We may not have the course you’re looking for. If you enquire or give us a call on +45 89870423 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.
Does the constant flow of sensitive information within your company leave you uneasy? In the digital age, a robust system for Secure Internal Communication is no longer a luxury; it's a necessity. Data breaches and leaks can cripple a business, so how can you safeguard your confidential communications?
This blog dives into the world of Secure Internal Communication. We'll explore the key elements of a secure communication strategy, from encryption protocols to access controls. By understanding these practices, you can build a communication system that fosters collaboration while keeping your sensitive information safe. Let's ensure your internal conversations stay secure!
Table of Contents
1) Introduction to Secure Internal Communication
2) Why is Secure Internal Communication Important?
3) Five effective strategies for Secure Internal Communication
4) Challenges and Threats in Internal Communication Security
5) Essential Technological Features for Ensuring Secure Internal Communications
6) How to Select a Secure Internal Communications Platform?
7) Conclusion
Introduction to Secure Internal Communication
Secure Internal Communication stands as a cornerstone of organisational success. It encompasses numerous strategies, protocols, and technologies to mitigate risks while facilitating seamless communication among employees, departments, and stakeholders. Effective communication skills are crucial for ensuring clear and accurate message delivery. Encryption lies at the heart of SIC, with cryptographic algorithms employed to transform plaintext data into ciphertext.
Additionally, SIC mechanisms verify the identities of communicating parties, preventing impersonation or unauthorised access to communication channels. By implementing robust SIC measures, organisations can foster trust among stakeholders and mitigate the impacts of cyber attacks.
Importance of Secure Internal Communication
Ensuring the security of internal communications is crucial for protecting confidential information related to employees and the company. Private details such as banking information, health insurance particulars, and residential addresses are vulnerable in the event of a security lapse.
A cyber incident targeting internal communications can trigger a cascade of data breaches, affecting not only stakeholders but also customers. Once the damage is done, it’s challenging to reverse the effects and regain trust with a simple apology. The fallout from a breach in internal communication security may involve:
a) Misuse of sensitive data: Employee and customer information, once compromised, is at risk of being misused by cybercriminals.
b) Reputational erosion: Trust is the cornerstone of any relationship, and a breach can significantly undermine the confidence that customers, partners, and stakeholders place in a company.
c) Economic repercussions: The financial impact of a security breach extends beyond immediate rectification costs and legal fines; it can also lead to the loss of employees, customers, and revenue.
d) Legal consequences: Non-compliance with data protection laws like GDPR, HIPAA, or PCI DSS can result in hefty fines and legal action following a breach.
e) Operational disruptions: A security breach can halt regular business activities, causing operational downtime, reduced productivity, and negatively affecting employee morale and engagement.
f) Diminished trust: The most profound and lasting effect of a security breach is the loss of trust from employees and customers who rely on an organisation to safeguard their personal information.
Five effective strategies for Secure Internal Communication
Certain strategies are crucial for safeguarding Internal Communication. Hence, we have discussed the five recommended approaches below to bolster security and protect sensitive data. Organisations can employ those strategies within the organisational networks:
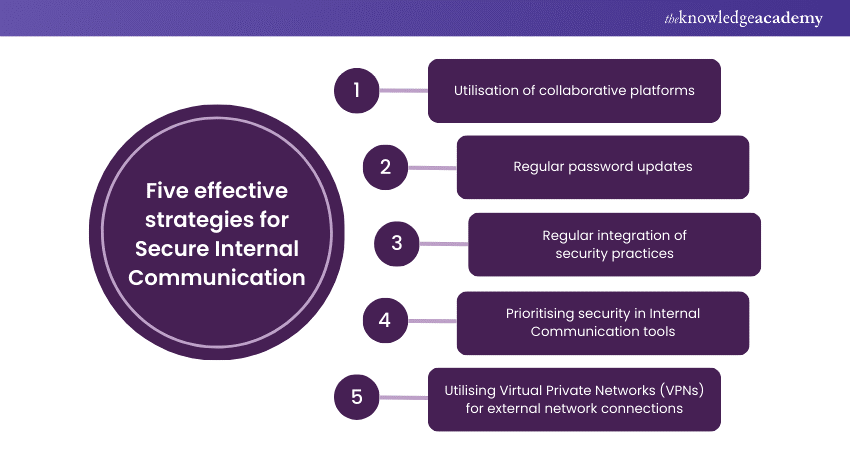
Utilisation of Collaborative Platforms
Use platforms such as Microsoft Teams, Slack, or Asana for secure communication. These tools offer encrypted messaging, secure file sharing, and efficient project management, streamlining workflows while maintaining data integrity.
2) Regular Password Updates
Establish a routine for updating passwords to prevent unauthorised access. Enforcing strong password protocols is a critical defense mechanism against cyber intrusions.
3) Regular Integration of Security Practices
Incorporate security measures into everyday tasks with continuous education and the application of encryption standards. This integration strengthens the organisation’s resistance to cyber threats.
4) Prioritising Security in Internal Communication Tools
Opt for internal communication tools that provide end-to-end encryption and multi-factor authentication (MFA). These features are essential for a robust security infrastructure.
5) Utilising Virtual Private Networks (VPNs) for External Network Connections
Use Virtual Private Networks (VPNs) to connect to the company’s network from external locations securely. VPNs provide a protected channel, ensuring that sensitive information remains confidential during transmission.
Unlock the confidence to navigate any situation with our Assertiveness Skills Training – Sign up now!
Challenges and Threats in Internal Communication Security
With the proliferation of cyber threats, safeguarding Internal Communication becomes increasingly imperative. Some common Internal Communication threats and how organisations can address them are discussed below:
1) Increasing Incidence of Cyber Threats
Organisations must combat the rising tide of cyber threats, including phishing attacks and malware infections. All these threats can pose significant risks to Internal Communication Security.
2) Limited Awareness Among Employees Regarding Secure Communication Practices
Addressing the gap in employee awareness of secure communication practices through comprehensive training sessions is crucial. As a result, organisations must educate employees on how to prevent security breaches.
3) Managerial Difficulty in Monitoring Employee Communications
Companies ought to strike a balance between security and privacy concerns when monitoring employee communications. Additionally, clear policies and transparent communication are key to maintaining trust.
4) Absence of an Integrated Security Policy for Communication
Creating and executing a thorough security policy is crucial for customising internal communication requirements. Thus, businesses should employ a cohesive strategy that enhances security and minimises vulnerabilities.
Take charge of your success with our Effective Communication Skills Training – join us now!
Essential technological features for ensuring Secure Internal Communications
To safeguard internal communication channels, companies need to implement certain technological features that provide robust protection against various threats. Some of those features are listed below:
a) Data Encryption: Encryption on-device and in the cloud ensures conversations and company assets remain inaccessible to unauthorised individuals.
b) Secure Instant Messaging: Allows managers and employees to exchange files and discuss work-related topics securely, without the distractions or security risks of personal messaging.
c) User Permissions: Defines who can access specific assets and conversations, ensuring sensitive information is only available to authorised personnel.
d) Cloud-based Storage: Limits information stored on employees’ devices, providing greater control over company assets and enhancing security.
e) Multi-factor Authentication: Requires users to verify their identity, typically by entering a code sent to their mobile phone, in addition to a password, thereby enhancing security.
f) Centralised Security Management and Monitoring: Ensures consistent enforcement of security policies across all communication channels, with real-time monitoring, alerts, and reporting.
g) Incident Response and Threat Intelligence Capabilities: Enables businesses to respond quickly to potential security threats and prevent data breaches.
h) Logging and Auditing Features: Tracks all communication activities, providing detailed records for compliance and incident investigation purposes.
i) Advanced Analytics and Reporting: Offers insights into communication patterns, user behaviour, and potential security threats, enabling proactive security measures.
j) Integration with Existing Systems: Seamless integration with existing systems and applications enhances efficiency and ensures a cohesive digital ecosystem.
k) Security and Compliance: Ensure tools comply with industry regulations and data protection laws to prevent potential legal issues.
How to select a Secure Internal Communications platform?
When choosing a communication platform, organisations must prioritise usability and compatibility to ensure seamless integration and user adoption. Discussed below are some effective tactics to guide them in this endeavour:
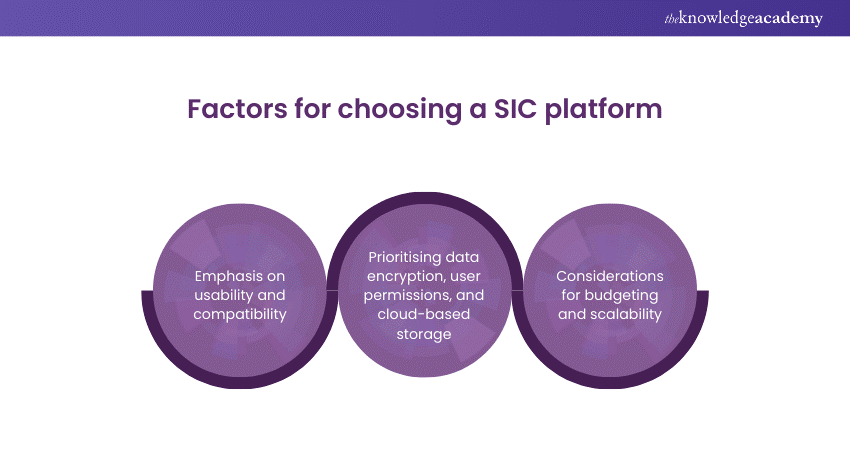
1) Emphasis on Usability and Compatibility
Select a communication platform that prioritises user-friendly design and seamless integration with existing systems. Usability and compatibility promote user adoption and efficiency across various communication media.
2) Prioritising Data Encryption, User Permissions, and Cloud-based Storage
Choose platforms offering advanced data encryption, customisable user permissions, and secure cloud-based storage. These features enhance data security and compliance.
3) Considerations for Budgeting and Scalability
Balance budget constraints with scalability requirements when selecting a Secure Internal Communications platform. An investment in scalable solutions ensures long-term viability and cost-effectiveness.
Conclusion
In conclusion, Secure Internal Communication can foster collaboration, protect sensitive information, and ensure organisational success. Hence, it is imperative for organisations to select SIC platforms that align with their unique needs and objectives. The appropriate platforms can enable them to effectively navigate the evolving landscape of digital threats.
Unleash your full potential on stage with our Public Speaking Course – register today!
Frequently Asked Questions

SIC (Secure Internet Connection) refers to a method of encrypting data in networking. This method ensures secure communication between devices, often utilised in VPNs for confidentiality and integrity.

The protocol commonly used to secure communication is Transport Layer Security (TLS), which encrypts data transmissions over a network, ensuring privacy, authentication, and data integrity between communicating applications.

The Knowledge Academy takes global learning to new heights, offering over 30,000 online courses across 490+ locations in 220 countries. This expansive reach ensures accessibility and convenience for learners worldwide.
Alongside our diverse Online Course Catalogue, encompassing 17 major categories, we go the extra mile by providing a plethora of free educational Online Resources like News updates, Blogs, videos, webinars, and interview questions. Tailoring learning experiences further, professionals can maximise value with customisable Course Bundles of TKA.

The Knowledge Academy’s Knowledge Pass, a prepaid voucher, adds another layer of flexibility, allowing course bookings over a 12-month period. Join us on a journey where education knows no bounds.

The Knowledge Academy offers various Communication Skills Training, including the Public Speaking Course, Assertiveness Skills Training, and Negotiation Skills Training. These courses cater to different skill levels, providing comprehensive insights into Delegation Skills for Effective Leadership.
Our Business Skills Blogs cover a range of topics related to Effective Delegation, offering valuable resources, best practices, and industry insights. Whether you are a beginner or looking to advance your Business skills, The Knowledge Academy's diverse courses and informative blogs have got you covered.
Upcoming Business Skills Resources Batches & Dates
Date
 Public Speaking Course
Public Speaking Course
Fri 28th Feb 2025
Fri 11th Apr 2025
Fri 27th Jun 2025
Fri 22nd Aug 2025
Fri 24th Oct 2025
Fri 28th Nov 2025







 Top Rated Course
Top Rated Course



 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


