We may not have the course you’re looking for. If you enquire or give us a call on +55 8000201623 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.
DNS Fast Flux has become synonymous with stealth and sophistication in cyber threats. As technology advances, so do the tactics of malicious actors seeking to exploit vulnerabilities and evade detection.
Furthermore, DNS Fast Flux represents a cunning evasion technique, where cybercriminals use rapid IP address rotation to create a constantly shifting network, making it a formidable challenge for Cybersecurity experts. Fast Flux is a technique in DNS used by cyber criminals to delay or evade detection. Check out this blog to know more about DNS Fast Flux in detail.
Table of Contents
1) Understanding what is DNS Fast Flux
2) Pros and cons of DNS Fast Flux
3) Exploring various detection and mitigation strategies
4) Scenarios of DNS Fast Flux in the real world
5) Conclusion
Understanding what is DNS Fast Flux
DNS Fast Flux is a sophisticated and evasive cyber technique that revolves around the Domain Name System or DNS, a fundamental component of the internet. It is a method used by cybercriminals to rapidly change the IP addresses associated with a single domain name, creating a constantly shifting network of intermediary servers or compromised hosts.
Additionally, this dynamic approach is employed to obscure malicious activities and maintain the availability of harmful online resources, making it challenging for security systems to detect and counteract them effectively.
The concept of Fast Flux can be likened to a shell game, where the cybercriminal continuously switches the IP addresses, making it difficult for authorities and security professionals to pinpoint the actual source of malicious activities such as hosting phishing websites, distributing malware, or launching Distributed Denial-of-Service or DDoS attacks.
Furthermore, these rapidly changing IP addresses are typically linked to compromised computers, which serve as unwitting intermediaries, or "Flux Agents," further obfuscating the true origin of the cyber threat.
DNS Fast Flux poses a significant challenge to cybersecurity experts due to its deceptive nature and ability to keep malicious infrastructure operational for extended periods. Detecting and mitigating these threats require advanced tools, real-time monitoring, and a deep understanding of DNS behaviour patterns to distinguish between legitimate and malicious uses of Fast Flux.
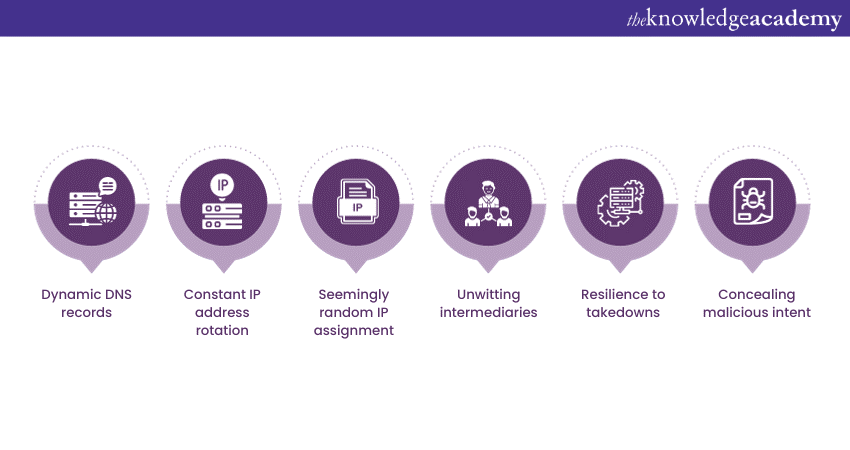
DNS Fast Flux is a complex and evasive cyber technique employed by malicious actors to obfuscate their activities and maintain the operational longevity of malicious websites or servers. To understand how it works, it's essential to break down its functioning into several key points:
Dynamic DNS records
DNS Fast Flux takes advantage of the dynamic nature of DNS records. Instead of a domain name pointing to a single, static IP address, Fast Flux domains have DNS records that point to multiple IP addresses.
Constant IP address rotation
The primary characteristic of DNS Fast Flux is the rapid rotation of these IP addresses. Cybercriminals maintain a pool of compromised or bot-infected computers, often referred to as "Flux Agents," each having its own IP address. These agents are continuously cycled in and out of the DNS records.
Seemingly random IP assignment
When a user attempts to access a Fast Flux domain, the DNS server returns IP addresses from this pool in a seemingly random order. This creates an ever-shifting network, making it extremely challenging to trace back to the source of malicious activities.
Unwitting intermediaries
The computers whose IP addresses are included in the Fast Flux network are typically compromised without their owners' knowledge. These compromised hosts act as intermediaries, relaying traffic to the ultimate malicious destination. Their involvement further obscures the true source of malicious content.
Resilience to takedowns
DNS Fast Flux is exceptionally resilient to takedown efforts. Even if security experts identify and block one of the IP addresses associated with a Fast Flux domain, another IP address quickly takes its place. This agility makes it challenging to disrupt the malicious infrastructure.
Concealing malicious intent
DNS Fast Flux blurs the line between legitimate and malicious domains. While it's widely used for malicious purposes such as hosting phishing websites, distributing malware, or launching DDoS attacks, it also has legitimate uses, such as ensuring high availability for Content Delivery Networks (CDNs). This dual nature makes it challenging to identify and mitigate Fast Flux attacks without inadvertently affecting legitimate services.
Pros and cons of DNS Fast Flux
Here are the various pros and cons of DNS Fast Flux, highlighted below:
|
Aspect |
Pros |
Cons |
|
Evasion of detection |
Effectively hides malicious infrastructure by constantly changing IP addresses. |
Makes it challenging for security systems to detect and block malicious activities.
|
|
Resilience to takedowns |
Rapid IP address rotation ensures that even if one IP is blocked, another takes its place quickly. |
Increases the difficulty of shutting down malicious operations entirely. |
|
Obscures source |
Involves a network of unwitting intermediaries (compromised hosts), making it hard to trace malicious activities back to their source.
|
Hampers efforts to identify and apprehend cybercriminals. |
|
Legitimate uses impacted |
Can inadvertently affect legitimate services using Fast Flux-like techniques for high availability. |
Security measures targeting Fast Flux may disrupt essential online services. |
|
Increased attack surface |
Creates more opportunities for cybercriminals to exploit compromised hosts. |
Puts innocent users at risk by involving their computers in illicit activities. |
|
Overheads for security professionals |
Requires specialised tools and constant monitoring to detect and mitigate Fast Flux attacks. |
Imposes a heavy burden on Cybersecurity teams to stay ahead of evolving tactics. |
|
Ethical concerns |
Raises ethical dilemmas for organisations and individuals unknowingly involved in Fast Flux attacks. |
Compromised hosts may suffer reputational damage, and their owners may face legal consequences. |
Learn to detect and debug Malware, by signing up for our Malware Analysis Training now!
Exploring various detection and mitigation strategies
Detecting and mitigating DNS Fast Flux attacks is a sophisticated and complex task due to the constantly changing nature of this evasion technique. Cybersecurity experts employ a combination of strategies and tools to effectively identify and counter Fast Flux threats. Here are several key detection and mitigation strategies:
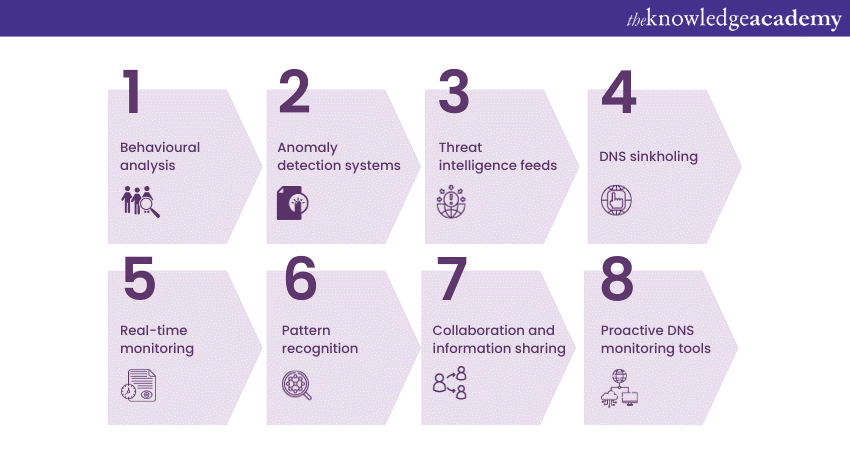
Behavioural analysis
Behavioural analysis involves monitoring DNS traffic for abnormal patterns. Security teams look for domains with rapidly changing IP addresses or those associated with a high number of Flux Agents (compromised hosts). Unusual DNS query patterns or excessive requests may trigger alerts.
Anomaly detection systems
Employing specialised anomaly detection systems can help identify Fast Flux activity. These systems use Machine Learning algorithms to establish baselines for normal DNS behaviour and flag any deviations from these patterns as potential threats.
Threat intelligence feeds
Subscribing to threat intelligence feeds provides real-time information about known Fast Flux domains and malicious IP addresses. This proactive approach allows security teams to block access to malicious resources before they cause harm.
DNS sinkholing
DNS sinkholing involves redirecting DNS requests for known malicious domains to a controlled server, effectively blocking access to the malicious resources. This technique is particularly effective when used against known Fast Flux domains.
Real-time monitoring
Continuously monitoring DNS traffic in real-time allows security professionals to spot suspicious activities as they happen. Real-time alerts and analysis enable swift responses to potential Fast Flux attacks.
Pattern recognition
The identification of patterns within DNS queries helps security experts can uncover Fast Flux behaviour. For example, recognising patterns where a single domain switches between numerous IP addresses rapidly can be indicative of a Fast Flux attack.
Collaboration and information sharing
Cybersecurity organisations, law enforcement agencies, and internet service providers collaborate to share information about Fast Flux threats. This cooperative approach allows for a more comprehensive understanding of evolving attack tactics.
Proactive DNS monitoring tools
Employing DNS monitoring tools that specialise in identifying Fast Flux techniques can provide an advantage. These tools often come with features designed to detect and mitigate Fast Flux behaviour automatically.
Rate limiting and query filtering
Implementing rate limiting and query filtering on DNS servers can help reduce the impact of Fast Flux attacks. By limiting the number of DNS queries from a single source, malicious activities can be slowed down or prevented.
Network traffic analysis
Analysing network traffic patterns, especially those associated with known Fast Flux domains, can provide insights into ongoing attacks. Suspicious or unexpected traffic patterns may indicate Fast Flux activity.
Blocking known malicious IPs
Maintaining a list of known and malicious IP addresses associated with Fast Flux domains and blocking access to these addresses can provide immediate protection against known threats.
Prevent system intrusions, by signing up for Introduction to System and Network Security Coursey now!
Scenarios of DNS Fast Flux in the real world
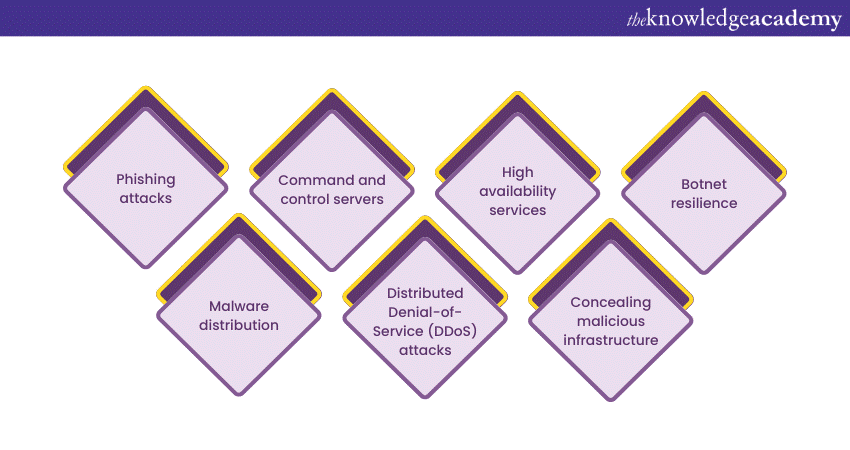
DNS Fast Flux has been deployed in various real-world scenarios, often with malicious intent:
a) Phishing attacks: Cybercriminals employ Fast Flux to host convincing phishing websites that imitate trusted organisations, aiming to steal confidential details such as login credentials, credit card details, or personal data.
b) Malware distribution: Fast Flux is used as a robust infrastructure for distributing malware. Malicious payloads are delivered via constantly changing IP addresses, making it challenging for security systems to block them.
c) Command and control servers: Malware operators utilise Fast Flux to hide the command and control servers of botnets. This enables them to maintain control over compromised machines while evading takedown attempts.
d) Distributed Denial-of-Service (DDoS) attacks: Fast Flux networks can be harnessed for launching DDoS attacks, leveraging the sheer number of Flux Agents to overwhelm target websites or services.
e) High availability services: Legitimate services like Content Delivery Networks (CDNs) employ Fast Flux-like techniques to ensure high availability, swiftly redirecting traffic to backup servers in case of server failures.
f) Concealing malicious infrastructure: Fast Flux is used to obscure the origin of various cyberattacks, making it complicated for investigators to trace back to the source of the malicious activities.
g) Botnet resilience: Botnets, like Storm Worm, have employed Fast Flux to maintain their resiliency even in the face of efforts to dismantle them, prolonging their nefarious operations.
Conclusion
DNS Fast Flux is a dynamic and elusive cyber technique that poses significant challenges to online security. Its ever-changing nature necessitates constant vigilance and the adoption of advanced detection and mitigation strategies to safeguard against its malicious applications in Cybersecurity.
Protect your organisation against cyber-attacks, by signing up for our Cyber Security Training now!
Frequently Asked Questions
Upcoming IT Infrastructure & Networking Resources Batches & Dates
Date
 BIND DNS Administration Training
BIND DNS Administration Training
Fri 10th Jan 2025
Fri 14th Feb 2025
Fri 11th Apr 2025
Fri 23rd May 2025
Fri 8th Aug 2025
Fri 26th Sep 2025
Fri 21st Nov 2025







 Top Rated Course
Top Rated Course


 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


