Who should attend this Reverse Engineering Training Course?
This Reverse Engineering Course is designed for individuals seeking to enhance their skills and knowledge in the field of Reverse Engineering. This course is particularly beneficial for professionals such as:
- Software Engineers
- Cybersecurity Professionals
- Ethical Hackers
- Malware Analysts
- Embedded Systems Engineers
- Security Researchers
- Digital Forensics Experts
Prerequisites of the Reverse Engineering Training Course
There are no formal prerequisites to attend the Reverse Engineering Training Course. However, a basic understanding of Windows OS and computer architecture concepts would be beneficial.
Reverse Engineering Training Course Overview
The Reverse Engineering Training Course, a cornerstone of our Advanced Technology Courses, immerses delegates in the intricate world of dissecting and comprehending the inner workings of software and hardware systems. Reverse Engineering is a pivotal skill in the technological realm, allowing individuals to unravel the complexities of existing technologies, enhance security measures, and foster innovation.
In an era where digital security is paramount, the importance of mastering Reverse Engineering cannot be overstated. Cybersecurity Professionals, Software Developers, and IT Forensics Experts are entrusted with safeguarding systems against evolving threats. A thorough understanding of Reverse Engineering empowers these professionals to proactively identify vulnerabilities, analyse malicious code, and fortify systems against potential cyber-attacks.
This 1-day training by the Knowledge Academy caters specifically to the needs of professionals aiming to delve into the realm of Reverse Engineering. Delivered by industry experts, the course provides a comprehensive overview of Reverse Engineering methodologies, tools, and practical applications.
Course Objectives
- To understand the principles and methodologies of Reverse Engineering
- To gain proficiency in analysing and dissecting software and hardware components
- To identify and assess security vulnerabilities in software applications
- To learn techniques for reconstructing and understanding proprietary algorithms and protocols
- To apply Reverse Engineering concepts to enhance cybersecurity measures
- To practice hands-on exercises and real-world case studies in a controlled environment
Upon completion, delegates will emerge with the expertise to conduct systematic Reverse Engineering, enabling them to enhance the security of digital systems, unravel complex algorithms, and contribute effectively to cybersecurity initiatives in their professional roles.








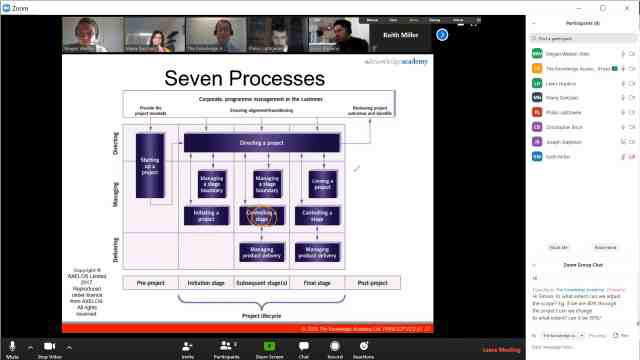
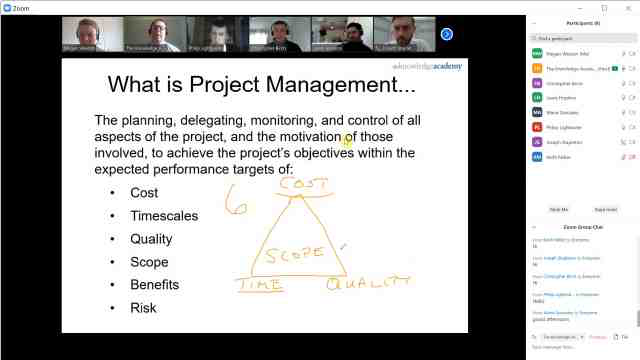


























 Back to course information
Back to course information




 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please

