We may not have the course you’re looking for. If you enquire or give us a call on +358 942454206 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.

Cyber-attacks are more sophisticated and frequent than ever in today’s digital age. Protecting digital assets is crucial for both organisations and individuals. Understanding the different Types of Ethical Hacking is important for staying one step ahead of cybercriminals.
Join us as we explore the fascinating Types of Ethical Hacking and their vital role in cyber security. Discover how these techniques can fortify your systems and networks against potential threats. By understanding and applying these methods, you’ll be better equipped to enhance your Cyber Security measures and outsmart potential attackers.
Table of Contents
1) What is Ethical Hacking?
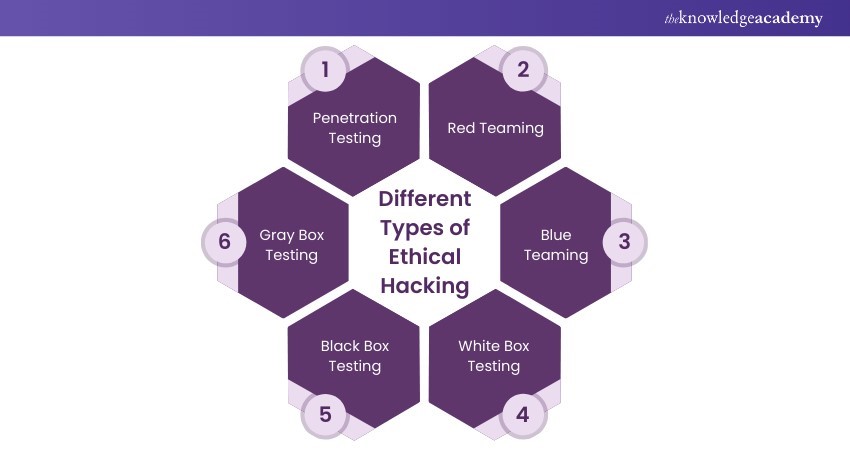
2) Different Types of Ethical Hacking
a) Penetration Testing
b) Red Teaming
c) Blue Teaming
d) White Box Testing
e) Black Box Testing
f) Gray Box Testing
g) Web Application Hacking
h) System Hacking
i) Web Server Hacking
3) Conclusion
What is Ethical Hacking?
Ethical Hacking involves legally and systematically breaking into computers and devices to evaluate and test an organisation's security measures. Unlike malicious hackers who exploit vulnerabilities for personal gain or harm, Ethical Hackers work with explicit permission from the organisation. Their primary goal is to identify and address security weaknesses before they can be exploited by cybercriminals.
Ethical Hackers use a range of tools and techniques similar to those employed by malicious hackers, including penetration testing, vulnerability scanning, and social engineering. However, their approach is guided by a code of conduct and a commitment to enhancing the organisation’s security posture. This proactive approach helps organisations safeguard sensitive information, ensure compliance with industry standards, and maintain trust with clients and stakeholders.
Key Concepts of Ethical Hacking
The three main concepts of Ethical Hacking are:
a) Scanning: Scanning is about finding out what devices are on a network and how they are set up. This helps to identify weak points that can be targeted in a hacking attempt. Tools like port scanners and network mappers are often used.
b) Enumeration: Enumeration involves collecting detailed information about the network, such as usernames and passwords. This information is used to plan further hacking steps. It includes techniques like checking network services and looking at system directories.
c) Exploitation: Exploitation is the stage where the Hacker uses the identified weak points to gain access to sensitive information or control over a device. This can involve methods like injecting harmful code or exploiting software bugs. The goal is to show how these security issues can be fixed.
Gain the skills to safeguard sensitive information with our Cyber Security Awareness Courses – join today!
Different Types of Ethical Hacking
Different Types of Ethical Hacking include various approaches and techniques to identify security weaknesses in digital systems. Some of them are mentioned below:
Penetration Testing
Penetration Testing, often called Pen Testing, is an approach to examine the security of an IT infrastructure by safely exploiting weakness. These may exist in operating systems, services, applications, and configurations. Pen Testers use tools and techniques to find weak points and attempt to breach the system.
Advantages of Penetration Testing:
a) Identifies vulnerabilities:
Penetration Testing helps discover and fix security weaknesses before Hackers can exploit them. By simulating real-world attacks, Pen Testers can find and report vulnerabilities that might not be detected through automated tools alone.
b) Improves security posture
The testing helps organisations understand their security strengths and weaknesses by providing insights into the effectiveness of current security measures. This information is important for improving overall security posture and ensuring robust defences.
c) Compliance
The testing assists organisations in meeting regulatory and industry standards for security. Many regulations, such as PCI DSS, HIPAA, and GDPR, require regular security assessments, including Penetration Testing, to ensure compliance.
d) Real-world testing
The testing simulates actual attacks, objectively assessing the system's defences. This helps organisations understand how their systems would perform under real attack conditions and prepare accordingly.
Red Teaming
Red Teaming is an advanced procedure where Ethical Hackers attempt to attack a system, simulating the actions of an adversary to expose vulnerabilities that security systems might overlook. The goal is to recommend improvements based on these findings.
Advantages of Red Teaming:
a) Realistic attack scenarios:
Red Teaming simulates real and highly skilled threats to assess the organisation’s readiness to handle them. This approach assists in finding flaws in the system that might not be obtained during usual testing.
b) Enhances incident response:
Red Team improves the organisation's ability to detect and respond to real attacks. Organisations can refine their processes and improve their response times by testing the effectiveness of incident response procedures
c) Continuous improvement:
The insights gained from the Red Team help constantly refine and strengthen security measures. This process ensures the organisation knows the emerging threats and maintains a strong security posture.
Blue Teaming
Blue Teaming is the defensive aspect of Cyber Security. The Blue Team is responsible for safeguarding the organisation's assets by monitoring systems, detecting attacks, and responding to incidents. Their primary objective is to ensure information systems' integrity, confidentiality, and availability
Advantages of Blue Teaming:
a) Proactive defence:
Blue Teaming emphasises preventing attacks and minimising damage. By implementing proactive defence measures, organisations can reduce the likelihood of successful attacks and limit their impact.
b) Improved detection:
Blue Teams enhance the organisation's ability to monitor, detect, and respond to security incidents. This includes using tools like SIEM (Security Information and Event Management) to analyse security events and identify potential threats.
c) Threat mitigation:
Blue Teams help identify and mitigate potential threats before they cause harm. Organisations can reduce risk exposure by regularly scanning for vulnerabilities and addressing them promptly.
White Box Testing
White Box Testing, also called Clear-Box or Glass-Box Testing, involves testing with full knowledge of the system's interior or internal structure. This type of testing is very comprehensive in assessing the code, security, and internal panto to determine areas with security vulnerabilities.
Advantages of White Box Testing:
a) In-depth analysis:
White Box Testing examines the system at its most detailed levels, thus pointing out all the possible internal flaws in its functioning. The testers can review and assess the feasibility of the code, architecture, and internal processes to reveal the security issues.
b) Early detection:
This testing enables one to detect security flaws early, reducing costs in the future. Thus, by detecting the existing problems at the initial phase, organisations can eliminate them before they become significant threats.
c) Detailed feedback:
The testing provides details about where and how risks are likely to occur to help in proper remedial measures. This detailed feedback enables the developers to know and address the underlying causes of security issues.
Black Box Testing
Black Box Testing involves testing without prior knowledge of the system. Testers interact with the system externally, like an end-user or an outsider. This approach helps identify vulnerabilities that external attackers could exploit.
Advantages of Black Box Testing:
a) External perspective:
Black Box Testing mimics the approach of an external attacker, identifying vulnerabilities visible from the outside. This approach helps organisations understand how their systems appear to potential attackers.
b) Unbiased testing:
Testers are not influenced by knowledge of the system's design, leading to objective results. This unbiased perspective ensures that vulnerabilities are identified based on their actual impact.
c) User experience focus:
Black Box Testing evaluates the system from an end-user’s perspective, enhancing usability alongside security. By considering the user experience, organisations can improve both security and functionality.
Gray Box Testing
Gray Box Testing is a hybrid approach combining White Box and Black Box Testing. These testers have partial knowledge of the system, allowing them to focus on specific areas while maintaining an external perspective. This method balances the thoroughness of white box testing with the realism of Black Box Testing.
Advantages of Gray Box Testing:
a) Balanced approach:
Gray Box Testing combines the thoroughness of White Box Testing with the realism of Black Box Testing. This balanced approach ensures comprehensive security assessments.
b) Targeted testing:
This testing allows testers to focus on known vulnerable areas while maintaining an external attacker’s perspective. This targeted approach helps identify and address specific security issues.
c) Efficient resource use:
Gray Box Testing leverages partial knowledge to streamline testing efforts, saving time and resources. By focusing on critical areas, organisations can optimise their security assessments.
d) Comprehensive insights:
This testing provides a well-rounded understanding of the system's security, identifying both internal and external vulnerabilities. This comprehensive insight helps organisations improve their overall security posture.
Web Application Hacking
Web Application Hacking is the exploitation of vulnerabilities in web applications. Web apps can be created in various languages, including PHP and Ruby on Rails, but they are usually written in HTML, CSS, and JavaScript. Due to the structure of these languages and how web browsers perceive them, certain operations on a website can be carried out without the proper authorisation.
Advantages of Web Application Hacking:
a) Strengthened Security:
By using Ethical Hacking to find and address web application vulnerabilities, businesses may better preserve sensitive user information and prevent cyber-attacks.
b) Conformity with Industry Standards:
Businesses can fulfill regulatory obligations like GDPR, PCI DSS, and ISO 27001, which frequently call for strict security measures, by regularly conducting web application penetration testing.
c) Proactive Threat Mitigation:
The danger of data breaches and service interruptions decreases when organisations use web application Hacking to identify and resolve vulnerabilities before malevolent actors exploit them.
d) Better Reputation and Trust:
Securing online apps shows a dedication to maintaining a brand's reputation and winning over customers' trust, which improves user retention and leads to business expansion.
System Hacking
System Hacking involves exploiting computer software to access target machines and obtain confidential information. The aim is to exploit vulnerabilities, conceal files, and gain elevated privileges.
Advantages of System Hacking:
a) Finding Security Vulnerabilities:
By using Ethical Hacking to expose system flaws, organisations may fix vulnerabilities before hackers can exploit them.
b) Enhancing Access Control:
System Hacking checks access controls and helps strengthen security against unwanted access by exposing vulnerabilities in authentication and authorisation processes.
c) Improving Incident Response:
By imitating attacks, system Hacking enhances an organisation's capacity to react to threats, minimising damage and speeding up recovery.
d) Optimising Security Policies:
Ethical System Hacking provides valuable insights that help improve security policies and procedures, keeping them up to date with emerging cyber threats and industry norms.
Web Server Hacking
Web Server Hacking refers to stealing private data, passwords, and other confidential information by using DoS attacks, SYN floods, snipping, and port scans. Hackers attack the web server to execute extortion, blackmail, sabotage, or attain financial gains.
Advantages of Web Server Hacking:
a) Identifying Configuration Flaws:
Ethical Web Server Hacking assists in identifying server weaknesses and configuration flaws, allowing organisations to prevent potential server attacks.
b) Protecting Sensitive Data:
Ethical Hackers protect sensitive data by identifying vulnerabilities in the data transfer and storage process.
c) Preventing Downtime and Service Disruption:
By identifying and preventing potential threats, web server hackers reduce the threat of server downtime and service interruptions caused by cyber-attacks.
d) Enhancing Server Security:
Web server hacking provides insights into strengthening security protocols and improving defences against attacks such as DDoS, server-side injection, and unauthorised access.
Accelerate your security professional career with our Mastering Metasploit Framework Course. Join now!
Conclusion
Learning the different Types of Ethical Hacking approaches is essential in strengthening Cyber Security. It provides insights into the motivations, methodologies, and roles involved in protecting digital systems. Hacking practices guided by ethics and principles also offer promising career opportunities, keeping prospective Hackers ahead of emerging threats and safeguarding our digital world.
Acquire practical skills to combat cyber threats with our Ethical Hacking Professional Course – join today!
Frequently Asked Questions

Careers in Ethical Hacking include roles such as Penetration Tester, Security Analyst, Vulnerability Assessor, Red Team Specialist, and Security Consultant. These professionals work to identify and fix security vulnerabilities, protect against cyber threats, and ensure compliance with security standards.

The seven types of Hackers include:
1) White Hat Hackers
2) Black Hat Hackers
3) Grey Hat Hackers
4) Script Kiddies
5) Hacktivists
6) State-Sponsored Hackers
7) Blue Hat Hackers

The Knowledge Academy takes global learning to new heights, offering over 30,000 online courses across 490+ locations in 220 countries. This expansive reach ensures accessibility and convenience for learners worldwide.
Alongside our diverse Online Course Catalogue, encompassing 19 major categories, we go the extra mile by providing a plethora of free educational Online Resources like News updates, Blogs, videos, webinars, and interview questions. Tailoring learning experiences further, professionals can maximise value with customisable Course Bundles of TKA.

The Knowledge Academy’s Knowledge Pass, a prepaid voucher, adds another layer of flexibility, allowing course bookings over a 12-month period. Join us on a journey where education knows no bounds.

The Knowledge Academy offers various Ethical Hacking Courses, including the Ethical Hacking Professional Course and Mastering Metasploit Framework Course. These courses cater to different skill levels, providing comprehensive insights into Information Security Risk Management.
Our IT Security & Data Protection Blogs cover a range of topics related to Cyber Security, offering valuable resources, best practices, and industry insights. Whether you are a beginner or looking to advance your Cyber Security skills, The Knowledge Academy's diverse courses and informative blogs have got you covered.
Upcoming IT Security & Data Protection Resources Batches & Dates
Date
 Certified Cyber Security Professional (CCS-PRO)
Certified Cyber Security Professional (CCS-PRO)
Fri 21st Mar 2025
Fri 23rd May 2025
Fri 22nd Aug 2025
Fri 5th Dec 2025







 Top Rated Course
Top Rated Course



 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


