We may not have the course you’re looking for. If you enquire or give us a call on +44 1344 203 999 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.
Penetration Testing, also known as “pen-testing” or "ethical hacking", plays a critical role in identifying vulnerabilities in systems, networks, and applications. To effectively conduct Penetration Testing, professionals rely on a diverse array of tools. Penetration Testing Tools empower security professionals to identify weaknesses, assess potential risks, and implement robust countermeasures. A survey by Statista found that in 2020, 44% of Cybersecurity professionals globally used Penetration Testing Tools as part of their security strategies.
As the frequency and complexity of cyberattacks continue to rise, staying ahead of potential threats is paramount. In this blog, we'll explore the top 25 Penetration Testing Tools essential for protecting digital assets and key features.
Table of Contents
1) What are Penetration Testing Tools?
2) Importance of Penetration Testing Tools
3) 25 Best Penetration Testing Tools you can work with
a) Nmap
b) Metasploit
c) Wireshark
d) Burp Suite
e) Nessus
f) Acunetix
g) BeEF
h) Kali Linux
i) Hashcat
j) OpenVAS
4) Conclusion
What are Penetration Testing Tools?
Penetration Testing Tools are software applications designed to automate and assist in the process of ethical hacking. These tools simulate various types of cyberattacks to comprehensively evaluate a system's security posture. They help identify vulnerabilities, misconfigurations, and potential entry points that attackers might exploit.
Importance of Penetration Testing Tools
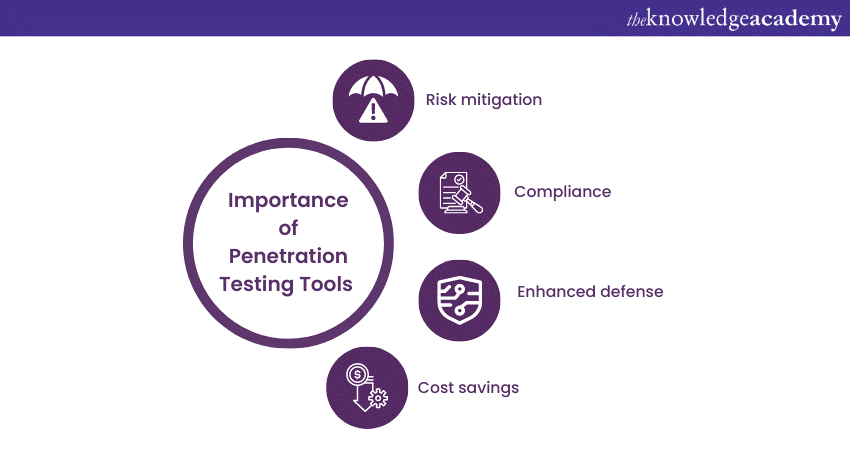
Penetration Testing serves as a proactive approach to cybersecurity. Its importance lies in the following:
a) Risk mitigation: Identifying vulnerabilities before they are exploited minimises the risk of data breaches and system compromises.
b) Compliance: Many industries and regulations require regular security assessments to ensure compliance with security standards.
c) Enhanced defence: By understanding vulnerabilities, organisations can fortify their defences and patch weak points.
d) Cost savings: Detecting and addressing vulnerabilities early can save the significant costs associated with recovering from a successful cyberattack.
25 Best Penetration Testing Tools you can work with
Penetration Testing Tools come in various forms, including commercial and open-source options, each offering unique features to address different aspects of security testing. Here are the popular Penetration Testing Tools used by experts:
1) Nmap
Nmap (Network Mapper) is a versatile and widely used network scanning tool. It excels at discovering devices, services, and open ports within a network. Nmap's robust scanning capabilities allow security professionals to gain insights into the network's structure, identify potential vulnerabilities, and map attack surfaces.
Key Features:
a) Host discovery and network scanning
b) Service and version detection
c) Scriptable interaction with target systems
d) Network mapping and port scanning
2) Metasploit
Metasploit is a widely acclaimed Penetration Testing framework that is a go-to choice for many security professionals. Metasploit simplifies and automates the process of conducting Penetration Tests by providing a user-friendly interface for crafting and executing various types of attacks. This tool caters to both beginners and experienced Penetration Testers, making it an essential asset for any security toolkit.
Key Features:
a) Exploit development and testing
b) Network and web application Penetration Testing
c) Post-exploitation activities and payload delivery
d) A comprehensive database of known vulnerabilities and exploits
Unlock the secrets of ethical hacking with our Ethical Hacker Training – Sign up today!
3) Wireshark
Wireshark is a popular open-source packet analyser that allows users to capture, analyse, and interpret network traffic. It provides a detailed view of data packets traversing a network, allowing security analysts to identify anomalies, detect unauthorised activities, and diagnose network issues.
Key Features:
a) Deep inspection of network traffic
b) Support for a wide range of protocols
c) Real-time and offline analysis capabilities
d) Detailed packet-level analysis and filtering
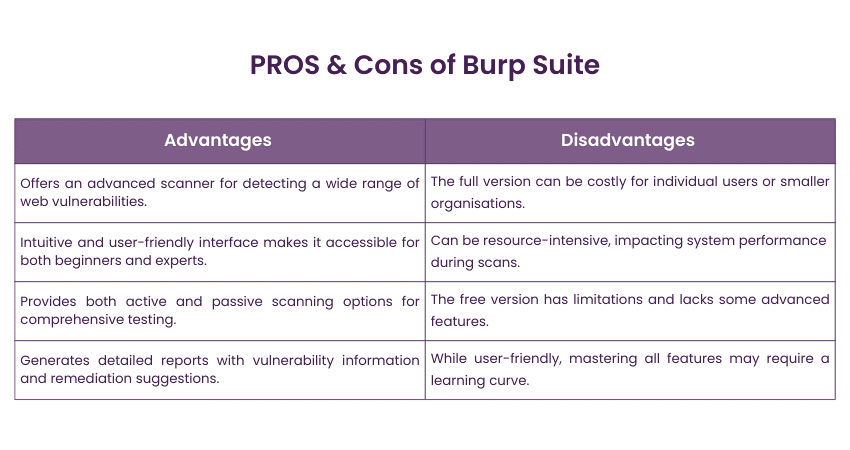
4) Burp Suite
Burp Suite is a favourite among professionals specialising in web application security. This comprehensive toolkit offers a range of tools, including a proxy, scanner, and various utilities for web security testing. Burp Suite aids in identifying common web vulnerabilities such as SQL injection, cross-site scripting (XSS), and insecure configuration issues.
Key Features:
a) Web vulnerability scanning and assessment
b) Intercepting proxy for modifying and analysing traffic
c) Application-aware spidering and scanning
d) Active and passive vulnerability scanning
5) Nessus
Nessus is a leading Penetration Testing tool known for its comprehensive scanning capabilities. It helps security teams identify vulnerabilities, misconfigurations, and compliance issues across various assets, including networks, systems, and applications. Its reporting capabilities allow users to generate detailed reports for stakeholders, making it a valuable tool for both security practitioners and compliance professionals.
Key Features:
a) Vulnerability assessment and scanning
b) Extensive database of known vulnerabilities
c) Configuration and compliance audits
d) Remediation suggestions and reporting
6) Acunetix
Acunetix is a specialised web vulnerability scanner that excels in detecting and addressing security issues in web applications. Acunetix also provides insights into the OWASP Top Ten vulnerabilities, helping organisations prioritise and remediate critical issues.
Key Features:
a) Web application security scanner
b) Comprehensive scanning of HTML5, JavaScript, and single-page applications
c) Detection of SQL injection, XSS, and other vulnerabilities
d) Integration with popular issue-tracking tools
7) BeEF
BeEF (Browser Exploitation Framework) is a unique tool that targets web browsers using client-side attacks. It focuses on exploiting vulnerabilities in web browsers to establish control over a victim's browser and gather information.
Key Features:
a) Browser-based exploitation framework
b) Targets web browsers' vulnerabilities and weaknesses
c) Demonstrates the potential impact of client-side vulnerabilities
d) Useful for understanding and mitigating browser-based attacks
8) Kali Linux
Kali Linux is a widely used Linux distribution designed for Penetration Testing, ethical hacking, and security analysis. It provides a robust environment for conducting comprehensive Penetration Tests, making it a staple in the toolkit of ethical hackers.
Key Features:
a) Debian-based Linux distribution designed for Penetration Testing
b) Pre-installed with a vast array of security tools
c) Easily customisable and extensible for specific testing needs
d) Offers a comprehensive platform for various security assessments
9) Hashcat
Hashcat is a powerful password-cracking tool that specialises in recovering passwords from various hash formats. While not exclusively a social engineering tool, Hashcat can be used to assess the strength of passwords in a social engineering context. It supports multiple algorithms and attack modes, making it effective for cracking both individual and enterprise passwords.
Key Features:
a) Advanced password recovery and cracking tool
b) Supports a wide range of hash algorithms and encryption methods
c) Utilises GPU acceleration for faster cracking
10) OpenVAS
OpenVAS (Open Vulnerability Assessment System) is a feature-rich open-source vulnerability scanner. It helps in identifying security issues within networks and systems by performing comprehensive vulnerability assessments. It is particularly effective for regular vulnerability scanning and ensuring that systems remain up to date with the latest security patches.
Key Features:
a) Open-source vulnerability assessment system
b) Extensive database of security checks and tests
c) Regularly updated vulnerability feeds
d) Scalable and customisable scanning capabilities
11) Nikto
Nikto is a command-line web vulnerability scanner that focuses on identifying common issues in web servers and applications. Nikto's simplicity and speed make it an efficient tool for quickly assessing the security posture of web servers.
Key Features:
a) Web server scanner that detects various vulnerabilities
b) Checks for outdated software, server misconfigurations, and known vulnerabilities
c) Generates comprehensive reports of scan results
12) SQLMap
SQL Map is a powerful open-source tool designed specifically for detecting and exploiting SQL injection vulnerabilities in web applications. Its capabilities include fingerprinting databases, dumping data, and executing custom SQL queries.
Key Features:
a) Specialised tool for automated SQL injection and database takeover
b) Detects and exploits SQL injection vulnerabilities
c) Provides options for data extraction, access escalation, and more
d) Supports various database systems
13) W3af
W3af is an open-source web application attack and audit framework. W3af includes various plugins for discovering weaknesses like SQL injection, cross-site scripting (XSS), and more. While its primary focus is on technical vulnerabilities, these can be exploited with social engineering tactics.
Key Features:
a) Web application attack and audit framework
b) Identifies and exploits web vulnerabilities
c) Supports both automatic and manual exploitation
d) Focuses on discovering vulnerabilities unique to web applications
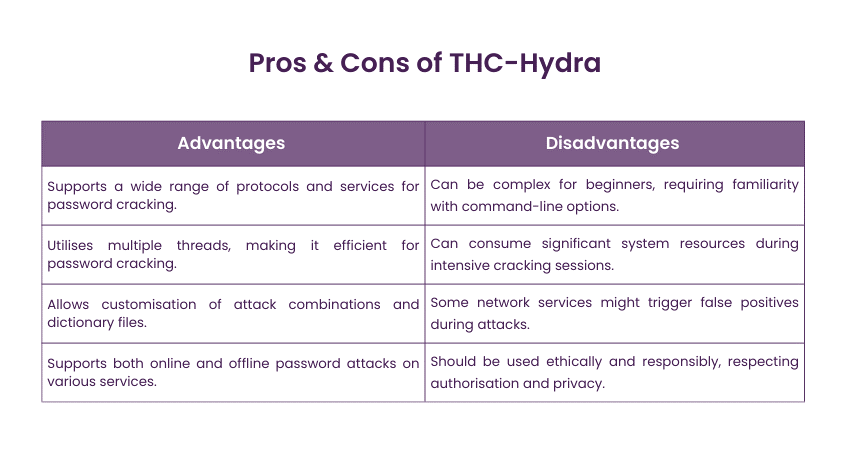
14) THC-Hydra
THC-Hydra (also known as Hydra) is a fast and flexible password-cracking tool that supports numerous network protocols and attack modes. Although primarily used for brute force attacks, it can be integrated into social engineering campaigns to test the strength of passwords and assess an organisation's susceptibility to credential-based attacks.
Key Features:
a) Fast and flexible password-cracking tool
b) Supports numerous protocols for brute force attacks
c) Customisable dictionaries and attack combinations
d) Multi-threaded for efficient password cracking
Learn the intricacies of tools used for Penetration Testing with our Tools and Techniques for Penetration Testing - join now!
15) OWASP SAP
OWASP SAP (Zed Attack Proxy) is a commonly used open-source tool for finding web application vulnerabilities. Its user-friendly interface and active community support make it a preferred choice for those new to web application security testing.
Key Features:
a) Web application security scanner and proxy
b) Intercepting and modifying web traffic
c) Automated and manual testing of web applications
d) Scans for various vulnerabilities like XSS, SQL injection
16) Cain and Abel
Cain and Abel is a multifunctional network analysis and password recovery tool. It supports several network protocols and attack methods, including ARP poisoning, brute force attacks, and dictionary attacks. While primarily used for educational and research purposes, Cain and Abel offer valuable insights into network vulnerabilities.
Key Features:
a) Multipurpose tool for network security assessment
b) Capable of recovering various types of passwords
c) Sniffs network traffic for password hashes and cracks them
d) Includes features for ARP poisoning and wireless network analysis
17) WiFite
WiFite is an automated script designed to target and attack wireless networks. It streamlines the process of identifying and exploiting vulnerabilities in Wi-Fi networks, making it particularly useful for beginners or those seeking a simple approach to wireless Penetration Testing.
Key Features:
a) Automated wireless network auditing tool
b) Cracks WEP, WPA, and WPS keys
c) Supports multiple wireless adapters and attack methods
d) Useful for assessing the security of wireless networks
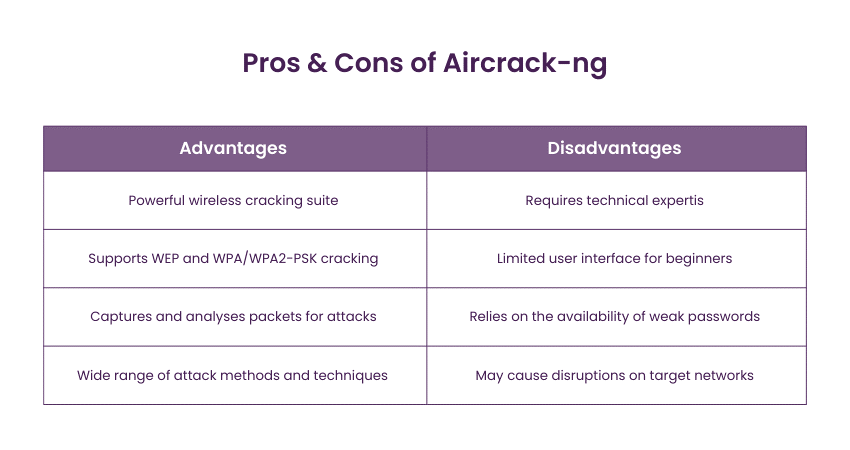
18) Aircrack-ng
Aircrack-ng is a versatile set of tools used for auditing wireless networks' security. Aircrack-ng's suite includes tools for packet capture, monitoring, and analysis, enabling security professionals to assess the security of wireless networks. It's a valuable tool for identifying weak encryption settings and potential vulnerabilities in Wi-Fi networks.
Key Features:
a) Wireless network cracking suite
b) Supports WEP and WPA/WPA2-PSK encryption cracking
c) Captures packets and performs dictionary attacks
d) Assessing the security of wireless networks
19) Vega
Vega is an open-source web vulnerability scanner and testing platform. It provides a user-friendly interface for scanning web applications and identifying security issues. Vega supports various testing modules, including automated scanners, proxies, and analysis tools. Its extensibility through plugins makes it a versatile tool for both beginners and experienced testers.
Key Features:
a) Scans for SQL injection, cross-site scripting (XSS), and more
b) Provides a comprehensive report of vulnerabilities found
c) Suitable for both manual and automated security testing
20) Wapiti
Wapiti is a command-line tool for identifying vulnerabilities in web applications. It performs black-box testing by analysing the response of web applications to various payloads and input data. Wapiti's modular architecture allows for flexibility in selecting specific vulnerability checks, making it suitable for tailored testing scenarios.
Key Features:
a) Web application vulnerability scanner
b) Identifies vulnerabilities like SQL injection and XSS
c) Audits both static and dynamic web pages
d) Generates reports with detailed information and recommendations
21) WebScarab
WebScarab is a Java-based tool focused on web application security. It acts as a proxy between the user and the application, allowing security professionals to intercept, modify, and analyse HTTP and HTTPS traffic. WebScarab provides modules for various tasks, including parameter manipulation, session tracking, and vulnerability scanning.
Key Features:
a) Monitors and manipulates web traffic between a browser and server
b) Helps identify vulnerabilities and security issues
c) Supports both manual and Automated Testing
22) Reaver
Reaver is a widely used tool designed for attacking WPS-enabled wireless routers and recovering WPA/WPA2 passphrases. It exploits the WPS (Wi-Fi Protected Setup) protocol vulnerabilities to obtain the Wi-Fi credentials.
Key Features:
a) Wireless Network Penetration Testing tool
b) Exploits WPS vulnerabilities in WPA/WPA2 networks
c) Automatically recovers WPA/WPA2 passphrases
d) Targets the weaknesses in Wi-Fi Protected Setup (WPS)
23) Kismet
Kismet is a versatile wireless network detector, sniffer, and intrusion detection system. It passively monitors wireless traffic, capturing packets from nearby Wi-Fi networks. Kismet provides insights into SSIDs, MAC addresses, encryption methods, and more.
Key Features:
a) Wireless network detection and intrusion detection system
b) Scans for hidden and non-beaconing networks
c) Identifies and tracks wireless devices and their activities
d) Useful for monitoring Wi-Fi traffic and identifying threats
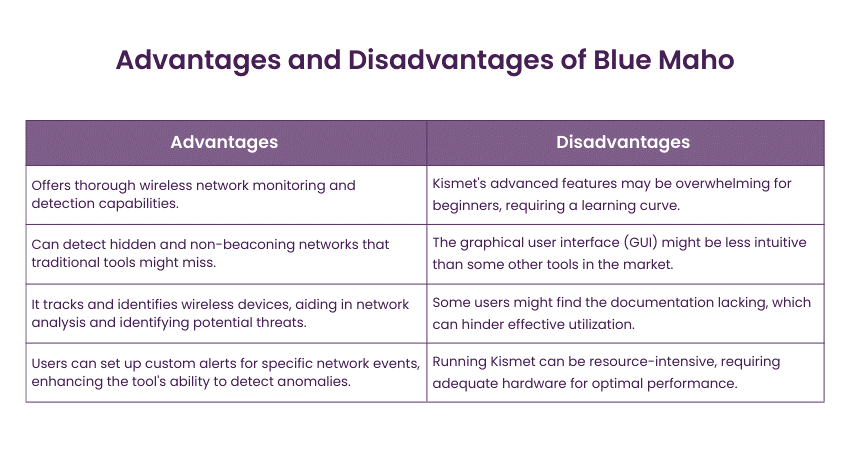
24) BlueMaho
BlueMaho is a specialised tool that focuses on Bluetooth security testing. It allows Penetration testers to discover and exploit vulnerabilities in Bluetooth-enabled devices like phones, headsets, and IoT devices.
Key Features:
a) Bluetooth Penetration Testing Tool
b) Targets Bluetooth-enabled devices for security assessments
c) Collects information, exploits vulnerabilities, and conducts attacks
d) Demonstrates the risks associated with insecure Bluetooth devices
25) Social-Engineer Toolkit (SET)
The Social Engineer Toolkit (SET) is a powerful framework designed for social engineering attacks. It automates a wide range of attack vectors, including phishing, credential harvesting, and malicious USB attacks. SET enables Penetration Testers to craft convincing social engineering campaigns by generating phishing emails, malicious websites, and other lures.
Key Features:
a) Framework for simulating social engineering attacks
b) Automate phishing, credential harvesting, and more
c) Demonstrates vulnerabilities related to human behaviour
d) Raises awareness about social engineering risks
26) Intruder
Intruder is a powerful vulnerability scanner designed to find Cybersecurity weaknesses in your digital estate, providing detailed risk explanations and helps with their remediation before a breach can occur. It offers an automated approach to Penetration Testing, making it an ideal solution for companies of any size.
Featuring an extensive array of over 11,000 security checks, Intruder delivers enterprise-grade vulnerability scanning capabilities accessible to all users. Its checks encompass the detection of misconfigurations, missing patches, and prevalent web application vulnerabilities such as SQL injection and cross-site scripting.
It helps you save time by prioritising results based on their relevance and conducts proactive scans to identify the latest vulnerabilities, ensuring proactive defence against potential threats. Intruder also integrates seamlessly with all the major cloud providers as well as apps and integrations like Slack and Jira.
27) Astra
Astra's Pentest offers a comprehensive Penetration Testing solution inspired by hacker techniques, combining an intelligent automated vulnerability scanner with detailed manual Penetration Testing conducted by security experts.
Astra presents an engineer-friendly Pentest dashboard designed for visualising vulnerabilities, assigning them to team members, and fostering collaboration with security experts. The recently introduced AI-powered Astranaut Bot provides engineers with contextual insights to aid in resolving vulnerabilities effectively.
Here are some of the features of Astra Pentest:
a) Scans progressive web apps and single-page apps
b) Scan behind logged-in pages
c) Schedule automated scans for continuously scanning your application for vulnerabilities every time you release new code
d) Intensive remediation support
e) Publicly verifiable pentest certificate
Unlock the power of Cybersecurity – register in our Ethical Hacking and Penetration Testing Training today!
28) John the Ripper
John the Ripper is another notable password-cracking tool compatible with various environments, with a primary focus on UNIX systems. Renowned for its exceptional speed, it stands out as one of the swiftest tools in its category.
An exciting feature of John the Ripper is its provision of password hash and strength-checking code, which can be seamlessly integrated into custom software or code, adding a unique aspect to its functionality. The tool is available in both free and pro versions, and you can access it by visiting their website.
29) Invicti
Invicti stands out as an exact automated scanner capable of uncovering vulnerabilities like SQL Injection and Cross-site Scripting within web applications and web APIs. What sets Invicti apart is its distinctive ability to validate identified vulnerabilities, ensuring they are genuine and not false positives.
With this capability, users can save valuable time that would otherwise be spent manually verifying identified vulnerabilities post-scan completion. It is available on Windows software and as an online service; Invicti offers flexibility in its deployment options, catering to varied user preferences and needs.
30) Hexway
Hexway offers users two self-hosted workspaces tailored for Penetration Testing (PTaaS) and vulnerability management. These environments are designed to streamline and centralise data from pentesting tools such as Nmap, Nessus, Burp, and Metasploit, enabling fast and efficient workflows.
Hexway caters to pentesters who recognise the importance of time efficiency, which is why its platform, Hive, have a comprehensive toolkit for handling security data and delivering real-time work results.
Some of its key features are:
a) Integrations with tools (Nessus, Nmap, Burp, etc.)
b) Continuous scanning
c) Customer support
d) Checklists & pentest methodologies
e) All security data in one place
31) Zed Attack Proxy (ZAP)
ZAP is a fully free web application scanner and security vulnerability finder. It offers a comprehensive range of features including proxy intercepting capabilities, various scanners, and spiders.
32)Retina
Unlike specific applications or servers, Retina focuses on assessing the entire environment within a company or firm. Delivered as a comprehensive package known as Retina Community, this commercial product serves as a vulnerability management tool rather than a Penetration Testing solution. Its approach involves scheduled assessments and presenting detailed results to address security vulnerabilities effectively.
33) Canvas
CANVAS, developed by Immunity, is a popular tool boasting over 400 exploits and diverse payload options, making it valuable for various applications including web applications, wireless systems, and networks. It has a command-line and GUI interface that works best on Linux, Apple Mac OS X, and Microsoft Windows.
Conclusion
Penetration Testing Tools are indispensable assets in identifying and addressing vulnerabilities before malicious actors can exploit them. From commercial solutions to free and open-source options, the range of tools available caters to different testing needs. Incorporating these 25 best Penetration Testing Tools into your security methods can boost your defences and protect your digital assets against emerging cyber risks.
Enhance your cybersecurity skills with our Automation and Penetration Testing Course. Register now!
Frequently Asked Questions

A Penetration Testing tool is software designed to simulate cyberattacks on computer systems, networks, or applications to identify security vulnerabilities. It helps assess the strength of a system's defences by attempting to exploit weaknesses, enabling organisations to proactively address and mitigate potential security risks before they are exploited by malicious actors.

Different types of penetration testing include Network Penetration Testing, Web Application Penetration Testing, Mobile Application Penetration Testing, Wireless Network Penetration Testing, and Social Engineering Penetration Testing. Each type focuses on assessing specific areas of an organisation's security infrastructure to identify vulnerabilities and assess overall security posture.

The Knowledge Academy takes global learning to new heights, offering over 30,000 online courses across 490+ locations in 220 countries. This expansive reach ensures accessibility and convenience for learners worldwide.
Alongside our diverse Online Course Catalogue, encompassing 17 major categories, we go the extra mile by providing a plethora of free educational Online Resources like News updates, Blogs, videos, webinars, and interview questions. Tailoring learning experiences further, professionals can maximise value with customisable Course Bundles of TKA.

The Knowledge Academy’s Knowledge Pass, a prepaid voucher, adds another layer of flexibility, allowing course bookings over a 12-month period. Join us on a journey where education knows no bounds.

The Knowledge Academy offers various Automation & Penetration Testing Courses, including Tools and Techniques for Penetrating Testing, Fundamentals of Test Automation etc. These courses cater to different skill levels, providing comprehensive insights into Cyber Security Skills.
Our IT Security & Data Protection Blogs covers a range of topics related to Fundamentals of Test Automation, offering valuable resources, best practices, and industry insights. Whether you are a beginner or looking to advance your IT skills, The Knowledge Academy's diverse courses and informative blogs have you covered.
Upcoming IT Security & Data Protection Resources Batches & Dates
Date
 Tools and Techniques for Penetrating Testing
Tools and Techniques for Penetrating Testing
Thu 1st Jan 1970







 Top Rated Course
Top Rated Course


 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


