We may not have the course you’re looking for. If you enquire or give us a call on +44 1344 203 999 and speak to our training experts, we may still be able to help with your training requirements.
We ensure quality, budget-alignment, and timely delivery by our expert instructors.

Memory is the heart of any computer or electronic device, acting as the workspace where the processor stores and accesses data and instructions. Among the various types of memory, RAM and ROM are the most prominent, each with its own unique characteristics and functions. But What is ROM exactly?
ROM, or Read-Only Memory, is a type of non-volatile memory that permanently stores data and instructions. Unlike RAM, which can be modified and erased, ROM is read-only and cannot be altered by the processor. It's primarily used to store the bootstrap process that initiates system startup. ROM is also found in many other devices, such as calculators, washing machines, and ovens.
As a non-volatile memory, ROM ensures data retention even when the power is off, storing essential data and firmware needed to boot electronic devices. In this blog, we will explore What is ROM, its features, types, advantages, and disadvantages.
Table of contents
1) Understanding What is ROM
2) Block Diagram of ROM
3) The Internal Structure of ROM
4) How Does ROM Work?
5) Types of ROM
6) Example Applications of ROM
7) Advantages and Disadvantages of Different Types of ROM
8) Difference Between RAM and ROM
9) Conclusion
Understanding What is ROM
ROM is an acronym for Read Only Memory. It is a type of permanent or non-volatile memory that stores instructions and data permanently. Non-volatile means that the data does not disappear when the power is turned off. Read-Only Memory is mainly used to store the bootstrap process that helps to start the system. The bootstrap process is a set of instructions that tells the processor how to load the operating system and other essential programs. ROM is also used to store firmware, which is software that controls the basic functions of hardware devices, such as keyboards, mice, printers, etc.
Unlock your potential in the digital age with our comprehensive Computer Science and Fundamentals Training – Empower Your Future Today!
Block Diagram of ROM
It consists of n input lines and m output lines. The m input lines are used in this circuit diagram to receive the input address for the ROM. The input address in this diagram is determined by where you want to access the content of the ROM.
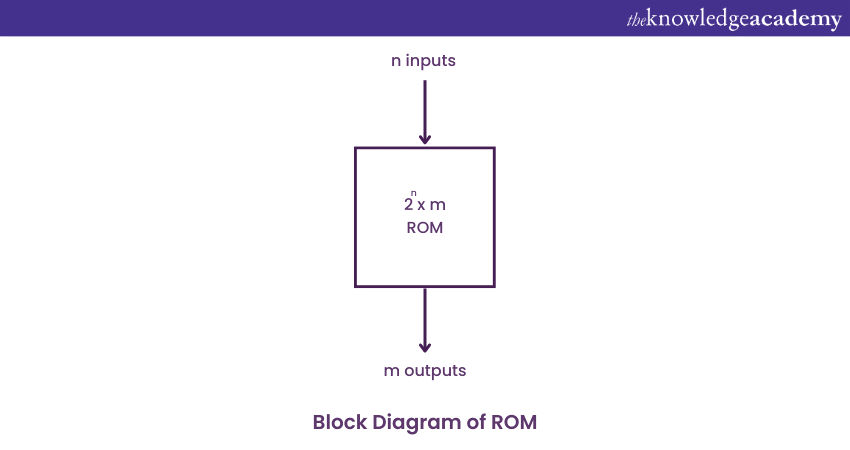
Since each of the m input lines is binary in nature, they can either hold the value 0 or 1. There are a total of 2^n addresses that are referred to by the input lines, and each of these addresses contains m bit information. This information is presented as the output of the ROM. Such a ROM is specified by 2^n x m ROM notation.
Internal structure of ROM
The internal structure of Read-Only Memory consists of two basic components: a decoder and OR gates. A decoder is a circuit combination that converts a coded form (such as binary) to a normal form (such as decimal). The input is binary, and the output is decimal. The OR gates in the Read-Only Memory take the outputs of the decoder as their inputs. This ROM can store 64 words, each with 4 bits.
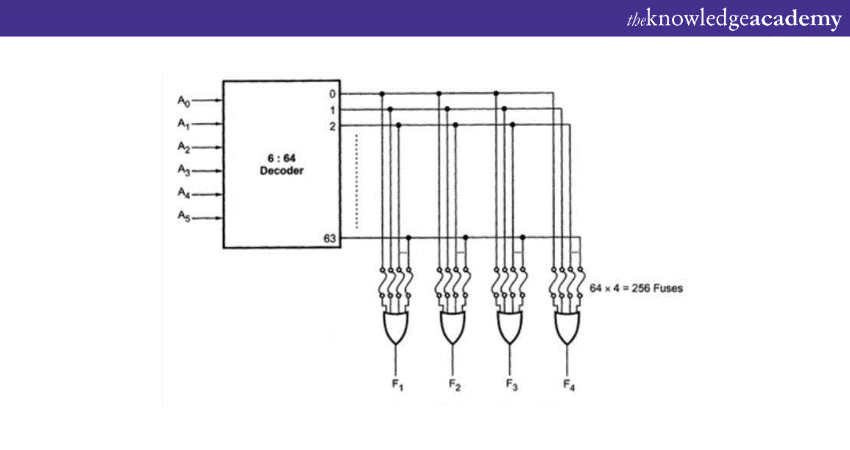
There are four output lines, and one of the 64 words is selected by the six input lines. The input lines specify the address of the word in binary. For example, if the input is 000000, the output is word number 0. If the input is 111111, the output is word number 63.
How Does ROM Work?
ROM is powered by a small, long-life battery within the computer. It consists of two basic components: a decoder and OR logic gates. The decoder receives binary input and converts it to its decimal equivalent. The OR gates use the decoder's decimal output as their input.
ROM functions like a disk array and contains a grid of rows and columns to manage system operations. Each element in the grid corresponds to a specific memory element on the ROM chip, connected by diodes.
When a request is made, the address input locates the specific memory location. The value read from the ROM chip corresponds to the contents of the selected array element.
Unlock your IT potential with our IT Fundamentals Training – take the first step towards a tech-savvy future!
Types of ROM
There are different types of Read-Only Memory, depending on how they are programmed and modified. Some of the common types are:
1) MROM (Masked ROM)
This type of ROM has the data hard-wired into it during the manufacturing process. It is inexpensive and fast, but it cannot be changed or updated by the user. For example, an MROM chip may store the Basic Input/Output System (BIOS) of a computer, which contains the instructions for booting and initialising the hardware components.
2) EPROM (Erasable Programmable ROM)
This type of ROM can be erased and reprogrammed by exposing it to ultraviolet light for a certain period of time. The ultraviolet light removes the charge that stores the data in the ROM chip. After erasing, the user can program new data using a PROM Programmer. For example, an EPROM chip may store the software of a video game console, which can be updated by replacing the old chip with a new one.
3) Mask ROM
This is a type of ROM that is customised for a specific application or device during the manufacturing process. The data stored in mask ROM cannot be changed or erased by any means.
Mask ROM is also known as custom ROM or application-specific ROM. Mask ROM is fast and reliable, but it lacks flexibility and adaptability. Mask ROM is used for storing programs that are unique to a particular device or system, such as video game cartridges and embedded systems.
4) Programmable Read Only Memory (PROM)
PROM, or Programmable Read-Only Memory, starts as an empty ROM. The process begins with the creation of a blank memory, followed by programming. An electronic device called a PROM Programmer or PROM burner writes data onto the PROM chip.
Once programmed, the PROM cannot be altered, which is why it is known as a one-time programmable device. During programming, current flows through all possible paths in the chip. The programmer uses high voltage to burn out unwanted fuses, selecting a specific path for the current. This allows users to add data and instructions according to their needs.
5) Erasable Programmable Read Only Memory (EPROM)
This is a type of ROM that can be programmed and erased by the user multiple times using ultraviolet light. The data stored in EPROM can be read by the computer but not modified by the user. EPROM is also known as UV erasable ROM or UV ROM.
EPROM offers more flexibility and reusability than PROM, but it requires a special device called an EPROM eraser, and it takes a long time to erase the data. EPROM is used to store programs that need to be updated occasionally, such as software updates and patches.
6) Electrically Erasable Programmable Read Only Memory (EEPROM)
EEPROM, or Electrically Erasable Programmable Read-Only Memory, was designed to address the limitations of EPROM. Unlike EPROM, EEPROM allows for multiple erases and reprograms without the need for specialised tools or ultraviolet light.
Its main advantage is the ability to update specific data without having to erase the entire chip first. This means you won't lose important information when updating your EEPROM chip.
Unlock your potential in this digital age with our extensive Computer Science Course – Empower Your Future Today!
Example Applications of ROM
ROM is used in various hardware components, including computer systems, game consoles, and embedded devices. Here are some common applications:
a) Operating Systems: ROM stores essential components of the Operating System (OS), ensuring they remain intact even when the power is turned off and back on.
b) Firmware: Devices like BIOSuse ROM to store firmware, which initialises hardware components during the boot process.
c) System Settings: Critical system settings and configurations are often stored in ROM.
d) Game Consoles: Game cartridges use ROM chips to store game data permanently.
Unlock the power of your computer with our Computer Hardware Troubleshooting Masterclass – troubleshoot like a pro today!
Advantages and disadvantages of different types of ROM
The advantages and disadvantages of different types of Read-Only Memory are summarised in the table below:
|
Type |
Advantages |
Disadvantages |
|
MROM |
Cheap, reliable, permanent |
Inflexible, unchangeable |
|
PROM |
Customisable, permanent |
Expensive, limited capacity |
|
EPROM |
Flexible, reusable |
Requires UV light, slow erasure |
|
EEPROM |
Flexible, reusable, fast erasure |
Expensive, limited lifespan |
|
Flash EPROM |
Flexible, reusable, fast erasure, high capacity, low power |
Expensive, limited lifespan |
|
Mask ROM |
Fast, reliable, permanent |
Inflexible, unchangeable |
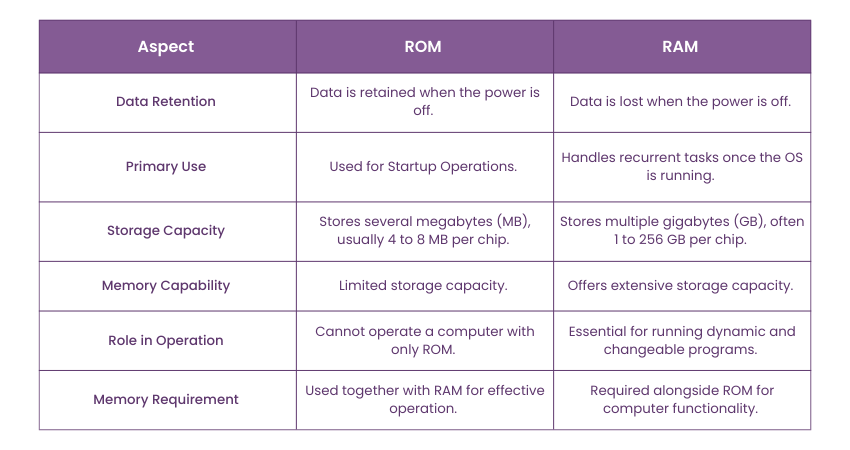
Difference Between RAM and ROM
This table highlights the differences and roles of ROM and RAM in a computer system. Understanding these distinctions is important for optimising performance and ensuring efficient operation.
Conclusion
In this blog, we discussed What is ROM, its features, types, advantages, and disadvantages. Read-Only Memory is an important component in many devices and systems. It provides fast access to data, protects it from accidental changes, reduces power consumption, and enhances security. ROM is used to store firmware or software that controls basic functions such as booting and initialising systems.
Empower your team with End User Training for enhanced productivity and efficiency today!
Frequently Asked Questions
How Long can Data be Retained in ROM?

Data in ROM can be retained indefinitely, as it is non-volatile memory. It does not require power to maintain its contents, allowing data to persist for the life of the device. ROM is used to store permanent data, such as firmware, that does not need frequent updates or changes.
What are the Four Levels of Computer Memory?

The four levels of computer memory are registers, cache, main memory (RAM), and secondary storage (e.g., hard drives, SSDs). Registers are the fastest and smallest, followed by cache memory. RAM offers more space but is volatile, while secondary storage provides large, non-volatile storage for long-term data retention.
What are the Other Resources and Offers Provided by The Knowledge Academy?

The Knowledge Academy takes global learning to new heights, offering over 3,000 online courses across 490+ locations in 190+ countries. This expansive reach ensures accessibility and convenience for learners worldwide.
Alongside our diverse Online Course Catalogue, encompassing 19 major categories, we go the extra mile by providing a plethora of free educational Online Resources like News updates, Blogs, videos, webinars, and interview questions. Tailoring learning experiences further, professionals can maximise value with customisable Course Bundles of TKA.
What is The Knowledge Pass, and How Does it Work?

The Knowledge Academy’s Knowledge Pass, a prepaid voucher, adds another layer of flexibility, allowing course bookings over a 12-month period. Join us on a journey where education knows no bounds.
What are the Related Courses and Blogs Provided by The Knowledge Academy?

The Knowledge Academy offers various End User Training, including Keynote Training, Google G Suite Training and the LibreOffice Training. These courses cater to different skill levels, providing comprehensive insights into How to Improve End User Experience.
Our Office Applications Blogs cover a range of topics related to End User Experience, offering valuable resources, best practices, and industry insights. Whether you are a beginner or looking to advance your Office Applications, The Knowledge Academy's diverse courses and informative blogs have got you covered.
Upcoming Office Applications Resources Batches & Dates
Date
 Computer Science Course
Computer Science Course
Fri 6th Jun 2025
Fri 8th Aug 2025
Fri 3rd Oct 2025
Fri 5th Dec 2025






 Top Rated Course
Top Rated Course



 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


