We may not have the course you’re looking for. If you enquire or give us a call on +44 1344 203999 and speak to our training experts, we may still be able to help with your training requirements.
We ensure quality, budget-alignment, and timely delivery by our expert instructors.
For the data encryption pros or general tech enthusiasts, the Data Encryption Standard (DES) is a delightful blast from the past. Once reigning as the gold standard for encryption standard, DES was the go-to option for keeping information secure in the digital realm. But as technology evolved, so did the ingenuity of techniques to break its shield.
While the Data Encryption Standard is now considered outdated, it's importance as the forefather of modern encryption standards can't be denied. This blog dives deep into the story of DES, spotlighting all it offered to the digital landscape at its prime. So read on and get a glimpse of a groundbreaking era in Cryptography.
Table of Contents
1) Understanding Data Encryption Standard (DES)
2) Key Features of Data Encryption Standard (DES)
3) The Working Mechanism of Data Encryption Standard (DES)
4) How Does DES compare to Other Encryption Standards?
5) Implementing Data Encryption Standards in Your Organisation
6) Uses of Data Encryption Standard (DES)
7) Benefits of Data Encryption Standard (DES)
8) Drawbacks of the Data Encryption Standard (DES)
9) Conclusion
Understanding Data Encryption Standard (DES)
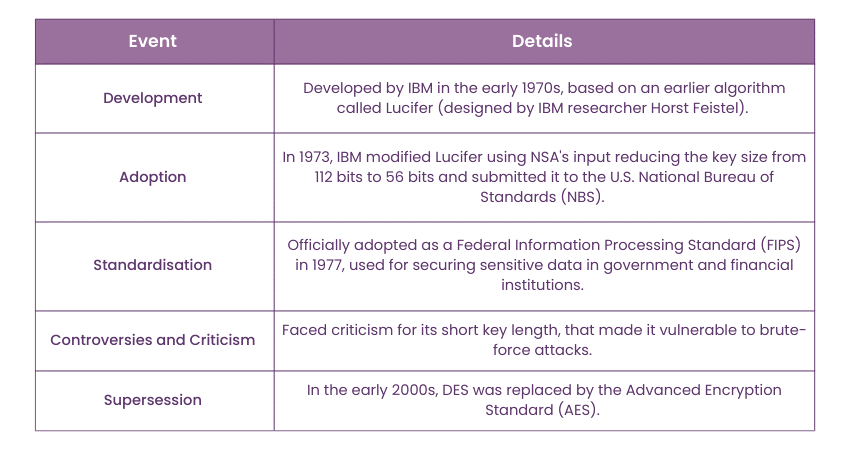
Data Encryption Standard (DES) is a now outdated symmetric key data encryption method. It was adopted in 1977 by government agencies to protect sensitive data and was officially retired in 2005. DES was the first encryption algorithm approved for public disclosure.
This move ensured its quick adoption by industries, including financial services, that needed strong encryption. Because of its simplicity, DES was also used in a variety of embedded systems, including smart cards, SIM cards, modems, routers and set-top boxes.
Key Features of Data Encryption Standard (DES)
DES has numerous distinctive features that contributed to its widespread utility:
1) Symmetric Key Encryption: DES uses the same key for encryption and decryption which must be kept secret to maintain the data's security.
2) Block Cipher: DES encrypts data in chunks rather than bit by bit. It processes data in fixed-size blocks of 64 bits.
3) 56-bit Key Length: The DES algorithm uses a 56-bit key, providing a standardised method for safeguarding digital communications.
4) Feistel Structure: DES operates on a Feistel network. This network divides the data block into two halves and processes them through multiple rounds of substitution and permutation.
The Working Mechanism of Data Encryption Standard (DES)
DES has played a significant role in securing information and systems. Though currently considered obsolete, understanding DES can still be beneficial as it's responsible for laying the groundwork for modern cryptology. The working mechanism of DES consists of processes such as encryption, decryption and key generation, which are explained below:
Encryption Process
The encryption process consists of the following steps:
1) Initial Permutation (IP): First, the plaintext data is subjected to a permutation that rearranges the bits to increase diffusion.
2) Round Function (F): DES uses 16 rounds of processing, and each round involves:
a) Expansion: Right half of the data block is expanded from 32 to 48 bits.
b) Key Mixing: The expanded right half is XORed by a subkey derived from the main key.
c) Substitution: The XORed result is passed through a series of substitution boxes, called S-boxes, that reduce the 48-bit block back to 32 bits.
d) Permutation: A permutation function scrambles the bits further.
3) Swapping Halves: Following each round, the two halves of the data block are swapped.
4) Final Permutation (FP): Following the final round, the data block is subjected to a final permutation that produces the ciphertext.
Decryption Process
The decryption process in DES is essentially the reverse of encryption that applies the same keys in reverse order and retrieves the original plaintext from the ciphertext.
Key Generation
The key generation process involves creating a 56-bit key from an original 64-bit key by removing every 8th bit. This key is then utilised in various stages of the encryption and decryption processes.
Looking to mitigate the risks of digital manipulation? Sign up for our Social Engineering Training!
How Does DES Compare to Other Encryption Standards?
DES was the most widely adopted encryption standards of its time, but more efficient and secure algorithms have overshadowed it since. Some of the significant encryption standards in use today include the following:
1) Advanced Encryption Standard (AES): This is a symmetric block cypher that employs the same key for the purposes of encryption and decryption. It is faster and more secure than DES, boasting key sizes of 128, 192, and 256 bits. AES is widely implemented worldwide in hardware and software development to encrypt sensitive data.
2) Rivest Shamir Adleman (RSA): This asymmetric encryption algorithm uses a pair of keys:
a) A public key for encryption
b) A private key for decryption
This makes RSA more secure than DES, as only the intended recipient with the private key can decrypt the information. RSA is typically used over the internet for secure communication between two parties.
3) Blowfish: It's a symmetric encryption algorithm that operates on 64-bit data blocks. It uses variable-length keys, making it far more secure and adaptable to diverse security requirements. Despite its age, Blowfish is still deemed a reliable encryption method.
Implementing Data Encryption Standards in Your Organisation
Businesses of all sizes need their sensitive data to be safeguarded from unauthorised access. Implementing data encryption standards can ensure the confidentiality and integrity of your data, whether stored in the cloud, on-premises, or transmitted over the internet. Here are the essential steps to implement data encryption standards in your organisation:
1) Evaluate Your Organisation's Data Security Requirements
Start by identifying the data types your organisation handles and the level of protection each type needs. You must consider factors such as industry standards, regulatory requirements, and the potential impact of data breaches on your business operations. This assessment will help you determine the right encryption standards and implementation methods.
2) Select Suitable Encryption Algorithms and Protocols
This step depends on your security needs. The Advanced Encryption Standard (AES) is a good choice for symmetric encryption for most organisations due to its performance and security. For secure communication between two parties, you can also opt for asymmetric encryption methods like Elliptic Curve Cryptography (ECC) or Rivest-Shamir-Adleman (RSA).
3) Deploy Encryption Tools and Solutions
Utilise encryption tools and solutions that support the algorithms and protocols you selected for your organisation. Many software and hardware vendors provide encryption solutions that integrate with existing applications and systems. Consider encryption key management solutions to store, manage, and rotate encryption keys for additional security.
4) Educate Staff on Encryption Best Practices
Your employees must be educated on the importance of data encryption and proper use of encryption tools. Training and awareness programs at regular intervals can help ensure that your staff adheres to encryption best practices and complies with internal and external policies.
5) Continuously Monitor and Update Encryption Strategies
Review and update your encryption strategies regularly to stay ahead of evolving threats and technological advancements. Continuous assessment of your encryption methods' effectiveness is essential.
Become an expert at identifying and mitigating digital threats with our comprehensive Cyber Security Risk Management Course - Sign up now!
Uses of Data Encryption Standard (DES)
DES was widely used in several domains, including:
1) Banking and Finance: DES helped in the protection of ATM transactions, secure online banking and electronic fund transfers (EFTs).
2) Government Communications: DES was important in securing sensitive communications and government data.
3) Commercial Applications: DES helped in ensuring data integrity and confidentiality in numerous commercial software and hardware systems.
Benefits of Data Encryption Standard (DES)
DES offered numerous benefits during its time, including the following:
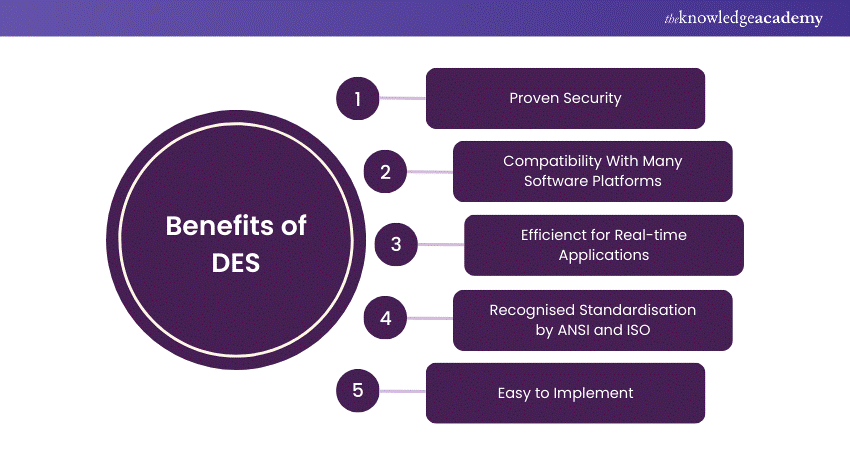
1) Standardisation: As a federally adopted standard, DES offered a uniform method for encryption, which simplified integration across various systems.
2) Simplicity: The block cipher structure and symmetric key approach made it relatively easy to implement and understand DES.
3) Widespread Adoption: Once DES was adopted by the National Institute of Standards and Technology (NIST), it ensured its use in diverse applications. These applications ranged from securing government communications to safeguarding financial transactions.
Drawbacks of the Data Encryption Standard (DES)
While DES was groundbreaking for its time, it possessed significant limitations that resulted in its eventual replacement:
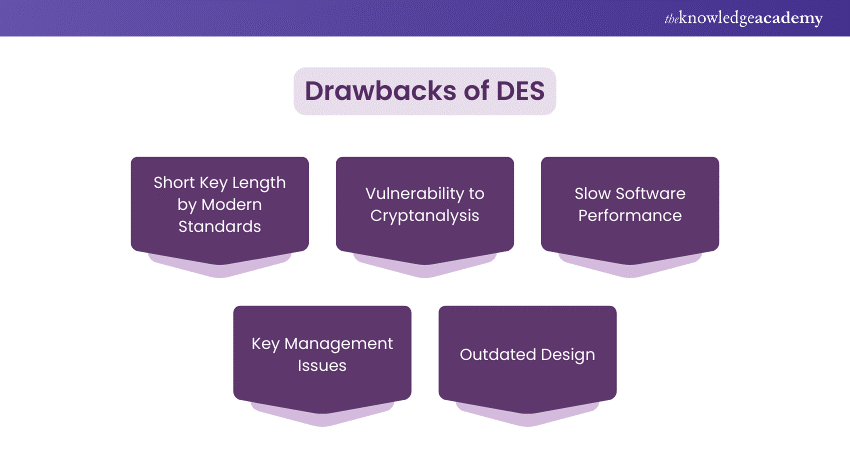
1) Key Length: The 56-bit key length is too short by modern standards, making DES susceptible to brute-force attacks.
2) Computational Power: Advancements in computational power have rendered DES insecure, because modern computers can quickly crack DES-encrypted data.
3) Replacement: In 2001, DES was succeeded by the AES standard, which offers longer key lengths and stronger security features.
Conclusion
In conclusion, the Data Encryption Standard (DES) played a vital groundbreaking role in the evolution of Cryptography and planted the seeds for modern encryption practices. Before the advent of modern methods such as AES, RSA and Blowfish, DES's 56-bit key found applications in modems, routers, SIM cards, financial services and more. The various aspects of DES, as explored in this blog, offer valuable insights into the foundations of data security.
Respond to cyber threats with confidence in our up-to-date Cyber Security Awareness Course - Sign up now!
Frequently Asked Questions
Which is the Most Recommended Encryption Standard?

Blowfish, Triple-DES algorithm and Advanced Encryption Standard (AES) algorithm are among the most recommended encrypted standards.
What are the Three Types of Encryption Standards?

The three main types of encryption standards are:
a) Symmetric Encryption: Examples include Advanced Encryption Standard (AES) and Triple Data Encryption Standard (3DES).
b) Asymmetric Encryption: Rivest-Shamir-Adleman(RSA) is one of the best examples.
c) Hashing: Examples include Secure Hash Algorithm (SHA) and Message Digest Algorithm 5 (MD5).
What are the Other Resources and Offers Provided by The Knowledge Academy?

The Knowledge Academy takes global learning to new heights, offering over 3,000 online courses across 490+ locations in 190+ countries. This expansive reach ensures accessibility and convenience for learners worldwide.
Alongside our diverse Online Course Catalogue, encompassing 19 major categories, we go the extra mile by providing a plethora of free educational Online Resources like News updates, Blogs, videos, webinars, and interview questions. Tailoring learning experiences further, professionals can maximise value with customisable Course Bundles of TKA.
What is The Knowledge Pass, and How Does it Work?

The Knowledge Academy’s Knowledge Pass, a prepaid voucher, adds another layer of flexibility, allowing course bookings over a 12-month period. Join us on a journey where education knows no bounds.
What are the Related Courses and Blogs Provided by The Knowledge Academy?

The Knowledge Academy offers various Cyber Security Courses, including the Cyber Security Awareness Course and the Fraud Analytics Training Course. These courses cater to different skill levels, providing comprehensive insights into Cyber Resilience Framework.
Our IT Security & Data Protection Blogs cover a range of topics related to data security, offering valuable resources, best practices, and industry insights. Whether you are a beginner or looking to advance your data protection skills, The Knowledge Academy's diverse courses and informative blogs have got you covered.
Upcoming IT Security & Data Protection Resources Batches & Dates
Date
 Introduction to System and Network Security
Introduction to System and Network Security
Fri 21st Mar 2025
Fri 16th May 2025
Fri 18th Jul 2025
Fri 19th Sep 2025
Fri 21st Nov 2025






 Top Rated Course
Top Rated Course



 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


