We may not have the course you’re looking for. If you enquire or give us a call on +91 8037244591 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.

Cyber-attacks are a growing cause of concern for company owners today. A 2022 report stated that the UK's average cost of cyber security attacks was about £1,200. Nowadays, companies prioritize investing in Cybersecurity measures and professionals who can implement them, saving money and time.
One such security measure that companies follow is known as the Red Team and the Blue Team. They play a cardinal role in the pursuit of data protection and safeguarding company secrets, passwords, client data, and more. Let us try to understand the Red Team vs Blue Team agenda by dissecting their roles and responsibilities.
This blog explains the differences between the Red Team and Blue Team in Cyber security. These two teams help in protecting your company from cyber-attacks.
Table of contents
1) What is a Red Team?
a) How do Red Teams work?
b) Types of attacks initiated by the Red Team
2) What is a Blue Team?
a) How do Blue Teams work?
b) Defence schemes implemented by the Blue team
3) How do the teams work together?
4) Red Team and Blue Team: Benefits
5) Conclusion
Learn about the various forms of cyber-attacks and ways to evade them. Sign up for our Cyber Security Risk Management course now!
What is a Red Team?
The Red Team consists of security professionals who carry out procedures that help expose any security vulnerabilities within an organisation. They deploy complex attacks to detect discrepancies in the people and technology that contribute to the company's overall security.
Since their function is to simulate attacks, the team mainly comprises ethical hackers capable of an equivalent of breaking but in a virtual space. They work in offensive mode with the cardinal objective of strengthening their organisation's security walls.
How do Red Teams work?
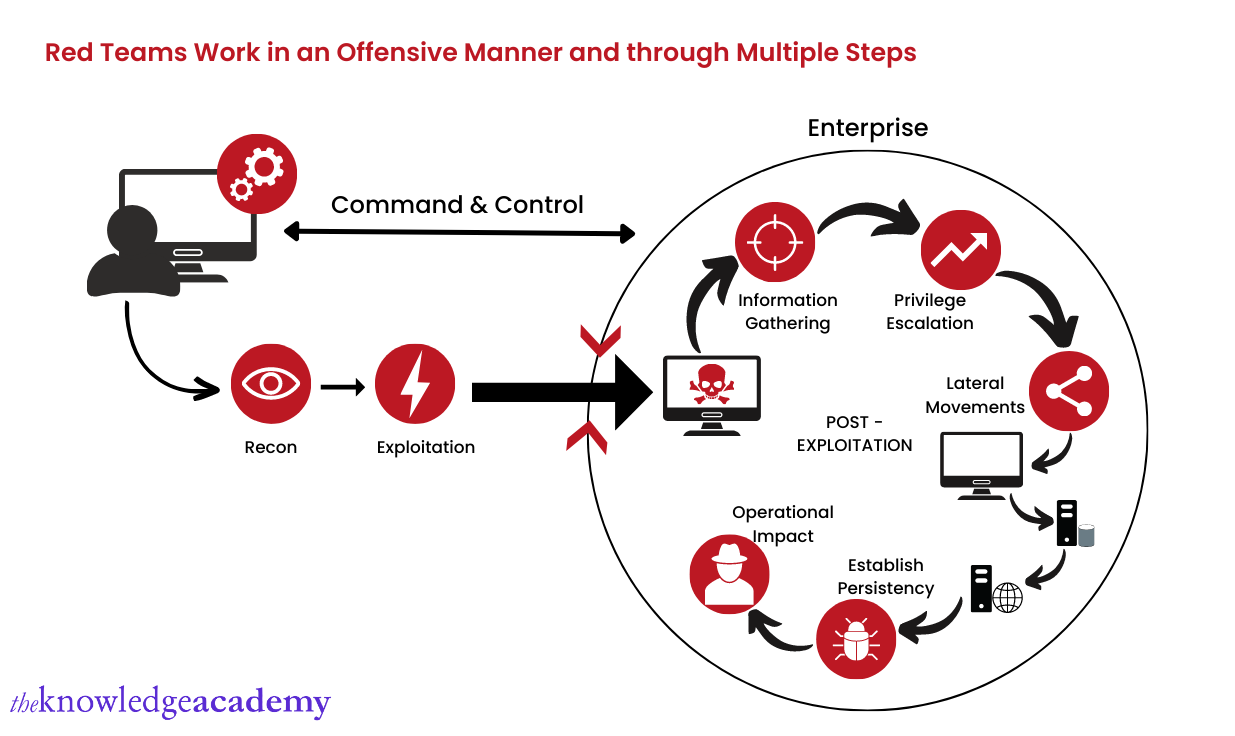
Red Teams are responsible for launching attacks to detect cracks and crevices in their company's Cybersecurity. They follow a specially devised set of steps to help them achieve their targets. Here are some of the basic steps they follow:
a) Examining possible risks: Their first order of business would include listing all the possible vulnerabilities to identify and address. The size of the matter can be anything ranging from major security flaws to tiny factors like passwords. The team tries to avoid as much insider information as possible to carry out the attacks in the most realistic manner.
b) Prioritising risks: Once they have gone through the possible threats, they must zero in on a specific one(s). The type of threats you might potentially face depends mainly on the industry you're working in. You can lose anything from your clients' credentials to integral company secrets.
c) Attack: The Red Team, after deciding the number and types of attacks that are potential threats to the company, will launch attacks via various methods. Their attacks remain active until or unless they have been successful or detected.
d) Feedback: The final phase is to record the observations that sprouted due to this attack. The report must contain every minor detail of the attack. This includes the entire plan of attack, mode of execution, number of faults found, the kind of defences that worked or could've potentially worked, and more.
Increase your understanding of cyber-attacks and learn the various methods to fight them. Sign up for our Cyber Security Training course now!
Types of attacks initiated by the Red Team
The Red Team uses different ways to instigate attacks to discover weaknesses in the system. After an initial assessment of the possible threats, they extrapolate the findings with all the existing adversary tactics, techniques, and procedures (TTPs). The Red Team achieves its goals by searching for cracks in the current security framework through methods like the ones listed below.
a) Penetration testing: One of the most commonly used modes of attack by the Red Team would be Penetration testing. Through this method, testers make use of software tools to try and gain access to a system or network.
b) Social engineering: Human error is one of the most common modes of data breach. Social engineering uses methods like email phishing that can break down physical security, to test the competence of company employees and security procedures. One of the main things this type of attack helps unveil is the extent to which employees follow the established security regulations. Social engineering helps reveal employees prone to make silly mistakes like giving up confidential data to unknown sources on the internet and more.
c) Card cloning: The concept of card cloning is pretty self-explanatory. It merely means to clone an employee's security card that can grant you access to a source of precious information. The card type can vary from users' credit cards to security personnel cards that give access to data-sensitive rooms like a server room.
d) Intercepting communication software tools: Internal and external communication is consistently high in a company. Thus, intercepting communication software tools can lead to a large-scale data breach. Tools such as packet sniffers help you read messages sent on the network and continue to formulate a cyber-attack.
e) Providing feedback for the Blue Team: After carrying out multiple attacks threatening virtual security, the Red Team has to provide detailed observations and feedback to the Blue Team. They must inform the Blue team about various findings for the best security results.
What is a Blue Team?
While the Red teams are responsible for launching attacks, the Blue Team is endowed to defend the company's Cybersecurity. The Blue Team comprises security professionals who are familiar with the company's security policies and can keep working on strengthening the existing defense methods, highlighting the importance of Cyber Security Essentials in fortifying organisational defenses.
They possess strong analytical skills that help in identifying potential threats. As the Red teams initiate attacks and the Blue team tries to fend them off, both teams contribute to understanding the weaknesses and strengths of the company's security system.
Learn to develop security requirements based on business goals by signing up for our Microsoft Cybersecurity Architect SC100 course now!
How do Blue teams work?
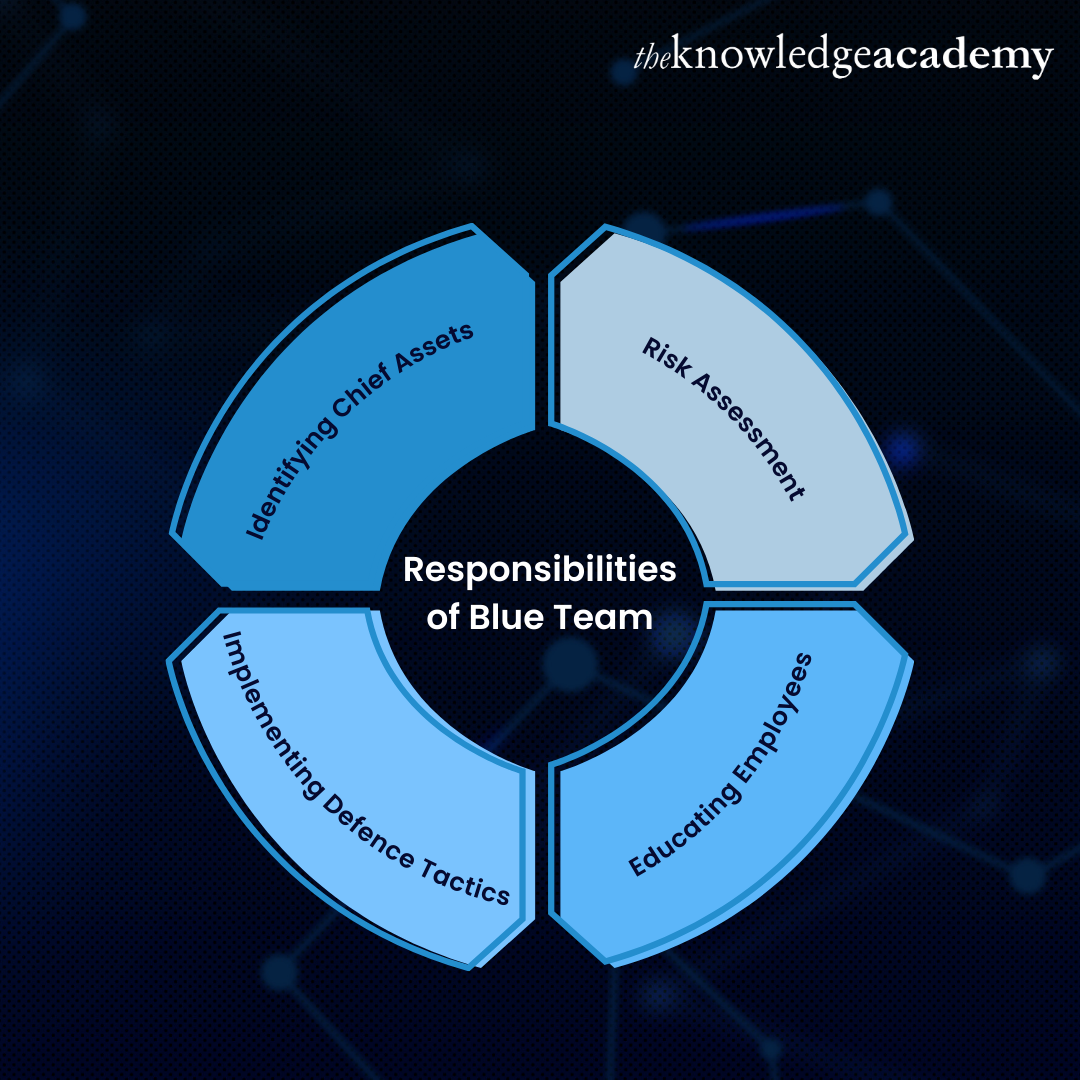
Blue teams are formed to conduct evaluations and provide techniques that contribute to sustaining an organisation's Cybersecurity and minimising corporate damage. The team can consist of people within the organisation or even belong to independent consultations. They work in multiple steps like follows:
a) Identifying chief assets: The Blue team's first step is identifying the critical assets they should protect. The significance of assets can vary depending on how their protection is important to the company and how their absence might affect it.
b) Risk assessment: After identifying your chief assets, the next step is to perform a risk assessment. This includes prioritising your threats, analysing security measures, planning for better measures, etc.
c) Educating employees: The Blue team is in charge of educating the employees on basic security procedures and cues to look for that can detect a potential cyber-attack. The significance of strong passwords is another crucial point communicated to them and sometimes implemented for the systems.
d) Implementing defence tactics: Once the major threat(s)has been identified, the Blue team plans the right defence tactic to avoid it. But the controls to be implemented must be approved by Senior management using a cost-benefit analysis. This allows the company to invest in Cybersecurity that is cost-effective and valuable to it.
Defence schemes implemented by the Blue team
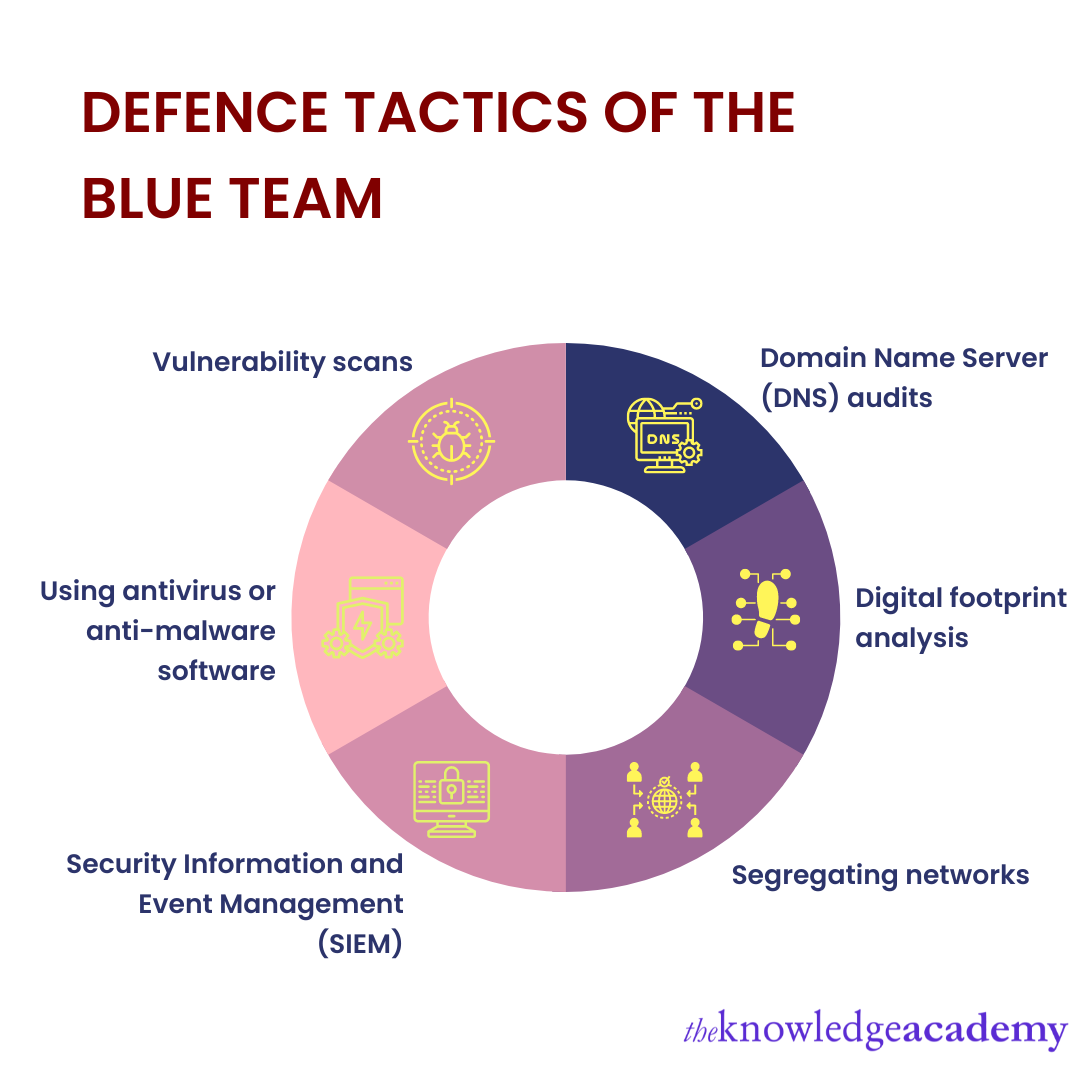
The Blue team implements different types of defence schemes that help strengthen security. They have the right to demand emergency firewall installations to prevent data access. Some of the exercises that help you deter potential cyber threats are as follows:
a) Domain Name Server (DNS) audits: One of the major exercises carried out by the Blue team includes performing Cyber Security Audits, such as DNS audits. It helps avoid stale DNS issues, halting phishing attacks and DNS web attacks.
b) Digital footprint analysis: A digital footprint contains all cues that help map out your online activity. Conducting digital footprint analyses is one of the defence tactics that helps the Blue team keep track of possible security breaches and fix them.
c) Segregating networks: Network segregation is the process of separating crucial network elements from the comparatively less important ones to strengthen security. Segregating networks and ensuring their correct arrangement is an important exercise.
d) Security Information and Event Management (SIEM): Implementing SIEM solutions can increase your threat detection rate and provide a vast range of helpful data. They are also useful for generating faster response times for cyber threats.
e) Using antivirus or anti-malware software: The Blue team uses basic antivirus or anti-malware software to detect and/or delete potential malware that threatens security. Worms are one of the various forms in which harmful software presents itself. Keeping your antivirus or anti-malware software updated and functional is a powerful defence against such threats.
f) Vulnerability scans: Reports in the past decade have shown the presence of at least one vulnerability in 76% of all applications. Conducting routine vulnerability scans is a good practice for determining security faults within your system, application, or network. With the help of consistent scans, it is easy to assess an organisation’s stance on its security and manage the problem before it hits the roof.
How do both the teams work together?

Both the Red and Blue team in Cyber Security always work together to produce significant data, with the ultimate goal of strengthening Cybersecurity. The Red team, comprised of ethical hackers, is responsible for deploying attacks that can expose flaws in the company's Cybersecurity. The Blue team is responsible for defending against these advances and constantly upgrading security practices.
Both teams will be in sync with one another. The extent of information they share depends on the attack the Red Team is planning. If they wish to test their company's response to a 'legitimate' threat, the attack is carried out without informing the Blue team.
After both teams exercise their roles, they record all their observations and formulate a detailed report. Both their reports are detrimental to figuring out future steps that can strengthen your organisation's existing Cybersecurity and policies.
Red Team and Blue Team: Benefits
Organisations highly prefer the Red Team, and Blue Team approaches for maintaining security. Both teams provide valuable insights that can help strengthen security measures. Here are some of the benefits of this approach.
a) Helps to expose flaws
b) Improves Cybersecurity
c) Improves the skills of security professionals and employees in maintaining the security
d) Advocates the need for employees to stay vigil while handling sensitive data to mitigate human error
e) Strengthen network security
Conclusion
Implementing and maintaining Cybersecurity is an important step organisations are pushed to follow nowadays. Out of the numerous security measures available, the Red Team vs Blue Team approach is a handy tool for ensuring Cybersecurity. Hope this blog has helped explain what is Red Team and Blue Team in cyber security and their differences.
Learn about the potential threats a business can face and the different kinds of cyber-attacks present. Sign up for our Certified Cyber Security Professional (CCS - PRO) course now!
Frequently Asked Questions
Upcoming IT Security & Data Protection Resources Batches & Dates
Date
 Certified Cyber Security Professional (CCS-PRO)
Certified Cyber Security Professional (CCS-PRO)
Fri 21st Mar 2025
Fri 23rd May 2025
Fri 22nd Aug 2025
Fri 5th Dec 2025







 Top Rated Course
Top Rated Course






 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


