Ottawa is the capital city of Canada. It is located on the bank of the Ottawa River in the east of Southern Ontario province. It has an estimated population of 885,000 people. Ottawa is the fourth largest city in the world. The name of this city comes from the Algonquin word Odawa which means “to trade”. Education in Canada is mostly free and publicly funded. It is overseen by the federal, provincial and local governments, with the education within provincial jurisdiction and the curriculum overseen by the province. Education is compulsory in most provinces up to the age of 16. Parents can choose between sending their children to one of the public schools or they can sent them to a fee paying private school. Those who live in Ottawa and find that picking a secondary school is a fraught decision involving school zones and ratings. There are four main public school boards in Ottawa. One is English, one is English-Catholic, and one is French and another is French-Catholic. The Ottawa-Carleton District School Board which is the largest with 147 schools to oversee. The catholic school board has 85 schools, the Conseil des écoles catholiques du Centre-Est has 49 schools and the Conseil des écoles publiques de l'Est de l'Ontario has 37 schools. Canada’s higher has a very good reputation. However there is no formal ranking system and students will often choose colleges and universities bases on geographic convenience and the reputation of a particular course. Ottawa is one of the best educates cities in Canada as it is believed that over half of the population have graduated from college or university. Ottawa has the highest per capita concentration of engineers, scientists, and residents with PhDs in Canada. The University of Ottawa was founded in 1848 and was the first higher education institute to be established in the city. The university is a bilingual public university. The University of Ottawa is ranked in the top 300 universities in the world, coming in at number 284 and is a top 15 university in Canada. The university has faculties in the following areas: arts, civil law, common law, education, engineering, post graduate studies, health sciences, medicine, science, social sciences and the school of management. Ottawa also has two main public colleges Algonquin College and La Cité collégiale. There are also 2 catholic universities in the city; Dominican University College and Saint Paul University.
Free Wi-Fi
To make sure you’re always connected we offer completely free and easy to access wi-fi.








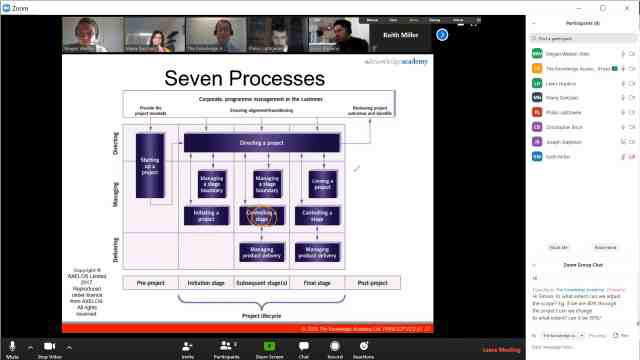
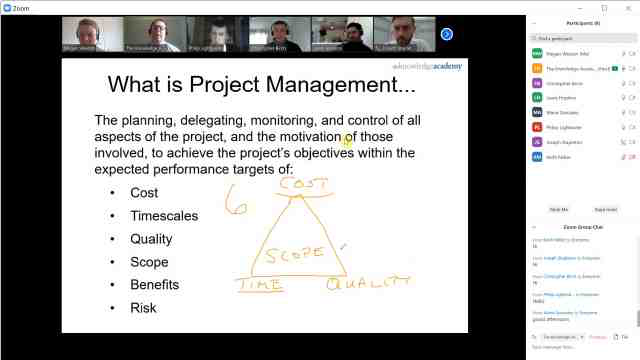























 Back to course information
Back to course information




 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please

