We may not have the course you’re looking for. If you enquire or give us a call on +44 1344 203999 and speak to our training experts, we may still be able to help with your training requirements.
We ensure quality, budget-alignment, and timely delivery by our expert instructors.

Imagine having the ability to uncover hidden treasures buried deep within the vast expanse of the internet, invisible to the average user. Welcome to the intriguing world of Google Dorking – a powerful technique that transforms you into a digital detective, revealing hidden files, sensitive data, and more with just a few clever search commands.
Whether you’re a Cyber Security enthusiast, an Ethical Hacker, or simply curious about mastering the art of advanced searches, this blog on Google Dorking is your gateway to exploring the internet’s hidden layers.
Table of Contents
1) What is Google Dorking?
2) How Does Google Dorking Work?
3) Google Dorking Techniques
4) Examples of Google Dorking
5) Search Operators and Commands
6) Risks Associated with Google Dorking
7) How to Prevent Google Dorking?
8) Conclusion
What is Google Dorking?
Google Dorking, also known as Google Hacking, involves using advanced search techniques to find information inaccessible through conventional search methods. You can uncover files, sensitive data, and other information that typically remains hidden from standard searches by using specific search operators.
Imagine Google as a vast library with millions of books (websites). Most people browse the shelves and pick up the most obvious books (conducting basic searches). However, a few know how to use a special magnifying glass (advanced search techniques) to read between the lines, discover secret messages, or uncover hidden compartments.
Just like a magnifying glass reveals hidden details, Google Dorking allows you to use clever search techniques to unearth valuable information that’s invisible to the average searcher.
How Does Google Dorking Work?
Google Dorking leverages advanced search operators to uncover hidden or sensitive information on websites indexed by Google. By using specific commands, such as "intitle:" to search within titles, "inurl:" to search within URLs, or "filetype:" to target specific file types like PDFs, users can refine their searches to reveal data often missed by regular search queries.
Key Points:
a) Advanced Search Operators: Commands like "intitle:", "inurl:", and "filetype:" help pinpoint specific information within Google’s vast index.
b) Targeted Searches: Combining these operators with relevant keywords allows users to filter search results and access data that might otherwise remain hidden.
c) Example Query: A search like filetype:pdf confidential could reveal confidential PDF documents that are inadvertently accessible online.
d) Cyber Security Application: Google Dorking is commonly used by Cyber Security professionals to identify security vulnerabilities, such as exposed login pages, directories, or sensitive files.
e) Ethical Considerations: While Google Dorking can be a powerful tool for web exploration, it can also be misused, leading to unauthorised access to sensitive data. Therefore, it's crucial to use this technique responsibly.
Google Dorking Techniques
If you want to dive deeper into search results and uncover information hidden from regular browsing, mastering a few specific Google Dorking techniques can make a significant difference. Here are some key methods:
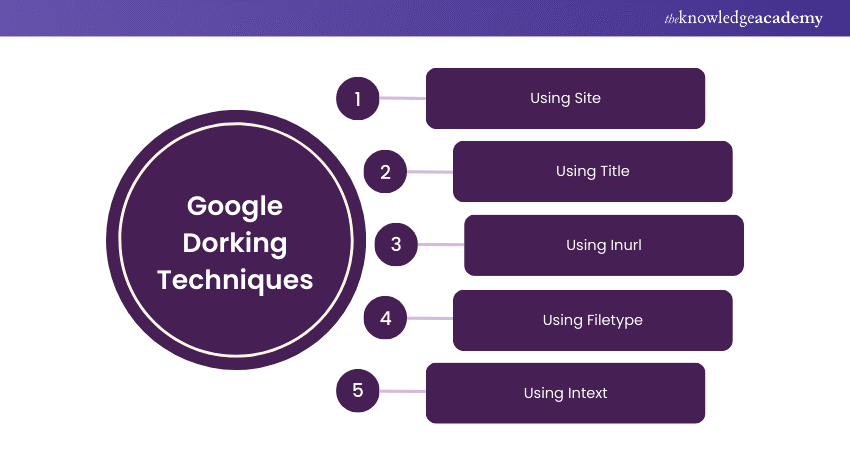
a) Site: This technique restricts your search to a specific website or domain. For example, using site:example.com will display results exclusively from "example.com."
b) Title: The "intitle:" command searches for specific keywords within the title of web pages. For instance, intitle:"login" can help locate pages with "login" in their titles, often leading to login portals.
c) Inurl: The "inurl:" command searches for keywords within URLs. For example, inurl:admin might reveal admin pages.
d) Filetype: This command searches for specific file types, such as PDFs or Excel sheets. For example, filetype:pdf confidential can uncover potentially sensitive PDF documents.
e) Intext: The "intext:" command searches for specific words within the content of web pages. For instance, intext:"password" could expose pages containing visible passwords.
By mastering these Google Dorking techniques, you can reveal data that regular searches might overlook, giving you a deeper understanding of what's accessible online.
Examples of Google Dorking
Understanding Google Dorking becomes clearer with practical examples that demonstrate its effectiveness in uncovering hidden data. Here are some examples:
1) Exposing Directory Listings: The query intitle:"index of" confidential can expose directories containing sensitive files not meant for public access.
2) Finding Admin Pages: Using inurl:admin helps locate admin login pages, which might be unprotected and accessible to anyone.
3) Revealing Documents with Passwords: The query filetype:doc intext:"password" searches for word documents that may contain exposed passwords.
4) Locating Financial Data: A search like site:example.com filetype:xls could lead to publicly available spreadsheets containing financial data on a specific website.
5) Accessing Exposed Databases: The query inurl:php?id= is often used to find database records that are vulnerable to SQL Injection in Cyber Security Attacks.
Protect your business – start Cyber Security Risk Management Training today!
Search Operators and Commands
Mastering the right search operators is crucial for effective Google Dorking, as they allow you to filter results and uncover specific information with precision. Here are some key search operators and commands used in Google Dorking:
1) site: This operator restricts the search to a specific website or domain. For example, site:example.com will show results only from "example.com."
2) intitle: This command searches for a keyword within the title of web pages. Example: intitle:"login" displays pages with "login" in their title, often revealing login pages.
3) inurl: This operator searches for specific words within the URL. For example: inurl:admin helps locate URLs with "admin" in them, which might lead to admin panels.
4) filetype: This function is used to find specific file types, such as PDFs, Excel sheets, or word documents. For example, filetype:pdf "confidential" uncovers potentially sensitive PDF files.
5) intext: This command searches for a specific word or phrase within the content of web pages. Example: intext:"password" reveals pages containing the word "password," which might expose sensitive data.
Enhance your expertise in Computer Forensics with Computer Forensics Foundation Training – join today!
Risks Associated with Google Dorking
While Google Dorking can be a powerful tool for uncovering information, it also carries significant risks if used unethically or without proper precautions. The dangers associated with Google Dorking include:
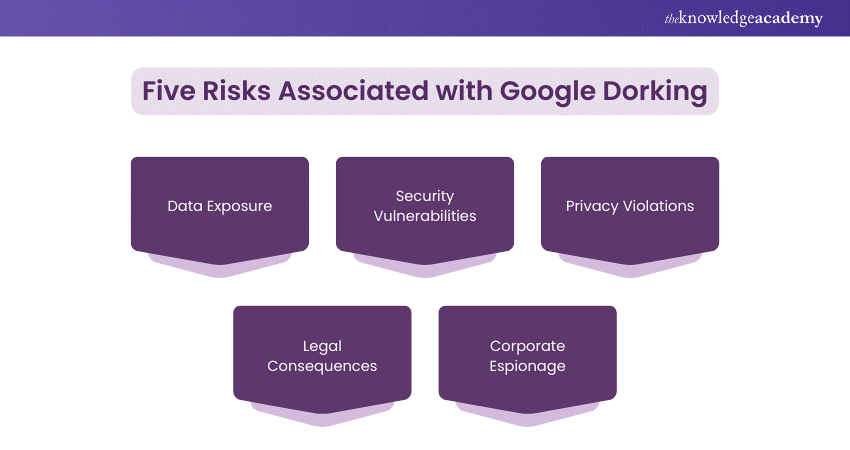
a) Data Exposure: Sensitive information, such as passwords, personal data, or confidential documents, can be unintentionally exposed and easily discovered using specific search queries.
b) Security Vulnerabilities: Hackers can exploit Google Dorking to identify weaknesses in websites, such as unprotected admin pages, exposed databases, or unsecured directories, potentially leading to security breaches.
c) Privacy Violations: Personal details, including addresses, medical records, or other private information, may be accessible, resulting in identity theft or malicious activities.
d) Legal Consequences: Misusing Google Dorking to access private or confidential information without authorisation can lead to legal repercussions, as it often crosses the line of ethical behaviour.
Corporate Espionage: Competitors may use Google Dorking to uncover proprietary data or business secrets that have been inadvertently exposed online, leading to potential corporate spying.
Master digital investigation techniques – register in Digital Forensics Trainingnow!
How to Prevent Google Dorking?
Given the risks associated with Google Dorking, organisations must adopt effective measures to protect their data and prevent unintended exposure. To safeguard against the dangers of Google Dorking, consider the following key steps:
a) Secure Sensitive Files: Ensure that confidential files are not stored in public directories, and implement strong access controls to restrict who can view or download these files.
b) Robots.txt Configuration: Use a robots.txt file to prevent search engines from indexing sensitive sections of your website, reducing the chances of them being exposed through Google Dorking.
c) Use Proper Permissions: Set strict permissions on files and directories to ensure that only authorised users can access them, minimising the risk of unauthorised access.
d) Regularly Audit Your Website: Conduct routine audits to identify and remove any exposed files or vulnerable pages that may have been indexed by search engines.
e) Avoid Storing Sensitive Data in URLs: Ensure that sensitive information is not included in URLs, as it can be easily discovered using Google Dorking techniques.
Conclusion
As we wrap up our journey into the fascinating world of Google Dorking, it’s clear that this technique opens up a realm of possibilities for those eager to explore the hidden corners of the internet. Whether you’re enhancing your Cyber Security skills, conducting Ethical Hacking, or simply satisfying your curiosity, mastering advanced search commands can be incredibly empowering. Remember, with great power comes great responsibility – always use your newfound skills ethically and responsibly.
Advance Your IT Security Career – Start CISM Certified Information Security Manager Training Today!
Frequently Asked Questions
What Browser is Best for Google Dorking?

The best browser for Google Dorking is typically Google Chrome, which is most compatible with Google's advanced search features and tools. However, other modern browsers like Firefox can also be effective.
What is the Name of the Google Dork Search?

The name of the Google Dork search is often referred to as "Google Dorking" or "Google Hacking." It involves using specific search operators like "intitle:", "inurl:", and "filetype:" to filter and uncover hidden or sensitive information from indexed websites. These searches can reveal files, login pages, and other data not easily visible through regular browsing.
What are the Other Resources and Offers Provided by The Knowledge Academy?

The Knowledge Academy takes global learning to new heights, offering over 3,000 online courses across 490+ locations in 190+ countries. This expansive reach ensures accessibility and convenience for learners worldwide.
Alongside our diverse Online Course Catalogue, encompassing 19 major categories, we go the extra mile by providing a plethora of free educational Online Resources like News updates, Blogs, videos, webinars, and interview questions. Tailoring learning experiences further, professionals can maximise value with customisable Course Bundles of TKA.
What is The Knowledge Pass, and How Does it Work?

The Knowledge Academy’s Knowledge Pass, a prepaid voucher, adds another layer of flexibility, allowing course bookings over a 12-month period. Join us on a journey where education knows no bounds.
What are the Related Courses and Blogs Provided by The Knowledge Academy?

The Knowledge Academy offers various Cyber Security Training, including the Cyber Security Awareness Training, Cyber Security Risk Management Training, and the Digital Forensics Training. These courses cater to different skill levels, providing comprehensive insights into the Top 8 Microsoft Security Essentials Alternatives.
Our IT Security & Data Protection Blogs cover a range of topics related to Cyber Security and data management, offering valuable resources, best practices, and industry insights. Whether you are a beginner or looking to advance your Information Security skills, The Knowledge Academy's diverse courses and informative blogs have got you covered.
Upcoming IT Security & Data Protection Resources Batches & Dates
Date
 Cyber Security Awareness
Cyber Security Awareness
Fri 9th May 2025
Fri 8th Aug 2025
Fri 5th Dec 2025






 Top Rated Course
Top Rated Course



 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


