We may not have the course you’re looking for. If you enquire or give us a call on +41 315281584 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.

Cyber Security Policy is a set of guidelines issued by organisations to establish a formal policy to ensure that any sensitive information from the organisation is not leaked. Implementing this set of Cyber Security guidelines or Policies is crucial to eliminate the chances of any possible cyber threats.
According to Statista’s research, the Cam4 data breach in March 2020 was the largest reported data breach or leakage as of August 2022. This data breach of Cam4 caused more than 10 billion data records to be exposed. The second largest data breach in history was the Yahoo breach in 2013.
This report highlights how cyber-attacks can expose massive chunks of sensitive information and hamper the organisation's reputation and profitability. Given the rise in cyber-attacks, we must understand the importance of Cyber Security Policies.
Hence, we will discuss the important aspects relevant to the Cyber Security Policy in this blog.
Table of Contents
1) What is a Cyber Security Policy?
2) Why is Cyber Security Policy important?
3) Discussing important Cyber Security Policies
4) Conclusion
What is a Cyber Security Policy?
A Cyber Security Policy is a set of rules documented by the leaders of the organisations to issue guidelines for their staff to follow. The policies can be either technical or non-technical.
The Cyber Security Policy help address IT and Security related issues. Documenting the policies can set a barrier between acceptable and unacceptable behaviour.
Creating Cyber Security Policies should give you a clear picture about:
a) Who is it aimed at?
b) Who is responsible for what?
c) Whom to and how to report the concerns?
d) How to enforce the policies?
The purpose of creating Cyber Security Policies is to make things accountable and ensure that the security process is progressing according to the standards.
The below image depicts the list of common Cyber Security threats faced in an IT Infrastructure.

Do you want to improve your aptitude and skills to mitigate cyber-related risks? Then, register with the CCNA Cybersecurity Operation Training now!
Why is Cyber Security Policy important?
Cyber Security Policies are a set of formal rules issued by an organisation. It ensures that the authorised users follow the guidelines related to information security. A weak Cyber Security Policy can ruin your organisation and create a huge negative impact which can be hard to cover up.
In 2013, the National Cyber Security Policy was set up to monitor, safeguard, and strengthen the defences against cyber-attacks. Each country has established their own set of Cyber Security Policies to tackle cyber threats.
This image collaborates the key points to understand the need for Cyber Security Policies in an organisation.
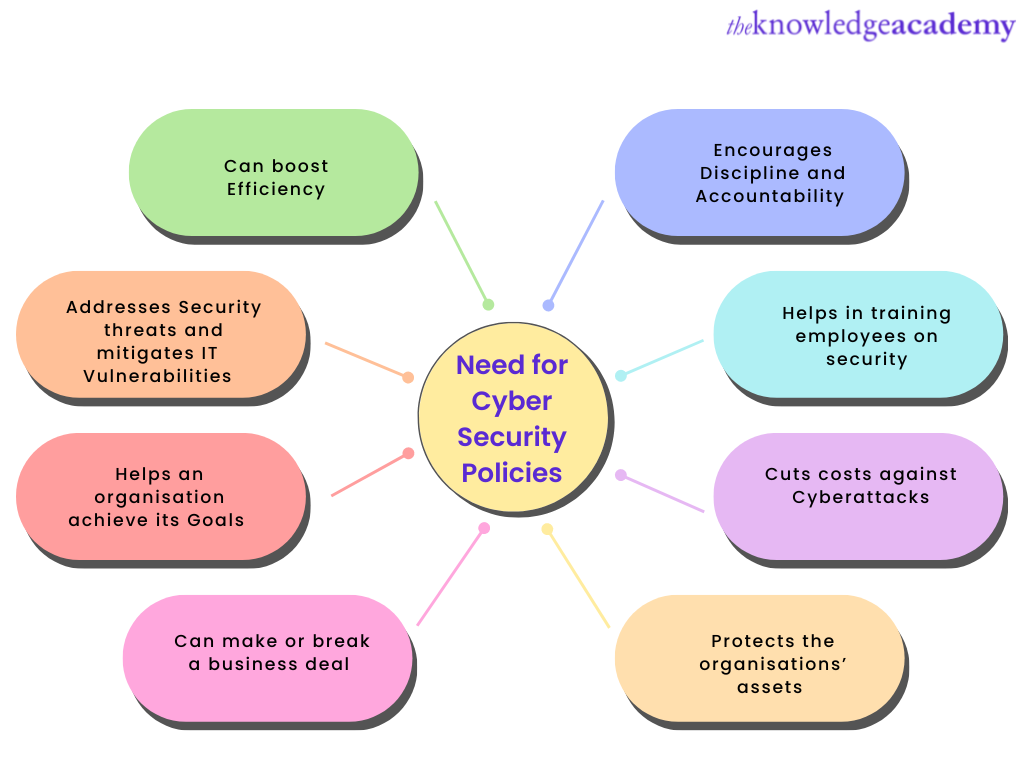
Further, let us discuss in detail why we need to implement Cyber Security Policies in an organisation.
1) It can boost efficiency
The best part of implementing a Cyber Security Policy is it can save time, money, and resources to increase efficiency. The policies can help organisations set specific standards for employee behaviour and activities. It can make the employees aware of what can be accepted and what cannot be accepted concerning the organisation's sensitive information.
2) It encourages discipline and accountability
In some unusual cases where a security system of the organisation gets compromised, the organisation’s security policy will initiate a necessary disciplinary action to support the case if it appears in court as a legal dispute. The security policies documented by the organisations act as a legal contract to validate that the organisation has taken all the necessary steps to safeguard its intellectual property, including the clients and customers.
3) It helps in training employees on security
A well-written security policy can also be viewed as a teaching tool that informs the readers regarding the significance of their role in safeguarding the company's data. It includes selecting the appropriate passwords and outlining procedures for file transfers and data storage. All these guidelines provided under a Cyber Security Policy will raise employee understanding of security and how it may be reinforced.
4) It can cut costs against cyberattacks
A cyberattack or a data breach can cost a huge financial disruption to an organisation. Hence, ensuring the right Cybersecurity policies can mitigate the risks and protect the interests of the organisation and the people related to it.
5) It protects the organisations’ assets
Implementing Cybersecurity Policies can aid in protecting the organisations’ assets (both digital and physical assets). The security policies will help the organisation keep track of its assets and ensure that it is safeguarded against external or internal threats.
6) It helps an organisation achieve its Goals
A well-crafted Cyber Security Policy can guide decisions within an organisation and help achieve its organisational goals. The drafted policy will state what the employees are permitted to do and what should not be done. It directs the best practices and helps the organisation in reducing any form of phishing attacks.
7) It addresses Security threats and mitigates IT security Vulnerabilities
The aim of crafting any Cyber Security Policy is to address the Cyber Security threats and implement the required strategies to minimise security vulnerabilities. Apart from mitigating the risks and vulnerabilities, it defines how to deal with an intrusion if it occurs.
Are you interested in detecting attacks and vulnerabilities before it infiltrates? If yes, then register with the CompTIA Cybersecurity Analyst CySA+ Certification course for expert training and help!
Discussing important Cyber Security Policies
Organisations use Cyber Security Policies to manage their network security. They set formal guidelines that their employees must follow. Many security policies are established automatically after the installation process. We can also alter the policies to suit the requirements of our environment. The following are some crucial cybersecurity policy suggestions:
Virus and spyware protection Policy
This policy helps to stop malware and other harmful code assaults on business computers, networks, and systems. This policy is crucial as it helps to avoid harm to user programmes, data, files, and hardware.
Antivirus software is a computer application that identifies, prevents, and acts against malicious software programs like viruses and worms. Most antivirus products have an auto-update capability that helps the program to download profiles of new viruses and scan them as soon as they are detected. Every computer system must have antivirus software as it is a minimal requirement to prevent cyber-attacks.
Account management Policy
This policy provides a standard for the establishment, management, use, and removal of the accounts that permit access to information and technological resources of the company.
Firewall Policy
A Firewall is a hardware or software program that aids in blocking hackers, viruses, and worms from trying to access your computer linked to the Internet. The Firewall checks each communication as it enters or leaves the Internet and blocks those that do not adhere to the set security standards. Firewalls play a significant role in malware detection to enhance the security system.
E-mail Policy
The term "email security" may refer to various policies and practices for protecting Email accounts, information, and communications from unwanted access, theft, or compromise. Usually, spam, malware, and phishing assaults propagate over email. Attackers lure victims into providing sensitive information by enticing them to open attachments or clicking on URLs that download malware onto the victim's device.
Email is an entry point for attackers who attempt to gain an advantage in a business network to infiltrate and avail sensitive data of the company. Hence, organisations need to employ an Email encryption system to protect potentially sensitive information from being read by any other viewer (other than the intended receivers) by encrypting or masking the content of email communications. Authentication is frequently used in email encryption.
This policy establishes guidelines for sending, receiving, or storing messages transferred by the corporate email system.
Intrusion prevention Policy
This policy helps install a system that can automatically detect and prevent browser and network assaults. Additionally, it shields applications against any vulnerabilities. It also examines one or more data packages and detects malware from the content that finds ways to enter the system through legitimate channels.
Security incident management Policy
This policy outlines the requirements for documenting and handling events involving information systems and business activities. The Incident response can help corporations detect security incidents as they happen and direct the necessary security measures.
Web Policy
This policy sets the guidelines for organisations regarding access to the Internet or Intranet and its Utilisation.
Patch management Policy
The computer systems and applications used for computing all have innate security flaws. These vulnerabilities allow the breeding and spread of malicious software, which might interfere with regular business activities. To effectively reduce this type of risk, software patches are introduced to ensure the elimination of a specific security Vulnerability.
Password Policy
The idea of usernames and passwords has long been used as a fundamental method for information security. It is one of the initial cybersecurity measures to protect information. This policy aims to provide a standard for creating secure passwords and guidelines for their protection, which involves the required frequency of password change to be followed.
Server Security Policy
This policy's objective is to provide requirements and limitations for the baseline configuration of internal server hardware owned, operated, or accessible through any channel on the company's internal network(s).
Conclusion
In this blog, we have discussed the role of Cybersecurity Policies in the digital world. We hope you have understood why Cybersecurity Policies need to be implemented and their importance in protecting against cyber-attacks.
Are you an expert professional with a high-level experience in a wide range of security zones? Then, this Microsoft Cybersecurity Architect SC100 training is for you.
Frequently Asked Questions
Upcoming IT Security & Data Protection Resources Batches & Dates
Date
 Certified Cyber Security Professional (CCS-PRO)
Certified Cyber Security Professional (CCS-PRO)
Fri 21st Mar 2025
Fri 23rd May 2025
Fri 22nd Aug 2025
Fri 5th Dec 2025







 Top Rated Course
Top Rated Course




 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


