We may not have the course you’re looking for. If you enquire or give us a call on +36 18508731 and speak to our training experts, we may still be able to help with your training requirements.
We ensure quality, budget-alignment, and timely delivery by our expert instructors.

SQL Injection Attack is considered one of the most common types of security exploits used by attackers to illegally access the data from the database of web applications. There have been continuous updates and development of newer security measures to tackle these common security vulnerabilities.
Do you know the reason for these evolving software updates and security developments?
Most of you should have guessed the reason by now. The reason is evident – hackers are inventing more intelligent and unique ways to keep up with the anti-hacking measures.
The survey done by Statista shows that the common IT vulnerabilities and exposures experienced worldwide in 2022 are more than 22,500. It is the highest reported annual figure to date.
In this blog, let us try to understand the SQL Injection Attack in Cyber Security in a more detailed way.
Table of Contents
1) What is an SQL Injection Attack?
2) Types of SQL Injection in Cyber Security
3) Consequences of a SQL Injection Attack
4) Ways to protect your database against SQL Injection Attack
5) How to detect SQL Injection Attack?
6) Conclusion
Interested in acquiring skills to mitigate cyber risks? Then, register for the CCNA Cybersecurity Operation Training now!
What is an SQL Injection Attack?
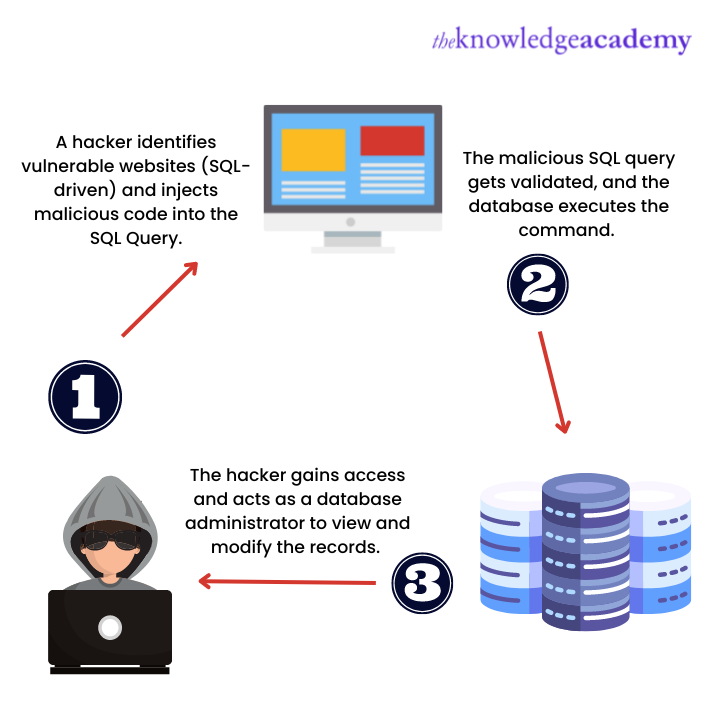
An SQL injection (SQLi) attack is a technique used by cyber attackers to exploit vulnerabilities using unauthorised access to web-based applications. This cyberattack injects malicious SQL code into a web-based application. The attacker can then use it to view, access, delete, or modify sensitive information from the database.
At times the attacker can take control of the server also. While websites are the most common target, SQL Injection attacks can also target any application that uses an SQL database. The common SQL databases include Oracle, MySQL, and SQL Server.
Types of SQL Injection in Cyber Security
There are several types of SQL injection attacks that can be used to exploit vulnerabilities in a web-based application. The following are the most common types of in-band SQL injection attacks mentioned.
In-band SQL Injection
The malicious user can use this type of SQL Injection Attack to attack using the communication channel.
Union-based injection: A Union-based injection is an attack involving injecting a UNION operator into a SQL query. It allows the attacker to retrieve additional data from the database.
In a union-based injection attack, the attacker injects a SELECT statement into a vulnerable SQL query. Along with the UNION operator and additional SELECT statements, the attacker can retrieve the data from the database they usually would not have access.
Error-based injection: An Error-based injection is a type of SQL injection attack that relies on causing an error in the database. Consequently, it can reveal sensitive information about the database's structure or the software being used.
In an Error-based injection attack, the attacker injects a command code into a vulnerable SQL query to cause an error in the database. The error message returned by the database is then used to extract information about the database structure or the software.
Inferential SQL Injection
Inferential SQL Injection is sometimes referred to as a Blind SQL Injection because the data from the website database is not transferred, to the attacker, unlike the In-band SQL Injection. As the time taken to perform this attack is longer, Inferential SQL Injection Attacks are less commonly used than In-Band SQL Injection Attacks.
Boolean-based injection: The Boolean-based injection is an attack involving injecting code that will cause a Boolean value (true or false) to be returned. This can determine whether a particular condition is met in the database.
In a Boolean-based injection attack, the attacker injects or sends a code into a vulnerable SQL query that will cause the database to return a Boolean value (true or false) based on the success or failure of a particular condition. The attacker can then use this Boolean value to infer whether a specific condition is met in the database, such as whether a particular username and password combination is valid.
Time-based injection: The time-based injection is an attack involving injecting code that will cause a delay in the database's response time, which can be used to extract sensitive information.
In a Time-based injection attack, the attacker injects code into a vulnerable SQL query and sends it to the database. Consequently, this will cause the database to pause for a specific time before returning a result. The attacker can then use this delay time to determine whether a particular condition is true or false based on how long the database takes to respond.
For example, an attacker injects a time-based injection attack by modifying the search term (in vulnerable website’s search function) to include a code that will cause a delay in the database's response time.
Example of a Code: $search_term = "' OR SLEEP(3) --"
In this case, if the database takes longer than 3 seconds to respond, the attacker could conclude that the condition is true. If the database responds more quickly, the attacker could conclude that the condition is false.
Stored procedure injection: Stored procedure injection is an attack involving injecting code into a stored procedure (a pre-defined set of SQL statements) in the database, which can be used to execute arbitrary code.
In a Stored procedure injection attack, the attacker injects a code or a command into a vulnerable stored procedure in the database, which the database can then execute. This allows the attackers to execute arbitrary code on the database server. It also gives them access to sensitive information or will enable them to take control of the server.
Out of Band SQL injection
Out of Band (OOB) SQL injection attack uses a separate channel to exfiltrate data from the database rather than relying on the database to return the results directly to the attacker. This injection technique will be helpful in situations where the attacker cannot directly access the data returned by the database. The reason may be either because the database is not connected to the internet or because a firewall is blocking the results.
In an Out of Band SQL injection attack, the attacker injects code into a vulnerable SQL query. The database sends the results of the query to a separate location, such as a server controlled by the attacker. Now, the attacker can access the results at this different location rather than receiving them directly from the database.
The OOB SQL injection attacks are more challenging to carry out compared to the other types of SQL injection attacks. The reason is the attacker's requirement to access a separate server that can receive the exfiltrated data. However, Out of Band SQL injection attacks can be effective in situations where other types of SQL injection attacks are not possible.
Do you want to professionally identify attacks and vulnerabilities of your software applications before infiltration? Then, you can register with the CompTIA Cybersecurity Analyst CySA+ Certification course for Expert training and help.
Consequences of a SQL Injection Attack
Organisations can suffer a setback based on the damage caused by the impact of an SQL Injection attack. The purpose of any malicious attack is to extract private and sensitive information of the targeted organisation.
Any vulnerable organisation suffering from the SQLi attack are susceptible to undergo the following impacts:
Confidential and sensitive data exposed: You are at a high risk as the attacker can alter, retrieve, delete, and modify the sensitive data stored in the database or the server of your organisation.
Privacy compromised: Based on the impact and the type of attack, your private user data, such as bank account details or credit card numbers stored on the SQL server, will be exposed to the attacker.
Gaining administrative access to the computer: The attacker might gain access to your system using malicious code if the database user has administrative privileges.
Risk of obtaining general access to the system: Using weak SQL commands and outdated programming language can give an attacker the liberty to check or access usernames and passwords. Getting general access to the system can be used by an attacker to manipulate and cause severe damage to sensitive information.
Data Integrity is compromised: In case of experiencing an attack, the data stored in the computer loses its standards as it is at a high risk of being exposed and manipulated.
As SQL Injection Attacks can bring severe drawbacks to your company, businesses must practice preventive measures and limit the vulnerabilities to avoid such attacks. Implementing robust Cyber Security for Business measures is crucial to safeguard against SQL Injection and other potential threats.

If you are willing to develop your skills and gain in-depth knowledge in Information security, register with CISSP Training now.
Ways to protect your database against SQL Injection Attack
Incorporating security measures when developing your website or web application limits the exposure to vulnerable SQL Injection attacks. The list below describes a few of the most effective ways to prevent SQL Injection Attacks.
1) Update or install the latest software to fix the exposed patches
2) Build SQL statements using parameters that are stored in the database or the application
3) Validate the user-supplied inputs (like drop-down menus)
4) Give minimum privileges to the users connected with the SQL database
5) Use Allow list input validation instead of Block List to prevent adding invalidated user input to the query
6) Instead of sending error messages to the web browser, configure them to avoid any possible intrusion
7) Avoid sharing database accounts across random websites and applications
In general, the organisations are recommended to follow the above measures along with the additional prevention means, based on the situational and technical demands of the company.
How to detect SQL Injection Attack?
If an SQL Injection Attack is carried out successfully, it can cause immense damage by revealing sensitive data and creating havoc. Additionally, it can have detrimental effects on the customer's trust. Hence, detecting this kind of malicious attack on time is crucial to protect the sensitive data stored in the database, server and other forms of online applications.
Firewalls are one of the most common tools to filter out SQLi attacks in Web applications. These Firewalls can be configured to flag the malicious SQL queries raised in web applications.
Following are the practices that can help you prevent and detect SQL Injection Attacks:
Educate and train employees on possible threats (giving previous examples) with preventive measures: The IT team, system admins, and software developers of an organisation must receive proper security training to understand the importance of how to prevent SQLi attacks from happening in web applications.
Never trust user input: The input received from the user in a SQL increases the chances of an SQL Injection Attack. It would be best to use security measures to mitigate the risks when entering user input.
Instead of using a Block list, use Allow list: Using Allow list is recommended because cyber criminals can usually break through or bypass the Block list.
Perform updates and adopt the latest versions of applications: Outdated software is one of the most common SQL Injection vulnerabilities. Often, the unpatched software is easier to manipulate than the updated software. Additionally, using older programming languages and syntax can be vulnerable to cyber-attacks.
Use of valid preventive methods: The best way to protect web-based applications is by using prepared standards, parameterised queries, and input validation.
Executing regular security scans: Performing regular check-ups or scanning for web applications can help you find vulnerabilities. This process helps in avoiding any serious damage.
Conclusion
In this blog, we have discussed SQL Injection Attacks and explained some examples of SQL Injection Attacks that exploit vulnerabilities in a website or web-based application. Reading this blog will give you an idea about how SQL server users are majorly under the threat of SQL Injection Attacks and the possible measures to avoid these cyber-attacks.
Nevertheless, it is significant for developers to be aware of these types of attacks and to take necessary steps to prevent them.
Are you an advanced professional with high experience and knowledge in a wide range of cybersecurity areas? Then, this Microsoft Cybersecurity Architect SC100 Training is definitely for you!
Upcoming Programming & DevOps Resources Batches & Dates
Date
 Certified Cyber Security Professional (CCS-PRO)
Certified Cyber Security Professional (CCS-PRO)
Fri 23rd May 2025
Fri 22nd Aug 2025
Fri 5th Dec 2025






 Top Rated Course
Top Rated Course




 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


