We may not have the course you’re looking for. If you enquire or give us a call on +420 210012971 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.
Picture this: you’re casually browsing the internet, and suddenly, pop-up ads flood your screen, files vanish, or your system locks up, demanding ransom. This is Malware - an insidious force lurking in the digital shadows, waiting to strike. But what is Malware exactly, and how does it bypass our defences so effortlessly?
In this comprehensive overview, we’ll explore What is Malware, its history, the various types that exist, and, most importantly, how you can protect yourself from becoming a victim. Ready to dive into the world of digital defence? Let’s uncover the secrets of Malware and learn how to safeguard your digital life.
Table of Contents
1) What is Malware?
2) What Does Malware Do?
3) Different Types of Malwares
4) How to Prevent Malware Infections?
5) Benefits of Malware Protection
6) Conclusion
What is Malware?
Malicious software, or Malware, is designed to exploit or damage networks, services, or devices. Cybercriminals use Malware to disrupt systems, steal sensitive data, or gain unauthorised access.
Every variety aims to compromise the target's security and functionality, while their modes of spreading infection and effect vary. Anti-malware software, updated computers, firewalls, and safe browsing practices are all part of protecting against Malware. Strong passwords and routine backups further reduce the risks caused by malicious software.
History of Malware
Here’s a brief timeline of key milestones in the evolution of Malware:
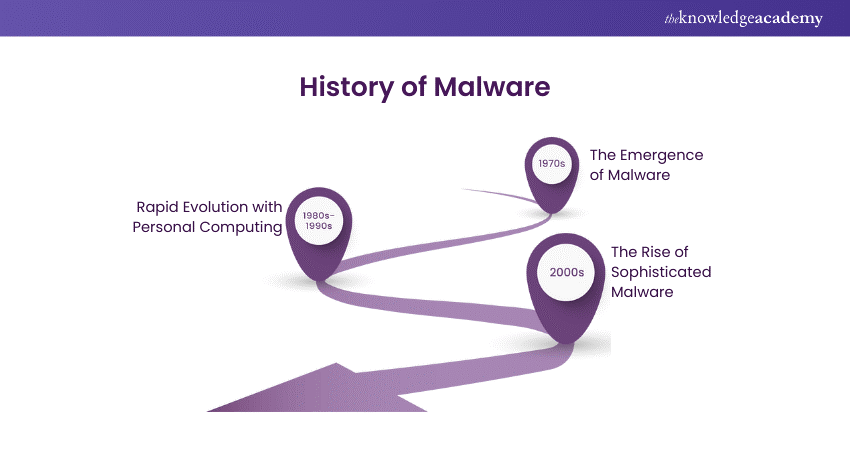
1) 1970s: The Emergence of Malware
a) Creeper Virus: The first known Malware to appear on ARPANET, the early internet. Although harmless, it marked the start of software being used for malicious purposes.
2) 1980s-1990s: Rapid Evolution with Personal Computing
a) Personal Computing Boom: The rise of personal computers led to rapid Malware evolution.
b) New Distribution Channels: The internet's introduction enabled Malware like the Brain virus (spread via floppy disks) and Melissa virus (spread via email attachments), highlighting the increasing threat of digital infections.
3) 2000s: The Rise of Sophisticated Malware
a) ILOVEYOU Virus (2000): Spread via email, causing global disruption and demonstrating the power of social engineering.
b) WannaCry Ransomware (2017): Exploited a Windows vulnerability, impacting hundreds of thousands of systems worldwide.
Impact: Highlighted the growing sophistication of Malware and the urgent need for strong Cyber Security measures.
What Does Malware Do?
Malware can have a wide range of effects, depending on its type and the intentions of its creator. Commonly, Malware is designed to:
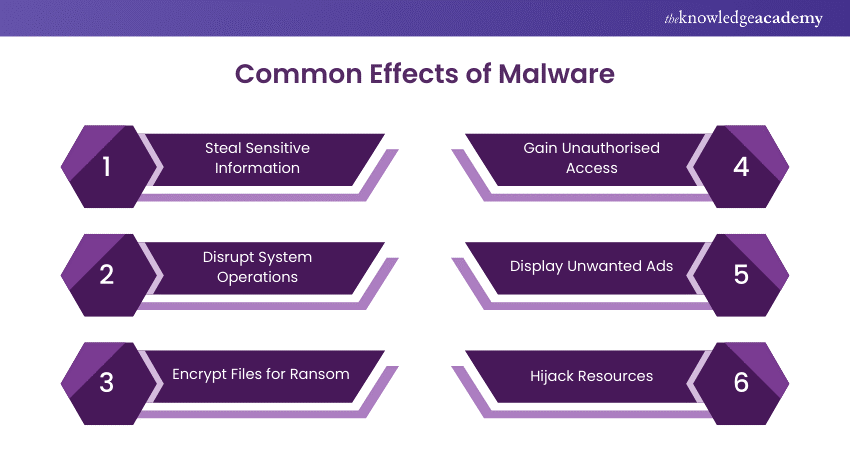
1) Steal Sensitive Information:
Spyware and keyloggers collect and send private information, like credit card details and passwords, to hackers.
2) Disrupt System Operations:
Worms and viruses can slow down or crash systems by taking resources, deleting files, and affecting data.
3) Encrypt Files for Ransom:
Ransomware encrypts documents and asks for money for their release, which usually leads to permanent data loss if the ransom is not paid.
4) Gain Unauthorised Access:
Trojans create backdoors, allowing attackers to gain control and unauthorised access to the infected device.
5) Display Unwanted Ads:
Adware bombards users with ads, potentially redirecting them to malicious sites that can further compromise their systems.
6) Hijack Resources:
Cryptojacking software quietly extracts cryptocurrency using your system's CPU and GPU, decreasing performance and raising costs related to energy.
Become a Certified Cyber Security Professional to safeguard digital environments with our Certified Cyber Security Professional (CCS-PRO) Course. Sign up now!
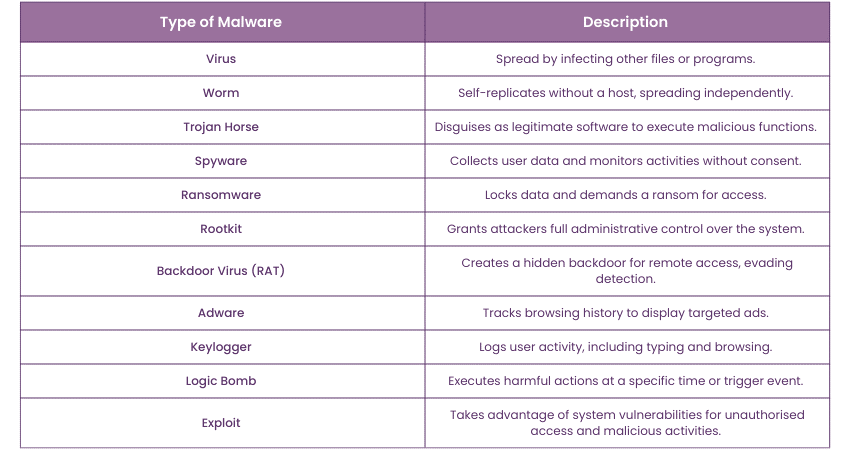
Different Types of Malware
Here are the unique traits and characteristics of different Types of Malware:
Develop advanced fraud detection strategies with our Fraud Analytics Course and start building a secure future today!
How to Prevent Malware Infections?
Preventing Malware infections requires a proactive approach to Cyber Security. Here are some effective strategies:
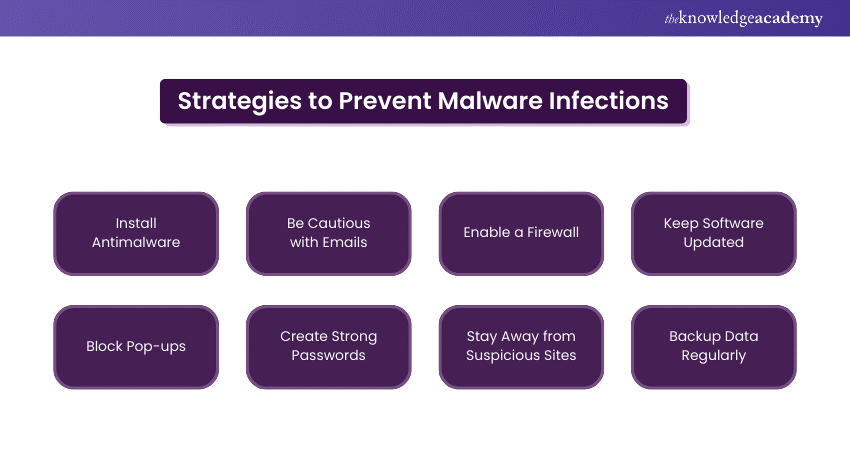
1) Install Antimalware
a) Essential for protecting PCs and network devices from Malware infections.
2) Be Cautious with Emails
a) Be careful with email attachments, especially from unknown senders.
b) Malware can be hidden in seemingly legitimate attachments.
3) Enable a Firewall
a) Set up a firewall on your network router.
b) Monitors and controls traffic, blocking unauthorised access and preventing Malware spread.
4) Keep Software Updated
a) Regularly update antimalware software to guard against new threats.
b) Updates often include patches for security vulnerabilities.
5) Block Pop-ups
a) Configure your web browser to block pop-ups.
b) Pop-ups can be gateways for Malware or lead to malicious sites.
6) Create Strong Passwords
a) Use strong, unique passwords for all accounts.
b) Enable multifactor authentication for added security.
7) Stay Away from Suspicious Sites
a) Avoid risky websites, especially those offering free downloads.
b) Such sites are often sources of Malware.
8) Backup Data Regularly
a) Regularly back up data to an offsite or offline location.
b) Protects against data loss in case of a Malware attack.
Protect your organisation from cyber attacks - start your journey with our Cyber Security Awareness Course today!
Benefits of Malware Protection
Malware protection offers several key benefits that help safeguard your devices and data:
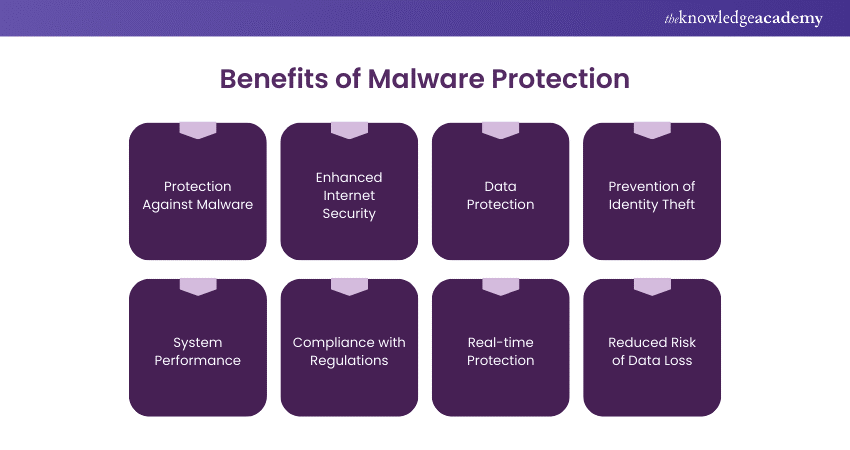
1) Protection Against Malware
a) Antimalware software detects and removes various types of Malware.
2) Enhanced Internet Security
a) Scans webpages, downloads, and emails for malicious content.
b) Secures online transactions by alerting users to fake payment portals.
3) Data Protection
a) Antimalware software safeguards sensitive data by detecting and blocking suspicious activities.
b) It prevents unauthorised access and makes sure that your files remain secure from Malware threats.
4) Prevention of Identity Theft
a) Antimalware software stops spyware and keyloggers.
b) This protection helps prevent identity theft by keeping your personal information, such as passwords, usernames, and credit card details, safe from malicious actors.
5) System Performance
a) Malware can significantly slow down your system.
b) By removing Malware, antimalware software helps maintain optimal system performance.
6) Compliance with Regulations
a) Using antimalware software helps comply with industry regulations and standards.
b) It protects digital assets and maintains consumer trust.
7) Real-time Protection
a) Antimalware solutions offer real-time protection.
b) They continuously monitor your system for threats.
c) These solutions respond immediately to any detected Malware.
8) Reduced Risk of Data Loss
a) Regular scans and updates provided by antimalware software reduce the risk of data loss.
b) The software identifies and mitigates threats before they can cause significant damage.
Step into the world of Cyber Security by mastering Malware Analysis Training to defend your systems and enhance your expertise!
Conclusion
Understanding What is Malware is essential to protect your digital life. By recognising the various types of Malware and implementing strong security measures, you can defend against these hidden threats. Stay informed, be proactive, and secure your devices to keep your online world safe from malicious attacks.
Stay ahead of cyber threats with our Cyber Security Training. Sign up today!
Frequently Asked Questions

The Malware collects data by
a) Infiltration
b) Keystroke Logging
c) Activity Monitoring
d) Data Extraction

a) To harm, disturb, or obtain illegal access to systems
b) To steal sensitive data, control devices, or extort money

The Knowledge Academy takes global learning to new heights, offering over 30,000 online courses across 490+ locations in 220 countries. This expansive reach ensures accessibility and convenience for learners worldwide.
Alongside our diverse Online Course Catalogue, encompassing 19 major categories, we go the extra mile by providing a plethora of free educational Online Resources like News updates, Blogs, videos, webinars, and interview questions. Tailoring learning experiences further, professionals can maximise value with customisable Course Bundles of TKA.

The Knowledge Academy’s Knowledge Pass, a prepaid voucher, adds another layer of flexibility, allowing course bookings over a 12-month period. Join us on a journey where education knows no bounds.

The Knowledge Academy offers various Cyber Security Training, including Malware Analysis Training, Certified Cyber Security Professional (CCS-PRO), Cyber Security Awareness and Fraud Analytics Training Course. These courses cater to different skill levels, providing comprehensive insights into Computer Worms.
Our IT Security & Data Protection Blogs cover a range of topics related to Malware Analysis, offering valuable resources, best practices, and industry insights. Whether you are a beginner or looking to advance your Cyber Security skills, The Knowledge Academy's diverse courses and informative blogs have got you covered.
Upcoming IT Security & Data Protection Resources Batches & Dates
Date
 Malware Analysis Training
Malware Analysis Training
Fri 14th Feb 2025
Fri 11th Apr 2025
Fri 13th Jun 2025
Fri 15th Aug 2025
Fri 10th Oct 2025
Fri 12th Dec 2025







 Top Rated Course
Top Rated Course



 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


