We may not have the course you’re looking for. If you enquire or give us a call on +44 1344 203 999 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.

As a Network Engineer or Network Analyst, you must be familiar with the term Networking. But when it comes to interviews, can you clear the tough Networking Interview Questions that probe your expertise? By engaging with these interview questions, you’ll not only solidify your knowledge but also sharpen your ability to articulate complex concepts, giving you the edge in your next Networking interview. So, wait no more to crack your interviews! This blog is designed to equip you with the Top Networking Interview Questions to ensure your success. Read ahead to learn more!
Table of Contents
1) Basic-level Networking Interview Questions
2) Intermediate-level Networking Interview Questions
3) Advanced Networking Interview Questions
4) Conclusion
Basic-level Networking Interview Questions
Explore basic Networking Interview Questions through the following introductory questions that will assess your foundational knowledge in Networking principles and technologies:
1) What is a VPN?
When asked this topic, interviewers often try to evaluate the candidate's understanding of basic Networking concepts and Cybersecurity procedures.
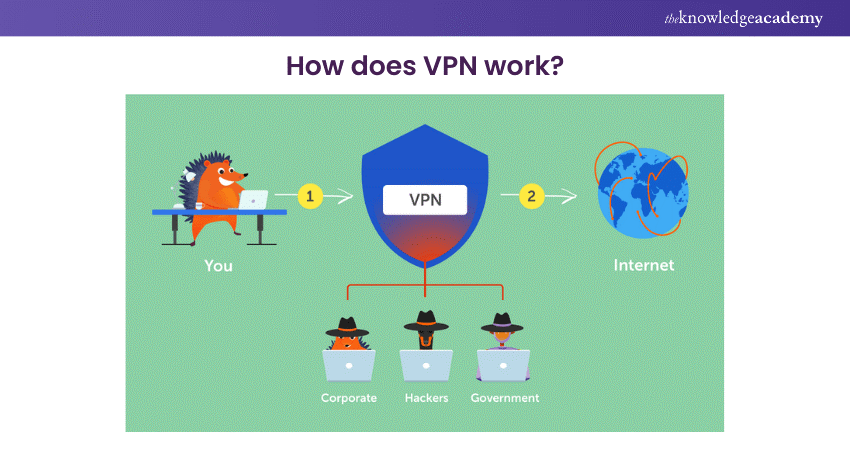
Here’s a sample answer:
Virtual Private Network (VPN) is used to set up private connections over unsecured networks such as the internet. VPNs protect users' privacy and security by encrypting data during transit between their device and the VPN server. This encryption mechanism renders intercepted data indecipherable, thus fortifying protection against potential breaches.
2) What is Internetworking?
This question aims to determine the candidate's understanding of Networking concepts, especially the combination of multiple computer networks.
Here's a sample answer:
Internetworking is the process of incorporating multiple computer networks to create a single, wide network architecture that allows for smooth communication and data exchange across different devices. The installation of routers, switches, and gateways allows for efficient data transmission and enables internetworking by connecting interconnected networks.
Join our VPN Training and secure your digital connections today!
3) Define HTTPS protocol.
Inquiring about HTTPS protocol underscores the significance of secure communication protocols in web-based interactions. Candidates are expected to demonstrate comprehension of HTTPS, a cornerstone technology underpinning secure web browsing and online transactions.
Here's a sample answer:
Hypertext Transfer Protocol Secure, or HTTPS, represents an extension of the conventional HTTP protocol tailored for secure data transmission across computer networks, predominantly the Internet. HTTPS emphasises data security by encrypting data exchanged between web browsers and servers, protecting sensitive information.
This includes user credentials and financial transactions, thwarting interception by malicious entities. HTTPS establishes a secure communication channel between the client and server using SSL/TLS encryption protocols.
4) Name some services provided by the Application Layer in the Internet model.
This question concentrates on the OSI model's application layer, testing candidates' understanding of the various services provided by this layer to support network applications and user interactions.
Here's a sample answer:
The Application Layer of the OSI model comprises of a variety of services designed to help network applications function and promote smooth communication between end-user devices. Among the numerous services provided by the application layer, significant instances include the following:
1) Email services include protocols like SMTP for email transmission and POP3/IMAP for email retrieval.
2) File transfer services, such as FTP, SFTP, and SCP.
3) Web browsing and data retrieval are supported by HTTP and its secure equivalent, HTTPS.
4) Domain Name System (DNS) functionality is pivotal for translating domain names into corresponding IP addresses.
5) Remote access and terminal emulation services, exemplified by Telnet and SSH.
6) Network Management Protocols like SNMP.
7) Directory services such as LDAP are instrumental in facilitating user authentication and directory management.
8) Real-time communication and collaboration services, including VoIP protocols like SIP and instant messaging protocols like XMPP.
5) What happens in the OSI model when a data packet moves from the lower to upper layers?
Networking Interview Questions about data packet traversal within the OSI model are designed to evaluate candidates' understanding of the Encapsulation process and the specific functionalities provided by each OSI layer.
Here's a sample answer:
As a data packet progresses through the levels of the OSI model, it undergoes a transformation known as Encapsulation. The Encapsulation process unfolds as follows:
a) At the Physical Layer (Layer 1), data packets are encoded into signals, with headers containing attributes like voltage levels and MAC addresses.
b) The Data Link Layer (Layer 2) frames packets, adding source/destination MAC addresses and error detection.
c) The Network Layer (Layer 3) adds IP addresses and routing information.
d) The Transport Layer (Layer 4) includes port numbers and checksums for transmission reliability.
e) Upper layers (Layers 5-7) add application-specific data for tasks like encryption and protocol processing, collectively ensuring efficient data transmission and processing.
6) What happens in the OSI model when a data packet moves from the upper to lower layers?
This question tests the candidate's knowledge of the OSI model's data Decapsulation process.
Here's a sample answer:
As a data packet traverses the OSI model layers during data Decapsulation, it undergoes successive transformations. Here's how:
a) Beginning from the upper layers (7-5), it sheds application-specific headers, progressing downwards.
b) At the Transport Layer (4), port numbers and checksums are removed.
c) The Network Layer (3) discards IP addresses and routing details.
d) While the Data Link Layer (2) sheds frame encapsulation.
e) Finally, at the Physical Layer (1), the packet transforms into pure data for transmission.
7) What is a Zone-based Firewall?
This question asks about the candidate's knowledge of advanced Network Security methods.
Here's a sample answer:
A Zone-based Firewall divides network segments into zones and controls traffic flow according to specified security policies. It improves Network Security by managing traffic between zones. It offers precise control, and segmentation to prevent illegal entry and threats.
8) What is a Server Farm?
When presented with this Networking Interview Question, interviewers seek to evaluate the candidate's comprehension of Data Centre Architecture and server deployment strategies. Proficiency in server farm deployment and management is crucial for professionals tasked with provisioning scalable and resilient IT infrastructures.
Here's a sample answer:
A Server Farm epitomises a centralised aggregation of multiple servers or computing resources clustered together within a data centre environment. It helps furnish scalable, high-performance computing capabilities.
Serving as the backbone of modern data centre architectures, Server Farms consolidate and centrally manage computing resources. They enable organisations to meet escalating demands and ensure optimal service delivery.
9) What is Confidentiality, Integrity and Availability?
This question examines the candidate's knowledge of key Information Security principles, including Confidentiality, Integrity, and Availability. Knowledge of these principles is critical for Cybersecurity professionals in charge of protecting sensitive data and maintaining resource integrity and accessibility.
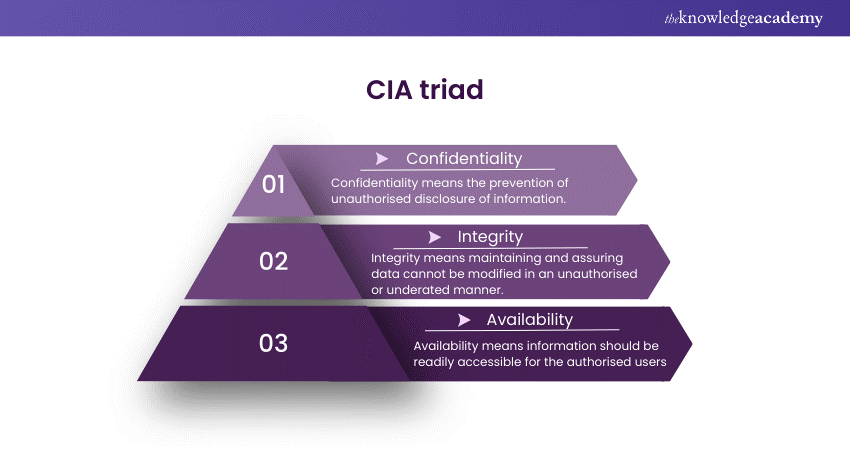
Here's a sample answer:
Confidentiality, Integrity, and Availability (CIA) are fundamental concepts in Information Security that ensure the protection, integrity, and accessibility of organisational data assets.
a) Confidentiality: Protects sensitive information by limiting access through access controls, encryption, and data categorisation.
b) Integrity: Ensures data accuracy and reliability by preventing unauthorised changes. Measures such as Cryptographic hashing and digital signatures ensure validity and identify manipulation.
c) Availability: Ensures authorised users can access resources by maintaining resilient infrastructure, redundancy, and disaster recovery strategies.
10) What is NOS in Computer Networking?
This question tests the candidate's knowledge of Network Operating Systems (NOS).
Here's a sample answer:
The Network Operating System (NOS) is specialised software that manages and administers network resources, devices, and services in Computer Networks. NOS is distinguished by its focus on promoting network-centric functionalities and acts as the foundation of network infrastructure management. NOS platforms empower Network Administrators to streamline network operations and optimise resource utilisation.
Unlock Networking fundamentals and accelerate your IT career today with our Introduction to Networking Training!
11) What is POP3?
Proficiency in POP3 is integral for individuals tasked with configuring email clients and managing electronic mail systems. Inquiry into POP3 Protocol elucidates the candidate's understanding of email protocols and their role in electronic mail transmission.
Here's a sample answer:
Post Office Protocol3 (POP3) retrieves email from a server to a local client, operating over TCP/IP. It's efficient but lacks features like folder synchronisation. POP3 uses a download-and-delete model, removing messages from the server upon retrieval. IMAP has largely supplanted it due to its broader functionality in modern email systems.
12) What do you understand by MAC address?
A Media Access Control (MAC) address is a unique hardware identifier for network interfaces, like network cards. It's expressed in alphanumeric characters and remains fixed. MAC addresses ensure devices are distinguishable in networks, aiding data packet delivery. These are immutable and vital for tasks like Ethernet frame forwarding and device identification in network communication.
13) What is an IP address?
This question targets the candidate's understanding of foundational identifiers critical for network communications and resource identification. Proficiency in IP addressing is indispensable for network administrators tasked with configuring and managing network devices and infrastructures.
Here's a sample answer:
An IP address labels networked devices, aiding their identification and communication across networks. It's crucial for internet communication, structured as decimal numbers separated by periods (e.g., 192.168.0.1 for IPv4).
IP addresses enable efficient routing and data delivery. IPv6 expands address space to accommodate more devices. They're vital for host addressing, routing, and seamless communication in IP-based networks.
14) What is a private IP address?
This question aims to evaluate the candidate's understanding of private IP addressing schemes.
Here's a sample answer:
A private IP address is for internal networks and is not accessible from the internet. It follows specific address ranges for local communication, creating isolated networks shielded from external access.
15) Differentiate between static IP addressing and dynamic IP addressing.
This question seeks to assess the candidate's understanding of IP addressing paradigms, specifically static and dynamic addressing, and their implications for network configuration and management.
Here’s how they differ:
|
Aspect |
Static IP Addressing |
Dynamic IP Addressing |
|
Definition |
IP address manually assigned to a device or network |
IP address automatically assigned by a DHCP server |
|
Configuration |
Manually configured by network administrator |
Automatically assigned upon device connection |
|
Stability |
Remains constant unless manually changed |
Can change over time, depending on DHCP lease duration |
|
Management |
Requires manual management and updates |
Less administrative overhead due to automatic allocation |
|
Security implications |
Potentially more secure as address doesn't change |
May introduce security risks due to changing addresses |
|
Scalability |
Less flexible for large networks |
More flexible for large networks due to dynamic allocation |
|
Cost |
May incur additional costs for each static IP address |
Typically, more cost-effective due to shared IP resources |
16) What are Routers?
This question is designed to examine the candidate's knowledge of Networking devices and their role in facilitating data transmission and network communication.
Here's a sample answer:
Routers are Networking devices which transfer data between networks. They operate at the Network Layer and use IP addresses to route traffic. Routers determine the best paths for data using routing protocols and tables, facilitating communication between networks. They offer functions like packet forwarding, NAT, QoS, and firewalling.
17) What is Data Encapsulation?
This question seeks to evaluate the candidate's comprehension of fundamental Networking concepts, underpinning the OSI model and the transmission of data across network layers.
Here’s a sample answer:
Data Encapsulation is the process of packaging data with suitable data, such as headers and trailers, as it passes through the various layers of a network protocol architecture. Each layer adds layer-specific metadata to the information packet to ensure correct routing and distribution throughout the network.
18) What is RAS?
This question aims to assess the candidate's familiarity Networking technologies.
Answer: RAS stands for Remote Access Service in Networking. It refers to the protocols and features that enable remote users to safely connect to a network through a communication link, such as a dial-up connection or a VPN. RAS allows users to interact with network services and resources as if devices were directly linked to the network.
19) What are the criteria for the best path selection of a Router?
In this question, the interviewer seeks to evaluate the candidate's understanding of routing protocols and the factors that influence a router's selection of the optimal path for data transmission.
Here's a sample answer:
Router path selection criteria:
1) Reachability: Determines if the destination network or host is accessible through the router's interfaces or learned routes from neighbouring routers.
2) Cost or metric: Utilises routing metrics like hop count, bandwidth, delay, and reliability to assess path efficiency. Routers prioritise paths with lower cumulative cost or metric values based on routing protocol-specific algorithms.
3) Administrative Distance: Assigns a numerical value to routing protocols or routes, indicating their trustworthiness or preference. Lower administrative distance values denote higher priority, guiding routers to prefer routes with lower administrative distance for data transmission.
4) Path stability: Considers historical routing data, route flapping events, and real-time network conditions to assess path reliability. Stable paths with minimal packet loss, latency, or congestion are favoured over unstable routes prone to disruptions.
5) Policy-Based Routing (PBR): Implements traffic forwarding policies or Quality of Service (QoS) requirements. This involves directing traffic based on user-defined criteria such as Access Control Lists (ACLs), packet attributes, or routing policies.
Build strong IT foundations and propel your career forward today with our IT Fundamentals Training!
Intermediate-level Networking Interview Questions
Explore intermediate Networking concepts through the following questions that assesses knowledge of Networking technologies:
1) What is the Software Layer or User Support Layer in the OSI model?
This question goes into the OSI model's Layered design, focusing on the higher categories, which include software-oriented functionalities for end-user interactions and application processing.
Here's a sample Answer:
The OSI model's software layers, often known as user support layers, are the Presentation Layer (Layer 6) and the Application Layer (Layer 7). The Presentation Layer conducts data translation, encryption, and compression to ensure system compatibility. The Application Layer delivers network services directly to end users and apps, allowing them to do operations like email, web browsing, and file transfer.
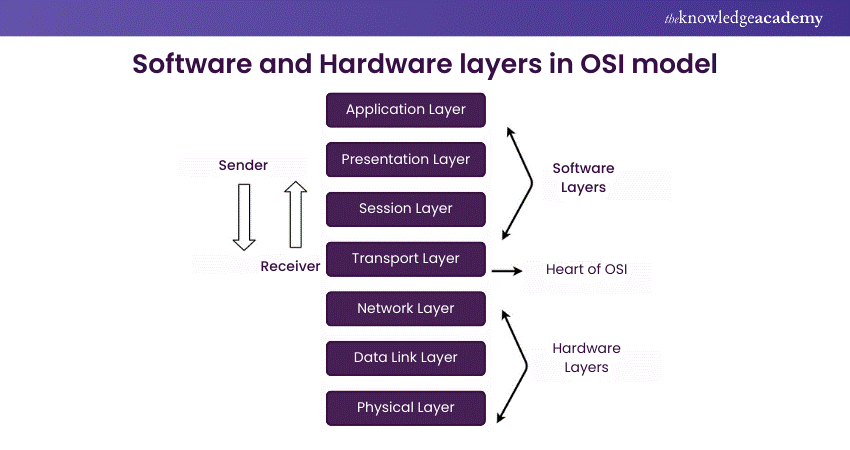
2) What are the hardware layers or network support layers in the OSI model?
This question tests the candidate's knowledge of the hardware-oriented layers that make up the lower layers of the OSI model and are responsible for data transmission, routing, and physical connectivity in networked systems.
Here's a sample answer:
The hardware layers, or network support layers, in the OSI model make the Physical Layer (Layer 1) and the Data Link Layer (Layer 2). The Physical Layer handles the actual transmission and reception of raw data over a physical medium, such as cables or wireless signals. The Data Link Layer handles the physical transmission link, ensuring error-free communication and addressing between devices on the same network segment.
3) In which OSI layer is the header and trailer added?
This question evaluates the candidates understand of the OSI model's Encapsulation process.
Here's a sample answer:
Headers and trailers are added to data packets at different layers of the OSI model. Typically, headers are added at the Network Layer (Layer 3), where logical addressing information, such as IP addresses, is encapsulated. Meanwhile, trailers are usually added at the Data Link Layer (Layer 2), where physical addressing, like MAC addresses, is appended.
4) Name two technologies by which you would connect two offices in remote locations.
This question targets the candidate's familiarity with remote connectivity technologies, which is essential for establishing interoffice communication and collaboration across geographically dispersed locations.
Here's a sample answer:
Two prominent technologies employed for connecting two offices in remote locations include:
a) Virtual Private Network (VPN): VPNs allow safe, encrypted communications between remote offices using public networks such as the internet.
b) Multiprotocol Label Switching (MPLS): MPLS technology connects remote offices in WANs, enabling scalable, reliable, and QoS-capable routing.
5) What are the different types of Networks?
This question targets the candidate's understanding of diverse Network Topologies and Architectures, encompassing various types of networks deployed across organisations and industries.
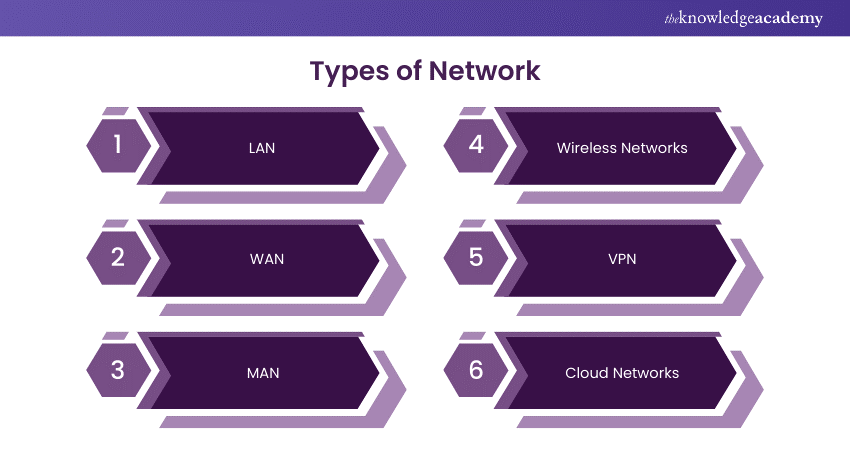
Here's a sample answer:
Prominent types of networks include the following:
a) Local Area Network (LAN): LANs represent localised network infrastructures confined to a limited geographic area, typically encompassing a single building or campus environment. LANs enable fast communication and resource sharing among devices, promoting collaboration and productivity within organisational premises due to low latency.
b) Wide Area Network (WAN): WANs span expansive geographic regions, interconnecting disparate LANs and remote locations via telecommunications or internet-based communication channels. WANs enable interoffice communication and global resource access through diverse network architectures, from leased lines to modern MPLS and VPNs.
c) Metropolitan Area Network (MAN): MANs bridge the gap between LANs and WANs, encompassing network infrastructures serving metropolitan or citywide regions. MANs enable efficient data transmission and resource sharing across urban areas, meeting diverse organisational and municipal needs with high-speed fibre optic links.
d) Wireless Networks: Wireless networks utilise radio frequency (RF) communication protocols to facilitate wireless connectivity and mobility within networked environments. WLANs offer flexible connectivity in limited areas, while cellular networks provide widespread coverage, enabling seamless connectivity and mobile service access.
e) Virtual Private Network (VPN): VPNs are encrypted channels over public networks, like the internet, allowing remote users to access organisational resources from anywhere. By leveraging VPN technologies, organisations can ensure data privacy, integrity, and confidentiality while facilitating seamless remote connectivity and collaboration.
f) Cloud Networks: Cloud networks encompass virtualised network infrastructures deployed within cloud computing environments, enabling on-demand resource provisioning, scalability, and accessibility. Using cloud Networking technologies like VPCs and SDN, organisations create resilient, elastic network architectures to adapt to changing business needs.
Elevate your Web Server skills with our NGINX Training today!
Advanced Networking Interview Questions
Explore advanced Networking Interview Questions through the following questions that will assess your advanced knowledge of Networking:
1) What is a Source Route?
Understanding source routes is fundamental in Networking as it involves specifying the path a packet should take through a network. In this question, the interviewer is likely to assess the candidate's understanding of Networking concepts related to routing.
Here's a sample answer:
A Source Route is a predefined path that specifies the sequence of intermediate network devices a data packet should follow to reach its destination. This path is determined by the sender and is included in the packet headers to guide its transmission through the network.
2) What is Symmetric and Asymmetric Encryption?
This question seeks to assess the candidate's understanding of Cryptographic techniques employed for securing data transmission and communication channels.
Here's a sample answer:
Symmetric Encryption entails the use of a single Cryptographic key for both Encryption and Decryption operations. Employing Symmetric Encryption algorithms like AES or DES, plaintext data is encrypted into ciphertext. This process requires a shared secret key securely distributed between communicating parties.
On the other hand, Asymmetric Encryption, or Public-key Cryptography, utilises a pair of mathematically related keys. A public key for Encryption and a private key for Decryption. This enables secure communication between parties without the need to share a secret key.
3) What is meant by Threat, Vulnerability, and Risk?
This question aims to assess the candidate's comprehension of fundamental concepts in Cybersecurity and Risk Management.
Here's a sample answer:
Threats: A Threat signifies potential harm that could compromise organisational assets, including confidentiality, integrity, or availability of information systems. Threats include the following:
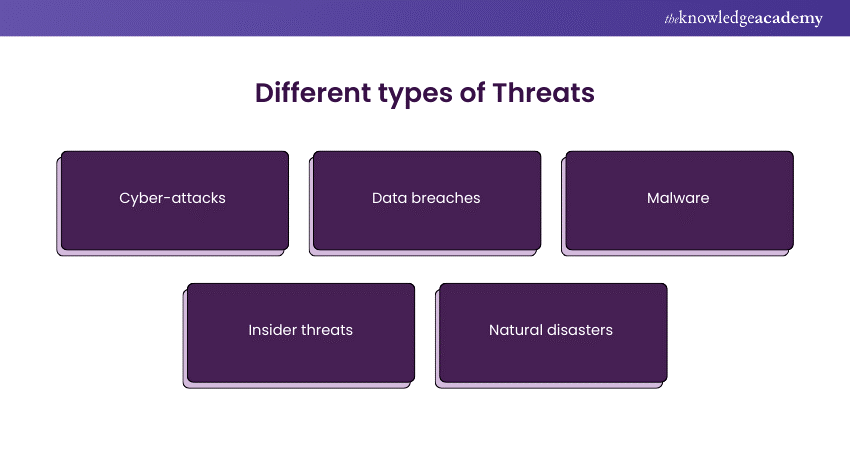
These can potentially pose harm or disruption to systems and networks.
Vulnerability: A vulnerability is a weakness in a system or process that could be exploited by threat actors to compromise security. Vulnerabilities encompass software vulnerabilities, hardware vulnerabilities, and human vulnerabilities, each posing distinct security risks to organisational assets.
Risk: Risk denotes the potential for harm, loss, or adverse impact resulting from the intersection of threats, vulnerabilities, and organisational assets. Risk embodies the likelihood and magnitude of potential security incidents occurring within an organisational context, as well as operational, reputational, and regulatory ramifications.
4) What are the different ways to exchange data?
This question aims to assess the candidate's understanding of data exchange mechanisms and protocols employed for transmitting information across networked systems and platforms.
Here's a sample answer:
Data exchange methods include the following:
a) Client-Server Communication: Client-server Communication entails the exchange of data between client devices and server systems hosting centralised resources, services, or applications. Client-server architectures utilise protocols like HTTP, HTTPS, FTP, and RPC for bi-directional data transmission, resource access, and service invocation between clients and servers.
b) Node-to-node Networking: Node-to-node Networking facilitates direct data exchange and communication between individual networked nodes without the need for centralised servers or intermediaries. P2P protocols like BitTorrent, Gnutella, and Direct Connect enable decentralised data sharing among peer nodes, fostering resilience and scalability.
c) Messaging Protocols: Messaging protocols encompass communication frameworks facilitating asynchronous data exchange and message transmission between distributed systems or applications. Messaging protocols like MQTT, AMQP, and JMS are tailored for specific paradigms such as publish-subscribe and point-to-point messaging.
d) File Transfer Mechanisms: File transfer mechanisms enable the exchange of files, documents, or multimedia content between networked devices or users. Common file transfer protocols include FTP, SFTP, SCP, and TFTP, each offering different levels of security, reliability, and performance.
e) Data Interchange Formats: Data interchange formats standardise the representation and encoding of structured data for transmission and interoperability across disparate systems and platforms. Data interchange formats like JSON, XML, CSV, and Protocol Buffers enable data exchange and serialisation within networked environments.
5) What is the difference between ‘standard' and ‘extended' Access Control List (ACL)?
This question aims to evaluate the candidate's understanding of Access Control mechanisms and Network Security policies. Specifically, it focuses on standard and extended access control lists (ACLs) used in network devices.
Here's a sample answer:
Standard ACLs filter traffic solely based on source IP addresses, often applied at network device interfaces like routers or firewalls for basic traffic control. However, their limited scope may inadvertently block legitimate traffic or expose networks to security risks.
Extended ACLs offer granular traffic filtering by considering various packet attributes like source/destination IPs, ports, and protocols. They enable precise security policies tailored to specific needs deployed at network ingress/egress points for enhanced traffic control, security enforcement, and protection of critical resources against threats.
6) Name the three means of user authentication.
Understanding different authentication mechanisms is crucial for ensuring secure access to systems and data. In this question, the interviewer aims to gauge the candidate's knowledge of Cybersecurity fundamentals, specifically related to user authentication methods.
Here's a sample answer:
The three primary means of user authentication are:
a) Password-based authentication: Passwords, commonly used for authentication, involve users providing a secret passphrase alongside a username for access. While simple, they face security risks like guessing, phishing, and reuse due to their susceptibility.
b) Multi-Factor Authentication (MFA): MFA demands users provide two or more authentication factors, like passwords, mobile phones, or biometric data, to verify identity. This method strengthens security by adding layers of verification beyond passwords, heightening the difficulty of unauthorized access attempts.
c) Public Key Infrastructure (PKI) authentication: PKI authentication relies on asymmetric Cryptography to authenticate users. Each user is issued a pair of cryptographic keys: a public key and a private key. The public key is shared openly, while the private key is kept secret.
Become a Cisco Certified Network Associate with CCNA Certification Training!
Conclusion
We hope that this blog helps you learn about some of the most common and important Networking Interview Questions. These questions will help you prepare for easy to hard challenges you may face while pursuing a career in Networking.
Master collaboration technologies with CCNP Collaboration Training!
Frequently Asked Questions
Upcoming IT Infrastructure & Networking Resources Batches & Dates
Date
 Introduction to Networking Training
Introduction to Networking Training
Fri 18th Oct 2024
Fri 29th Nov 2024
Fri 13th Dec 2024
Fri 7th Feb 2025
Fri 4th Apr 2025
Fri 6th Jun 2025
Fri 8th Aug 2025
Fri 3rd Oct 2025
Fri 5th Dec 2025







 Top Rated Course
Top Rated Course



 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


