We may not have the course you’re looking for. If you enquire or give us a call on 01344203999 and speak to our training experts, we may still be able to help with your training requirements.
We ensure quality, budget-alignment, and timely delivery by our expert instructors.
Ever wondered how safe you really are online? With the Internet integrated into nearly every aspect of our lives, ensuring one’s online security is now more crucial than ever. This is where Internet Security comes into play. What is Internet Security? It is the shield that protects your devices, personal data, and online activities from the constant threat of Cyber-attacks. From malware to phishing, these dangers are real and evolving. But no worries, Internet Security can protect you from these threats, ensuring your digital life remains safe and secure.
With proper Internet Security, you can better control your online safety. Without worry or fear, you can surf the Internet, work online, and shop on eCommerce sites! Sounds good? In this blog, we’ll explore the essentials of Internet Security and how you can safeguard your digital space from Cyber-attacks.
Table of Contents
1) What is Internet Security?
2) Common Internet Security Threats
3) Components of Internet Security
4) Tips for Improving Internet Security
5) Conclusion
What is Internet Security?
Internet Security refers to the strategic measures put in place to protect data, systems, and networks from various cyber threats. It encompasses strategies aimed at ensuring Confidentiality, Integrity, and Availability (CIA) of information in the digital realm.
These measures include implementing firewalls, antivirus software, encryption, and other tools. They help prevent unauthorised access, data breaches, and other malicious activities perpetrated by cybercriminals.
Common Internet Security Threats
In the world of Internet Security, several harmful threats pose risks to data, systems, and users. Acknowledging these threats is crucial for applying effective protection measures. Some common Internet Security threats include:
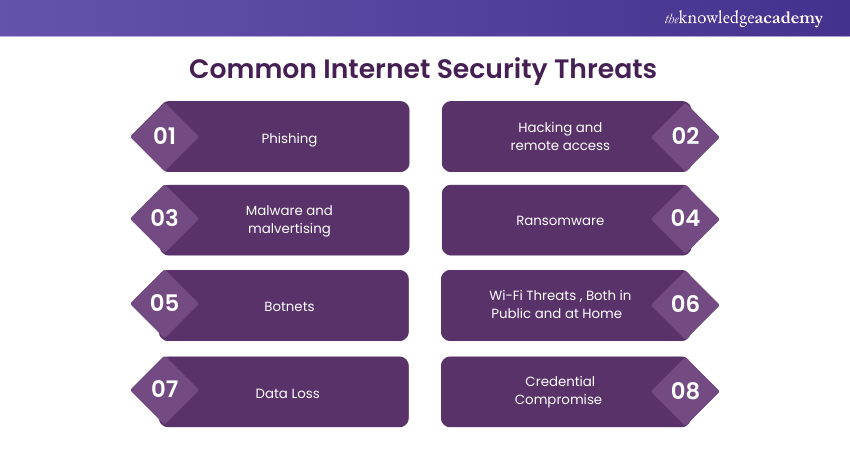
1) Phishing
Phishing is a cyber-attack technique where attackers pose as trustworthy entities to deceive individuals into providing sensitive information. This information could be anything from usernames and passwords to financial details. These attacks often come in the form of deceptive emails, messages, or websites that appear legitimate but are designed to steal personal information.
2) Hacking and Remote Access
Hacking is the art of gaining unauthorised access to a network or system. In this process, hackers find software vulnerabilities and penetrate them to steal sensitive information. The amazing thing is that hackers can remotely compromise systems and gain access to the target’s device.
3) Malware and Malvertising
Malicious software, or malware, encompasses a wide range of software designed to infiltrate, harm, or gain unauthorised access to computer systems. Malware can include viruses, worms, trojans, spyware, and ransomware. Malvertising, or malicious advertising, involves distributing malware through online advertisements displayed on legitimate websites, often exploiting vulnerabilities in ad networks or web browsers.
4) Ransomware
Ransomware is one of the most popular malware. In this, the attacker will encrypt the files out of a computer system and can access the data easily. He will then demand money in virtual currencies in exchange for the files. The impact of such cyberattacks can be severe not only for businesses but also for individuals. Financial damage, operational interruption, and data loss are some of the consequences.
5) Botnets
A botnet is a network of bots and compromised computers. They are typically under the control of a central Command and Control (C&C) server operated by cybercriminals. Botnets are often used to carry out coordinated attacks, such as Distributed Denial-of-Service (DDoS) attacks.
In such attacks, compromised devices flood a target server with traffic, causing it to become overwhelmed and unavailable. Botnets can also be used for Spamming in Cyber Security, phishing, credential stuffing, or Cryptocurrency Mining.
6) Wi-Fi Threats , Both in Public and at Home
Wi-Fi threats encompass risks associated with insecure wireless networks, both public and private. Attackers can intercept data transmitted over unsecured Wi-Fi networks. They do this by intercepting passwords, emails, or financial information, using techniques like packet sniffing or man-in-the-middle attacks.
Additionally, attackers may set up rogue Wi-Fi networks or use Wi-Fi spoofing to trick users into connecting to malicious access points. This enables them to steal data or distribute malware.
7) Data Loss
An organisation’s confidential data can be stolen in a number of ways. However, Malware is the most common attack perform to collect information. Apart from this, social engineering takes advantage of human errors to penetrate the victim’s system. To dodge this threat, store your personal data in personal accounts such as online storage or webmail.
8) Credential Compromise
Cybercriminals often collect user credentials to access corporate systems or online accounts. Credentials can be stolen through data breaches, phishing sites, or compromised via credential stuffing. Weak and reused passwords also put credentials at risk.
Become a Certified Cyber Security Expert with our Security Professional (CCS-PRO) Course - Register now!
Components of Internet Security
Internet Security encompasses various components and technologies to protect systems, data, and networks from Cyber Security Threats. Understanding these components, including Internet Security Suites, is essential for implementing comprehensive security measures. Some key components of Internet Security include:
1) URL Filtering
URL filtering involves using software or hardware to monitor and restrict access to specific websites based on predefined criteria. This helps prevent users from accessing malicious or inappropriate websites that may pose security risks.
2) Prevention of Malicious Downloads
This component focuses on identifying and blocking malicious files or software before they can be downloaded or executed on a system. It often involves the use of antivirus software, Intrusion Detection Systems (IDS), or advanced threat prevention solutions to detect and quarantine suspicious files.
3) Protection Against Botnets
Botnet protection measures aim to detect and mitigate the presence of botnets within a network. Besides botnet threats, organizations must also secure against pharming attacks that redirect users to fraudulent websites.
4) Implementation of Data Loss Prevention (DLP) Measures
Data Loss Prevention steps can effectively prevent the unauthorised exposure or leakage of sensitive data. This may include encrypting data at rest and in progress, monitoring data access and usage, and executing policies and controls to prevent data exfiltration. These elements work together to establish a layered security strategy that helps mitigate the risk of malicious attacks and safeguard data assets' integrity, confidentiality, and availability.
5) Browser Selection
All Web browsers come with their level of protection against online threats. Some are better at safeguarding your online activities. For example, secure browsers automatically clear cookies after you visit websites, which stops hackers from accessing your bank or tax accounts if your device is stolen. Additionally, secure browsers use SSL certificates to protect connections between users and the websites they dwell on.
Unlock your future and start your journey to success with our Virtual Online Job Roles Training – Sign up today!
Tips for Improving Internet Security
Enhancing Internet Security involves adopting proactive measures and best practices to defend against Cyber threats. Here are some valuable tips to bolster your online security posture:
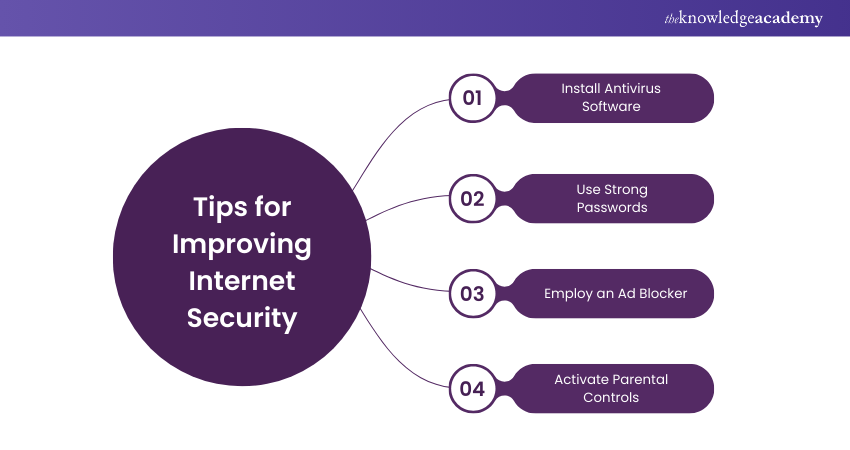
1) Install Antivirus Software on all Your Devices
Utilise reputable antivirus software across your computers, smartphones, and other devices to detect and neutralise malware threats effectively. Regularly update the antivirus software to make sure it can find and mitigate the latest threats.
2) Use Strong Passwords
Employ complex and unique passwords or passphrases for each online account, incorporating a combination of uppercase and lowercase letters, numbers, and special characters. Avoid using simple passwords, such as names, common words, or sequences, to enhance security.
3) Employ an Ad Blocker
Consider installing ad-blocking extensions or software to minimise exposure to potentially malicious advertisements and avoid accidental clicks on suspicious links. Ad blockers can greatly lower the risk of encountering a virus or phishing scams.
4) Activate Parental Controls
Enable parental control features on devices and Internet routers to regulate and monitor online activities, especially for children, and restrict access to inappropriate content. Parental controls can help protect children from accessing harmful or age-inappropriate material online. By implementing these tips and remaining vigilant online, you can significantly enhance your Internet Security and mitigate Cyber threats.
Protect Your Digital Footprint – Discover What is Google Dorking and ways to safeguard sensitive information!
What are the Benefits of Internet Security Solution?
Internet Security solutions provide vital protection against Cyber threats, assuring data security and peace of mind in our digital world. Let's explore other benefits of Internet Security here:
1) Protection Against Cyber Threats: Protects your devices and networks from malware, phishing, and other Internet-based attacks.
2) Data Security: This ensures the protection of your sensitive data by using encryption, data loss prevention, and multi-factor authentication.
3) Email Security: Email security stops Cyber criminals from taking advantage of personal email accounts, which are frequently targeted in attacks.
4) Remote Access Security: Ensures the safety of your digital resources when connecting to them from different places, essential in today's mobile environment.
5) Peace of Mind: It offers assurance that your digital data is protected by strong security measures.
6) Identity Protection: It prevents identity theft by securing personal and financial information over the Internet.
7) Continuous Monitoring: Continuous monitoring involves regular checking for vulnerabilities and threats to provide proactive protection.
8) Compliance With Regulations: Assists organisations in fulfilling legal and regulatory mandates concerning data security.
9) Prevention of Financial Loss: Minimises the chances of suffering financial losses due to Cyber-attacks or data breaches.
10) Improved Productivity: Reduces downtime and interruptions from Cyber threats, enabling more streamlined operations.
Conclusion
In our rapidly evolving digital world, prioritising Internet Security is essential. Safeguarding your personal and confidential information from Cyber threats requires alert and proactive measures. By staying informed about potential risks and applying strong security practices, you can defend against the wrong side of the digital landscape. Remember, your digital safety is in your hands, and with the right tools, you can shield what matters most to you.
Become an Online Security Expert with our Online Internet Security Specialist Training – Sign up today!
Frequently Asked Questions
What Educational Background is Typically Required for a Career in Internet Security?

A profession in Internet Security normally necessitates a Diploma in Computer Science, Cyber Security, or Information Technology. Obtaining certifications like CISSP is crucial for developing specialised knowledge in the industry. Acquiring hands-on experience from internships or laboratory work is also vital for honing essential skills.
How can Someone Break into the Field of Internet Security With No Prior Experience?

As a beginner with no prior experience, you can get certificated in CompTIA Certification. Later, you can acquire hands-on skills through internships, labs, and working on self-study projects to gain practical experience. Also, connect with professionals in the industry to create job possibilities.
What are the Other Resources and Offers Provided by The Knowledge Academy?

The Knowledge Academy takes global learning to new heights, offering over 3,000 online courses across 490+ locations in 190+ countries. This expansive reach ensures accessibility and convenience for learners worldwide.
Alongside our diverse Online Course Catalogue, encompassing 19 major categories, we go the extra mile by providing a plethora of free educational Online Resources like News updates, Blogs, videos, webinars, and interview questions. Tailoring learning experiences further, professionals can maximise value with customisable Course Bundles of TKA.
What is The Knowledge Pass, and How Does it Work?

The Knowledge Academy’s Knowledge Pass, a prepaid voucher, adds another layer of flexibility, allowing course bookings over a 12-month period. Join us on a journey where education knows no bounds.
What are the Related Courses and Blogs Provided by The Knowledge Academy?

The Knowledge Academy offers various Virtual Online Job Roles Training, including the Virtual Assistant Course, Online Virtual Recruitment Training, and Online Teacher Training. These courses cater to different skill levels, providing comprehensive insights into What is Cyber Security.
Our Business Skills Blogs cover a range of topics related to Internet Security, offering valuable resources, best practices, and industry insights. Whether you are a beginner or looking to advance your Business Skills, The Knowledge Academy's diverse courses and informative blogs have got you covered.
Upcoming Business Skills Resources Batches & Dates
Date
 Online Internet Security Specialist Training
Online Internet Security Specialist Training
Fri 11th Apr 2025
Fri 13th Jun 2025
Fri 15th Aug 2025
Fri 10th Oct 2025
Fri 12th Dec 2025






 Top Rated Course
Top Rated Course



 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


