We may not have the course you’re looking for. If you enquire or give us a call on +852 2592 5349 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.
Are you ready to dive into the world of Ethical Hacking? Picture a career where you're not just defending but actively protecting digital assets. With cyber threats everywhere, how can organisations stay ahead of malicious hackers? The answer is a well-crafted Ethical Hacking Roadmap - your guide to mastering the skills needed to outsmart Cybercriminals.
What does it take to excel in Ethical Hacking? Whether you're new to Cyber Security or shifting focus, this Ethical Hacking Roadmap guides you in developing essential skills and earning key certifications. Dive into the world of Ethical Hacking, where every obstacle is a chance to acquire knowledge, grow, and make a real impact in the fight against cybercrime.
Table of Contents
1) What is Ethical Hacking?
2) Essential Skills for Ethical Hackers
3) CEH Exam
4) Challenges of Ethical Hacking
5) Career opportunities in Ethical Hacking
6) Conclusion
What is Ethical Hacking?
Ethical Hacking, Penetration Testing or simply white hat hacking is the authorised practice of assessing the security of computer systems and networks. Ethical Hackers use their knowledge to identify vulnerabilities and potential weaknesses, helping organisations strengthen their security measures.
Ethical Hackers provide valuable insights into system and network security by simulating real-world cyber-attacks. They employ network scanning and system testing techniques to uncover vulnerabilities and recommend remedial actions. Ethical Hacking plays a crucial role in ensuring the integrity and confidentiality of digital assets.
Importance of Ethical Hacking
As cyber threats become more frequent, organisations require skilled professionals to identify vulnerabilities and protect their valuable data and systems. Ethical Hackers play a proactive role in security by helping organisations identify weaknesses before malicious hackers exploit them.
Ethical Hackers contribute to the resilience of systems and networks by conducting thorough security assessments. As technology advances, the demand for Ethical Hackers with up-to-date skills and knowledge will continue to grow, making their role vital in safeguarding digital assets.
Essential Skills for Ethical Hackers
To succeed as an Ethical Hacker, one must possess many essential skills. These include technical proficiency, which entails having a deep understanding of various technologies, programming languages, and cybersecurity tools. Here are some ranges of skills you can leverage as an Ethical Hacker to effectively assess vulnerabilities, enhance security measures, and contribute to the overall safety of organisations:
Certifications and Education
Pursuing certifications can allow you to gain valuable knowledge and demonstrate your commitment to information security and Ethical Hacking. To establish a strong foundation in Ethical Hacking, consider pursuing the following certifications and educational paths:
1) Certified Information Systems Security Professional (CISSP): A widely acknowledged certification for information security professionals. While not specifically tailored to Ethical Hacking, it provides a comprehensive understanding of various domains within information security, including risk management, cryptography, and network security. CISSP certification demonstrates expertise in securing computer systems and protecting organisations against cyber threats.
2) CompTIA Security+: This entry-level certification covers foundational knowledge of cybersecurity principles and best practices. This certification focuses on network security, risk management, cryptography, and incident response. CompTIA Security+ certification equips individuals with the fundamental skills to secure computer systems and networks effectively.
3) Bachelor's Degree in Computer Science: This degree provides a solid educational foundation for Ethical Hacking. This degree program covers computer science topics, including programming languages, algorithms, computer networks, and software development. Students gain a deep understanding of computer systems and acquire the technical skills necessary for Ethical Hacking.
4) Bachelor's Degree in Cybersecurity: This degree focuses on cybersecurity, providing specialised knowledge and skills. This degree program covers the details of network security, digital forensics, Ethical Hacking, and information security management. Students learn to identify vulnerabilities, protect systems, and mitigate cyber threats effectively.
Take our CISSP Certification Course and gain the foundation of an Ethical Hacker!
Tools and Technologies
To effectively perform Ethical Hacking and enhance Cyber Security, professionals utilise a variety of tools and technologies that can assess the security of systems, identify vulnerabilities, and propose necessary security measures. Here are some essential Ethical Hacking Tools commonly employed in the field:
1) Network Scanners: Network scanners are crucial tools for Ethical Hackers to gather information about networks and identify potential vulnerabilities. These tools scan network devices, ports, and services, providing insights into network topology and identifying weak points that can be exploited.
2) Vulnerability Assessment Software: Vulnerability assessment software plays a vital role in Ethical Hacking by identifying vulnerabilities in systems and applications. These tools scan for known vulnerabilities, misconfigurations, and weak security practices, allowing Ethical Hackers to address these issues and strengthen the security posture of targeted systems.
3) Password Crackers: Password crackers are used to uncover passwords or bypass authentication mechanisms. Ethical Hackers employ these tools to test the strength of passwords and identify weak or easily guessable passwords. This enables them to assess the overall security of systems and recommend more robust password practices.
4) Forensic Analysis Tools: Forensic analysis tools aid Ethical Hackers in investigating security incidents and conducting digital forensics. These tools help collect evidence, analyse system logs, recover deleted files, and uncover malicious activities. Forensic analysis tools are crucial for identifying the source of attacks and understanding the extent of a security breach.
5) Network Sniffers: Network sniffers, also known as packet analysers, allow Ethical Hackers to capture and analyse network traffic. These tools help understand the flow of data within a network, identify potential security risks, and detect unauthorised or suspicious activities. Network sniffers are valuable for monitoring network communication and identifying potential vulnerabilities or weaknesses.
6) Exploitation Frameworks: Exploitation frameworks provide a collection of tools and resources for identifying and exploiting vulnerabilities. These frameworks often include many exploits, payloads, and post-exploitation modules, enabling Ethical Hackers to assess and exploit vulnerabilities effectively. These tools require a deep understanding of Ethical Hacking principles and should be used responsibly and ethically.
Networking and System Knowledge
Ethical Hackers must understand networking and system fundamentals to assess and secure computer systems effectively. This knowledge allows them to identify security weaknesses, assess the risk posed by various components, and implement appropriate security measures to protect networks and systems from potential threats. Here are key areas of knowledge in this domain:
Protocols: TCP/IP protocols form the foundation of modern network communication. Ethical Hackers must have a strong foundation of protocols such as IP, TCP, UDP, ICMP, and DNS. Knowing how these protocols work and their vulnerabilities enable hackers to identify potential weaknesses and exploit them if necessary.
Operating Systems: Proficiency in different operating systems is crucial for Ethical Hackers. Understanding the inner workings of popular operating systems like Windows, macOS, and Linux is essential. Knowledge of system architecture, file systems, user management, and process control helps hackers identify security gaps and potential attack vectors specific to each operating system.
Firewalls and Routers: Firewalls and routers are critical in securing networks. Ethical Hackers must understand how these devices work, including their configurations, rule sets, and security mechanisms. Familiarity with firewall and router technologies allows hackers to analyse network traffic, identify potential vulnerabilities, and recommend appropriate security measures.
Wireless Networks: As wireless networks have become a prominent part of our everyday lives, Ethical Hackers must possess knowledge of wireless protocols, encryption methods, and vulnerabilities associated with Wi-Fi networks. Understanding concepts like WEP, WPA, WPA2, and WPA3, as well as techniques such as rogue access point detection and wireless packet capture, empowers hackers to assess the security of wireless networks.
Learn the basics of Ethical Hacking with the Ethical Hacking Professional Course!
CEH Exam
To become an Ethical Hacker, having a technical background is crucial. One of the key steps is passing the Certified Ethical Hacker (CEH) exam, a recognised certification that equips professionals with the skills needed for Ethical Hacking. The CEH programme covers the latest techniques to identify and mitigate hacker attacks and network vulnerabilities.
As technology advances, the CEH course and exam are regularly updated to ensure professionals remain current. Obtaining this certification is vital for anyone looking to excel in the Ethical Hacking field.
Learning and Certification
You can register for various online Cyber Security courses that offer certificates to learn the necessary concepts and start your professional journey. These courses provide access to top-notch study materials and training from qualified professionals. Once certified, you can seize the best opportunities in the field.
Exam Overview
a) Number of Questions: 125
b) Passing Score: 70%
c) Duration: 4 hours
d) Application: Apply online to take the exam. If you fail, you can retake it by emailing the EC Council manager with your previous score and paying the fee again.
e) Certification Maintenance: Renew every three years with 120 EC Council continued education credits.
Eligibility Criteria for CEH
To be eligible for the CEH exam, you must meet certain criteria. There are two pathways to certification:
a) With Training: Attend an official training program approved by EC Council training partners.
b) Without Formal Course: Have a minimum of two years of information security experience.
Become a Certified Ethical Hacker with our expert-led Certified Ethical Hacker Certification Course and secure your future in Cyber Security today!
Challenges of Ethical Hacking
Ethical Hacking, while essential for Cyber Security, comes with its own set of challenges. Here are some of the key challenges faced by Ethical Hackers:
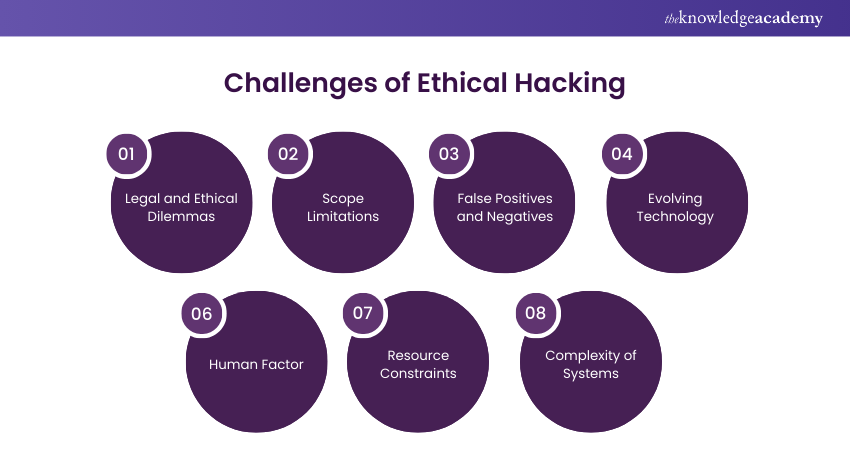
1) Legal and Ethical Dilemmas: Ethical Hackers operate in a delicate space, balancing legality and ethical considerations. They must ensure they have proper authorisation and adhere to legal boundaries to avoid potential lawsuits.
2) Scope Limitations: Ethical Hacking engagements often come with predefined scopes, limiting the areas that can be tested. This can result in some vulnerabilities being overlooked.
3) False Positives and Negatives: Identifying vulnerabilities can sometimes lead to false positives (non-issues flagged as issues) or false negatives (real issues not detected), which can affect the accuracy of the assessment.
4) Evolving Technology: The fast-evolving landscape of technology requires ethical hackers to frequently update their skills and knowledge to remain informed of new threats and vulnerabilities.
5) Human Factor: Humans remain a significant Cyber Security vulnerability. Social engineering attacks exploit human psychology, making it challenging to secure systems completely.
6) Resource Constraints: Ethical Hacking requires significant resources, including time, tools, and expertise. Limited resources can hinder the effectiveness of Ethical Hacking efforts.
7) Complexity of Systems: Modern IT environments are complex, with interconnected systems and applications. This intricacy makes it difficult to identify and address all potential vulnerabilities.
Join our Certified Penetration Testing Professional Certification Course to gain the skills needed to excel in Penetration Testing and Cyber Security!
Career Opportunities in Ethical Hacking
Ethical Hacking has emerged as a highly sought-after profession in cybersecurity. As organisations prioritise the protection of their digital assets and sensitive data, the demand for skilled Ethical Hackers continues to grow. Here are some exciting career opportunities in Ethical Hacking:

1) Ethical Hacker/Penetration Tester: They assess the security of systems, networks, and applications by performing penetration tests. They identify vulnerabilities, exploit them ethically, and recommend enhancing security measures.
2) Security Consultant: They offer expert advice and guidance on security practices and policies. They assess risks, design security architectures, and develop strategies to protect organisations from cyber threats.
3) Incident Responder: They play a crucial role in handling and mitigating the impact of security incidents. They investigate breaches, contain threats, and develop incident response plans to minimise future risks.
4) Security Analyst: They specialise in investigating cybercrimes and collecting digital evidence. They analyse data breaches, conduct forensic examinations, and provide evidence for legal proceedings.
5) Forensic Analyst: They specialise in investigating cybercrimes and collecting digital evidence. They analyse data breaches, conduct forensic examinations, and provide evidence for legal proceedings.
6) Security Engineer: They design and implement secure systems and networks. They develop security protocols, configure firewalls, and ensure the overall security of the infrastructure.
7) Security Auditor: They assess the effectiveness of security controls and policies. They conduct audits, identify vulnerabilities, and provide recommendations for industry standards and regulations compliance.
Prepare for a rewarding career in Cyber Security with our Ethical Hacking Training, covering essential techniques and certifications!
Conclusion
This Ethical Hacking Roadmap provides a comprehensive framework for individuals aspiring to become Ethical Hackers. You can embark on a successful and responsible journey in Ethical Hacking by acquiring the necessary skills, certifications, and knowledge. This includes expertise in cloud security, legal and ethical considerations, and other critical areas. Start your journey today and become a leader in safeguarding digital landscapes!
Try our Mastering Metasploit Framework Course and use Metasploit in penetration testing!
Frequently Asked Questions

The five stages of Ethical Hacking are:
1) Reconnaissance - Gathering information
2) Scanning - Identifying vulnerabilities
3) Gaining Access - Exploiting vulnerabilities
4) Maintaining Access - Sustaining access
5) Covering Tracks - Erasing evidence

The future scope of ethical hackers is promising, with a growing demand for cyber security experts to combat increasing cyber threats. Opportunities in sectors like finance, government, and tech will continue to expand.

The Knowledge Academy takes global learning to new heights, offering over 30,000 online courses across 490+ locations in 220 countries. This expansive reach ensures accessibility and convenience for learners worldwide.
Alongside our diverse Online Course Catalogue, encompassing 17 major categories, we go the extra mile by providing a plethora of free educational Online Resources like News updates, Blogs, videos, webinars, and interview questions. Tailoring learning experiences further, professionals can maximise value with customisable Course Bundles of TKA.

The Knowledge Academy’s Knowledge Pass, a prepaid voucher, adds another layer of flexibility, allowing course bookings over a 12-month period. Join us on a journey where education knows no bounds.

The Knowledge Academy offers various Ethical Hacking Training, including Ethical Hacking Professional and Mastering Metasploit Framework. These courses cater to different skill levels, providing comprehensive insights into Ethical Hacker Roles and Responsibilities.
Our IT Security & Data Protection Blogs cover a range of topics related to Ethical Hacking, offering valuable resources, best practices, and industry insights. Whether you are a beginner or looking to advance your IT Security skills, The Knowledge Academy's diverse courses and informative blogs have got you covered.
Upcoming IT Security & Data Protection Resources Batches & Dates
Date
 Ethical Hacking Professional
Ethical Hacking Professional
Thu 16th Jan 2025
Thu 6th Mar 2025
Thu 22nd May 2025
Thu 24th Jul 2025
Thu 4th Sep 2025
Thu 20th Nov 2025
Thu 18th Dec 2025







 Top Rated Course
Top Rated Course



 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


