We may not have the course you’re looking for. If you enquire or give us a call on +44 1344 203 999 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.

Imagine navigating a vast ocean as the captain of a modern vessel, where the safety of everyone onboard hinges on your vigilance and strategic foresight. Similarly, a Chief Information Security Officer (CISO) commands the Cybersecurity ship, steering through treacherous waters of cyber threats and regulatory changes. This blog delves into the Chief Information Security Officer Interview Questions that test a candidate's readiness to safeguard an organisation’s precious data and lead with strategic insight.
Whether you're aspiring to become a CISO or aiming to fortify your organisation’s Cybersecurity framework, mastering these Chief Information Security Officer Interview Questions is crucial. Here, we provide insights and detailed answers to prepare you to articulate your vision and demonstrate your capability in this high-stakes role.
Table of Contents
1) Commonly asked Chief Information Security Officer Interview Questions
2) Chief Information Security Officer Interview Questions for beginners
3) Chief Information Security Officer Interview Questions for intermediates
4) Advanced Chief Information Security Officer Interview Questions
5) Conclusion
Commonly asked Chief Information Security Officer Interview Questions
The interview panel expects the candidates to demonstrate an excellent grasp of both Cybersecurity fundamentals and operational ethics while tackling the challenging CISO position. To gain insights into applicants’ suitability for this pivotal role, interviewers envisage interrogating them with inquisitive questions covering a wide range of subjects.
This enquiry deals with Cybersecurity management issues such as risk assessment, incident response plans, respective compliance, and personnel management. Additionally, interviewers may inquire about candidates' Leadership Styles, decision-making processes, and approaches to addressing security incidents.
Chief Information Security Officer Interview Questions for beginners
These questions focus on foundational knowledge and practical experience in Cybersecurity. They assess candidates' understanding of basic concepts such as SSL, cloud security risks, and incident response procedures. Let's talk about some of them in detail:
1) What does SSL stand for?
Interviewers like to understand candidates' foundational knowledge about basic CISO requirements through this question. So, their response must have a great beginning, a riveting middle, and an end that highlights their extensive knowledge.
Sample answer: As a cryptographic protocol, Secure Sockets Layer (SSL) securely establishes an encrypted connection, ensuring end-to-end privacy. It is often employed as the means of transmitting data from a web browser to a web server. It also ensures confidential data remains encrypted and, thus, remains indecipherable by unauthorised access.
2) Over which port do you perform pinging?
Interviewers often seek candidates with a strong grasp of network fundamentals. Thus, their response must comprise comprehensive knowledge of common networking protocols.
Sample answer: Pinging is performed over port Internet Control Message Protocol (ICMP). As a network diagnostic utility, Pinging tests the host's reachability on an Internet Protocol (IP) network. By default, the ping command sends ICMP echo request packets to the target host, and the target host responds with ICMP echo replies to packets.
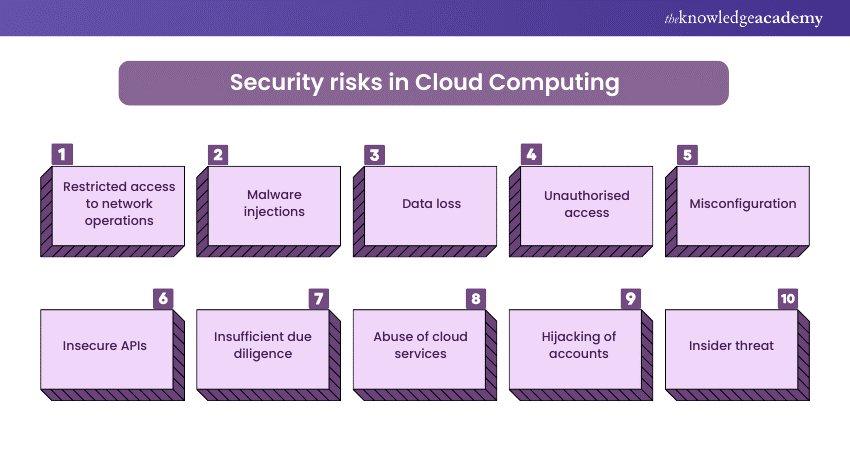
3) Does Cloud Computing pose security risks?
This question delves into the candidate's awareness of Cybersecurity Challenges in modern computing environments.
Sample answer: Yes, Cloud Computing can pose security risks if things are not implemented and managed in the right way. Although Cloud Computing offers numerous benefits, some characteristic security issues, such as data privacy and compliance and shared responsibility, are associated with this. Organisations must implement strict security controls like authentication, confidentiality, integrity, and non-repudiation to avoid such risks.
4) Have you participated in an audit before, and if so, how did it unfold?
Interviewers are interested in candidates' experiences with audit processes, as they provide insights into the candidate's understanding of compliance requirements.
Sample answer: “Yes, I have participated in audits before, both as an auditee and as an Auditor. As an Auditor, the audit process typically involves:
a) Preparing documentation, policies, and procedures related to the audited area.
b) Facilitate information requests, interviews, and observations by collaborating with internal and external auditors.
c) Addressing audit findings, remediation plans, and corrective actions to improve compliance and operational effectiveness.
In the context of auditing, I have performed audits in line with the methods, standards and guidelines of auditing the sufficiency and effectiveness of controls, processes and systems. My assessment consisted of interviews, reviews of documents, evaluation of the management mistakes, security issues and areas for improvement.”
Seize the chance to lead in the world of Cybersecurity with our CISSP-ISSAP Training – join us now and elevate your expertise!
5) Can you effectively communicate technical matters to the board during meetings?
Effective communication is a crucial skill for Cybersecurity professionals. Thus, candidates should emphasise their ability to translate complex technical information into clear, accessible language.
Sample answer: “Yes, I can use my clear and concise Communication Skills to provide the necessary technical details to the board. I use a simple and brief tone so that the non-technical shareholders can easily and fully assimilate it. Moreover, I adapt both my communication style and my content to match up to what the board understands, values and technical calibre.”
6) How do you ensure the timely installation of software updates and patches?
This question assesses the candidate's approach to maintaining the security of organisational systems.
Sample answer: “To ensure timely installation of software updates and patches, I implement a structured patch management process that includes the following steps:
a) Regular vulnerability scanning and risk assessment to identify security vulnerabilities and prioritise patching based on severity, exploitability, and potential impact.
b) Establishing patching policies, procedures, and schedules to define roles, responsibilities, and timelines for patch deployment, testing, and validation.
c) Automating patch deployment and distribution using centralised patch management tools and systems to streamline the patching process, minimise downtime, and ensure consistency across the organisation.
d) Conducting thorough testing and validation of patches in a controlled environment to assess compatibility, stability, and functionality before deployment to production systems.
e) Monitoring patch deployment status, compliance, and effectiveness through reporting, logging, and performance metrics.”
7) How do you manage requests from employees wishing to utilise personal devices for work?
This question explores the candidate's approach to balancing employee productivity and organisational security in a Bring Your Own Device (BYOD) environment.
Sample answer: “When managing requests from employees wishing to utilise personal devices for work, I follow a risk-based approach. To do this, I check that security requirements are balanced with employee productivity and satisfaction. My approach includes:
a) Assessing the security risks associated with personal devices, such as smartphones, tablets, and laptops.
b) BYOD policies, guidelines, and security controls to govern the use of personal devices for work.
c) Providing security awareness training and user education to employees on the risks and responsibilities associated with using personal devices for work.
d) Implementing Mobile Device Management (MDM) solutions and endpoint security tools to enforce security policies.
e) Regularly reviewing and updating BYOD policies and security controls to adapt to evolving threats, technologies, and regulatory requirements.”
8) What is your initial inquiry when confronted with a breach?
This question evaluates the candidate's response to Cybersecurity incidents and their ability to initiate an effective incident response process.
Sample answer: “My initial inquiry when confronted with a breach is to assess the scope and severity of the incident. This involves gathering essential information, such as:
a) The nature and extent of the breach, including the systems, applications, and data affected.
b) The potential impact on business operations, customers, partners, and other stakeholders.
c) The root cause of the breach, whether it was due to a technical vulnerability, human error, or malicious activity.
d) The immediate actions needed to contain the breach, mitigate further damage, and preserve evidence for forensic analysis and investigation.
By gathering this information promptly, I can determine the appropriate response strategy, mobilise resources, and communicate effectively with stakeholders. This also helps me address the breach effectively and minimise its impact on the organisation.”
9) How does compliance influence your decision-making process?
This question examines the candidate's understanding of the relationship between Cybersecurity and regulatory compliance.
Sample answer: Compliance influences my Decision-making Process since it aids in assessing and managing risks related to regulatory requirements and internal policies. Compliance considerations impact decision-making in the following ways:
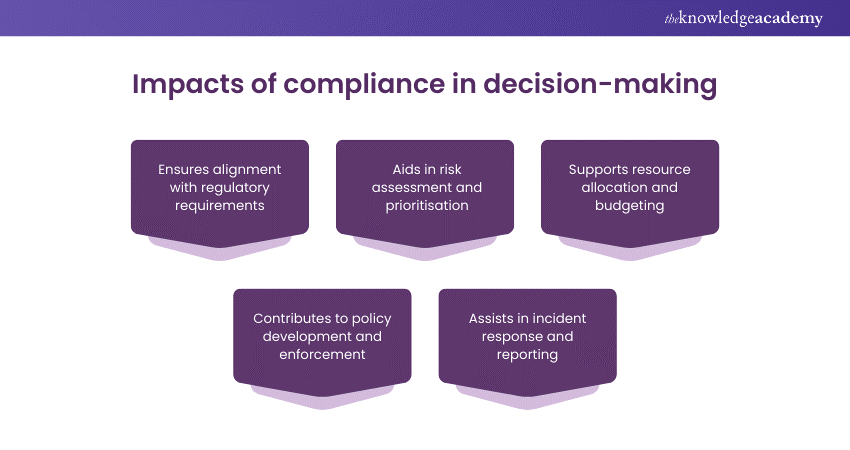
a) Alignment with regulatory requirements: I ensure that security initiatives and investments align with applicable laws, regulations, and industry standards. This also aids in mitigating legal and financial risks, avoiding penalties, and maintaining compliance.
b) Risk assessment and prioritisation: I prioritise security initiatives based on their alignment with compliance obligations. Along with this, I focus on the severity of associated risks and the potential impact on business operations, reputation, and stakeholders.
c) Resource allocation and budgeting: I allocate resources and budgetary allocations to address compliance requirements. This also helps to balance competing priorities and constraints.
d) Policy development and enforcement: I develop and enforce security policies, procedures, and controls that meet regulatory requirements and industry best practices. This also ensures that employees understand their obligations and adhere to compliance guidelines.
e) Incident response and reporting: I integrate compliance considerations into incident response planning and breach notification procedures. It also aids in timely and accurate communication with regulatory authorities, affected individuals, and other stakeholders.
Gain the knowledge to excel in today's digital landscape –sign up for our CISSP Training!
Chief Information Security Officer Interview Questions for intermediates
Intermediate-level questions delve deeper into candidates' expertise in implementing Multi-Factor Authentication and safeguarding mobile devices. Let's explore some of those questions and ways to answer them:
10) What lessons have you gleaned from your tenure as Chief Information Security Officer?
This question probes into the candidate's insights gained while serving as a CISO. It aims to understand their reflections on challenges faced and strategies employed.
Sample answer: “In my CISO role, I've learned the critical importance of proactive risk management in addressing dynamic cyber threats effectively. Additionally, keeping up with emerging technologies and industry trends has become imperative to anticipate and adapt to evolving cyber threats. These lessons underscore the necessity for a proactive approach to Cybersecurity governance, encompassing risk management, communication, collaboration, and continuous learning.”
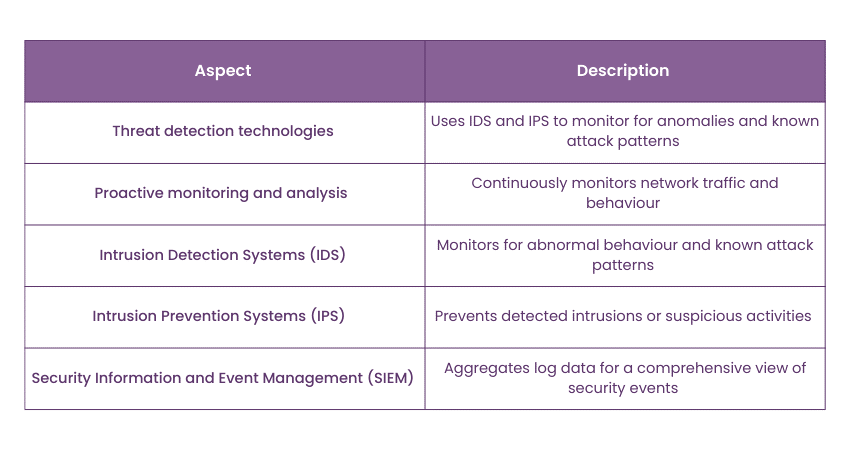
11) What methodologies do you employ to detect suspicious activity within the network?
This question delves into the candidate's approach to detecting potential security threats within the organisation's network infrastructure.
Sample answer: “In detecting suspicious activity within the network, I employ a multifaceted approach that combines advanced threat detection technologies with proactive monitoring and analysis. This includes leveraging Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) to monitor network traffic for anomalous behaviour and known attack patterns. Additionally, I utilise Security Information and Event Management (SIEM) solutions to aggregate and correlate log data from various sources.”
12) How do you go about implementing Multi-Factor Authentication for employees?
This question seeks insight into the candidate's approach to implementing Multi-Factor Authentication (MFA) and enhancing authentication security within the organisation.
Sample answer: “Implementing Multi-Factor Authentication (MFA) involves several key steps. First, I assess the organisation's authentication requirements and identify systems and applications that require MFA. Next, I select MFA solutions based on security features, user experience, scalability, and integration capabilities.
Then, I configure and deploy the chosen MFA solution, providing comprehensive user education and training to ensure effective usage. Finally, I continuously monitor MFA usage, conduct regular audits, and update configurations as needed to address emerging threats and vulnerabilities.”
13) What procedures do you follow to safeguard the security of mobile devices used by employees?
This question aims to understand the candidate's procedures for handling the security of mobile devices used by employees within the organisation.
Sample answer: “Providing security for personal cell phones must be done through means that enable the preservation of private information and data. MDM plays a significant role in policy setup, policy management, and device management. By means of data-at-rest encryption and data-in-transit encryption, I aim to meet the goals of the required security level and regularly review systems.”
14) What tactics do you employ to fortify defences against phishing attacks?
This question explores the candidate's strategies for strengthening defences against phishing attacks and common Cybersecurity threats.
Sample answer: “To fortify defences against phishing attacks, I employ several tactics. These measures may involve yearly phishing training for the employee on stronger filtering solutions and phishing tools. Also, I enforce Multi-Factor Authentication to access some of the systems and applications. It helps me create an incident response team to deal with phishing incidents and add phishers' threat intelligence to proactively predict emerging phishing attempts.”
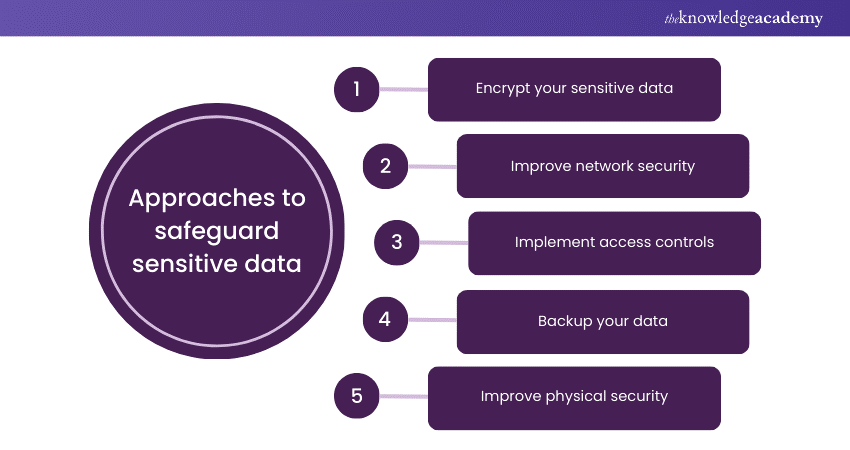
15) What precautions do you take to prevent unauthorised access to sensitive data?
This question seeks insights into the candidate's precautions for preventing unauthorised access. It also assesses how they deal with sensitive data within the organisation.
Sample answer: “Preventing unauthorised access to sensitive data must be developed in a multisided security manner. By using the Role-based Access Control (RBAC) approach, I can control access to data according to the users who request it. Besides the encryptions for both at-rest and in-transit data, I also pack into it where sensitive data is concerned. By means of this IDPS system, weird activity scan algorithms like this can also be turned on.”
16) How do you address employees’ IT security-related grievances?
This question aims to understand how the candidate handles IT security-related grievances from employees within the organisation.
Sample answer: “Addressing IT security-related grievances involves active listening, transparent communication, empowerment, and continuous improvement. I listen attentively to employees' concerns, provide clear and transparent explanations of security policies and procedures, empower employees with knowledge and tools to stay secure, and continuously evaluate and improve security processes based on feedback to enhance the overall security posture of the organisation.”
17) What strategies do you utilise to monitor user behaviour and spot potential malicious activity?
This question delves into the candidate's strategies for monitoring user behaviour and detecting potential malicious activity within the organisation.
Sample answer: “Users’ behaviour and the blocking out of malicious attempts involves the use of secure analytics, the formation of intelligence, and proactive detection. I employ UEBA techniques and threat intelligence feeds for my research. This is because it allows me to scrutinise user behaviour, find anomalies that could be malicious, and act expediently when security incidents occur.”
Join the elite league of security professionals with our CISSP Certification Course – book your spot now!
18) What experience do you possess in disaster recovery planning?
This question seeks insight into the candidate's experience in disaster recovery planning, a critical aspect of Cybersecurity governance.
Sample answer: “In disaster recovery planning, I have gained skills of making customised disaster recovery plans DRPs that are centered on provision of strategies, and steps. This includes performing threat assessments and impact analysis for business including defining the Recovery Time Objectives (RTOs) or Recovery Point Objectives (RPOs).
In addition, it requires implementing redundancy, feasibility technologies, and conducting the DRPs regularly. Thereby, it can help simulate different situations to test the weakening and strengthening of processes and capabilities gradually.”
19) Can you simplify the concept of hyper-convergence for a non-technical executive?
This question aims to assess the candidate's ability to simplify technical concepts for non-technical stakeholders, specifically hyper-convergence.
Sample answer: Hyper-convergence is a contemporary IT infrastructure model that commences the combination of computing, storage, and networking resources to an individual, integrated structure. It holds many important tools at a time, which simplifies data centre operation, reduces complexity, and increases the chance for a single hardware solution to smoothly take organisation to the next level.
20) What is the most impactful executive decision you've made in a similar role?
This question explores the candidate's most impactful executive decision made in a similar role, providing insights into their leadership and decision-making abilities.
Sample answer: “One of the most impactful executive decisions I made in a similar role was advocating for the adoption of a zero-trust security model. This decision transformed our approach to Cybersecurity by shifting from a perimeter-based security paradigm to continuous verification and least privilege access. Implementing zero-trust policies significantly enhanced our ability to detect and mitigate advanced threats, reduce the attack surface, and protect sensitive data from unauthorised access, strengthening our overall Cybersecurity posture.”
Advanced Chief Information Security Officer Interview Questions
Advanced-level questions challenge candidates to demonstrate strategic thinking, Leadership Skills, and in-depth knowledge of Cybersecurity governance. Let's explore some of those questions in the following points:
21) How confident are you in making executive decisions?
This question probes into the candidate's confidence level in making executive decisions, which is crucial for a leadership role.
Sample answer: “I am highly confident in making executive decisions, drawing upon my experience, expertise, and strategic vision to navigate complex challenges and drive organisational success. I believe in assessing all available information and consulting with key stakeholders when necessary.”
22) How would you characterise your approach to management?
This question aims to understand the candidate's Management Style and philosophy, which influences how they lead and inspire teams.
Sample answer: “I characterise my approach to management as collaborative, empowering, and results-driven. I believe in fostering a culture of open communication, trust, and accountability, empowering team members to contribute their unique strengths and ideas towards shared goals. I prioritise mentorship, professional development, and continuous improvement.”
23) Have you ever had to revise a security policy, and if so, what prompted the modification?
This question explores the candidate's experience in revising security policies and the factors that prompted the modifications.
Sample answer: “Yes, I have revised security policies in previous roles to adapt to evolving threats, regulatory requirements, and organisational changes. For example, a significant data breach incident prompted the revision of our incident response policy to enhance detection, response, and recovery capabilities. Additionally, updates to privacy laws and industry standards necessitated revisions to our data protection and compliance policies to ensure alignment and mitigate risks effectively.”
24) What obstacles do you anticipate encountering in this role?
This question seeks insight into the candidate's ability to anticipate and overcome challenges inherent in the CISO role.
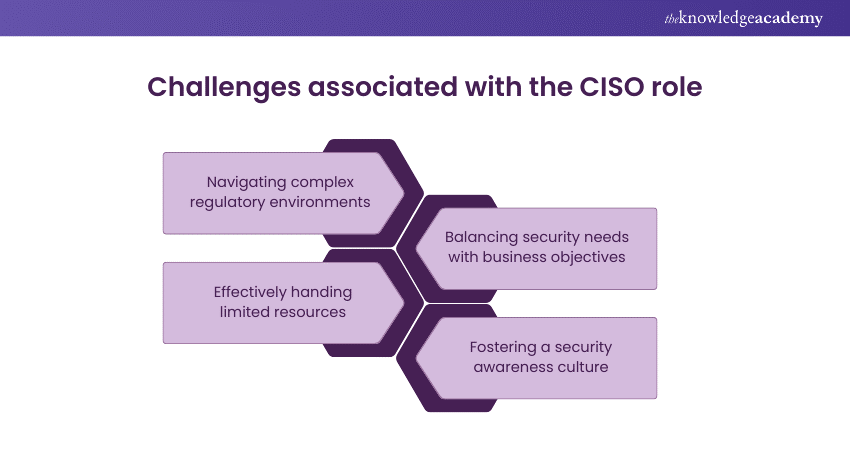
Sample answer: “I have anticipated several obstacles in this role, including navigating complex regulatory environments, balancing security needs with business objectives. Alongside, I was required to effectively manage limited resources besides fostering a culture of security awareness and compliance. Addressing these challenges requires strategic thinking, effective communication, stakeholder engagement, and a proactive approach to risk management.”
25) In your view, what are the essential qualities of a CISO?
This question aims to understand the candidate's perspective on the key qualities and attributes necessary for a successful Chief Information Security Officer (CISO).
Sample answer: Essential qualities of a CISO include strong leadership and communication skills, strategic thinking, technical expertise, business acumen, integrity, resilience, adaptability, and a commitment to continuous learning and improvement. A successful CISO should also possess the ability to build and lead high-performing teams, foster collaboration across departments, and navigate complex challenges with confidence and professionalism.
26) Can you narrate an instance of encountering a security issue in a previous role and your approach to handling it?
This question invites the candidate to share a specific experience of dealing with a security issue in a previous role, demonstrating their problem-solving skills and decision-making abilities.
Sample answer: “In a previous role, we experienced a ransomware attack that compromised critical systems and data. My approach involved initiating our incident response plan, which included isolating affected systems, containing the spread of malware, and restoring data from backups. Additionally, I collaborated closely with internal teams, external vendors, and law enforcement agencies to investigate the incident, mitigate the impact, and strengthen our defences against future attacks. This experience reinforced the importance of preparedness, resilience, and collaboration in effectively managing security incidents.”
Conclusion
In conclusion, the role of the Chief Information Security Officer is multifaceted and challenging. By preparing comprehensive responses to the Chief Information Security Officer Interview Questions, you can successfully secure the job position. We hope this blog helped aspiring CISOs showcase their readiness to lead Cybersecurity efforts and safeguard organisational interests.
Transform your career with our Information Systems Security Management Training – register today and secure your future!
Frequently Asked Questions
Upcoming IT Security & Data Protection Resources Batches & Dates
Date
 Chief Information Security Officer Training
Chief Information Security Officer Training
Mon 17th Mar 2025
Mon 19th May 2025
Mon 18th Aug 2025
Mon 1st Dec 2025







 Top Rated Course
Top Rated Course



 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


