks and Hackers
6) The Difference Between Hackers and Cyber Attackers
7) Risks Linked to Hacking for Banks and Financial Institutions
8) How to Prevent Hacking?
9) Conclusion
What is Hacking?
Hacking occurs when an individual exploits vulnerabilities in a computer system or network in order to achieve unauthorised access or control. Hackers employ different strategies to breach security systems, swipe confidential data, or interrupt services. Nevertheless, not all Hacking is against the law; some hackers aim to discover weaknesses and enhance security.
As technology progresses, Hacking methods are becoming increasingly intricate. It is essential for individuals and organisations to remain knowledgeable about the most recent techniques and strategies to safeguard themselves. becoming an Ethical Hacker helps individuals stay ahead of these evolving threats and contribute to better security practices.
Types of Hacking
Hacking can be divided into several categories based on the intent and legality of the actions. Here are the three main types of Hacking:
1) White Hat / Ethical Hacking
White Hat hackers, or Ethical Hackers, utilise their skills for both defence and beneficial purposes. Here’s what they do:
1) Purpose: Use Ethical Hacking skills for good, focusing on improving security.
2) Employment: Hired by companies or governments to identify and fix vulnerabilities.
3) Actions: Perform controlled Hacking attempts to reveal weaknesses before malicious hackers can exploit them.
4) Impact: Help organisations strengthen their Cyber Security defences.
2) Black Hat Hacking
Black hat hackers are considered the "bad guys" of the Hacking community. They participate in illegal actions to either cause harm or gain financially. Their characteristics include:
1) Purpose: Engage in illegal activities with malicious intent.
2) Targets: Exploit system vulnerabilities for financial gain, theft, or to cause harm.
3) Focus: Often targets personal information, intellectual property, or financial data.
4) Outcome: Sell stolen data on the dark web or exploit it for identity theft and fraudulent activities.
3) Grey Hat Hacking
Grey hat hackers are positioned between white hat and black hat hackers. Here is what makes them different:
1) Purpose: Operate between ethical and malicious Hacking.
2) Actions: Exploit security weaknesses without permission but without harmful intent.
3) Objective: Increase knowledge about weaknesses, occasionally through the disclosure of flaws.
4) Consequences: This could result in legal problems, as unauthorised Hacking is still against the law, even if no harm is intended.
Unlock professional Ethical Hacking skills and elevate your career in the Cyber Security field with our Ethical Hacking Professional – sign up today!
The Most Hacker-Prone Devices
Certain devices are more susceptible to Hacking than others. Hackers often focus on gadgets that store sensitive data or have less robust security features.
1) Smart Devices
a) Target: Smartphones and IoT devices.
b) Vulnerability: Android devices are more exposed due to open-source and inconsistent software development.
c) Risk: Data theft, corruption, and exploitation of weak IoT security.
2) Webcams
a) Target: Built-in webcams on computers.
b) Vulnerability: Easily compromised through Remote Access Trojans (RAT).
c) Risk: Spying, reading messages, monitoring browsing, and hijacking webcams.
3) Routers
a) Target: Internet routers.
b) Vulnerability: Hackers can intercept data and access connected devices.
c) Risk: DDoS attacks, DNS spoofing, cryptomining, and data interception.
4) Email
a) Target: Email accounts.
b) Vulnerability: Propagation of malicious software, ransomware, and phishing attempts.
c) Risk: Stealing sensitive data, sharing harmful links, and infecting systems.
5) Jailbroken Phones
a) Target: Phones with jailbroken operating systems.
b) Vulnerability: Removal of official security measures.
c) Risk: Data theft, manipulation of the device, and attacks on connected networks.
Elevate your Ethical Hacking abilities by Mastering the Metasploit Framework Course and staying ahead of cyber threats today!
How Much Harm Can Hackers Cause?
Cyber Security breaches can lead to significant disruption and harm. Once hackers gain access to your data or devices, they can:
a) Steal your money and open credit card or bank accounts in your name
b) Damage your credit score by making unauthorised transactions
c) Request new PINs or credit cards, enabling further fraud
d) Make purchases on your behalf, draining your accounts
e) Add themselves as authorised users to your accounts for easier access to credit
f) Obtain cash advances, leaving you with the debt
g) Exploit your Social Security number for identity theft and fraud
h) Sell your personal information to others for malicious use
i) Delete or corrupt important files on your devices
j) Leak sensitive personal data or threaten to do so for extortion purposes
Learn to identify vulnerabilities and secure networks with the Certified Penetration Testing Professional Certification Course today!
Historic Cyberattacks and Hackers
Here are some of the most significant cyberattacks and infamous hackers who left a lasting mark on digital history:
1) The 414s
a) Timeframe: Early 1980s
b) Targets: Los Alamos National Laboratory, Sloan-Kettering Cancer Center
c) Impact: Motivated the US Congress to pass the Computer Fraud and Abuse Act, making malicious Hacking a crime.
2) The Morris Worm
a) Timeframe: 1988
b) Creator: Robert Tappan Morris
c) Impact: Forced thousands of computers offline, caused an estimated £7.6 million in damages.
d) Significance:
Morris was the first person punished under the Computer Fraud and Abuse Act.
3) Colonial Pipeline
a) Timeframe: 2021
b) Method: Ransomware attack
c) Impact: Temporarily shut down the pipeline, which supplies 45% of the US East Coast's petroleum.
d) Outcome: Colonial Pipeline paid a ransom of £3.34 million to regain access to its data.
4) Change Healthcare
a) Timeframe: 2024
b) Impact: Massive data breach disrupting billing systems across the US healthcare industry.
c) Data Compromised: Personal data, payment details, and insurance records for millions of people.
d) Estimated Costs: Potentially affected up to one-third of all Americans, with costs reaching £760 million.
Master advanced Hacking techniques and safeguard digital assets with our Certified Ethical Hacker Certification Course today!
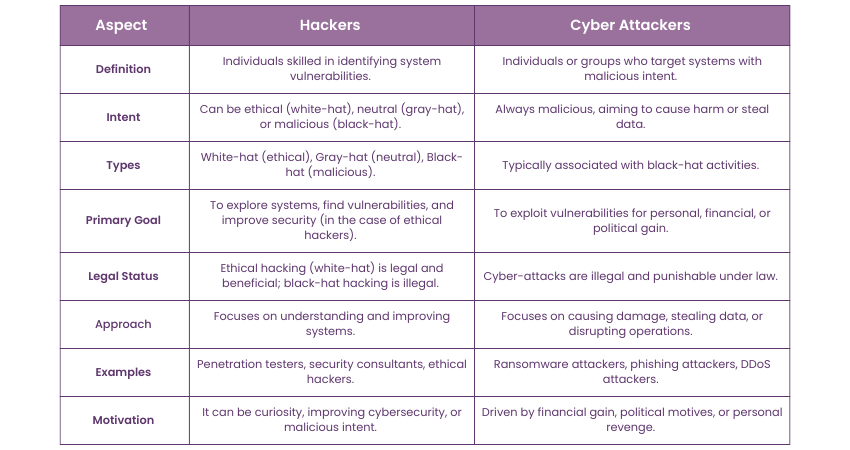
The Difference Between Hackers and Cyber Attackers
Hackers are professionals either on the right side of the law or, in some cases, on the wrong side of the law and capable of discovering system flaws. On the other hand, cyber attackers knowingly infect systems with malicious intent for the purpose of acquiring information, paralysing organisational processes or destroying something.
Risks Associated with Hacking for Banks and Financial Institutions
Hacking examinations are riskier to banks and financial institutions, including data demonstrations through which clients’ details, such as account details and identity information, may be processed. Computer fraud is also a severe risk since intruders can snoop through funds and transactions and completely drain accounts.
Furthermore, ransomware attacks can halt all types of banking operations through the locking of various important systems in the banking system in exchange for a ransom to be paid out. Another major risk of cybercrime is reputational loss; customers cease to trust the relevant institutions to safeguard their information.
How to Prevent Hacking?
Here are several steps to keep your devices and networks secure:
1) Update Your Software and Hardware
a) Regularly update software and hardware to install security patches.
b) Security updates fix vulnerabilities that hackers can exploit.
2) Keep Devices Secure
a) Make sure to create secure passwords and always lock your devices when they are not being used.
b) Stop unauthorised entry, regardless of whether your device is taken.
3) Use a VPN
a) VPNs encrypt your internet connection, making it harder for hackers to intercept data.
b) This is crucial while using public Wi-Fi networks, which are prone to Hacking.
4) Use a Password Manager
a) Password managers generate and store complex, unique passwords.
b) Decreases the risk of using weak or repetitive passwords that are easy to hack.
5) Avoid Public Wi-Fi for Sensitive Data
a) Don't access personal or financial data on unsecured public Wi-Fi.
b) Public networks are often targets for data interception.
6) Use a Good Quality Antivirus
a) Set up efficient antivirus software to defend against malware, viruses, and various other threats.
b) Make sure to consistently update your antivirus software to protect against emerging threats.
7) Avoid Logging in as Admin by Default
a) For day-to-day tasks, use a regular user account.
b) This limits the damage hackers can cause if they gain access.
8) Brush up on Anti-phishing Techniques
a) Phishing attacks confuse users into disclosing sensitive data.
b) Stay cautious of suspicious emails, links, or requests for personal data.
9) Avoid Questionable Websites
a) Avoid visiting websites known for hosting malware or harmful content.
b) Check for 'https://' in URLs to ensure a secure connection.
10) Turn Off Features You Don't Need
a) Disable features like remote access or Bluetooth when not in use.
b) Reduces entry points for potential hackers.
Master Ethical Hacking and safeguard businesses against cyber threats with our Ethical Hacking Training – join now!
What is the Biggest Hack in History?
Among them one of the largest data breaches known as Yahoo data breach that hit more than 3 billion users between 2013 and 2014. That leaked two of the most wanted mail accounts of Hollywood actresses and exposed the private information of around a half billion people including their names, email addresses as well as passwords.
The other significant event happened in 2017, Equifax Data breach; 147 million people’s data of sensitivity like the Social Security number affected. These hacks demonstrate the cost and loss organizations and people will incur due to cyber-attacks.
Which Country Has the Most Hackers?
It is indisputable that China is seen to be at the top of all the world countries for having many hackers because of its sponsored hacking teams and cyber-sparge. The Chinese hackers have been named in many global cyber assaults on governments, financial institutions, and corporations.
There are other countries that also have a lot of hacker problems, such as Russia, the U.S., and North Korea. Russia is notorious for ransomware attacks, and North Korea hacks for its regime financing. In the United States, there is a high population of white hat hackers who work on the defence side of security.
How do Hackers Hack Your Phone?
There is always this phishing attack where hackers manage to con phone users into downloading malicious links or apps. Some may appear genuine, but they lead you to download something that contains viruses, thus making it easy for hackers to get to your phone and get all details such as messages, photos and even financial details.
If you are wondering How to Know if your Phone is Hacked, watch out for unusual behaviour like unexpected battery drainage, strange pop-ups, or unauthorised transactions. Hackers also use spyware or take advantage of an open Wi-Fi network to take control of your device. When you are working on an open network, this is the most appropriate time for hackers to steal your data.Install security applications, update every other software you have on the computer, and do not open strange links.
Want to impress your interviewers? Master Ethical Hacker Interview Questions and Answers to stand out and show off your expertise!
Conclusion
Understanding What is Hacking empowers you to take control of your digital safety. By staying informed about different Hacking methods and adopting strong security practices, you can safeguard your personal and professional data. Take charge of your online safety and confidently defend against potential cyber threats.
Master Malware And Memory Forensics Training to enhance your Cyber Security skills and protect critical systems.
Frequently Asked Questions
Is Hacking Illegal?

Unauthorised access to computers or networks for malicious purposes, like theft of data or causing harm, can lead to illegal Hacking. However, Ethical Hacking, done with permission to improve security, is legal. The legality depends on the hacker’s intent and actions.
What Should I do if I Suspect a Hack?

If you suspect your account has been breached, promptly disconnect from the web, modify all your passwords, upgrade your security tools, and monitor for any strange behaviour. To receive additional assistance, contact a cybersecurity expert or your IT department.
What are the Other Resources and Offers Provided by The Knowledge Academy?

The Knowledge Academy takes global learning to new heights, offering over 3,000 online courses across 490+ locations in 190+ countries. This expansive reach ensures accessibility and convenience for learners worldwide.
Alongside our diverse Online Course Catalogue, encompassing 19 major categories, we go the extra mile by providing a plethora of free educational Online Resources like News updates, Blogs, videos, webinars, and interview questions. Tailoring learning experiences further, professionals can maximise value with customisable Course Bundles of TKA.
What is The Knowledge Pass, and How Does it Work?

The Knowledge Academy’s Knowledge Pass, a prepaid voucher, adds another layer of flexibility, allowing course bookings over a 12-month period. Join us on a journey where education knows no bounds.
What are the Related Courses and Blogs Provided by The Knowledge Academy?

The Knowledge Academy offers various Ethical Hacking Training, including Ethical Hacking Professional and Mastering Metasploit Framework. These courses cater to different skill levels, providing comprehensive insights into Ethical Hacking.
Our IT Security & Data Protection Blogs cover a range of topics related to Hacking, offering valuable resources, best practices, and industry insights. Whether you are a beginner or looking to advance your IT Security & Data Protection skills, The Knowledge Academy's diverse courses and informative blogs have got you covered.
Upcoming IT Security & Data Protection Resources Batches & Dates
Date
 Ethical Hacking Professional
Ethical Hacking Professional
Thu 1st May 2025
Thu 4th Sep 2025
Thu 20th Nov 2025






 Top Rated Course
Top Rated Course



 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


