We may not have the course you’re looking for. If you enquire or give us a call on +39 800580270 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.
In today's interconnected digital landscape, DNS Security plays a pivotal role in safeguarding networks and data. DNS Security encompasses a set of measures designed to fortify the Domain Name System, the backbone of internet communication. This comprehensive blog explores the core principles and techniques underpinning DNS Security, providing a clear understanding of what DNS Security is and how it fortifies online infrastructure.
Delve into the intricate world of DNS protection and discover the tools and strategies that ensure your network remains resilient in the face of evolving cyber threats.
Table of Contents
1) Definition of DNS Security
2) Importance of DNS Security
3) How does DNS Security function?
4) List of common DNS Attacks
5) How is DNS utilised in attacks?
6) What is DNSSEC?
7) Common DNS Security extensions
8) How DNS Security improves security & performance?
9) Top trends of DNS Security
10) Best practices of DNS Security
11) Conclusion
Definition of DNS Security
Domain Name System, or DNS Security, refers to the measures and protocols implemented to protect the DNS infrastructure from cyber threats and vulnerabilities. The DNS serves as a critical component of internet functionality, translating human-readable domain names into IP addresses that computers can understand. Without proper security measures, DNS is susceptible to various attacks, including DNS cache poisoning, Distributed Denial-of-Service (DDoS) attacks, and domain hijacking. DNS Security encompasses techniques like DNS Security Extensions (DNSSEC) to add cryptographic signatures to DNS data, ensuring data integrity and authenticity. It also involves firewalls, intrusion detection systems, and monitoring to safeguard DNS servers and mitigate risks, providing a secure and reliable internet experience.
Elevate your DNS expertise with BIND DNS Administration Training and fortify your network security today.
Importance of DNS Security
DNS Security is of paramount importance in the digital age, as the DNS is a critical component of internet infrastructure. Ensuring its security is vital for several reasons:
1) Data protection: Secure DNS prevents unauthorised access and modification of DNS records, safeguarding sensitive data like IP addresses. It protects users from being redirected to malicious sites.
2) Business continuity: DNS Attacks can disrupt online services and lead to downtime, impacting businesses. DNS Security measures ensure business continuity.
3) Preventing malware: DNS Security helps detect and block malware by identifying malicious domains and preventing communication with command and control servers.
4) Privacy: Secure DNS protocols protect user privacy, preventing eavesdropping on DNS queries and the sites users visit.
How Does DNS Security Function?
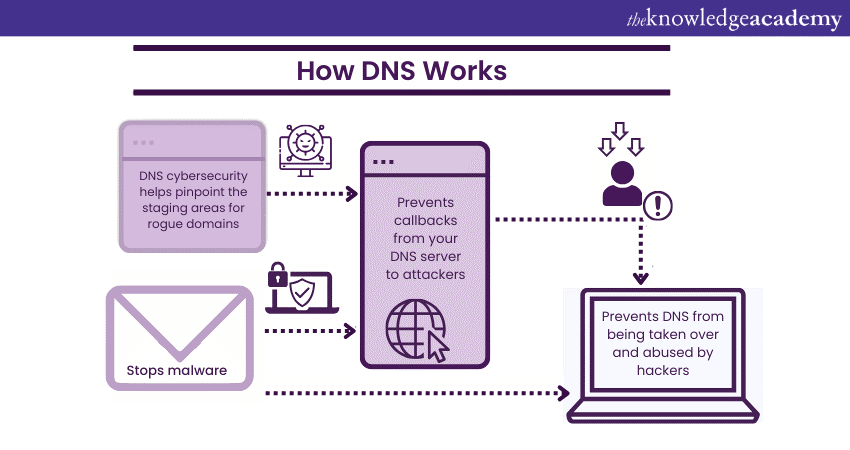
Monitoring DNS requests and the associated IP addresses is a crucial aspect of network security. It helps in the early detection of potential threats and ensures a safer online environment. Implementing security policies that identify unusual DNS behaviour enhances network protection and aids in the prompt identification of malicious activities and compromised systems.
DNS Security plays a vital role in identifying the origins of rogue domains. To prevent unauthorised infiltration or exfiltration attempts, such as DNS leaks, it's essential to secure DNS servers and block queries from potential staging sites across various ports and protocols. In cases where compromised devices access your network, DNS Security becomes a shield against any malware they may attempt to transmit. Additionally, it thwarts any attempts by hackers to hijack your DNS server by disrupting the communication lines between the server and potential attackers, ensuring the integrity and security of your DNS infrastructure.
List of common DNS Attacks
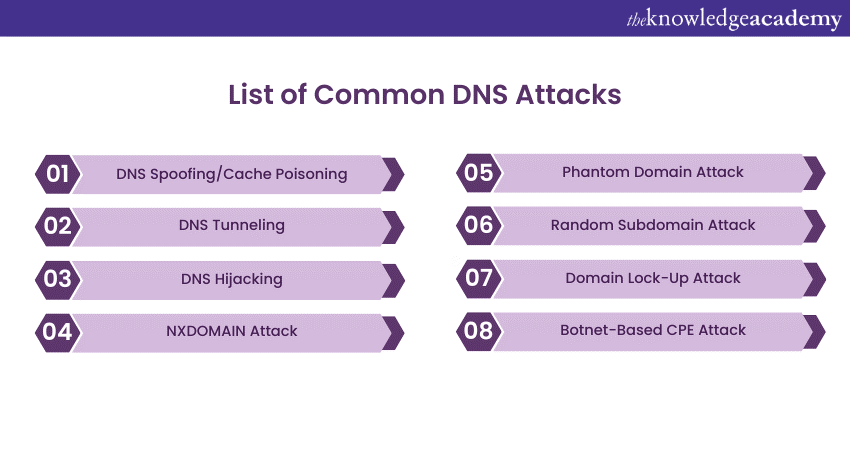
Attackers have devised various strategies to exploit DNS servers, posing significant security risks. The following are common DNS Attacks:
a) DNS Spoofing/Cache Poisoning: Attackers insert counterfeit DNS data into a resolver's cache, causing the resolver to provide an incorrect IP address for a domain. This can divert traffic to a malicious destination, often a replica of the original site used for distributing malware or collecting sensitive information.
b) DNS Tunnelling: This technique leverages other protocols like Secure Shell (SSH), Transfer Control Protocol (TCP), or Hyper Text Transfer Protocol (HTTP) to tunnel through DNS queries and responses. Malicious actors can pass malware or stolen data within DNS queries, bypassing conventional firewall detection.
c) DNS Hijacking: In DNS hijacking, attackers redirect queries to a different domain name server. This can be achieved through malware or unauthorised modification of a DNS server. Unlike DNS spoofing, this attack targets the DNS record of the website on the nameserver, not a resolver's cache.
d) NXDOMAIN Attack: This DNS flood attack overwhelms a DNS server with requests for non-existent records, aiming to disrupt legitimate traffic and cause a denial-of-service situation. Advanced attack tools can auto-generate unique subdomains for each request, potentially filling a recursive resolver's cache with junk requests.
e) Phantom Domain Attack: Similar to an NXDOMAIN attack, a phantom domain attack disrupts DNS resolvers. Attackers set up phantom domain servers that respond slowly or not at all, causing resolvers to wait for responses. This leads to slow performance and denial of service.
f) Random Subdomain Attack: Attackers send DNS queries for numerous random, non-existent subdomains of a legitimate site. The objective is to overwhelm the domain's authoritative nameserver, making it challenging to look up the website. This also burdens the ISP serving the attacker, as their resolver's cache accumulates bad requests.
g) Domain Lock-Up Attack: In this attack, attackers create special domains and resolvers to establish TCP connections with legitimate resolvers. When the targeted resolvers send requests, these domains respond with slow streams of random packets, consuming the resolver's resources.
h) Botnet-Based CPE Attack: Perpetrators employ Customer Premises Equipment or CPE devices provided by service providers to customers (e.g., modems, routers) in botnet-based attacks. Compromised CPEs become part of a botnet used to execute random subdomain attacks against a single site or domain.
Elevate your IT skills and knowledge – Join our IT Support and Solutions Training today and become a tech expert!
How is DNS utilised in attacks?
DNS infrastructure is a critical component of the Internet, but it's also a prime target for various threats, including:
a) Distributed Denial of Service (DDoS): DDoS attacks against DNS servers can render websites inaccessible by overwhelming DNS servers with a barrage of seemingly legitimate traffic. A notable case is the 2016 DDoS attack on Dyn, where a botnet consisting of Internet-connected cameras disrupted major websites like Amazon, Netflix, Spotify, and Twitter.
b) DNS DDoS Amplification: DNS relies on User Datagram Protocol or UDP, a connectionless transport protocol, making it vulnerable to source address spoofing. Attackers can manipulate DNS responses to be much larger than requests, leveraging this to amplify their attacks. By sending a small request to a DNS server, they trigger a massive response directed at the target, resulting in a Denial of Service (DoS) situation for the target host.
c) Other Denial of Service (DoS) Attacks: Besides network-based DDoS attacks, DNS server applications can be targeted by application-layer DoS attacks. These attacks exploit vulnerabilities in DNS server applications, rendering them incapable of responding to legitimate requests, further disrupting service.
What is DNSSEC?
DNS Security Extensions (DNSSEC) is a crucial security protocol devised to address these vulnerabilities. Its primary objective is to safeguard against various attacks by applying digital signatures to data, ensuring its integrity. This signing process is analogous to a person signing a legal document with a distinctive signature; it's unique and verifiable. In DNSSEC, these digital signatures serve to validate that data remains unaltered.
DNSSEC adopts a hierarchical digital signing approach across all DNS layers. For instance, in a 'google.com' lookup, the root DNS server signs a key for the .COM nameserver, which, in turn, signs a key for Google.com's authoritative nameserver. Importantly, DNSSEC maintains compatibility with traditional DNS lookups to ensure accurate resolution, albeit without added security. It functions synergistically with other security measures like SSL/TLS, forming a comprehensive internet security strategy.
DNSSEC establishes a chain of trust between parent and child domains, extending to the root zone. Uncompromised integrity at any DNS layer is essential; otherwise, requests become vulnerable to on-path attacks. To solidify this trust chain, the root zone itself undergoes human validation. A Root Zone Signing Ceremony, involving selected individuals from across the globe, publicly and meticulously signs the root DNSKEY RRset, assuring its untampered status.
Elevate your organisation's defence strategies – Register for Security Management, Planning, and Asset Protection Training now.
Common DNS Security Extensions
The four most common DNS Security Extensions are:
a) DNS Key: DNSKEY is a critical Extension that introduces cryptographic public and private key pairs into the DNS. These key pairs are used to create digital signatures for DNS data, ensuring its authenticity and integrity.
b) Resource Record Signature (RRSIG): RRSIG is employed to store digital signatures for DNS resource records. Each RRSIG covers a specific DNS resource record set, validating its legitimacy.
c) Next-Secure (NSEC): NSEC records are used to indicate the non-existence of a specific domain name between two existing domain names in a signed zone. They help prevent DNS cache poisoning attacks by providing authenticated denial of existence.
d) Delegation Signer (DS): DS records are used to establish a chain of trust between parent and child zones. The parent zone signs its child zone's DNSKEY with a DS record, ensuring that the child zone's keys are legitimate and not tampered with.
How DNS Security improves security & performance?
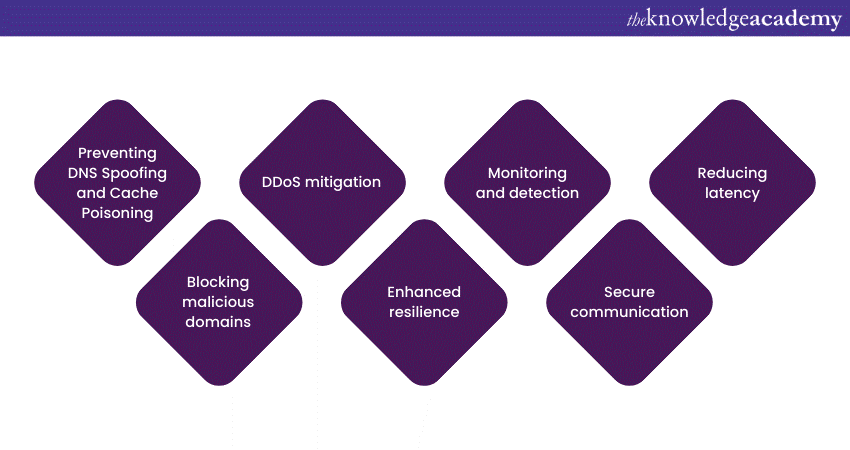
DNS Security plays a crucial role in enhancing both the security and performance of network services. It addresses vulnerabilities in DNS infrastructure to protect against various cyber threats and improve the overall efficiency of the DNS system. Here's how DNS Security contributes to enhanced security and performance:
a) Preventing DNS Spoofing and Cache Poisoning: DNS Security measures like DNSSEC use digital signatures to verify the authenticity and integrity of DNS data. This protection prevents attackers from poisoning DNS caches and spoofing DNS records, ensuring users are directed to the correct websites.
b) Blocking malicious domains: DNS filtering and firewalling are used to block access to known malicious domains, limiting the risk of users accessing harmful content or being redirected to malicious sites.
c) DDoS mitigation: DDoS attacks can disrupt DNS services by overwhelming servers with traffic. DNS Security solutions help in mitigating such attacks, ensuring DNS services remain available during high-traffic events.
d) Enhanced resilience: Anycast routing distributes DNS requests across multiple geographically dispersed servers. This approach increases the resilience of DNS services, making it more difficult for attackers to target a single point of failure and ensuring service availability.
e) Monitoring and detection: DNS Security practices involve continuous monitoring of DNS traffic and maintaining detailed logs. This proactive approach helps detect unusual or suspicious DNS activity, allowing for early intervention against potential security threats.
f) Secure communication: Using secure communication protocols like DNS over HTTPS (DoH) or DNS over TLS (DoT) encrypts DNS queries and responses during transmission. This ensures that data privacy and integrity are maintained, reducing the risk of eavesdropping and data manipulation.
g) Reducing latency: By improving DNS resolution times through optimised server selection and load balancing, DNS Security measures help reduce network latency and enhance the overall performance of web services.
Unlock the world of networking expertise – Join our Introduction to Networking Training today and embark on a journey of limitless digital connectivity.
Top trends of DNS Security
Five prominent trends are propelling DNS Security into the spotlight:
a) Critical role in healthcare security: DNS Security has become indispensable in protecting healthcare services, particularly as the sector is increasingly targeted by cyber threats. Ensuring the integrity and availability of healthcare data is of paramount importance, and DNS Security plays a vital role in achieving this.
b) Data exfiltration prevention: The value of DNS Security as a defence against data exfiltration is on the rise. By monitoring DNS traffic, organisations can thwart attempts to siphon sensitive data out of their networks, safeguarding confidential information and maintaining data privacy.
c) Whitelisting for IoT security: DNS Security is embracing whitelisting techniques to bolster the security of Internet of Things (IoT) ecosystems. By allowing only trusted devices and connections, organisations can mitigate the risks associated with IoT vulnerabilities and prevent attackers from exploiting these ecosystems.
d) Hybrid work environment protection: With the proliferation of hybrid work arrangements, DNS Security is extending its reach to secure multi-cloud workplaces. As organisations operate across various cloud environments, ensuring the security and reliability of DNS services is crucial for maintaining productivity and data protection.
e) Response to high-profile attacks: The increasing prevalence of high-profile cyberattacks, often involving DNS manipulation, is driving the adoption of DNS Security. News-making incidents highlight the urgency of fortifying DNS infrastructure against various threats, making DNS Security an integral component of a comprehensive cybersecurity strategy.
Best Practices of DNS Security
To enhance DNS Security, consider these five best practices:
a) Enable DNS Logging: Keep track of client activities and resolve DNS-related issues efficiently.
b) Lock DNS Cache: Control access to your cache to thwart unauthorised data exploitation.
c) Filter DNS Requests: Block malicious domains to prevent potential threats from accessing your network.
d) Configure Access Control Lists (ACLs): Restrict DNS system access to authorised administrators only, minimising the risk of unauthorised alterations.
e) Implement DNSSEC: Use digital signatures to validate DNS data and maintain data integrity.
Conclusion
In an age where data breaches and cyberattacks pose formidable challenges, DNS Security emerges as an indispensable fortress. Understanding What is DNS Security nd what it entails is pivotal to fortifying digital ecosystems. This blog elucidates its core principles, empowering you to navigate the intricate realm of DNS Security with confidence.







 Top Rated Course
Top Rated Course




 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


