We may not have the course you’re looking for. If you enquire or give us a call on +30 2111995372 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.
Microsoft, a pioneering force in the tech industry, recognises the gravity of this challenge and has responded with a robust solution - Microsoft Security Copilot. Microsoft Security Copilot is a modern cybersecurity tool. It helps make digital environments safer by working together with different sources of information.
This blog dives deep into the realm of Microsoft Security Copilot, unravelling its capabilities, benefits, real-world applications, and the considerations organisations must consider. Join us to explore how Microsoft Security Copilot can elevate your cybersecurity strategy to new heights.
Table of Contents
1) To Understand Microsoft Security Copilot
2) Utilising Microsoft Security Copilot
3) Benefits of Microsoft Security Copilot
4) Challenges and considerations
5) Conclusion
To understand Microsoft Security Copilot
Microsoft Security Copilot is a cutting-edge integrated security solution that empowers organisations to effectively detect, investigate, and respond to cybersecurity threats.
Microsoft Security Copilot is a comprehensive security orchestration and automation platform that combines a wide array of security tools, technologies and features into a single, cohesive environment. Its overarching goal is to streamline security operations by providing a unified interface for security teams to monitor, analyse, and act upon potential threats and security incidents.
Key features and capabilities
Let us dive deeper into some of the key features and capabilities that make Microsoft Security Copilot a game-changer in the world of cybersecurity:
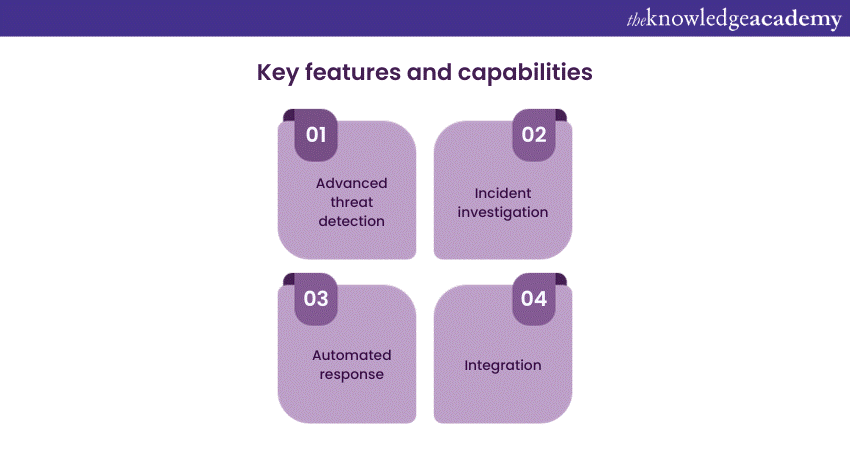
Advanced threat detection
Microsoft Security Copilot harnesses the ability of machine learning, artificial intelligence, and behavioural analytics to identify potential threats lurking within an organisation's network.
By continuously monitoring network traffic, user behaviour, and system activities, it can pinpoint anomalies and potential security breaches that might otherwise go unnoticed. This proactive threat detection is invaluable in today's landscape, where cyberattacks are becoming increasingly sophisticated.
Incident investigation
In the unfortunate event of a security incident, Microsoft Security Copilot provides security teams with the necessary tools to conduct in-depth studies. Security analysts can dig deep into the data to understand the scope and impact of the incident, as well as the tactics and techniques employed by malicious actors. This level of visibility is crucial for mounting an effective response and preventing future attacks.
Automated response
One of the standout features of Microsoft Security Copilot is its ability to automate response actions. This means that, in many cases, the platform can immediately mitigate a threat without requiring manual intervention. For example, it can isolate an infected device from the network, deactivate compromised user accounts, or block malicious communication channels. This automation speeds up the response time and reduces the potential for human error, ensuring a more effective defence.
Integration
Microsoft Security Copilot is designed to seamlessly integrate with an organisation's existing Microsoft security solutions, creating a unified security ecosystem. This integration enhances the overall visibility into the security posture and allows for a more coordinated and cohesive response to threats. It works harmoniously with tools like Microsoft Defender for Endpoint, Microsoft 365 Defender, and Azure Sentinel, creating a robust defence-in-depth strategy.
Ready to enhance your cybersecurity skills with Microsoft Security Engineer Training? Take the first step towards becoming a security expert. Explore our course now
Utilising Microsoft Security Copilot
Now that we have a solid understanding of Microsoft Security Copilot and its core features let us explore how organisations can effectively utilise this powerful cybersecurity solution to enhance their security posture.
Setting up Microsoft Security Copilot
Implementing Microsoft Security Copilot involves crucial steps, beginning with the initial setup. Here is an overview of the process:
1) Assessment and planning: Before deployment, assessing your organisation's security infrastructure and identifying specific goals and requirements is essential. This assessment helps plan the deployment and customisation of Microsoft Security Copilot to align with your organisation's unique needs.
2) Data sources integration: To maximise the platform's effectiveness, you must integrate various data sources, such as logs from security appliances, endpoints, cloud services, and network traffic. Microsoft Security Copilot is designed to work seamlessly with Microsoft 365 Defender, Microsoft Defender for Endpoint, and other Microsoft security solutions, simplifying data integration.
3) Policy configuration: Define security policies and rules that align with your organisation's security objectives. These policies govern how Microsoft Security Copilot will respond to different security events, ensuring a consistent and automated approach to threat mitigation.
4) User and role management: Establish user accounts and role-based access control (RBAC) to determine who has access to specific features and functionalities within the platform. This step ensures that only authorised personnel can view and act upon security data.
5) Automation workflows: Create automation workflows that dictate how the platform should respond to various security incidents. These workflows range from simple actions like blocking an IP address to more complex responses like initiating a forensic investigation.
6) Testing and validation: Before fully deploying Microsoft Security Copilot in a production environment, conduct thorough testing to ensure that policies, automated responses, and integration with existing security tools function as expected.
7) Training and skill development: Train your security personnel in using Microsoft Security Copilot effectively. This may involve understanding the platform's user interface, interpreting security alerts, and responding to incidents. Microsoft provides extensive training resources and certifications to support skill development.
Analysing and correlating security data
One of the critical strengths of Microsoft Security Copilot lies in its ability to collect and analyse vast amounts of security data in real time. Here is how organisations can leverage this capability:
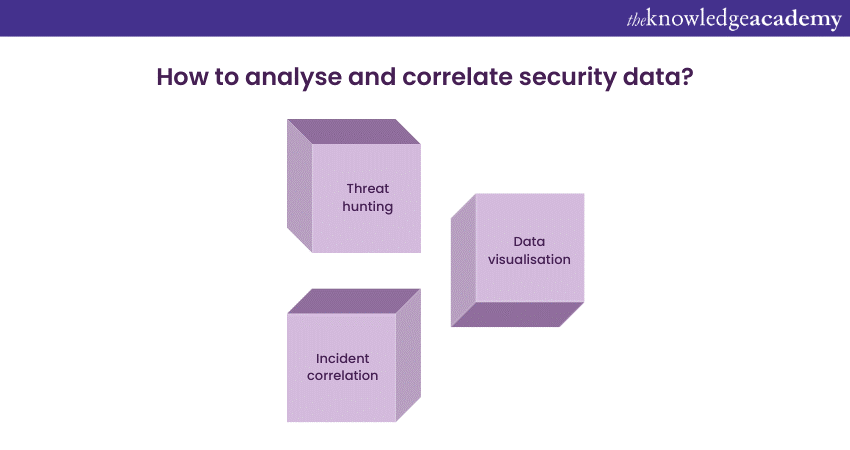
1) Data visualisation: Utilise the platform's dashboard and visualisation tools to gain real-time insights into your organisation's security posture. Dashboards provide a consolidated view of security events, allowing security teams to quickly identify anomalies and potential threats.
2) Incident correlation: Microsoft Security Copilot employs advanced correlation techniques to link seemingly unrelated security events. This capability is crucial for identifying complex attack patterns that may span multiple systems or involve various attack vectors.
32) Threat hunting: Security teams can proactively hunt for threats using Microsoft Security Copilot's data analytics abilities. By leveraging recorded data and machine learning algorithms, security professionals can search for indicators of compromise and emerging threats.
Automated threat detection and response
Automation is a crucial pillar of Microsoft Security Copilot's capabilities. Here are how organisations can harness its power:
1) Real-time alerting: Configure the platform to generate real-time alerts when suspicious activities or security breaches are detected. These alerts can be customised to fit the severity and nature of the threat.
2) Automated remediation: Define automated response actions to specific security events. For example, if a compromised endpoint is detected, Microsoft Security Copilot can automatically isolate the device from the network to prevent further damage.
3) Security playbooks: Create security playbooks that outline the step-by-step response procedures for different incidents. These playbooks can be executed automatically or used as guides for human analysts during investigations.
Enhancing incident response capabilities
Microsoft Security Copilot significantly enhances an organisation's incident response capabilities:
1) Incident triage: The platform prioritises security alerts, helping incident responders focus on the most critical threats first. This prevents alert fatigue and ensures efficient resource allocation.
2) Forensic analysis: Security teams can use Microsoft Security Copilot to conduct detailed forensic research of security incidents. This includes examining logs, identifying the incident's root cause, and understanding the attacker's tactics, techniques, and procedures (TTPs).
3) Collaboration and reporting: The platform facilitates collaboration among incident responders, allowing them to share information, collaborate on investigations, and generate comprehensive incident reports for management and regulatory purposes.
Unlock your potential as a Microsoft Security Operations Analyst SC-200 with our comprehensive training program. Get started on your path to expertise today!
Benefits of Microsoft Security Copilot
Microsoft Security Copilot offers a myriad of benefits that are instrumental in fortifying an organisation's cybersecurity posture:
1) Improved threat visibility: By consolidating and correlating security data from various sources, Microsoft Security Copilot provides security teams with a complete picture of potential threats. This enhanced visibility ensures that even subtle indicators of compromise are not overlooked, enabling proactive threat detection.
2) Streamlined incident management: The platform's automation capabilities expedite incident response. It can automatically trigger predefined actions when security events occur, minimising response times. This lessens the effect of security incidents and ensures a more coordinated and consistent approach to threat mitigation.
3) Proactive threat hunting: Microsoft Security Copilot actively uses AI and machine learning to hunt for emerging threats. Analysing historical data and identifying patterns helps security professionals stay ahead of cyber adversaries and thwart potential attacks before they escalate.
4) Reduced response time: Automation is a game-changer in cybersecurity. With automated responses to security incidents, organisations can dramatically reduce response times, minimising the window of opportunity for attackers to exploit vulnerabilities.
5) Comprehensive integration: Microsoft Security Copilot integrates with existing Microsoft security solutions, creating a cohesive and interconnected security ecosystem. This integration not only simplifies management but also enhances the effectiveness of each security tool.
Ready to master Microsoft Security, Compliance, And Identity Fundamentals SC-900? Begin your journey to expertise now with our specialised training course
Challenges and considerations
While Microsoft Security Copilot offers an array of advantages, organisations must also consider and address specific challenges and considerations:
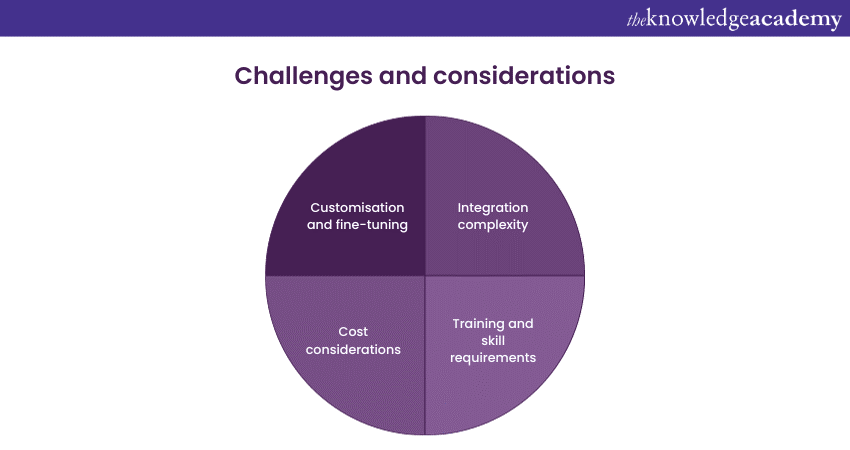
1) Integration complexity: Integrating Microsoft Security Copilot into an existing security infrastructure can be complex. It needs a deep knowledge of the organisation's IT ecosystem and the intricacies of Microsoft's security tools. Ensuring a seamless integration without disrupting ongoing operations can take time and effort.
2) Training and skill requirements: Effectively utilising the platform demands well-trained security personnel who understand its features and capabilities. Organisations must invest in training and skill development to maximise the benefits of Microsoft Security Copilot. This includes understanding its user interface, creating effective security policies, and interpreting security alerts accurately.
3) Cost considerations: While the long-term benefits of improved security and incident response are substantial, organisations must carefully evaluate the initial and ongoing costs associated with Microsoft Security Copilot. This includes licensing fees, personnel training, and potential infrastructure upgrades.
4) Customisation and fine-tuning: Significant customisation and fine-tuning may be required to align the platform with an organisation's security needs. This process can be time-consuming and necessitates ongoing maintenance and adjustment as the threat landscape evolves.

Conclusion
Microsoft Security Copilot embodies the cutting edge of cybersecurity innovation. It empowers organisations to detect and respond to threats efficiently, precisely, and proactively. The benefits of enhanced threat visibility, streamlined incident management, and automated response actions are transformative in today's digital domain.
With Microsoft Security Copilot, organisations possess a formidable ally in the battle against cyber adversaries, a powerful tool that can help safeguard their digital assets, and a platform poised to adapt to the evolving cybersecurity landscape.
Frequently Asked Questions
Upcoming Microsoft Technical Resources Batches & Dates
Date
 Microsoft Security Operations Analyst SC200
Microsoft Security Operations Analyst SC200
Thu 1st Jan 1970







 Top Rated Course
Top Rated Course


 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


