We may not have the course you’re looking for. If you enquire or give us a call on +44 1344 203 999 and speak to our training experts, we may still be able to help with your training requirements.
We ensure quality, budget-alignment, and timely delivery by our expert instructors.

The ISO 27005 Risk Assessment Process provides organisations with a structured approach to navigate the complex domain of Information Security Risks. In this blog, we embark on a journey to demystify and embrace the ISO 27005 Risk Assessment Process. From defining the scope to assessing risks and developing treatment plans, we will explore each facet.
Read this blog to learn how the ISO 27005 Risk Management Process is used for information security. Establish context, define risk appetite, and protect your organisation from breaches. Join us as we unlock the potential of ISO 27005 for a safer, more secure digital future.
Table of Contents
1) Understanding ISO 27005
2) Key components of ISO 27005 Risk Assessment Process
3) Implementing ISO 27005 Risk Assessment
a) Define the scope
b) Identify assets
c) Identify threats and vulnerabilities
d) Assess risks
e) Develop risk treatment plans
4) Conclusion
Understanding ISO 27005
Understanding ISO 27005 is critical for establishing strong Information Security practices. ISO 27005 is a standard within the ISO 27000 series, specifically managing Risk Management in Information Security.
This standard is built upon a risk-based philosophy, emphasising the need for organisations to tailor their security measures to address the specific risks they face. ISO 27005 helps organisations understand their Information Security landscape by defining Risk Assessment methodologies, criteria, and scopes.
By following ISO 27005, organisations can effectively prioritise and allocate resources to mitigate potential threats, achieve compliance, and ultimately bolster their data security posture. It serves as a roadmap for organisations to navigate the complex terrain of modern Cybersecurity, helping them stay proactive and resilient in the face of evolving threats.
Ready to elevate your organisation's Information Security Risk Management practices? Explore our ISO 27005 Training!
Key components of ISO 27005 Risk Assessment Process
The critical components of the ISO 27005 Risk Assessment Process form the foundation for a systematic and comprehensive approach to managing Information Security Risks. These components work together to identify, analyse, evaluate, and treat risks effectively:
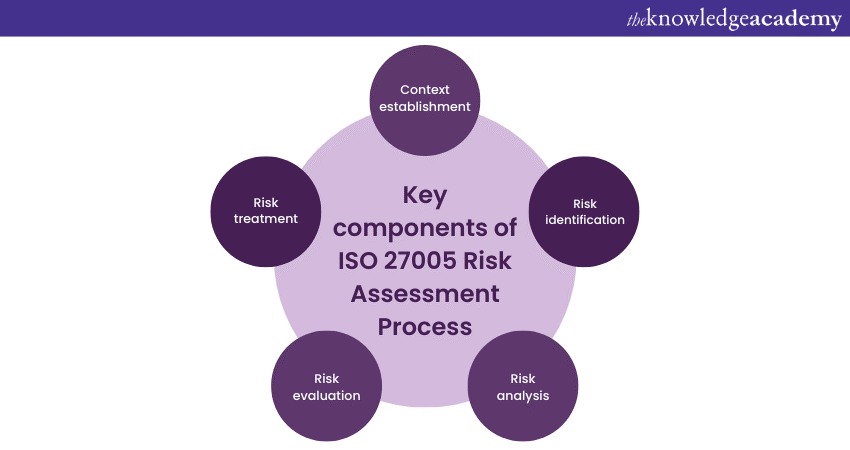
a) Establishing the context: This initial step sets the stage for the Risk Assessment Process. Organisations define the scope, objectives, and context of the assessment. It involves specifying the Risk Assessment methodology, criteria for risk acceptance, and the overall framework for Risk Management.
b) Risk identification: Here, organisations identify assets, threats, and vulnerabilities within their scope. Threats encompass potential sources of harm, while vulnerabilities are weaknesses that those threats may exploit. Comprehensive identification is crucial to understanding the landscape of potential risks.
c) Risk analysis: Once identified, risks undergo examination to determine their potential impact and likelihood. Impact refers to the harm that could result from a risk materialising, while likelihood assesses the probability of it happening. This analysis helps prioritise risks and focus resources on the most critical areas.
d) Risk evaluation: In this step, organisations combine the risk analysis results to evaluate the overall level of risk. Typically, this is done by assigning risk scores or ratings. The evaluation assists in making informed decisions about which risks need immediate attention and which can be managed over time.
e) Risk treatment: Finally, organisations develop risk treatment plans. These plans outline strategies to mitigate, transfer, or accept risks. Mitigation measures aim to reduce the risk's impact or likelihood, while risk transfer involves mechanisms like insurance. Acceptance acknowledges that some risks may be within acceptable tolerances or that the cost of mitigation outweighs the potential harm.
Ready to elevate your organisation's Information Security Risk Management practices? Then, explore our ISO 27005 Training!
Implementing ISO 27005 Risk Assessment
Implementing the ISO 27005 Risk Assessment Process is critical for organisations aiming to safeguard their information assets and maintain robust cybersecurity. This systematic approach helps effectively identify, analyse, evaluate, and mitigate risks.
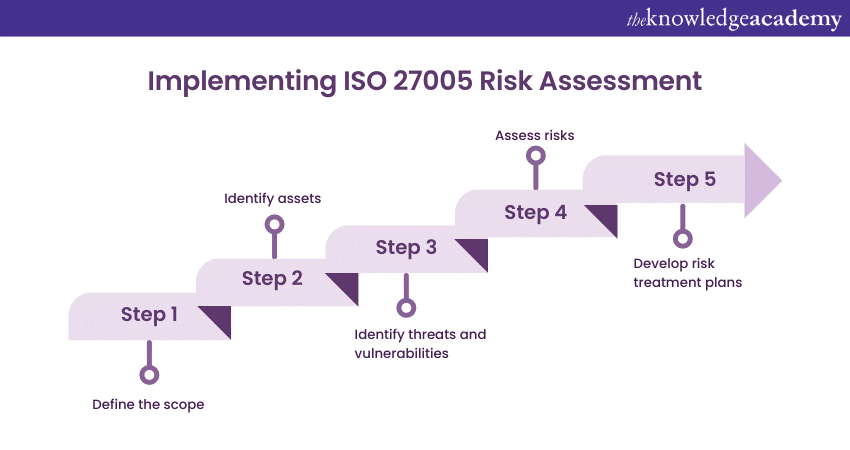
Define the scope
It is essential to clearly describe the scope of the Risk Assessment Process before beginning to determine what you want to achieve through Risk Assessment. It could be compliance, improved security, or protecting critical assets. Specify the scope's boundaries, including the support, processes, and areas to be assessed. This could range from a specific department to the entire organisation.
Choose a Risk Assessment methodology that aligns with your organisation's goals and resources. ISO 27005 provides several methods, including qualitative, quantitative, or a combination of both. Define the criteria for assessing and accepting risks. These criteria can vary based on organisational priorities, regulatory requirements, or industry standards.
Identify assets
The next crucial step is identifying all the assets within your defined scope. Identify sensitive data such as customer information, financial records, intellectual property, and proprietary information. List the hardware and software systems supporting your organisation's operations. Consider the human resources within your organisation, including their roles and access to information. Include physical assets like buildings, servers, and networking equipment.
Identify threats and vulnerabilities
You must identify potential threats and vulnerabilities that could exploit your identified assets. Threats can originate from various sources. Consider the risks posed by events like earthquakes, floods, or fires.
Evaluate the threat landscape for malware, phishing attacks, data breaches, and other cyber threats. Assess the risks associated with unintentional actions or negligence by employees. Consider potential threats from competitors attempting to gain a competitive advantage through illicit means.
Assess risks
Determine the potential consequences of a risk if it were to materialise. This might include financial losses, reputation damage, legal penalties, or operational disruptions. Assign impact values based on severity, such as low, moderate, or high.
Evaluate the probability of a risk occurring. Factors influencing likelihood include historical data, current security measures, and external threats. Assign likelihood values, such as rare, unlikely, possible, or probable.
Calculate a risk score by combining the assigned impact and likelihood values. Standard scoring methods include numeric scales, colour-coding, or descriptive scales like low, medium, and high. This scoring helps prioritise risks for further analysis. After scoring, classify risks, such as bass, moderate, and increased risk. This classification guides subsequent risk treatment decisions.
Develop risk treatment plans
Once you have assessed the risks, it is time to develop risk treatment plans to mitigate, transfer, or accept them. Develop mitigation strategies for high and moderate stakes to reduce their impact or likelihood. These strategies include implementing security controls, training employees, or improving disaster recovery plans.
Organisations may sometimes transfer risks, typically through insurance or outsourcing. Ensure that the terms and conditions of risk transfer agreements are well-defined and align with your organisation's objectives.
For low risks, organisations may opt to accept them. However, even taken risks should be monitored, and contingency plans should be in place if they escalate. Implement the chosen risk treatment measures and continually monitor their effectiveness.
Regularly review and update risk treatment plans as the threat landscape evolves. Document all risk treatment plans and associated actions, responsibilities, and timelines. Clear documentation ensures that everyone involved in Risk Management understands their roles and responsibilities.
Conclusion
Ready to strengthen your risk management strategy? Get the ISO 27005 PDF and start implementing best practices for information security.
The ISO 27005 Risk Assessment Process is not merely a compliance requirement but a strategic imperative in Information Security. By systematically implementing this process, organisations gain the tools to proactively identify, assess, and mitigate risks that could jeopardise their critical assets and data. In a world with cyber threats, ISO 27005 equips organisations with the resilience to adapt and respond effectively. Embrace ISO 27005 as a cornerstone of your security strategy, ensuring a safer digital domain for your organisation and its stakeholders.
Upcoming IT Security & Data Protection Resources Batches & Dates
Date
 ISO 27005 Foundation
ISO 27005 Foundation
Mon 31st Mar 2025
Mon 30th Jun 2025
Mon 6th Oct 2025






 Top Rated Course
Top Rated Course



 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


