We may not have the course you’re looking for. If you enquire or give us a call on +08000201623 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.

Picture this: You’re the curator of a grand digital library—the Database Management System (DBMS). Your shelves are filled with tables, each holding precious data. But how do you ensure that the information within stays pristine, like a well-kept secret? Enter the unsung heroes: Integrity Constraints in DBMS! These guardians don’t wear capes, but they’re the reason your data remains reliable and accurate. They enforce rules, like stern librarians, ensuring that relationships between tables stay harmonious.
This blog explores the core concept of Integrity Constraints in DBMS, explores their benefits, and peeks into their different types. So, grab your magnifying glass (or SQL query) and let’s dive into the world of data guardianship!
Table of Contents
1) What are Integrity Constraints in DBMS?
2) Why are Integrity Constraints Important in DBMS?
3) Types of Integrity Constraints in DBMS
4) Benefits of Integrity Constraints in DBMS
5) Conclusion
What are Integrity Constraints in DBMS?
Integrity Constraints are rules designed to ensure the accuracy and consistency of data within a database. They enforce business rules and verify correct Data Entry. For instance, a basic constraint might require that all customers have a valid email address, preventing invalid entries.
Additionally, constraints can enforce relationships between tables, such as limiting each customer to a single shipping address. By implementing these constraints in SQL, data inconsistencies and errors are minimised, streamlining Data Management and querying.
Why are Integrity Constraints Important in DBMS?
Integrity Constraints are essential for several reasons:
1) They help to ensure data accuracy by preventing invalid data from being entered into the database.
2) They help maintain data consistency by ensuring it is consistent across different tables and fields.
3) They help to prevent unauthorised access to data by ensuring that only authorised users can access specific data.
Gain expertise on mainframe and network applications through our Teradata Courses - Sign up now!
Types of Integrity Constraints in DBMS
Integrity Constraints in DBMS ensure that data is consistent and accurate. There are four main types of Integrity Constraints: domain, entity, referential, and key. Here, we'll take a closer look at these Integrity Constraint types.
Domain Constraint
In a Database Management System (DBMS), a Domain Constraint specifies the permissible values for a given attribute in a database table. It ensures that the data entered into a column falls within a defined range or set of values, thus maintaining data integrity.
The following example will illustrate how this constraint functions:
Consider a database table for employee information, where the "Age" column should only accept values between 18 and 66. This constraint ensures that no invalid ages are entered into the database.
Here’s a simple table illustrating this constraint:
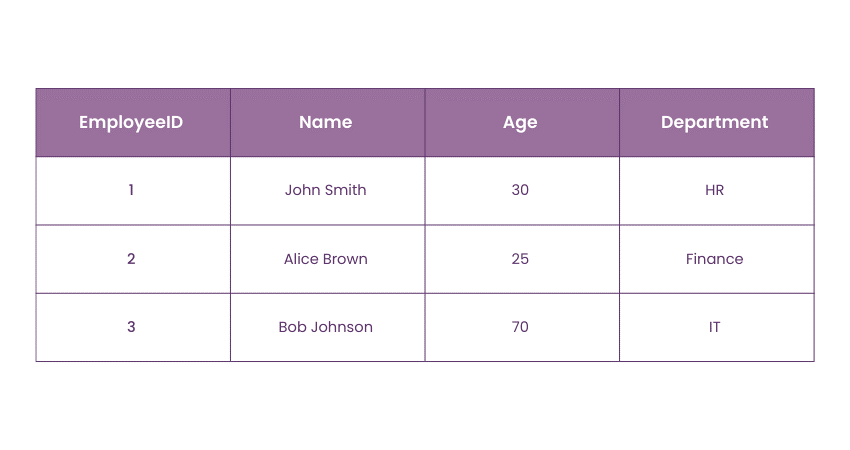
In this example, the Domain Constraint for the "Age" column specifies that ages must be between 18 and 66. The entry for Bob Johnson with an age of 70 violates this constraint and would not be allowed in the database.
Entity Integrity Constraint
The Entity Integrity Constraint ensures that each row in a table can be uniquely identified by a primary key. It mandates that the primary key of a table must be unique and cannot contain NULL values.
The key points of Entity Integrity Constraint are:
a) Uniqueness: Each value in the primary key column(s) must be unique across all rows.
b) Non-null: The primary key column(s) cannot have NULL values, as NULL does not represent a unique value.
As an example, consider a table Students where StudentID is defined as the primary key.
Students Table:
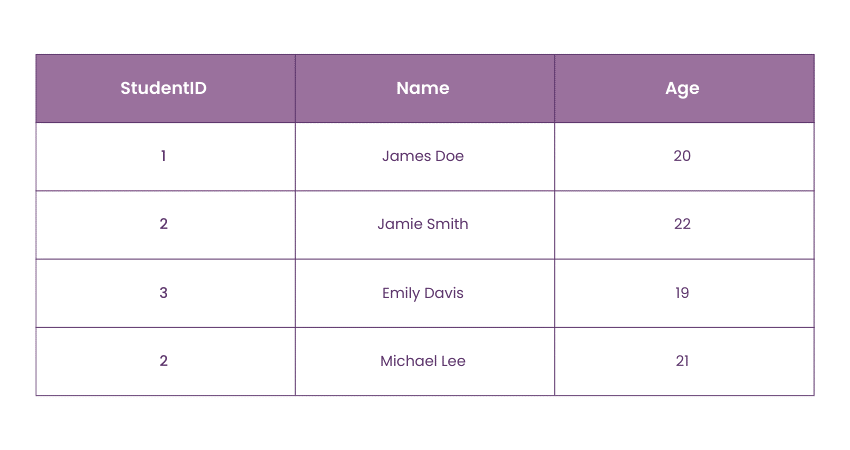
In this table:
1) Primary Key: StudentID
2) Constraint Violations:
a) The StudentID of 2 appears twice, violating the uniqueness requirement.
b)There are no NULL values in StudentID, so the non-null requirement is met.
The Entity Integrity Constraint ensures that each StudentID is unique across the table, and no record can have a NULL StudentID. The second occurrence of StudentID 2 in the table demonstrates a violation of the Entity Integrity Constraint.
Referential Integrity Constraint
The Referential Integrity Constraint ensures that relationships between tables remain consistent. Specifically, it requires that a foreign key in one table must either match an existing primary key in another table or be NULL if allowed. This constraint maintains the accuracy and consistency of data across related tables.
Here are some key Points of Referential Integrity Constraint to remember:
a) Foreign Key: A column (or set of columns) in one table that refers to the primary key in another table.
b) Consistency: Every value in the foreign key column must match a value in the referenced primary key column or be NULL.
c) Cascading Actions: Referential integrity can include rules for actions like updating or deleting rows, such as cascading changes to maintain consistency.
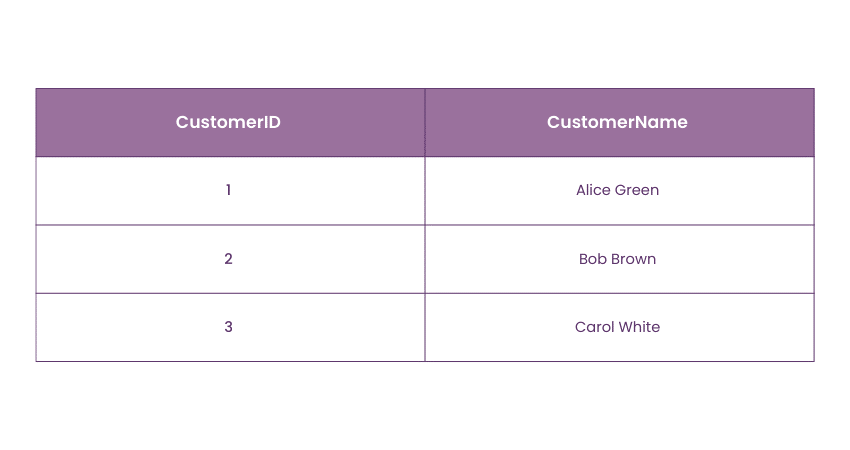
As example, consider two tables: Orders and Customers. You want to ensure that every CustomerID in the Orders table corresponds to a valid CustomerID in the Customers table.
Customers Table:
Orders Table:
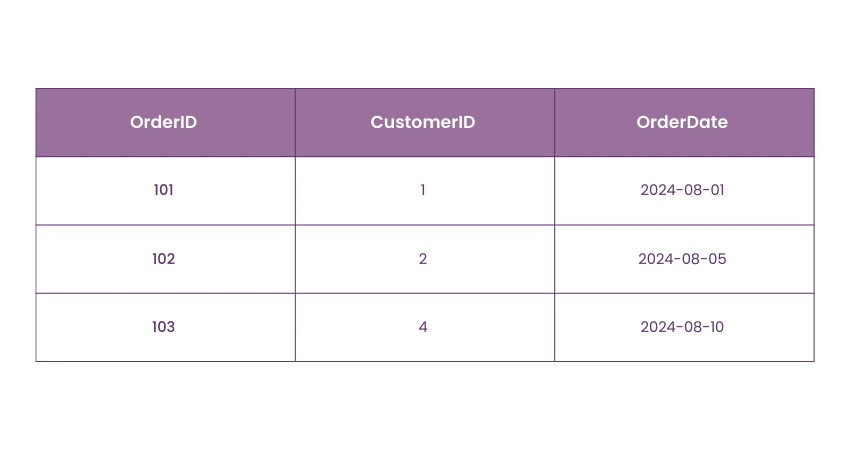
In this example:
1) CustomerID in the Orders table is the foreign key.
2) CustomerID in the Customers table is the primary key.
3) Constraint Violations: The CustomerID of 4 in the Orders table does not exist in the Customers table, violating the Referential Integrity Constraint.
This constraint ensures that every CustomerID in the Orders table must exist in the Customers table, which maintains consistency across related tables.
Key Constraint
A Key Constraint is a rule that ensures the uniqueness of data within a table. It can involve various types of keys, each serving to uniquely identify rows and maintain data integrity. There are three types of Key Constraints as listed below:
a) Primary Key Constraint: This ensures that each row in a table is uniquely identified by a primary key column or a set of columns. The primary key must be unique and cannot contain NULL values.
b) Unique Key Constraint: This ensures that all values in a column or a combination of columns are unique across the table, but unlike a primary key, it allows NULL values (depending on the DBMS).
c) Foreign Key Constraint: This type ensures referential integrity between two tables by enforcing that a foreign key column matches a primary key in another table.
Let’s consider a table Products where ProductID is defined as the primary key and ProductName must be unique but can have NULL values.
Products Table:
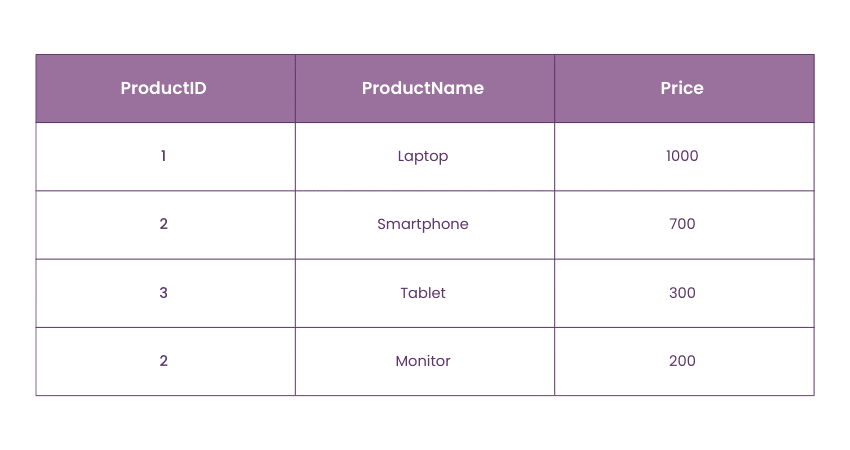
In this table:
a) Primary Key Constraint: ProductID must be unique and non-null for each row. The entry with ProductID 2 appears twice, violating the primary Key Constraint.
b) Unique Key Constraint: If ProductName was required to be unique, then no two rows could have the same ProductName. In this case, the ProductName constraint is not violated, but if applied, it would prevent multiple entries with the same name.
The Key Constraint ensures that the ProductID is unique across the table, while unique Key Constraints enforce the uniqueness of data in specific columns, depending on the requirements.
Expand your knowledge and expertise on database approaches and DBMS with our Relational Databases & Data Modelling Training - Sign up now!
Benefits of Integrity Constraints in DBMS
Integrity Constraints offer significant benefits in the field of Database Management. Let’s take a closer look at some of them
1) Simplicity of Declaration
One benefit of Integrity Constraints is that they can be declared easily. Integrity Constraints are written in a declarative language, meaning they can be specified without writing code. This makes it convenient for even non-technical users to understand and specify rules.
2) Centralised Rule Management
Another advantage of Integrity Constraints is they provide a centralised way to specify rules. Therefore, rules must only be specified once, which can be enforced across the entire database. This is much more efficient than specifying rules individually for each application or user.
3) Flexibility in Data Loading
Integrity Constraints offer flexibility when loading data into the database. When data is loaded, the Integrity Constraints are checked automatically. In other words, if there are any problems with the data, they can be immediately detected and corrected.
4) Enhanced Application Development Efficiency
Integrity Constraints can also help maximise application development productivity. Developers do not have to write code to enforce rules; they can just specify them using an Integrity Constraint language. This saves time and effort during development and makes creating consistent and reliable applications easier.
5) Instant User Feedback
When users attempt to violate a rule, using Integrity Constraints in DBMS can provide immediate feedback. For example, if a user tries to insert an invalid value, the database will reject the attempted insertion and return an error message to the user instead. This indicates to the user that their input is incorrect and must be corrected.
Conclusion
Integrity Constraints play a crucial role—the silent conductors ensure harmony in the Database. As we bid adieu to this exploration, remember that these guardians keep our data virtuous, relationships intact, and queries singing sweetly. So, whether you’re crafting SQL statements or pondering data integrity, tip your hat to these unsung heroes.
Looking to secure a strong foundation for your Database Management career? Sign up for our Introduction To Database Training now!
Frequently Asked Questions

A Foreign Key Constraint in a Database Management System maintains the referential integrity between two tables.

A Unique Constraint ensures that all values in a column (or a set of columns) are unique across the table. It prevents duplicate values in a column. A foreign key establishes a relationship between two tables by linking a column (or a set of columns) in one table to the primary key or a unique key in another table.

The Knowledge Academy takes global learning to new heights, offering over 30,000 online courses across 490+ locations in 220 countries. This expansive reach ensures accessibility and convenience for learners worldwide.
Alongside our diverse Online Course Catalogue, encompassing 19 major categories, we go the extra mile by providing a plethora of free educational Online Resources like News updates, Blogs, videos, webinars, and interview questions. Tailoring learning experiences further, professionals can maximise value with customisable Course Bundles of TKA

The Knowledge Academy’s Knowledge Pass, a prepaid voucher, adds another layer of flexibility, allowing course bookings over a 12-month period. Join us on a journey where education knows no bounds.

The Knowledge Academy offers various Database Courses, including the InfluxDB Course and the Introduction to Database Course. These courses cater to different skill levels, providing comprehensive insights into What is DBMS.
Our Programming & DevOps Blogs cover a range of topics related to DBMS, offering valuable resources, best practices, and industry insights. Whether you are a beginner or looking to advance your DBMS skills, The Knowledge Academy's diverse courses and informative blogs have got you covered.
Upcoming Programming & DevOps Resources Batches & Dates
Date
 Introduction to Database Training
Introduction to Database Training
Fri 10th Jan 2025
Fri 14th Feb 2025
Fri 11th Apr 2025
Fri 23rd May 2025
Fri 8th Aug 2025
Fri 26th Sep 2025
Fri 21st Nov 2025







 Top Rated Course
Top Rated Course



 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


