We may not have the course you’re looking for. If you enquire or give us a call on +30 2111995372 and speak to our training experts, we may still be able to help with your training requirements.
We ensure quality, budget-alignment, and timely delivery by our expert instructors.
Picture this scenario: You’re entering a facility where confidential data is stored. You pause and wonder, how secure is it? Are there measures in place to prevent unauthorised access? This is where ISO 27001 Physical Security becomes crucial. This is a vital part of an organisation's information security framework. It ensures that physical access to sensitive information is strictly controlled and monitored.
Implementing this security procedure helps businesses protect their assets from physical threats, ensuring that only authorised individuals can access critical areas. Let's explore its fundamentals and see how it can bolster your defences.
Table of Contents
1) Key Components of ISO 27001 Physical Security Controls
2) The Importance of Implementing Physical Security Controls
3) Steps to Implementing ISO 27001 Physical Security Controls
4) Conclusion
Key Components of ISO 27001 Physical Security Controls
ISO 27001 Key Features for Physical Security is comprehensive, ensuring that every potential point of vulnerability is addressed, thereby maintaining the sanctity and safety of an organisation's critical information and infrastructure. Here are some of its key components:

a) Secure Areas: This goes beyond just locked doors. Establishing security perimeters often involves multi-faceted measures such as surveillance cameras, intrusion detection systems, and even security personnel. This ensures that sensitive areas are well-guarded against unauthorised access and potential threats.
b) Entry Controls: One of the primary defenses against physical breaches, ISO/IEC 27002 PDF emphasizes entry controls using mechanisms like biometric access systems, magnetic card readers, and security tokens to ensure that only authorized individuals can access certain areas, particularly those containing sensitive information.
c) Equipment Security: It's crucial to protect physical assets from theft, damage, or compromise. This means securing storage rooms, using tamper-evident seals, having proper disposal mechanisms for obsolete equipment, and providing secure mounting racks for servers.
d) Working in Secure Areas: Creating protocols for those working in sensitive areas ensures that security isn't compromised. This could involve policies like mandatory screen locks when workstations are unattended or rules about not leaving sensitive documents on desks.
e) Public Access Areas: Areas like reception, delivery, and loading zones require special attention since they might be more accessible to outsiders. Effective surveillance, visitor logs, and restricted movement can counteract potential vulnerabilities.
f) Maintenance of Security: It’s not enough to just implement security measures; they must be regularly reviewed and maintained. This includes assessing the functionality of security systems, updating access rights, or even routine inspections.
The Importance of Implementing Physical Security Controls
Physical Security Controls are not just about guarding tangible assets; they're about preserving an organisation's reputation, ensuring its operational continuity, and instilling trust among clients and stakeholders. ISO 27001 Requirement points will help you to understand the importance of implementing it:
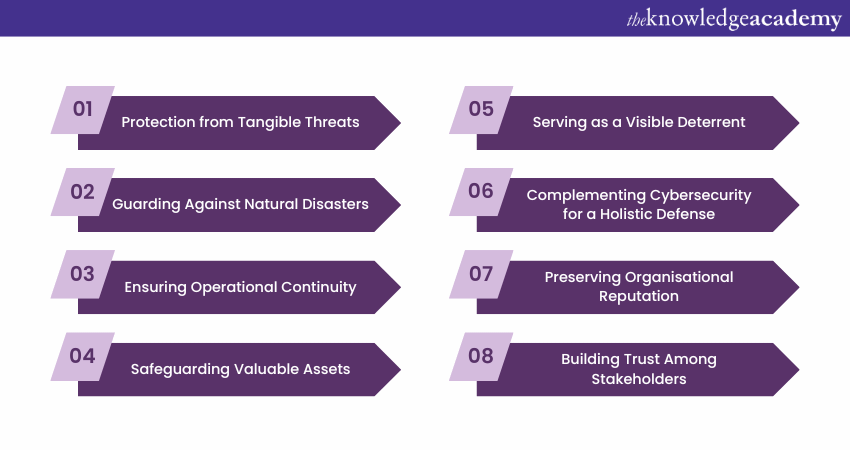
a) Tangible Threats: While cyber threats are evolving rapidly, tangible threats such as theft, vandalism, or even espionage have not diminished. Unauthorised personnel accessing servers can potentially cause as much damage as a hacker breaking into a network.
b) Natural Disasters and Environmental Factors: Physical Controls play a crucial role in protecting organisations from natural calamities like floods, fires, or earthquakes. Measures like fire suppression systems, water leak detectors, and climate-controlled environments ensure continuity and prevent data loss.
c) Operational Continuity: Any disruption, whether due to equipment malfunctions or unauthorised access, can disrupt business operations. Physical controls safeguard against such disruptions, ensuring seamless operational continuity.
d) Asset Protection: Beyond data, businesses have valuable physical assets, from devices to documents. Secured storage areas, surveillance systems, and robust access controls prevent asset theft or tampering.
e) Deterrent Effect: Visible Physical Security measures act as deterrents. The mere presence of security personnel, cameras, and access controls can dissuade potential malicious actors from attempting a breach.
f) Holistic Security Posture: For a comprehensive security approach, cyber and physical security should go together. Overlooking one can lead to vulnerabilities in the other.
Learn Audits that uphold the highest security standards – join our ISO 27001 Lead Auditor Training.
Steps to implementing ISO 27001 Physical Security Controls
Here are some steps to implementing ISO 27001 Physical Security Controls mentioned below:
a) Risk Assessment: Begin by identifying potential risks to your physical assets. This involves evaluating locations, identifying vulnerabilities (like access points), and assessing the likelihood and impact of possible threats.
b) Define Security Perimeters: Establish boundaries around sensitive areas such as server rooms or data centres. These boundaries will help in creating clear zones that require specific security measures.
c) Design Entry Controls: Depending on the assessed risks, determine the types of access controls required. This might range from basic keycard access to more sophisticated biometric systems.
d) Install Surveillance Systems: Equip key areas with surveillance cameras and intrusion detection systems. Regularly monitor and maintain these systems to ensure they are always operational.
e) Develop Policies and Procedures: Draft clear guidelines for staff working in or around secure areas. This might include protocols for visitors, maintenance activities, and emergency response.
f) Train Personnel: Ensure that staff are adequately trained regarding the implemented controls, the significance of these measures, and their roles in maintaining security.
g) Regularly Review and Update: Physical security is not a one-time task. Periodically reassess risks, evaluate the efficacy of controls, and make necessary adjustments to stay ahead of emerging threats.
h) Engage Stakeholders: Involve relevant stakeholders, from management to IT teams, in understanding the importance of these controls, ensuring ISO 27001 Compliance, and promoting a security-first culture.
Learn to develop and manage effective security frameworks – register for our ISO 27001 Lead Implementer Training now!
Conclusion
Implementing ISO 27001 Physical Security Controls is imperative for organisational security. Through systematic assessment, execution, and continuous review, businesses not only protect tangible assets but also fortify their overall security stance. This ensures operational continuity and fosters unwavering trust among stakeholders and clients.
Build a solid foundation in Information Security – join our ISO 27001 Foundation Course now!
Frequently Asked Questions
What are The Key Physical Security Controls Required by ISO 27001?

ISO 27001 mandates essential physical security controls, including secure facility access, CCTV surveillance, restricted entry to sensitive areas, equipment protection, environmental safeguards (such as fire suppression), and visitor logging. These measures safeguard information assets against physical threats.
What are The Main Threats That Physical Security Controls Aim to Prevent?

Physical security controls are designed to prevent threats like unauthorised access, theft, vandalism, natural disasters, fire, and environmental hazards. These measures protect assets, data, and personnel by securing entry points, monitoring activities, and mitigating risks from physical breaches or damage.
What are the Other Resources and Offers Provided by The Knowledge Academy?

The Knowledge Academy takes global learning to new heights, offering over 3,000 online courses across 490+ locations in 190+ countries. This expansive reach ensures accessibility and convenience for learners worldwide.
Alongside our diverse Online Course Catalogue, encompassing 19 major categories, we go the extra mile by providing a plethora of free educational Online Resources like News updates, Blogs, videos, webinars, and interview questions. Tailoring learning experiences further, professionals can maximise value with customisable Course Bundles of TKA.
What is The Knowledge Pass, and How Does it Work?

The Knowledge Academy’s Knowledge Pass, a prepaid voucher, adds another layer of flexibility, allowing course bookings over a 12-month period. Join us on a journey where education knows no bounds.
What are the Related Courses and Blogs Provided by The Knowledge Academy?

The Knowledge Academy offers various ISO 27001 Training, including the ISO 27001 Foundation, ISO 27001 Lead Auditor and the ISO 27001 Internal Auditor. These courses cater to different skill levels, providing comprehensive insights into What is ISO.
Our ISO and Compliance Blogs cover a range of topics related to ISO Certifications, offering valuable resources, best practices, and industry insights. Whether you are a beginner or looking to advance your Security Management skills, The Knowledge Academy's diverse courses and informative blogs have got you covered.
Upcoming IT Security & Data Protection Resources Batches & Dates
Date
 ISO 27001 Foundation
ISO 27001 Foundation
Tue 22nd Apr 2025
Mon 23rd Jun 2025
Mon 28th Jul 2025
Mon 25th Aug 2025
Mon 22nd Sep 2025
Mon 27th Oct 2025
Mon 24th Nov 2025
Mon 15th Dec 2025






 Top Rated Course
Top Rated Course



 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


