We may not have the course you’re looking for. If you enquire or give us a call on +39 800580270 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.
In our digital age, staying safe online is more important than ever. Ethical hacking and cyber security experts play essential roles in protecting our data. Though both aim to secure information, their methods and responsibilities differ significantly. Here, we will delve into Ethical Hacking vs Cyber Security to understand the key difference between them.
Understanding these differences can help you appreciate their unique contributions. Are you curious about what sets them apart? This blog will guide you through Ethical Hacking vs Cyber Security. Let’s dive in!
Table of Contents
1) What is Cyber Security?
2) What is Ethical Hacking?
3) A Comparison Table: Ethical Hacking vs. Cyber Security
4) Differences Between Cyber Security and Ethical Hacking
5) Conclusion
What is Cyber Security?
Cyber Security safeguards an organisation's network, system, and data from cyber theft or crime. It stops data breaches, attacks from hostile entities, or unauthorised entry into the system. Professionals in cybersecurity need a deep comprehension of cybersecurity principles to prevent cybercriminal activities and safeguard systems from hackers.
Cybercrimes are on the rise every day. The hackers employ powerful encryption codes to gain access to a system and pilfer data. They employ various types of cyber attacks such as phishing, brute force entry, malware, ransomware, threatware, viruses, etc.
Phases of Cyber Security
Cyber security experts carry out phases in cyber security, requiring a solid grasp of multiple technical and computing subjects. There are four main phases that these can be divided into.
a) Recognise: This stage consists of identifying and comprehending different cyber security threats to the system and data.
b) Secure: Putting in place measures to guarantee data privacy.
c) Identify: The act of recognising cyber security incidents in real time.
d) Reacting: Responding effectively to identified cyber security incidents.
What is Ethical Hacking?
Consider creating an app with strong security measures: How can you guarantee its true security? Testing it for potential security breaches is the solution to that. This is precisely what ethical hacking involves.
Ethical hacking, a branch of cybersecurity, concentrates on discovering weaknesses in a system and addressing them before malicious hackers can benefit from them. Testing and validating systems are done to uncover weaknesses and report these flaws to the organisation. Penetration testers, who are also called cyber security professionals, are frequently in charge of this duty.
Benefits of Ethical Hacking
The Benefits of Ethical Hacking are numerous. It is a wide area that involves a methodical and preventive strategy to reduce risks and prevent any harmful events on the system. A few benefits of ethical hacking include:
a) Evaluating the robustness of passwords
b) Testing exploits to verify security settings and privilege levels in domain account and database administration.
c) Conducting penetration testing regularly is important after each software update/upgrade or when implementing a new security patch.
d) Making sure that communication of data cannot be intercepted.
e) Evaluating the legitimacy of authentication protocols.
f) Making sure that applications have security measures in place to safeguard the databases of both organisations and users.
g) Protection from denial-of-service attacks.
h) Testing of anti-intrusion features and network security.
Learn the basics of Ethical Hacking with our Ethical Hacking Professional Course – register today!
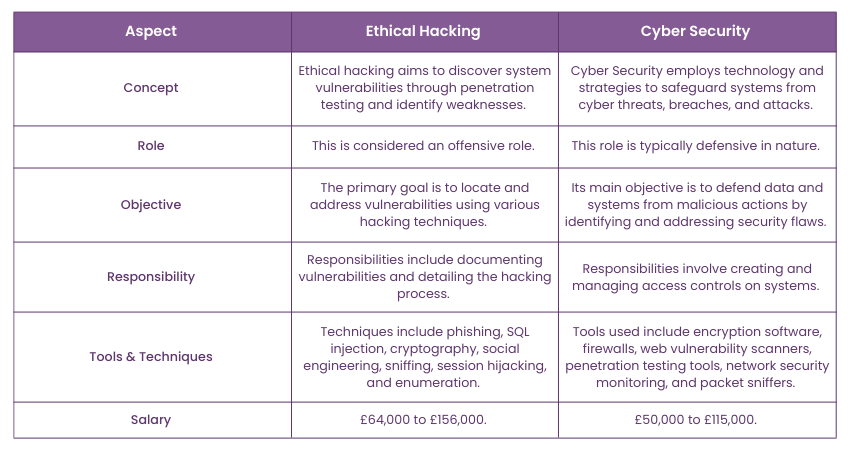
A Comparison Table: Ethical Hacking vs. Cyber Security
Cyber Security safeguards systems and data against cyber threats, whereas Ethical Hacking evaluates weaknesses through simulated attacks. Here is a comparison table between Ethical Hacking and Cyber Security :
Gain the skills to safeguard sensitive information with our Cyber Security Awareness Course – join today!
Differences Between Cyber Security and Ethical Hacking
1) Cyber Security vs Ethical Hacking: Objective
Cyber Security aims to defend systems from cyber threats by implementing protective measures and monitoring for breaches. In contrast, Ethical Hacking seeks to identify and address vulnerabilities by simulating attacks, helping to enhance system security.
2) Cyber Security vs Ethical Hacking: Methods
Cyber Security employs defensive tools such as firewalls, encryption, and security protocols to prevent unauthorised access and data breaches. Ethical Hacking uses techniques like phishing, SQL injection, and penetration testing to discover and fix system weaknesses.
3) Cyber Security vs Ethical Hacking: Work Intention
Cyber Security focuses on a defensive strategy to protect and secure systems from potential attacks and breaches. Ethical Hacking, however, adopts an offensive approach to proactively identify and resolve vulnerabilities by mimicking real-world attack scenarios.
4) Roles of Ethical Hacking
Ethical Hacking plays a major role in the security and integrity of Information Systems. Here are the key roles of Ethical Hackers:
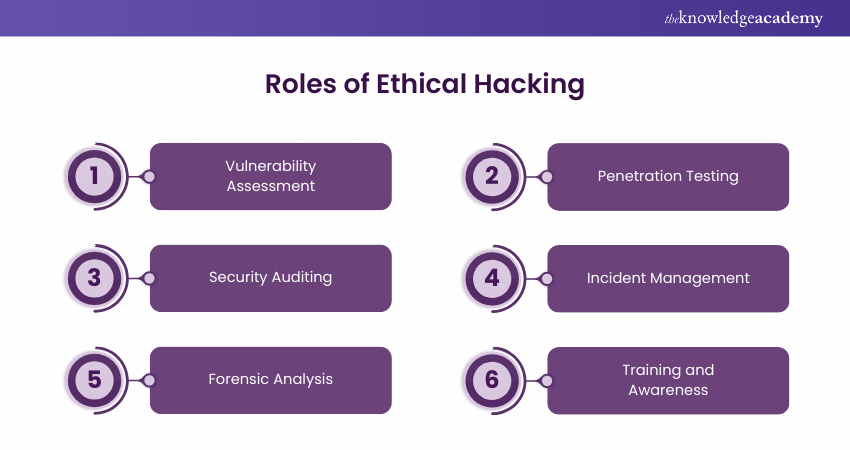
a) Vulnerability Assessment: Ethical Hackers carry out assessments to find out which systems, networks, and applications are vulnerable. This means the process of detecting the weak spots which include the software that is outdated, the faulty configurations, and the vulnerability to the malware attacks.
b) Penetration Testing: While vulnerability assessments find the possible security weaknesses, Penetration Testing is the one that uses these weaknesses to evaluate the possible breaches. Through this, the organisations are able to find out the real effectiveness of their current security systems in the real world.
c) Security Auditing: Ethical Hackers are engaged in a thorough examination of the existing security policies and procedures. This involves the check of the compliance to the required standards and rules to ensure that the safety procedures are current.
d) Incident Management: If there is a security breach, Ethical Hackers deal with the problem by looking into it and thus, the situation is prevented from happening again.
e) Forensic Analysis: After the breach, Ethical Hackers usually carry out forensic analysis, which includes the cause and the method of the attack. This study is significant for the knowledge of the causes of the breaches and the ways to prevent them in the future.
f) Training and Awareness: Ethical Hackers are not only responsible for the preservation of the company but they also train the employees the best security practices. They also inform them about the newest Cyber Security risks and how to prevent them.
5) Cyber Security vs Ethical Hacking: Process
The Cyber Security process involves routine maintenance, updates, and monitoring to ensure continuous protection against cyber threats. Ethical Hacking involves systematic testing and simulating attacks to uncover and resolve security gaps before malicious actors can exploit them.
6) Cyber Security vs Ethical Hacking: Responsibilities
Cyber Security professionals are reliable for designing and managing security measures, such as access controls and incident response protocols. Ethical Hackers are tasked with identifying vulnerabilities through simulated attacks and providing recommendations to enhance security.
7) Roles of Cyber Security
Cyber Security professionals play diverse roles, each critical to maintaining the digital fortress of an organisation:
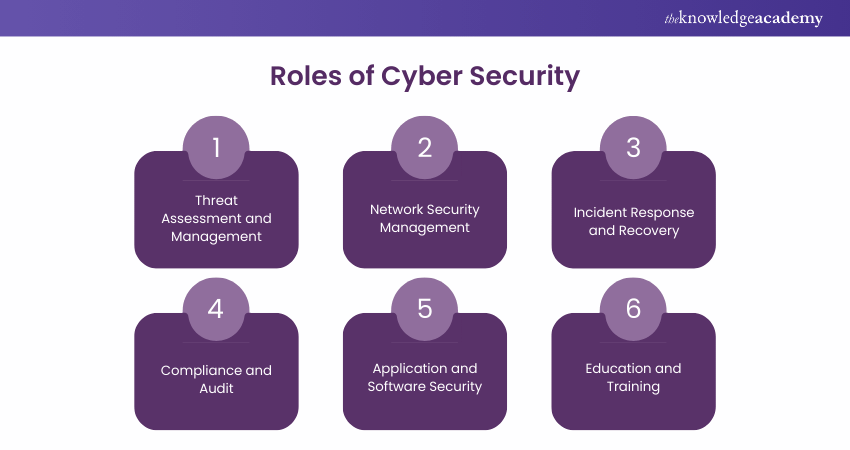
a) Threat Assessment and Management: The specialists find the possible risks to the organisation's digital assets and suggest ways to cope with them. This includes the monitoring of the new and the upcoming cyber dangers.
b) Network Security: MCyber Security standards and regulations. Cyber Security specialists do the security audits to check the security posture of the organisation against these standards.
c) Application and Software Security: This role is about creating security in the applications and the software, from the design to the development and the updates, so that they are free from vulnerabilities.
d) Education and Training: Cyber Security specialists instruct and mentor other employees in the best practices for security and the newest cyber threats. Thus, they spread security awareness in the company.
Conclusion
Ethical Hacking and Cyber Security are two distinct but related fields. Cyber Security protects systems and data from threats, Ethical Hacking, on the other hand, identifies the vulnerabilities. This blog on Ethical Hacking vs Cyber Security will guide you through unique roles, methods, and how they work together to strengthen your security strategy . Thus, they are the pillars of the whole security system, which makes it stronger.
Learn how cyber-attacks are executed with our Cyber Security Risk Management Course – join today!
Frequently Asked Questions

Integrate Cyber Security by establishing robust protection measures and regular updates. Incorporate Ethical Hacking by scheduling periodic penetration tests and vulnerability assessments to identify and address weaknesses proactively, enhancing overall security.

Ethical hackers must obtain explicit permission before testing systems, avoid causing harm, and report findings responsibly. They should adhere to legal standards and confidentiality agreements to ensure their actions are ethical and align with organisational security policies.

The Knowledge Academy takes global learning to new heights, offering over 30,000 online courses across 490+ locations in 220 countries. This expansive reach ensures accessibility and convenience for learners worldwide.
Alongside our diverse Online Course Catalogue, encompassing 17 major categories, we go the extra mile by providing a plethora of free educational Online Resources like News updates, Blogs, videos, webinars, and interview questions. Tailoring learning experiences further, professionals can maximise value with customisable Course Bundles of TKA.

The Knowledge Academy’s Knowledge Pass, a prepaid voucher, adds another layer of flexibility, allowing course bookings over a 12-month period. Join us on a journey where education knows no bounds.

The Knowledge Academy offers various Cyber Security Courses, including the Certified Cyber Security Professional Course, Cyber Security Awareness Course, and Cyber Security Risk Management Course. These courses cater to different skill levels, providing comprehensive insights into Information Security Risk Management.
Our IT Security & Data Protection Blogs cover a range of topics related to Cyber Security, offering valuable resources, best practices, and industry insights. Whether you are a beginner or looking to advance your Cyber Security skills, The Knowledge Academy's diverse courses and informative blogs have got you covered.
Upcoming IT Security & Data Protection Resources Batches & Dates
Date
 Ethical Hacking and Penetration Testing Training
Ethical Hacking and Penetration Testing Training
Fri 10th Jan 2025
Fri 14th Mar 2025
Fri 9th May 2025
Fri 11th Jul 2025
Fri 12th Sep 2025
Fri 14th Nov 2025







 Top Rated Course
Top Rated Course



 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


