Hyderabad is situated along the Musi River, and is the capital city of Andhra Pradesh and Telangana. City of pearls as the city is otherwise known, as for its pearl and diamond trading centre, it is the fourth most populated city within India and is home to around 6.8 million people as well as having a metropolitan population of around 7.75 million. The city which was established in 1591 has two main land marks, which are the Golconda and the Charminar which represents the history of Hyderabad. There are eleven universities within Hyderabad, six of which are owned by the state, three are deemed universities and the other two are central universities. The universities and institutions include an English and Foreign Languages University, NIFT Hyderabad, University of Hyderabad, Tata Institute of Social Sciences, Indian School of Business, National Academy of Construction and IIT Hyderabad all of which offer a wide range of different courses. However before students go off to do a degree within technology, construction, social science, engineering or international management, students must complete secondary schools and colleges, which include the Indus world school, Modern High School, St George’s Grammar school, the Meridian school, as well as international schools such as the Chirec International school which offers education from pre-primary to secondary school and offers students the opportunity to gain A and O levels, CBSE, IGCSE and CBSE.
Free Wi-Fi
To make sure you’re always connected we offer completely free and easy to access wi-fi.








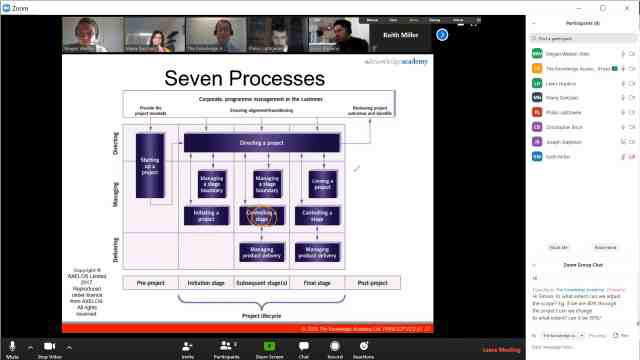
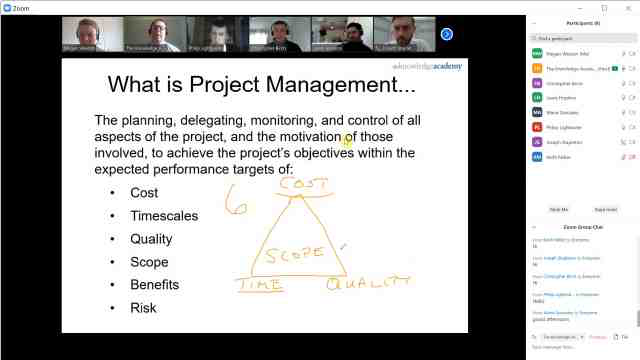



























 Back to course information
Back to course information




 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please

