We may not have the course you’re looking for. If you enquire or give us a call on 01344203999 and speak to our training experts, we may still be able to help with your training requirements.
We ensure quality, budget-alignment, and timely delivery by our expert instructors.
Ever wondered about the secret behind the shaping of modern advancements in technology today? Your curiosity surrounding such mysteries could help you unravel the concept of What is Reverse Engineering, a strategic process which is not merely about disassembling and understanding but about exploration into the core of innovation.
From decoding software intricacies to enhancing hardware components, Reverse Engineering is a key catalyst for progress. Dissecting the very essence of this enigmatic practice that shapes modern advancements will help you unlock the secrets that propel the world into a future defined by ingenuity and technological excellence.
You will learn about how Reverse Engineering is the procedure of deconstructing and analysing a product or system to understand its design, functionality, and components.
Table of Contents
1) What is Reverse Engineering?
2) Process of Reverse Engineering
3) Purpose of Reverse Engineering
4) Reverse Engineering examples
5) Conclusion
What is Reverse Engineering?
Reverse Engineering is a meticulous and strategic process that involves dissecting and understanding a product, system, or technology by working backward from its final form to uncover its underlying design, functionality, and components.
It is akin to deciphering a complex puzzle, where skilled individuals meticulously deconstruct a target to reveal its intricate details. In the domain of technology, Reverse Engineering is employed across various domains, including hardware, software, and electronics.
In hardware Reverse Engineering, analysts dismantle electronic devices to comprehend the inner workings of circuits and components. Meanwhile, software Reverse Engineering involves dissecting software code to unveil its logic, algorithms, and functionalities.
This method is crucial for debugging, optimising, and securing applications. Reverse Engineering extends its reach to product design and manufacturing, enabling the replication and improvement of mechanical components. Ethical hacking and cybersecurity also heavily rely on Reverse Engineering to identify vulnerabilities, understand malware, and fortify digital defences.
Process of Reverse Engineering
Reverse Engineering is the meticulous process of dissecting and understanding a product's design and functionality by working backward from its final form. From hardware and software to mechanical components, this strategic approach enables a comprehensive understanding, fostering innovation, problem-solving, and advancements across various technological domains.
Here are the various steps involved in the process of Reverse Engineering:
1) Extracting Information
In Reverse Engineering, information extraction is the art of extracting hidden details from a target system. Skilled analysts meticulously dismantle and study the components, unravelling the complexities to reveal the underlying data, algorithms, and functionalities.
This process involves decoding software logic, understanding hardware circuitry, and uncovering design principles. Information extraction is paramount for comprehending the intricacies of a system, facilitating improvements, and bolstering cybersecurity.
Moreover, the acquired insights not only foster innovation but also contribute to refining existing technologies and fortifying digital architectures against potential vulnerabilities.
2) Create a Model
In Reverse Engineering, model creation is the phase where extracted information is synthesised to reconstruct a comprehensive representation of the original system. This process involves piecing together hardware components, deciphering software code, and reconstructing mechanical designs.
Skilled practitioners employ various tools and techniques to build an accurate model that mirrors the intricacies of the original, enabling a profound understanding of functionality and structure.
The created model serves as a blueprint for innovation, allowing for improvements, optimisations, and informed decision-making across diverse technological domains, from software development to product design and beyond.
3) Commence Disassembly
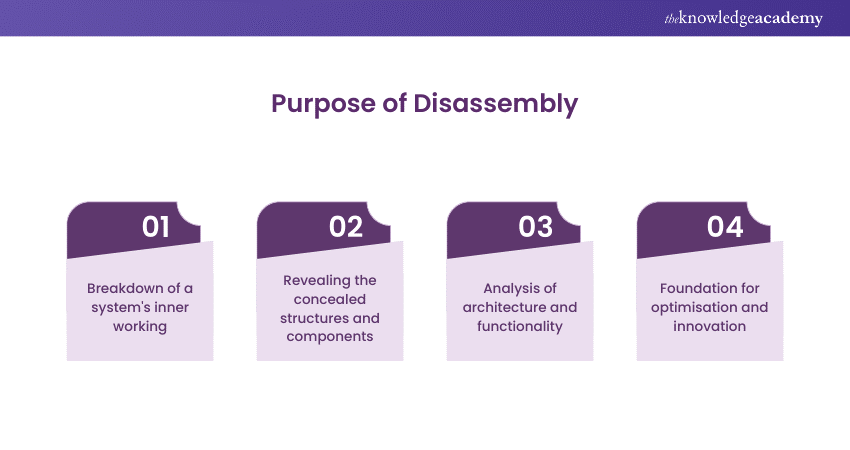
The initiation of disassembly in Reverse Engineering marks the crucial moment when analysts embark on unravelling the inner workings of a system. With precision and methodical expertise, practitioners carefully dismantle the target, beginning the meticulous process of uncovering its concealed components and structures.
This stage needs a keen eye for detail, as each disassembled part unlocks a piece of the puzzle, revealing the architecture, connections, and functionality of the original system. Disassembly sets the stage for subsequent analysis, enabling a comprehensive understanding that forms the foundation for innovation, optimisation, and problem-solving in fields ranging from technology to manufacturing.
4) Assess the Product
The product assessment stage in Reverse Engineering is a critical phase where practitioners thoroughly analyse the disassembled components. This meticulous examination involves scrutinising the functionality, materials, and design principles to extract valuable insights. Skilled analysts assess how each part interacts within the system, unravelling the intricacies of the original product.
This comprehensive evaluation guides the creation of accurate models, shedding light on the inner workings for further optimisation and innovation. The product assessment stage is pivotal in understanding the product's strengths and weaknesses, informing decisions that can translate into improvements in design, performance, and overall efficiency across various industries.
5) Reconstruct
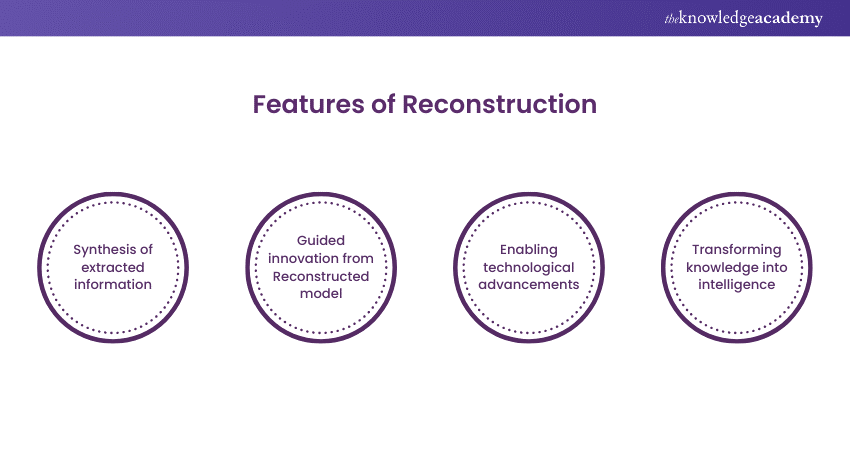
The reconstruction stage in Reverse Engineering is where disassembled components and extracted information are skilfully synthesised into a comprehensive model. This phase involves reassembling the product or system, aiming to replicate its original functionality and design.
This reconstructed model serves as a valuable blueprint, guiding innovation, optimisation, and problem-solving efforts. The stage of reconstruction is instrumental in turning extracted knowledge into actionable intelligence, facilitating advancements in technology, manufacturing, and various fields where Reverse Engineering is applied.
Purpose of Reverse Engineering
Reverse Engineering serves as a strategic process to unravel the intricacies of products, systems, or technologies. It aims to understand their design, functionality, and components by working backward from the final form.
This practice fosters innovation, problem-solving, and improvements across diverse domains such as technology, software development, and manufacturing.
Here are the various applications of Reverse Engineering:
1) Replacement of Legacy Parts
The replacement of legacy parts is a crucial facet of engineering and maintenance, driven by the need to upgrade outdated components with modern, efficient alternatives. This process involves a meticulous examination of existing systems, identifying obsolete or worn-out parts that hinder performance or compromise safety.
Skilled engineers employ Reverse Engineering techniques to comprehend the specifications of legacy components and subsequently design suitable replacements. The aim is not only to restore functionality but also to enhance overall system efficiency and longevity.
This strategic approach ensures that ageing systems can adapt to contemporary standards, technologies, and regulations, prolonging their operational life and aligning them with evolving industry demands. The replacement of legacy parts stands as a proactive measure, promoting sustainability and mitigating risks associated with obsolete technologies.
2) Parts Servicing or Repair
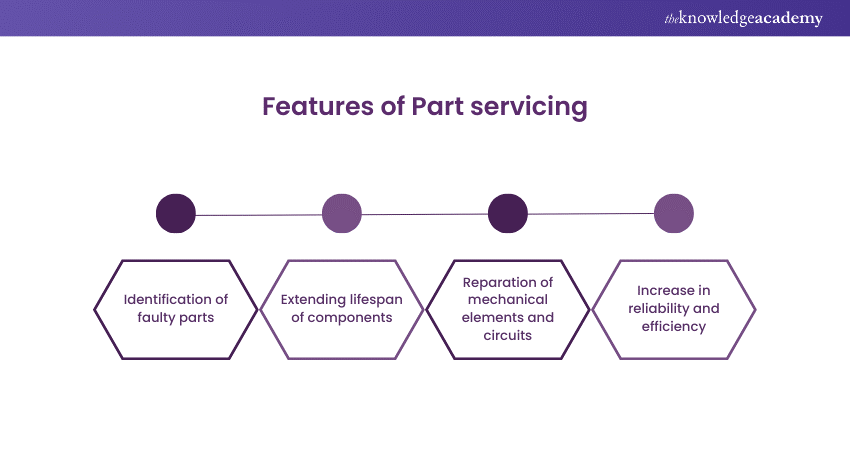
Servicing or repairing parts is an essential aspect of maintenance that aims to extend the lifespan and functionality of components within various systems. This meticulous process involves diagnosing issues through thorough inspections, identifying faulty or damaged parts, and implementing corrective measures.
Skilled technicians employ a combination of manual expertise and technological tools to disassemble, troubleshoot, and repair components, ensuring they meet optimal performance standards.
Whether it's fixing mechanical elements, electrical circuits, or software glitches, servicing or repairing parts plays a vital role in preventing system failures, reducing downtime, and promoting cost-effective solutions.
This proactive approach not only addresses immediate concerns but also contributes to the overall reliability and efficiency of machinery, systems, and technologies across diverse industries.
3) Analysis of Failures
The analysis of failures in Reverse Engineering is a meticulous process crucial for understanding the root causes behind malfunctions or shortcomings in a system. This investigative phase involves scrutinising disassembled components and extracting information to pinpoint areas of weakness or inefficiency.
Skilled analysts explore the intricacies of the original design, code, or structure, identifying errors, vulnerabilities, or outdated features that contribute to failures. By applying a critical lens to each element, from hardware components to software algorithms, practitioners gain valuable insights that inform subsequent improvements.
The analysis of failures in Reverse Engineering is a proactive strategy, allowing for the identification and rectification of issues before they escalate, ultimately contributing to enhanced reliability, performance, and longevity of the analysed systems across diverse technological domains.
4) Enhancement of Parts
The enhancement of parts in Reverse Engineering is a transformative process focused on improving the performance, efficiency, and overall functionality of existing components. Following the meticulous disassembly and analysis stages, skilled engineers employ innovative approaches to redesign and optimise the components.
This may involve incorporating advanced materials, leveraging modern manufacturing techniques, or refining software algorithms. The goal is to address identified weaknesses, enhance durability, and often introduce new features to meet evolving requirements.
The strategic application of Reverse Engineering in part enhancement ensures that legacy systems can benefit from contemporary advancements, extending their relevance and operational life.
By fostering innovation and adaptability, this process contributes to the continued efficiency and competitiveness of technologies across diverse industries, from manufacturing and automotive to electronics and beyond.
5) Diagnostics and Troubleshooting
Diagnostics and troubleshooting in Reverse Engineering represent a pivotal stage where meticulous examination and analysis are deployed to identify and rectify issues within a system. This phase involves a comprehensive assessment of disassembled components, software code, or mechanical structures to pinpoint anomalies, malfunctions, or inefficiencies.
Skilled practitioners use a combination of manual inspection and advanced tools to diagnose problems and understand the underlying causes of failures. Once issues are identified, troubleshooting strategies are employed to propose effective solutions, whether it involves repairing existing components or redesigning elements for improved performance.
This diagnostic and troubleshooting stage is not only reactive, addressing current concerns, but also proactive, preventing future issues and contributing to the overall reliability, efficiency, and longevity of the analysed systems across diverse technological domains.
Reverse Engineering Examples
Below are some examples of Reverse Engineering, described in further detail:
1) Software
Software analysis is paramount for understanding and optimising applications. Take, for example, a cybersecurity firm employing Reverse Engineering techniques to dissect malware. By disassembling the malicious code, analysts uncover its functionality, vulnerabilities, and potential attack vectors.
A notable example is Symantec, a cybersecurity company renowned for its threat intelligence and antivirus solutions. Symantec employs Reverse Engineering to analyse and counteract complex malware, providing crucial insights into evolving cyber threats.
In software development, Reverse Engineering is also instrumental in understanding proprietary code formats or file structures, facilitating interoperability. For instance, WineHQ, an open-source compatibility layer, utilises Reverse Engineering to run Windows applications on Unix-like operating systems.
This underscores how Reverse Engineering in the software domain not only enhances cybersecurity but also fosters cross-platform compatibility, driving innovation and adaptability in technology.
2) Computer Components
Reverse Engineering plays a pivotal role in understanding and improving computer components, ensuring compatibility and performance optimisation. Consider NVIDIA, a leading company in graphics processing units (GPUs).
Additionally, in the competitive field of graphics technology, Reverse Engineering allows NVIDIA to dissect competitors' hardware, gaining insights into design choices and performance optimisations. This process empowers them to refine their own products, enhancing efficiency and staying at the forefront of innovation.
Moreover, in the field of legacy systems, Reverse Engineering assists companies like iFixit. iFixit employs Reverse Engineering to analyse and create repair guides for obsolete computer components. This approach not only prolongs the lifespan of ageing hardware but also empowers users to troubleshoot and upgrade their devices, contributing to sustainability.
3) Assessments of Network Security
In the domain of network security, Reverse Engineering serves as a formidable tool for assessing vulnerabilities and fortifying digital defences. Consider the cybersecurity firm FireEye, known for its expertise in advanced threat intelligence.
FireEye employs Reverse Engineering to analyse sophisticated cyber threats, unravel their attack methodologies and identify potential weaknesses in network infrastructures. By dissecting malware and understanding its behaviour, FireEye enhances its threat detection capabilities, providing invaluable insights to safeguard organisations against evolving cyber threats.
Furthermore, companies like Rapid7 utilise Reverse Engineering techniques for penetration testing and vulnerability assessments. Through the meticulous dissection of network protocols and security mechanisms, Rapid7 uncovers potential weaknesses in clients' networks, offering proactive solutions to fortify their digital perimeters. Reverse Engineering not only bolsters network security but also ensures a proactive and adaptive approach to countering emerging threats.
Conclusion
We hope you now have a good idea of What is Reverse Engineering, a concept that is often a mystery to many, that unveils the intricate details of technologies, fostering innovation and problem-solving. It's basically the strategic process that not only dissects and understands but also transforms, enhancing efficiency, security, and adaptability across diverse industries, shaping the future of technological evolution.
Acquire the knowledge of Reversing techniques by signing up for our Reverse Engineering Training now!
Frequently Asked Questions

Reverse Engineering is used to (1) analyse a product for improvements, (2) study competitor designs, (3) recover lost designs or documentation, and (4) identify security vulnerabilities or ensure compatibility with other systems.

Reverse Engineering's ethics depend on intent and context. It's ethical for innovation, learning, or security but unethical if it violates copyrights, patents, or aims to replicate proprietary technology without permission.

The Knowledge Academy takes global learning to new heights, offering over 30,000 online courses across 490+ locations in 220 countries. This expansive reach ensures accessibility and convenience for learners worldwide.
Alongside our diverse Online Course Catalogue, encompassing 19 major categories, we go the extra mile by providing a plethora of free educational Online Resources like News updates, Blogs, videos, webinars, and interview questions. Tailoring learning experiences further, professionals can maximise value with customisable Course Bundles of TKA.

The Knowledge Academy’s Knowledge Pass, a prepaid voucher, adds another layer of flexibility, allowing course bookings over a 12-month period. Join us on a journey where education knows no bounds.

The Knowledge Academy offers various Advanced Technologies Courses, including Introduction to Virtualisation Technologies Course, Reverse Engineering Training, and Nano Technology Training. These courses cater to different skill levels, providing comprehensive insights into What Does a Nanotechnology Engineer Do.
Our Advanced Technology Blogs cover a range of topics related to Reverse Engineering, offering valuable resources, best practices, and industry insights. Whether you are a beginner or looking to advance your Engineering knowledge, The Knowledge Academy's diverse courses and informative blogs have got you covered.
Upcoming Advanced Technology Resources Batches & Dates
Date
 Reverse Engineering Training
Reverse Engineering Training
Fri 28th Feb 2025
Fri 4th Apr 2025
Fri 27th Jun 2025
Fri 29th Aug 2025
Fri 24th Oct 2025
Fri 5th Dec 2025







 Top Rated Course
Top Rated Course



 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


