We may not have the course you’re looking for. If you enquire or give us a call on +44 1344 203 999 and speak to our training experts, we may still be able to help with your training requirements.
We ensure quality, budget-alignment, and timely delivery by our expert instructors.

Ever felt like your computer has a mind of its own, opening strange ads or slowing down for no apparent reason? It might not be a ghost in the machine, but something far more dangerous. In the vast digital wilderness, countless Types of Malwares are lurking, ready to pounce on unsuspecting users.
Join us as we uncover the dark side of the digital realm, exploring the Types of Malwares and the damage they can inflict. We'll assist you through the treacherous terrain of cyber threats and arm you with the strategies you need to keep your devices and data safe. Ready to outsmart the hackers and reclaim your digital peace of mind? Let’s dive in!
Table of Contents
1) What is Malware?
2) What Does Malware Do?
3) Types of Malware
4) Benefits of Detecting and Removing Malware
5) Drawbacks of Detecting and Removing Malware
6) How to Prevent Malware Attacks?
7) Conclusion
What is Malware?
Malicious software, or Malware, is designed to exploit or damage networks, services, or devices. Cybercriminals use Malware to disrupt systems, steal sensitive data, or gain unauthorised access. Each type of Malware aims to compromise the target's security and functionality, with varying methods of infection and impact.
Protection against Malware includes:
a) Using antiMalware software
b) Keeping computers and systems updated
c) Enabling firewalls
d) Practicing safe browsing habits
e) Using strong passwords
f) Regularly backing up important data
What Does Malware Do?
Malware can have a wide range of effects, depending on its type and the intentions of its creator. Commonly, Malware is designed to:
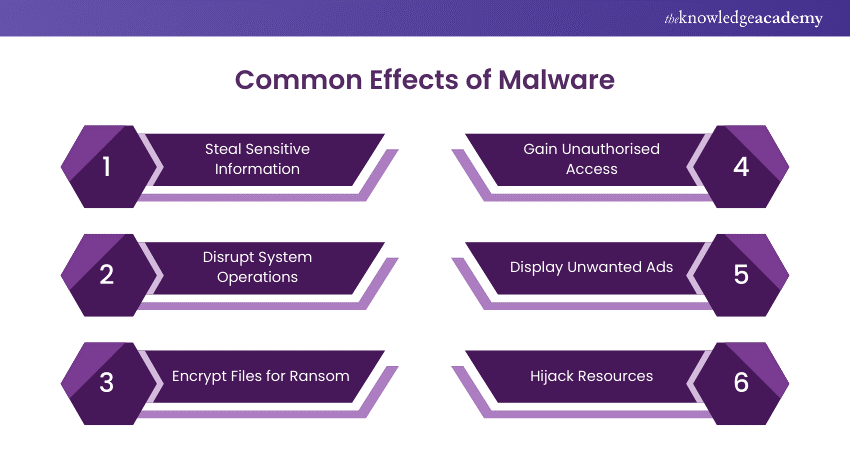
1) Steal Sensitive Information:
Spyware and keyloggers collect and send private information, like credit card details and passwords, to hackers.
2) Disrupt System Operations:
Worms and viruses can slow down or crash systems by taking resources, deleting files, and affecting data.
3) Encrypt Files for Ransom:
Ransomware encrypts documents and asks for money for their release, which usually leads to permanent data loss if the ransom is not paid.
4) Gain Unauthorised Access:
Trojans create backdoors, allowing attackers to gain control and unauthorised access to the infected device.
5) Display Unwanted Ads:
Adware bombards users with ads, potentially redirecting them to malicious sites that can further compromise their systems.
6) Hijack Resources:
Cryptojacking software quietly extracts cryptocurrency using your system's CPU and GPU, decreasing performance and raising costs related to energy.
Protect your organisation from cyber attacks – start your journey with our Cyber Security Awareness Course today!
Types of Malware
Here are the various Types of Malware you need to know, each posing different threats to your digital security.
1) Spyware
Spyware is a type of harmful software that secretly collects information about users’ activities without their knowledge or consent. This consists of sensitive data such as passwords, PINs, payment information, and personal messages.
Spyware isn’t limited to desktop browsers; it can also operate within critical apps or on mobile phones. Even if the stolen data isn’t highly sensitive, the presence of spyware can degrade system performance and erode productivity across an organisation.
Spyware Example:
DarkHotel is a notable example of spyware. It targeted business and government leaders using hotel Wi-Fi and employing various types of Malware to gain access to the systems of specific high-profile individuals. Once access was obtained, keyloggers were installed to capture passwords and other sensitive information from the targets.
2) Fileless Malware
Fileless Malware operates without installing any software initially. Instead, it modifies files that are native to the Operating System (OS), such as PowerShell or WMI. Because the Operating System recognies these altered files as legitimate, antivirus software often fails to detect fileless attacks. Due to their stealthy nature, these attacks are up to ten times more effective than traditional Malware attacks.
Fileless Malware Example:
Astaroth is a notable example of a fileless Malware campaign. It spammed users with links to a .LNK shortcut file. When users downloaded the file, it launched a WMIC tool along with several other legitimate Windows tools. These tools downloaded additional code that executed only in memory, leaving no trace that could be detected by vulnerability scanners. The attacker then downloaded and executed a Trojan, which collected credentials and transmitted them to a website.
3) Cryptojacking
Cryptomining, the process of verifying blockchain transactions, is highly profitable but demands significant processing power. Miners earn rewards for each validated transaction.
Malicious cryptomining, or cryptojacking, allows attackers to exploit an infected device’s resources such as electricity and computing power for verification. This exploitation causes performance degradation and financial loss.
Cryptojacking Example:
Coinhive was a well-known cryptojacking Malware that used web browsers to mine Monero cryptocurrency without the user's permission, resulting in important problems with performance and increasing electricity expenses.
4) Wiper Malware
A wiper is a type of Malware designed solely to erase user data irrecoverably. Wipers are deployed to disrupt computer networks in both public and private sectors. Threat actors also use wipers to eliminate traces of their intrusion, hindering the victim’s ability to respond effectively.
Wiper Malware Example:
On January 15, 2022, Malware known as WhisperGate targeted Ukrainian entities. This attack involved three components: a malicious bootloader that corrupted local disks, a Discord based downloader, and a file wiper. The attack coincided with the defacement of multiple Ukrainian government websites.
5) Adware
Adware tracks a user's browser history in order to decide which advertisements to display. Adware, which is like spyware, does not install software on the user's computer or log passwords. The main risk of adware is the loss of user privacy.
Data obtained by adware is combined with other information about the user's internet activities to generate an extensive profile. This data may be used or sold to advertisers without the user's consent.
Adware Example:
In 2017, adware known as Fireball infected 250 million computers and devices. It hijacked browsers to change default search engines and track web activity. Beyond being a nuisance, Fireball had the potential to execute remote code and download malicious files, making it a significant threat.
6) Worms
Worms take advantage of weaknesses in Operating Systems to break into networks. They can infiltrate through hidden software backdoors, security flaws, or even an infected flash drive.
Once within a system, these worms can be weaponised by hackers. They might use them to conduct DDoS attacks, steal critical information, or even launch ransomware assaults. Each of these activities can result in considerable harm and disruption.
Worms Malware Example:
Stuxnet, likely developed by US and Israeli intelligence, aimed to disrupt Iran’s nuclear program. It was introduced into Iran’s network via a flash drive. Although the environment was air-gapped, Stuxnet managed to escape its target network. Once in the wild, it spread aggressively but caused little damage, as its primary function was to interfere with industrial controllers managing uranium enrichment.
7) Viruses
A computer virus infects devices and replicates itself across systems, requiring human intervention to spread. Users often download the malicious code via malicious advertisements or phishing emails, allowing the virus to propagate throughout their systems. Viruses can modify computer functions and applications, copy, delete, and exfiltrate data, encrypt data for ransomware attacks, and carry out DDoS attacks.
Viruses Malware Example:
The Zeus virus, first detected in 2006, remains in use by threat actors today. It is employed to create botnets and as a banking Trojan to steal victims’ financial data. In 2011, Zeus’s creators released the Malware’s source code, enabling the development of updated and more dangerous versions of the original virus.
8) Rootkits
A rootkit is a software that allows malicious actors to remotely control a victim's computer with full administrator privileges. Rootkits can be introduced into apps, kernels, hypervisors, and firmware. They propagate through phishing, malicious attachments, malicious downloads, and infected shared drives. Rootkits can potentially hide additional Malware, such as keyloggers.
Rootkit Malware Example:
Zacinlo attacks devices when users install a fake VPN application. Once installed, it performs a security sweep to remove other Malware. Then, it opens invisible browsers to interact with content like a human, helping it evade behavioural analysis. Zacinlo’s payload involves clicking on ads in invisible browsers, committing advertising click fraud and earning commissions for the attackers.
9) Keyloggers
A keylogger is a kind of spyware that tracks and records user activities, frequently collecting every keystroke. While keyloggers can be used lawfully, such as to monitor employees or keep track on children's internet activity, they are frequently misused for malicious reasons.
When utilised by cybercriminals, they have the potential to steal passwords, financial information, and other sensitive data. These harmful keyloggers often find their way into systems through phishing emails, social engineering tricks, or malicious downloads.
Keylogger Example:
Olympic Vision is a keylogger that targets businessmen in the US, Middle East, and Asia for Business Email Compromise (BEC) attacks. It spreads through spear-phishing and social engineering, allowing attackers to steal data and monitor transactions.
10) Bots/Botnets
Bots are software applications that perform automatic operations when given a command. Bots are employed for good purposes, such as crawling search engines, but they can also be used illegally as Malware that propagates itself and links to a central server.
Bots are often used in large numbers to create a botnet, a network of bots that launch broad, remotely-controlled attacks like DDoS attacks.
Botnet Example:
Echobot, a variant of the infamous Mirai, targets a wide range of IoT devices by exploiting over 50 different vulnerabilities. It also includes attacks for Oracle WebLogic Server and VMware's SD-WAN networking software, as well as checks for unpatched legacy systems. Malicious actors can use Echobot to launch DDoS attacks, disrupt supply chains, steal sensitive information, and conduct corporate sabotage.
11) Mobile Malware
Mobile malware attacks have seen a significant increase recently. How to Know if Your Phone is Hacked is becoming a crucial concern as these threats are as diverse as those targeting desktops, including Trojans, ransomware, advertising click fraud, and more. They spread through phishing and malicious downloads, particularly impacting jailbroken phones that lack original system protections.
Mobile Malware Example:
Triada is a rooting Trojan that was introduced into the supply chain, causing millions of Android devices to ship with the Malware pre-installed. Triada gains access to sensitive areas of the Operating System and installs spam apps that display ads, sometimes replacing legitimate ads. When users click on these unauthorised ads, the revenue goes to Triada’s developers.
12) Trojan Horse
A Trojan Horse malware is harmful software that appears genuine to users. Trojans use social engineering techniques to infiltrate devices. Once inside, the Trojan’s payload—malicious code—is installed to facilitate the exploit. Trojans provide attackers with backdoor access to a device, enabling keylogging, virus or worm installation, and data theft.
Remote Access Trojans (RATs) allow attackers to take control of an infected device. Attackers can then use the infected device to spread the RAT to other devices, creating a botnet.
Trojan Example:
Emotet, first discovered in 2014, is a notable Trojan. Despite a global takedown in early 2021, attackers have rebuilt Emotet, which continues to help threat actors steal victims’ financial information.
Develop advanced fraud detection strategies with our Fraud Analytics Course and start building a secure future today!
Benefits of Detecting and Removing Malware
Here are the benefits of detecting and removing Malware, which enhances the security and efficiency of systems for both individuals and organisations:
a) Improved Security: Detecting and removing Malware enhances system security and reduces the risk of future infections.
b) Prevent Data Loss: Removing Malware protects important files and information from being lost or corrupted.
c) Protect Reputation: Eliminating Malware helps safeguard a company’s reputation by preventing potential harm to its image and brand.
d) Increased Productivity: Removing Malware can improve system efficiency and boost productivity for both individuals and organisations.
Drawbacks of Detecting and Removing Malware
Here are the drawbacks associated with detecting and removing Malware:
a) Time-consuming: The process can be lengthy and needs specialised tools and expertise.
b) Cost: Antivirus software and other necessary tools can be expensive for both individuals and organisations.
c) False Positives: Detection tools can sometimes produce false positives, causing unnecessary alarm and inconvenience.
d) Difficulty: Malware is constantly evolving, making detection and removal challenging and requiring specialised knowledge.
e) Risk of Data Loss: Some Malware removal tools can inadvertently cause data loss or system instability.
Become a Certified Cyber Security Professional to safeguard digital environments with our Certified Cyber Security Professional (CCS-PRO) Course. Sign up now!
How to Prevent Malware Attacks?
While complete protection from cybercriminals is impossible, companies can take several measures to mitigate or prevent Malware attacks, including:
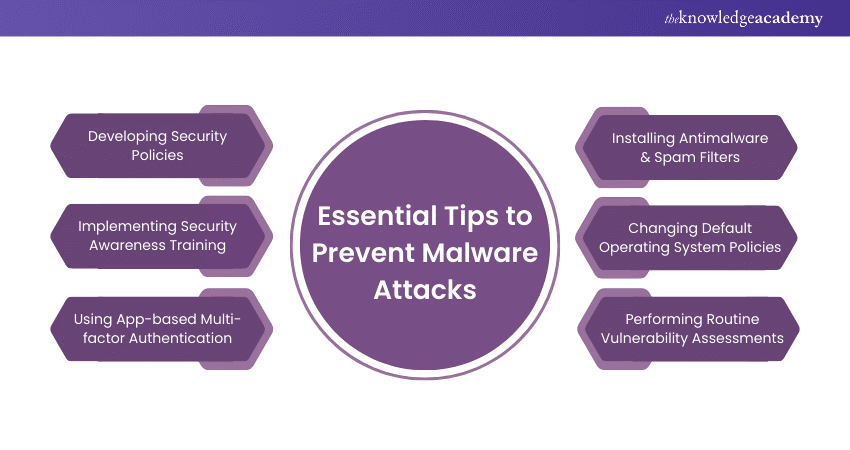
1) Developing Security Policies: Provide a roadmap for employees, detailing actions, timing, and access. Examples include Social Engineering Awareness, Server Malware Protection, Software Installation, and Removable Media Policies.
2) Implementing Security Awareness Training: Invest in training to save money lost to cyber attacks. Involves baseline testing, user training, phishing campaigns, and reporting results.
3) Using App-based Multi-factor Authentication: Prevent 99.9% of automated Malware attacks on Windows systems. Prefer app-based or hardware MFA over SMS-based MFA.
4) Installing Antimalware & Spam Filters: Add protections to mail servers as part of a defence-in-depth approach. Balance blocking malicious traffic and allowing legitimate traffic.
5) Changing Default Operating System Policies: Improve default settings, such as password history and age, to enhance security.
6) Performing Routine Vulnerability Assessments: Use tools like Nessus to scan ports, analyse protocols, and map networks. Display vulnerabilities and their severity in a dashboard.
Step into the world of Cyber Security by mastering Malware Analysis Training to defend your systems and enhance your expertise!
Conclusion
In a world where digital threats are constantly arising, understanding the Types of Malware and the distinction between Malware vs Virus is crucial for protecting your data and devices. By staying informed and implementing robust security measures, you can safeguard your digital world and keep cybercriminals at bay. Stay alert, and keep your data safe.
Stay ahead of cyber threats with our Cyber Security Training. Sign up today!
Frequently Asked Questions
How Does Malware Collect Data?

The Malware collects data by:
a) Logging keystrokes
b) Capturing screenshots
c) Accessing files
d) Monitoring network traffic
e) Exploiting system vulnerabilities
f) Stealing passwords and credit card details
g) Extracting personal data
What are the Main Sources of Malware?

The main sources of Malware include
a) Malicious email attachments
b) Infected websites
c) Compromised software downloads
d) Phishing attacks
e) Infected USB drives
f) Social engineering tactics
g) Vulnerabilities in outdated software or OS
What are the Other Resources and Offers Provided by The Knowledge Academy?

The Knowledge Academy takes global learning to new heights, offering over 3,000 online courses across 490+ locations in 190+ countries. This expansive reach ensures accessibility and convenience for learners worldwide.
Alongside our diverse Online Course Catalogue, encompassing 19 major categories, we go the extra mile by providing a plethora of free educational Online Resources like News updates, Blogs, videos, webinars, and interview questions. Tailoring learning experiences further, professionals can maximise value with customisable Course Bundles of TKA.
What is The Knowledge Pass, and How Does it Work?

The Knowledge Academy’s Knowledge Pass, a prepaid voucher, adds another layer of flexibility, allowing course bookings over a 12-month period. Join us on a journey where education knows no bounds.
What are the Related Courses and Blogs Provided by The Knowledge Academy?

The Knowledge Academy offers various Cyber Security Training, including Malware Analysis Training, Certified Cyber Security Professional (CCS-PRO), Cyber Security Awareness and Fraud Analytics Training Course. These courses cater to different skill levels, providing comprehensive insights into Computer Worms.
Our IT Security & Data Protection Blogs cover a range of topics related to Malware Analysis, offering valuable resources, best practices, and industry insights. Whether you are a beginner or looking to advance your Cyber Security skills, The Knowledge Academy's diverse courses and informative blogs have got you covered.
Upcoming IT Security & Data Protection Resources Batches & Dates
Date
 Certified Cyber Security Professional (CCS-PRO)
Certified Cyber Security Professional (CCS-PRO)
Fri 23rd May 2025
Fri 22nd Aug 2025
Fri 5th Dec 2025






 Top Rated Course
Top Rated Course



 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


