We may not have the course you’re looking for. If you enquire or give us a call on +44 1344 203999 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.

In today's digital landscape, where cyber threats are ever-evolving, and data breaches can have severe consequences, prioritising the security of systems and sensitive information is essential. Microsoft recognises the criticality of maintaining robust safety measures and has developed their security compliance toolkit as a comprehensive solution to address these challenges.
This toolkit serves as a valuable resource for system administrators, security professionals, and IT teams, equipping them with the needful tools and guidance to configure and enhance the protection of Microsoft-based systems.
This blog will discuss the Microsoft Security Compliance Toolkit, its benefits, and the steps to use it.
Table of Contents
1) What is the Microsoft Security Compliance Toolkit?
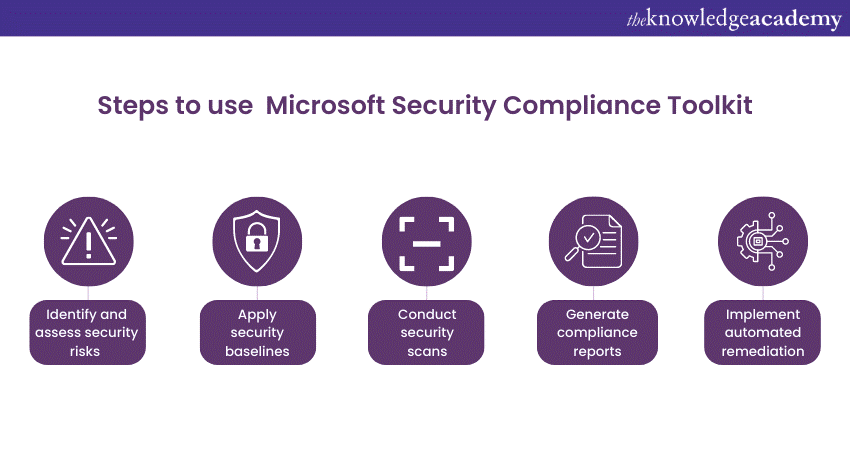
2) Step-by-Step Guide to Using the Microsoft Security Compliance Toolkit
a) Identify and assess Security Risks
b) Apply security baselines
c) Conduct security scans
d) Generate compliance reports
e) Implement automated remediation
3) Benefits of using the security compliance toolkit
4) Conclusion
What is the Microsoft Security Compliance Toolkit?
The Microsoft Security Compliance Toolkit is a comprehensive set of resources and tools used to assist organisations in securing their Microsoft-based systems effectively. It serves as an asset for system administrators, security professionals, and IT teams, offering guidance, best practices, and pre-defined safety settings to configure and protect Microsoft platforms.
The toolkit encompasses a wide range of Microsoft products and services, including Windows operating systems, the Azure cloud platform, the Office 365 productivity suite, and more. It provides a centralised repository of security baselines, configuration packs, and documentation that align with industry standards and regulatory requirements.
The toolkit is designed to simplify the complex task of securing Microsoft-based environments. It consolidates the most up-to-date security recommendations from Microsoft and industry experts, ensuring that users can implement safety configurations that are in line with the latest best practices.
Wish to become a Microsoft Security Engineer? Sign up for our Microsoft Security Engineer Training Courses now!
Step-by-Step Guide to Using the Microsoft Security Compliance Toolkit
Implementing the compliance toolkit may seem daunting, but it can be a streamlined process with the right approach and guidance. Here are the steps to use the toolkit and enhance the security of your systems:
1) Identify and assess security risks
The first step in using the toolkit is identifying and assessing the safety risks specific to your organisation. It is integral to thoroughly evaluate your systems, applications, and data to determine potential vulnerabilities and areas of weakness. This assessment will serve as a foundation for implementing appropriate safety measures.
2) Apply security baselines
Once you have identified the security risks, the next step is to apply the appropriate security baselines provided by the toolkit. These baselines are pre-defined sets of safety settings that align with industry standards and regulatory requirements. They serve as a starting point for securing your Microsoft-based systems.
Carefully review the available baselines and select the ones relevant to your environment. The toolkit offers baselines for various Microsoft services and products, such as Windows, Azure, and Office 365. Apply these baselines to your systems to ensure consistent and standardised safety configurations.
3) Conduct security scans
After applying the security baselines, it is crucial to conduct regular security scans to identify any deviations or vulnerabilities. The toolkit from Microsoft provides tools and utilities that enable you to scan your systems and assess their compliance with the applied baselines.
Leverage the scanning capabilities of it to identify safety gaps, misconfigurations, or potential risks. The scanning process will generate reports highlighting areas that require attention or remediation. These reports will serve as valuable insights for strengthening your safety posture.
4) Generate compliance reports
Compliance reporting is a vital aspect of maintaining a secure environment. The compliance toolkit offers features to generate compliance reports based on the applied security baselines and the results of security scans.
You must generate regular compliance reports to assess the level of adherence to safety standards and regulatory requirements. These reports will provide an overview of your organisation's security condition, identify areas of non-compliance, and help you prioritise remediation efforts.
5) Implement automated remediation
The toolkit offers automated remediation capabilities to streamline the security management process. These features allow you to automate the implementation of safety configurations and settings across your Microsoft-based systems.
Leverage its automated remediation capabilities to ensure consistent application of security baselines and settings. By automating the remediation process, you can minimise human error and reduce the time and effort required to maintain a secure environment.

Benefits of using the Security Compliance Toolkit
The compliance toolkit from Microsoft is perfect for organisations seeking to enhance safety measures and protect their systems. Let’s explore the benefits of using it:
Ensuring regulatory compliance
The toolkit simplifies meeting regulatory requirements by providing pre-defined security baselines and configuration packs. These resources align with standards such as the General Data Protection Regulation (GDPR), Health Insurance Portability and Accountability Act (HIPAA), Payment Card Industry Data Security Standard (PCI DSS), and more.
Streamlining security processes
Securing Microsoft-based systems can be a complex and time-consuming task. The toolkit streamlines this process by providing a centralised repository of resources, tools, and best practices. It consolidates the most up-to-date safety recommendations from Microsoft and industry experts, enabling organisations to implement safety configurations efficiently.
Enhancing security measures
The toolkit's primary goal is to enhance organisations' overall safety measures. By applying the provided security baselines and configuration packs, businesses can strengthen their safety posture and protect against potential threats.
It offers standardised and consistent safety configurations, ensuring systems are hardened and resilient to attacks. It provides a framework to identify vulnerabilities, conduct security scans, generate compliance reports, and implement automated remediation.
Ready to dive into the fundamentals of Microsoft Security Compliance and Identity? Register for our Microsoft Security, Compliance, And Identity Fundamentals SC900 Course today!
Conclusion
In conclusion, the toolkit is a valuable resource for organisations seeking to enhance the safety of their Microsoft-based systems. We hope this blog has aided in improving your understanding of what the Microsoft Security Compliance Toolkit is, the steps to use it, and its benefits.
Acquire the skills to design security for infrastructure by signing up for our Microsoft Cybersecurity Architect SC100 Course now!
Upcoming IT Security & Data Protection Resources Batches & Dates
Date
 Microsoft Cybersecurity Architect SC100
Microsoft Cybersecurity Architect SC100
Mon 17th Feb 2025
Mon 16th Jun 2025
Mon 11th Aug 2025
Mon 13th Oct 2025
Mon 8th Dec 2025







 Top Rated Course
Top Rated Course


 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


